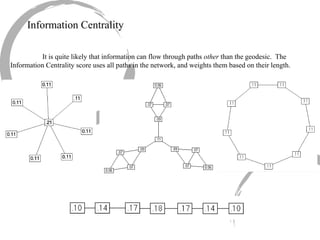
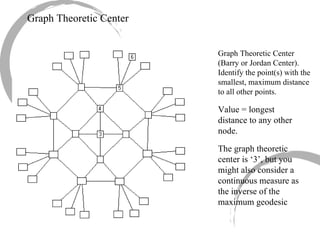
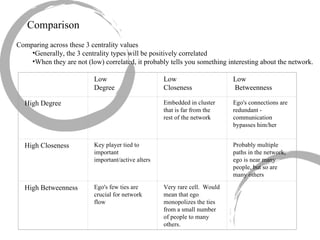
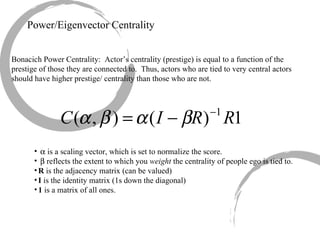
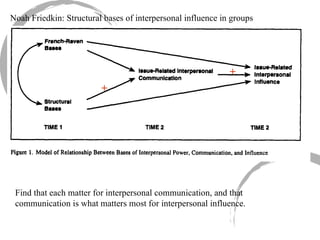
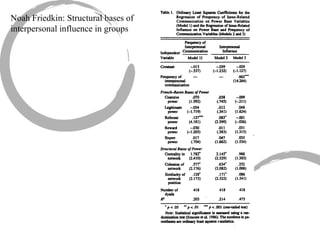
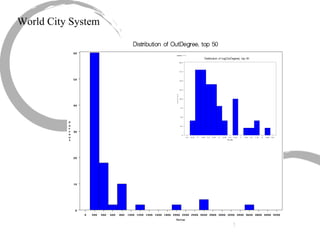
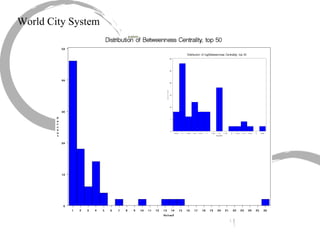
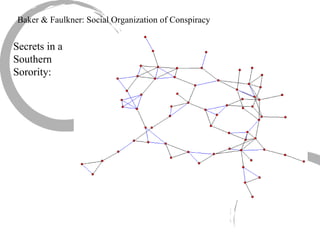
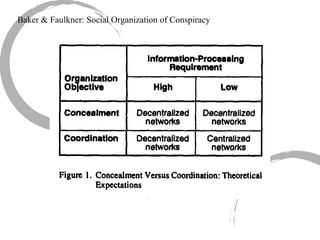
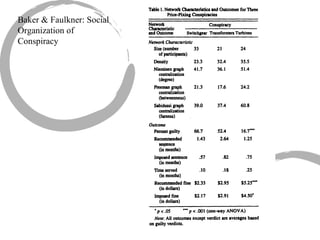
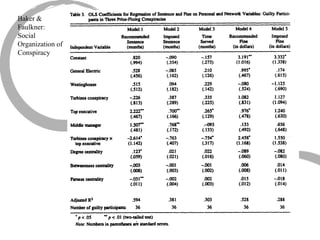
This summary provides an overview of centrality measures in social network analysis:
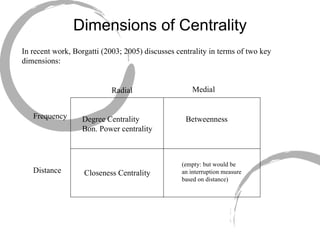
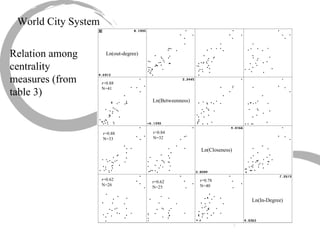
1) There are several approaches to measuring centrality in a network, including degree centrality, closeness centrality, betweenness centrality, and eigenvector centrality. These measures capture different aspects of a node's importance or influence.
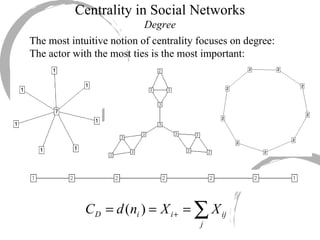
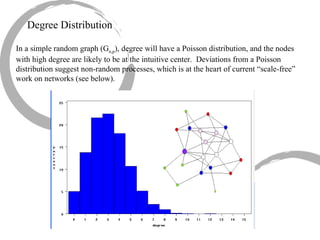
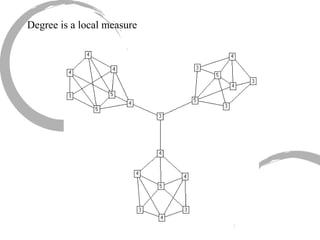
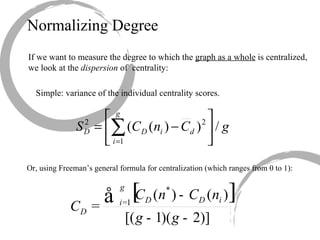
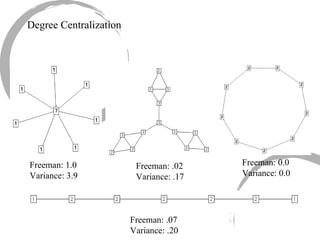
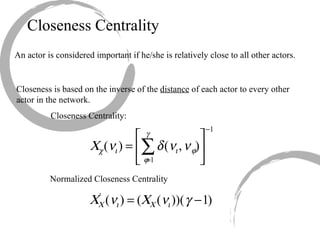
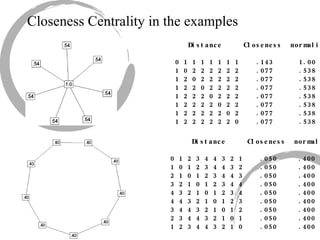
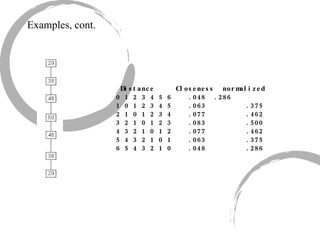
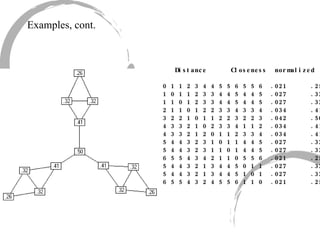
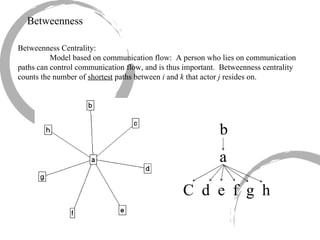
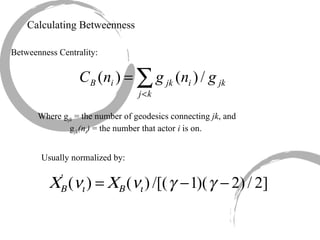
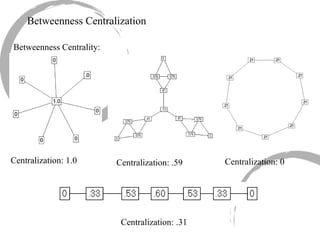
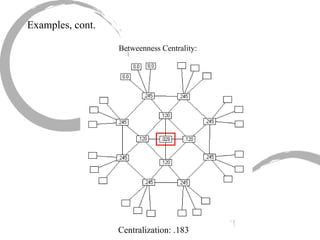
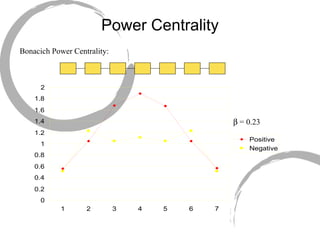
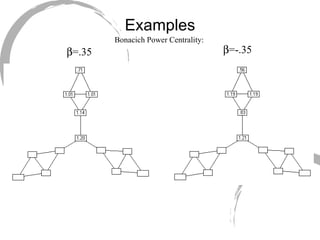
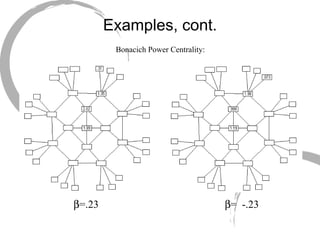
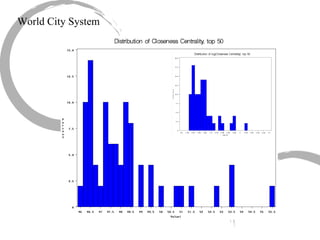
2) Degree centrality focuses on the number of ties a node has, closeness looks at distance to all other nodes, and betweenness considers dependency on shortest paths. Eigenvector centrality captures the influence of important neighbors.
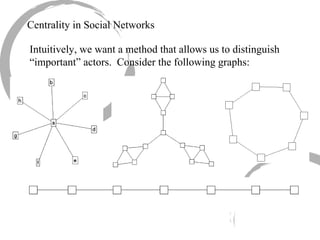
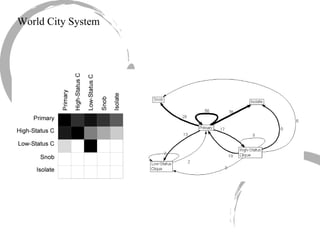
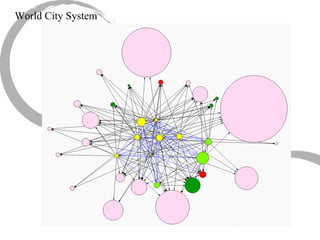
3) Comparing centrality measures can provide insight into a network's structure and a node's role, such as brokering connections vs. being well-connected locally.