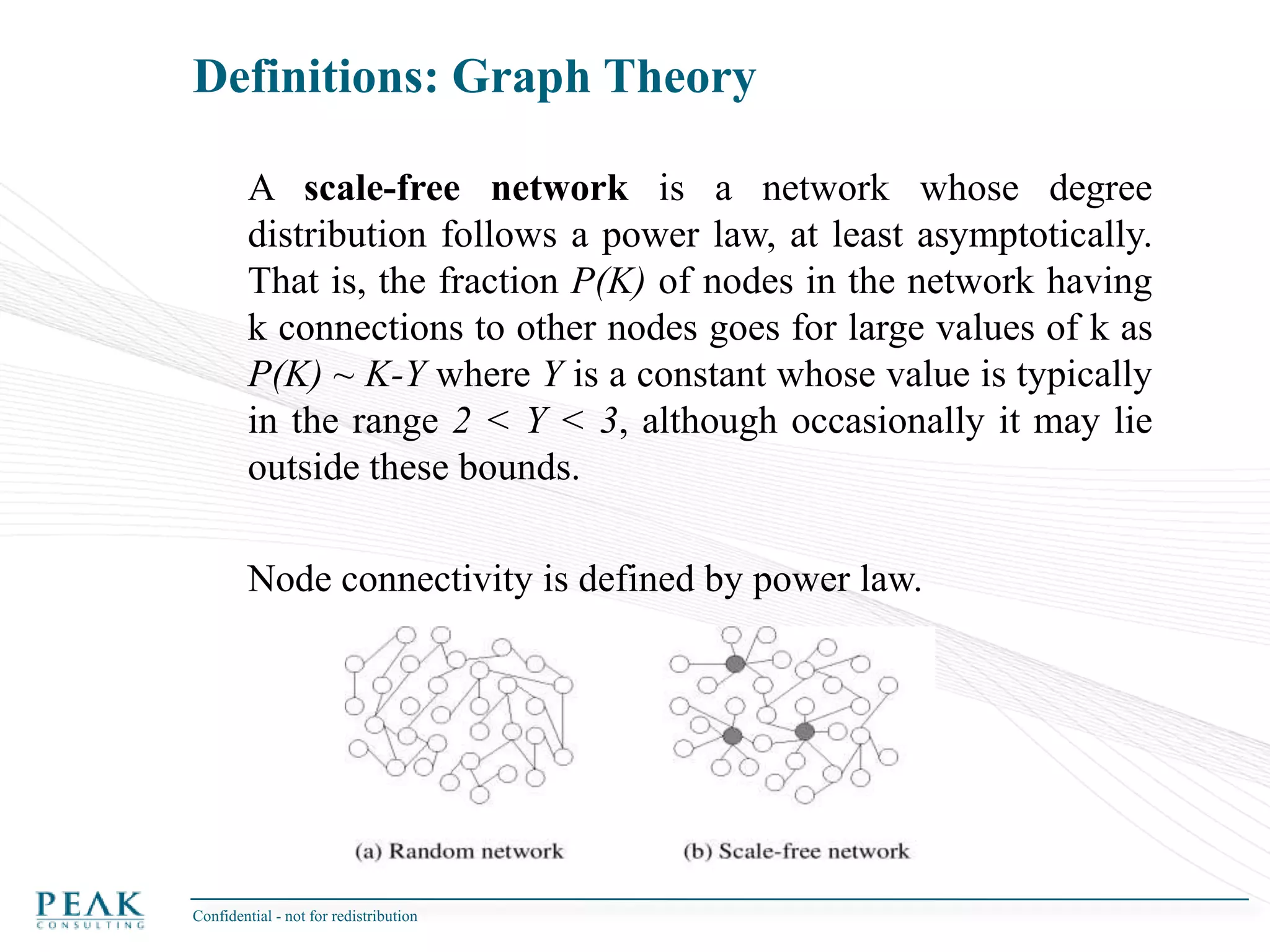
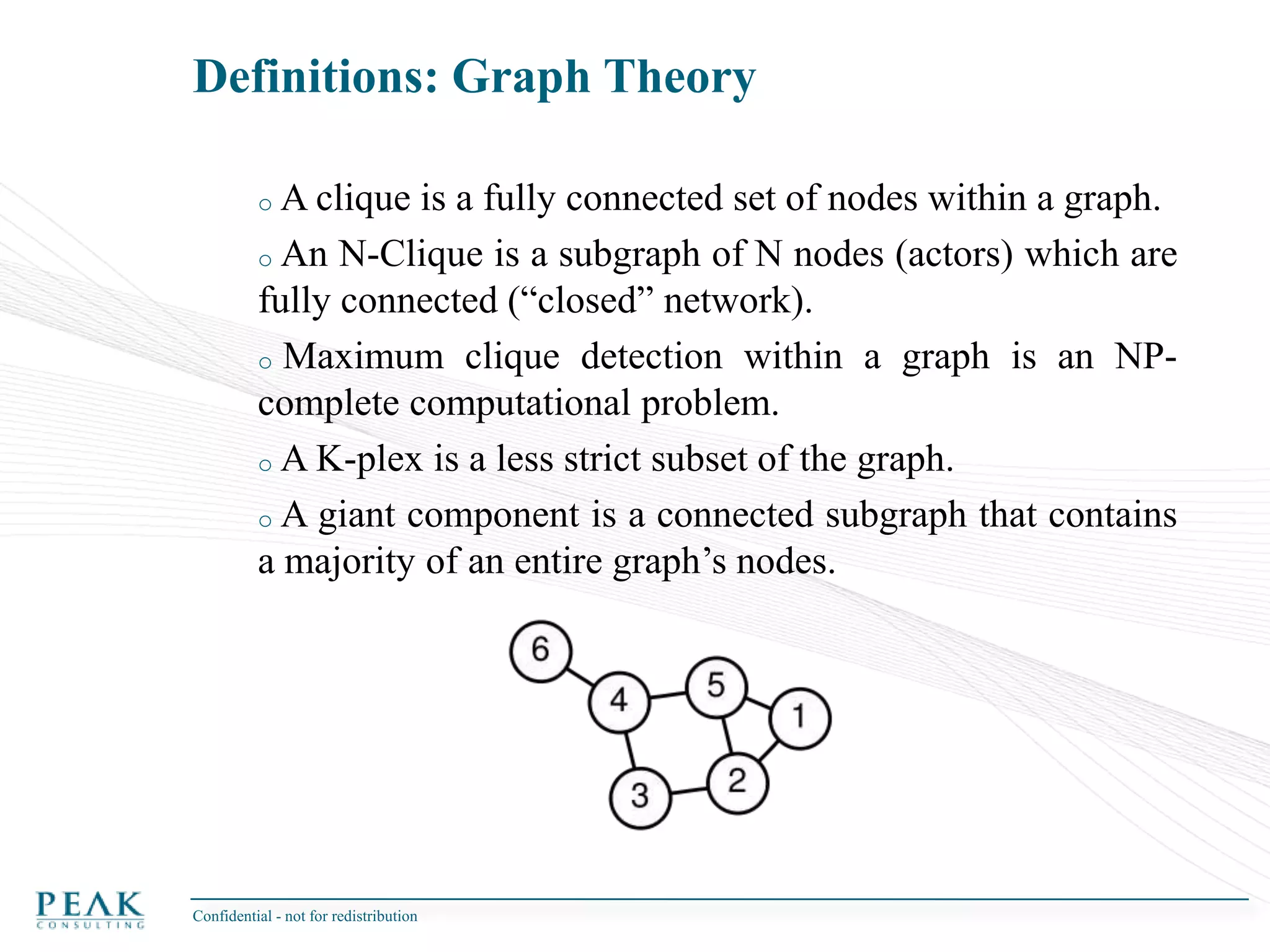
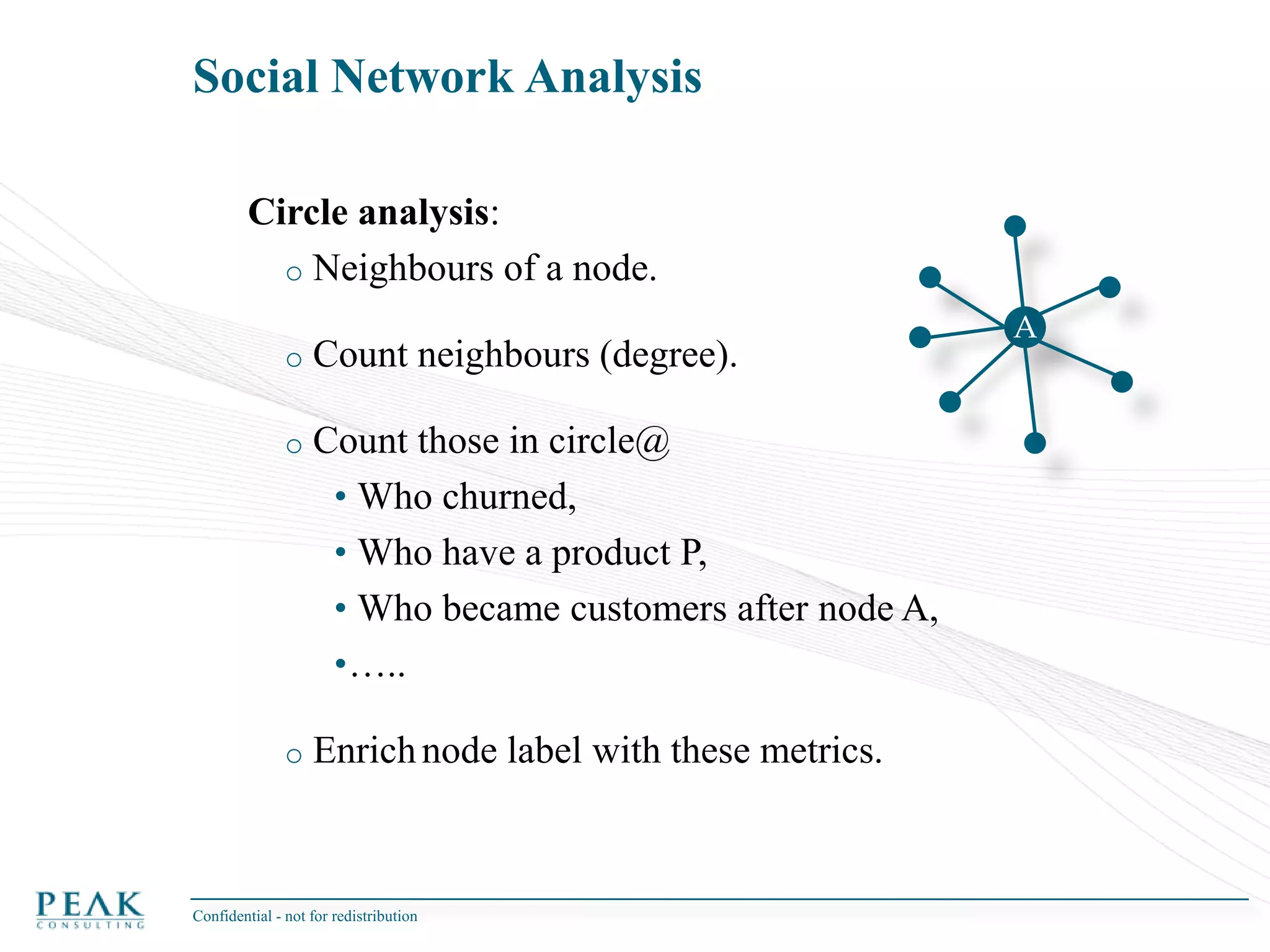
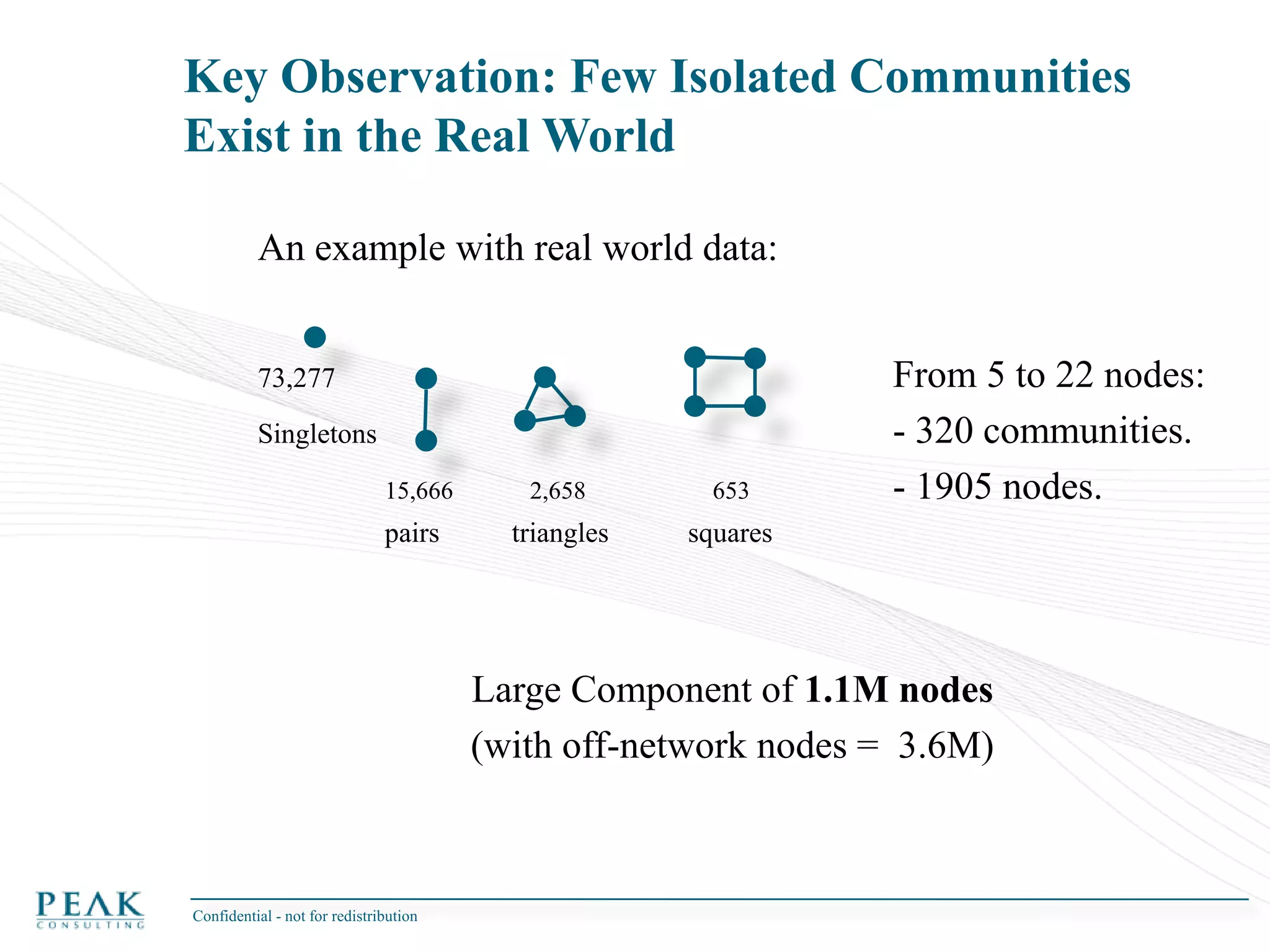
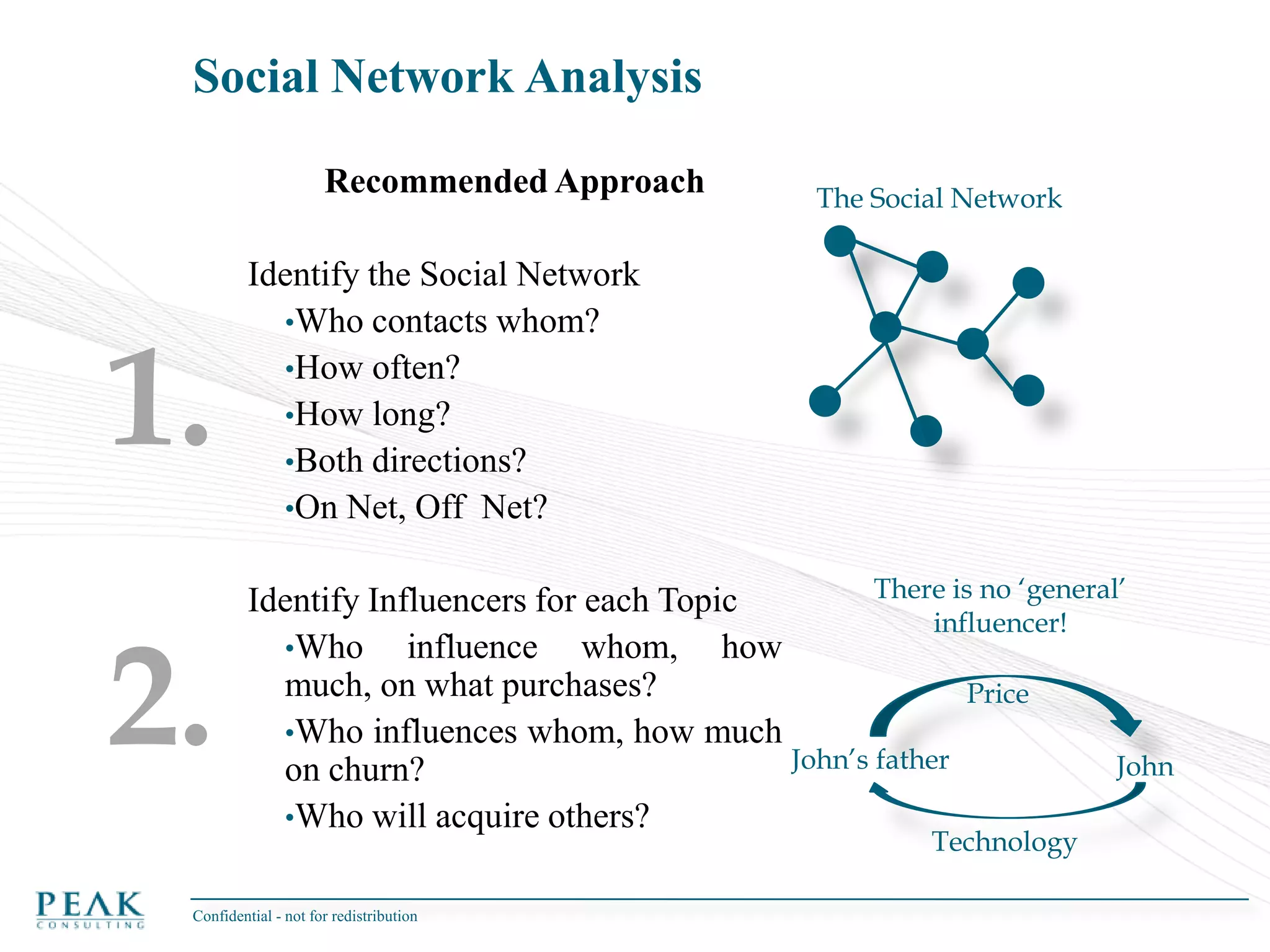
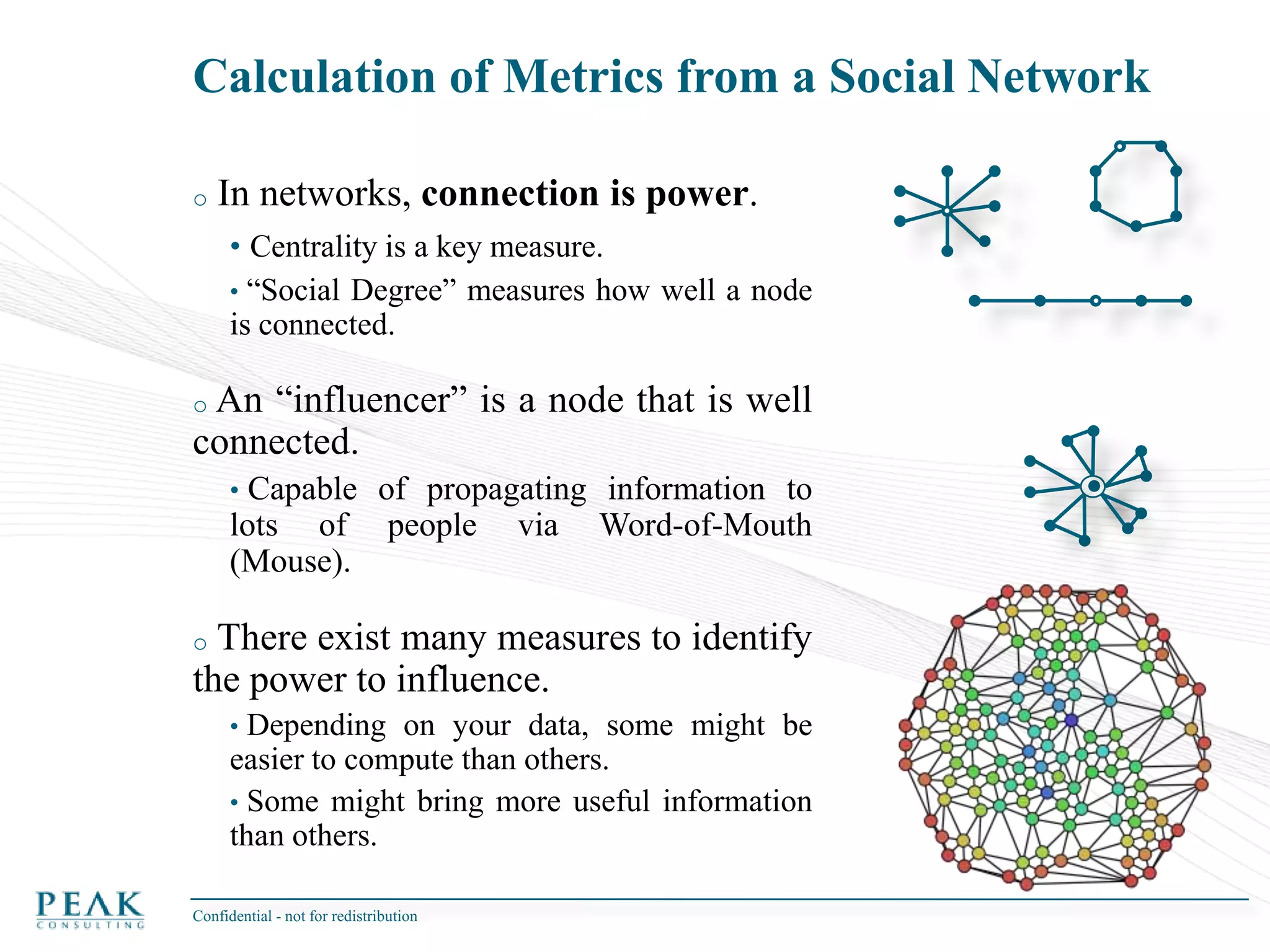
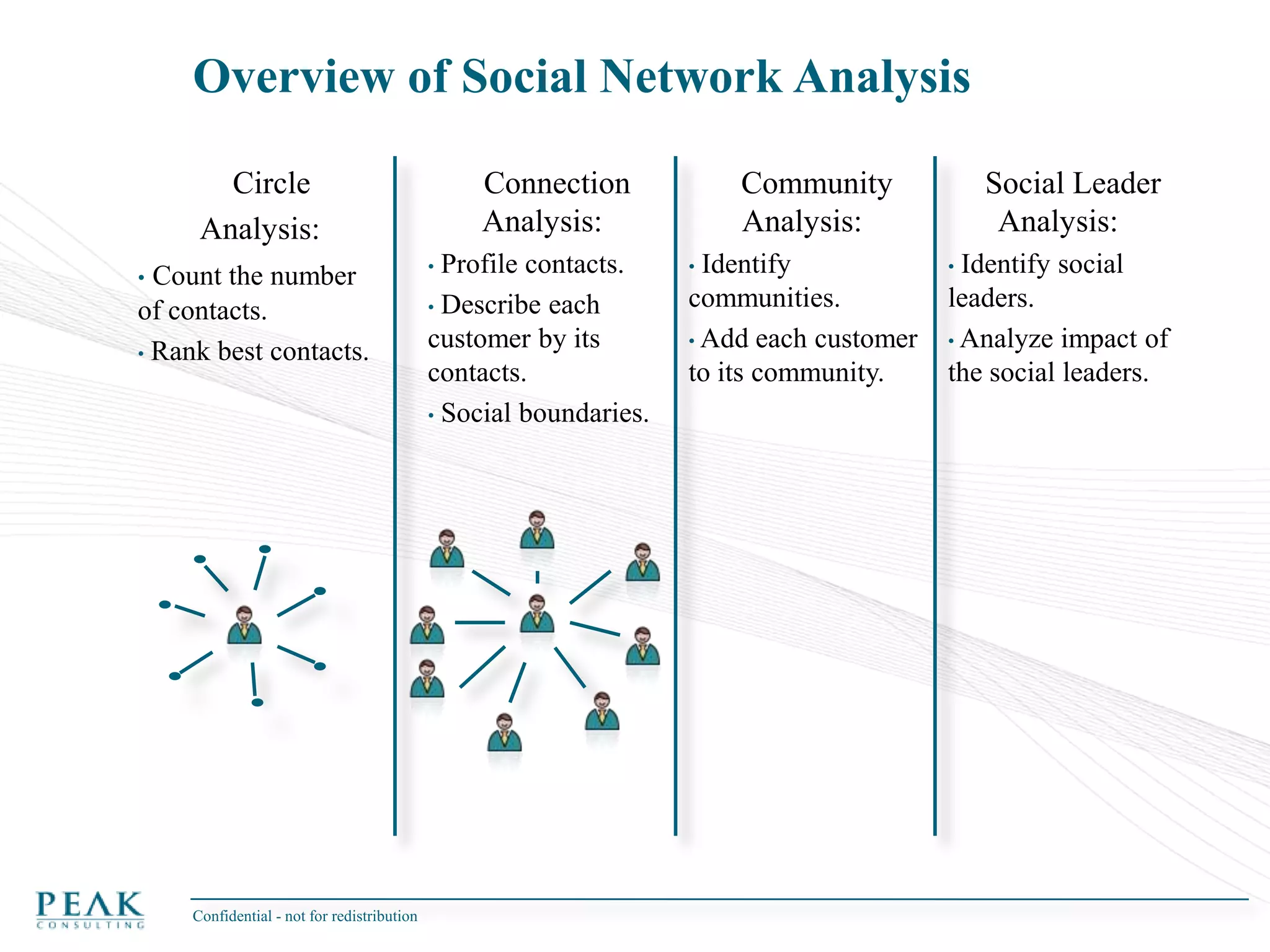
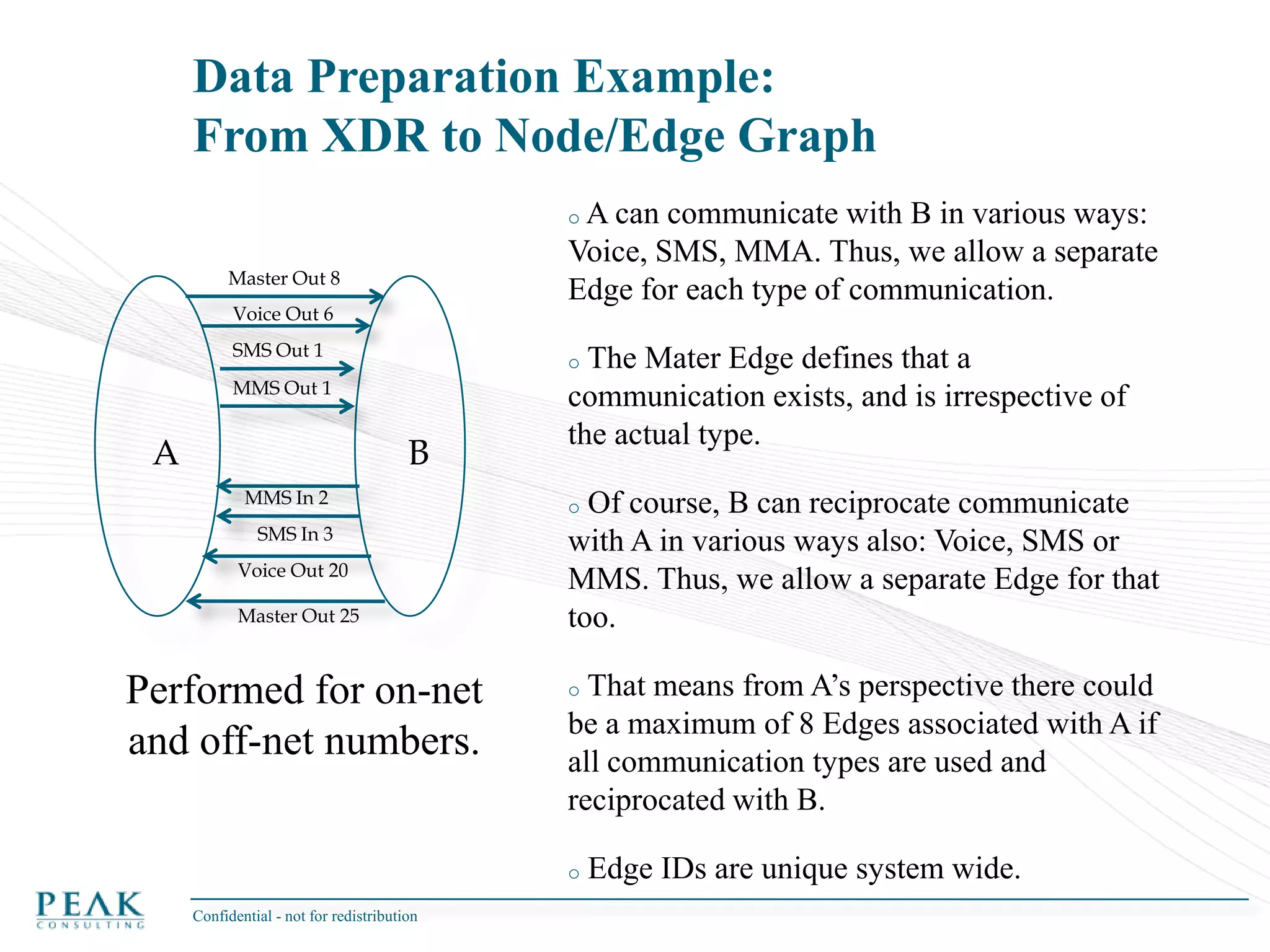
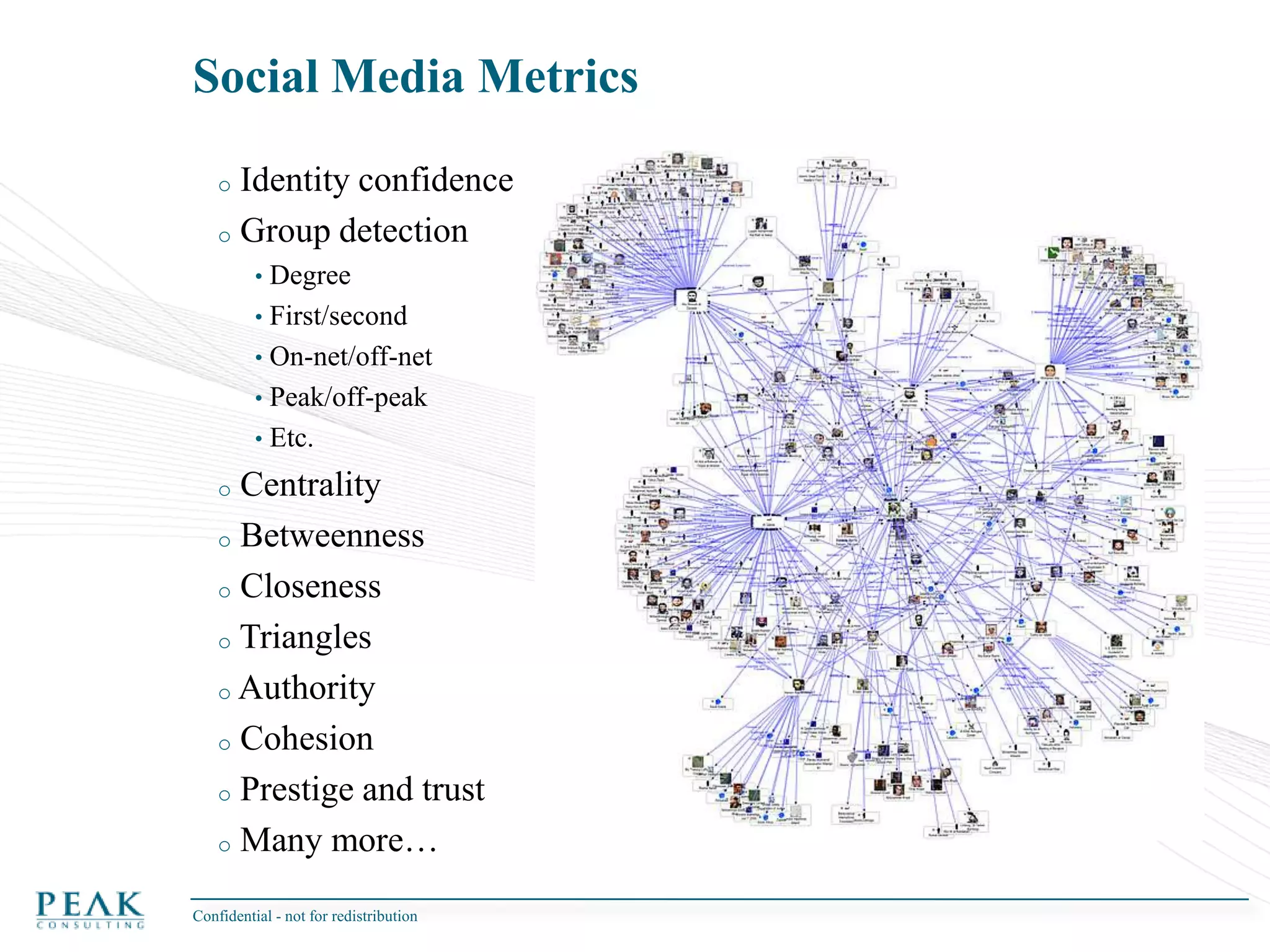
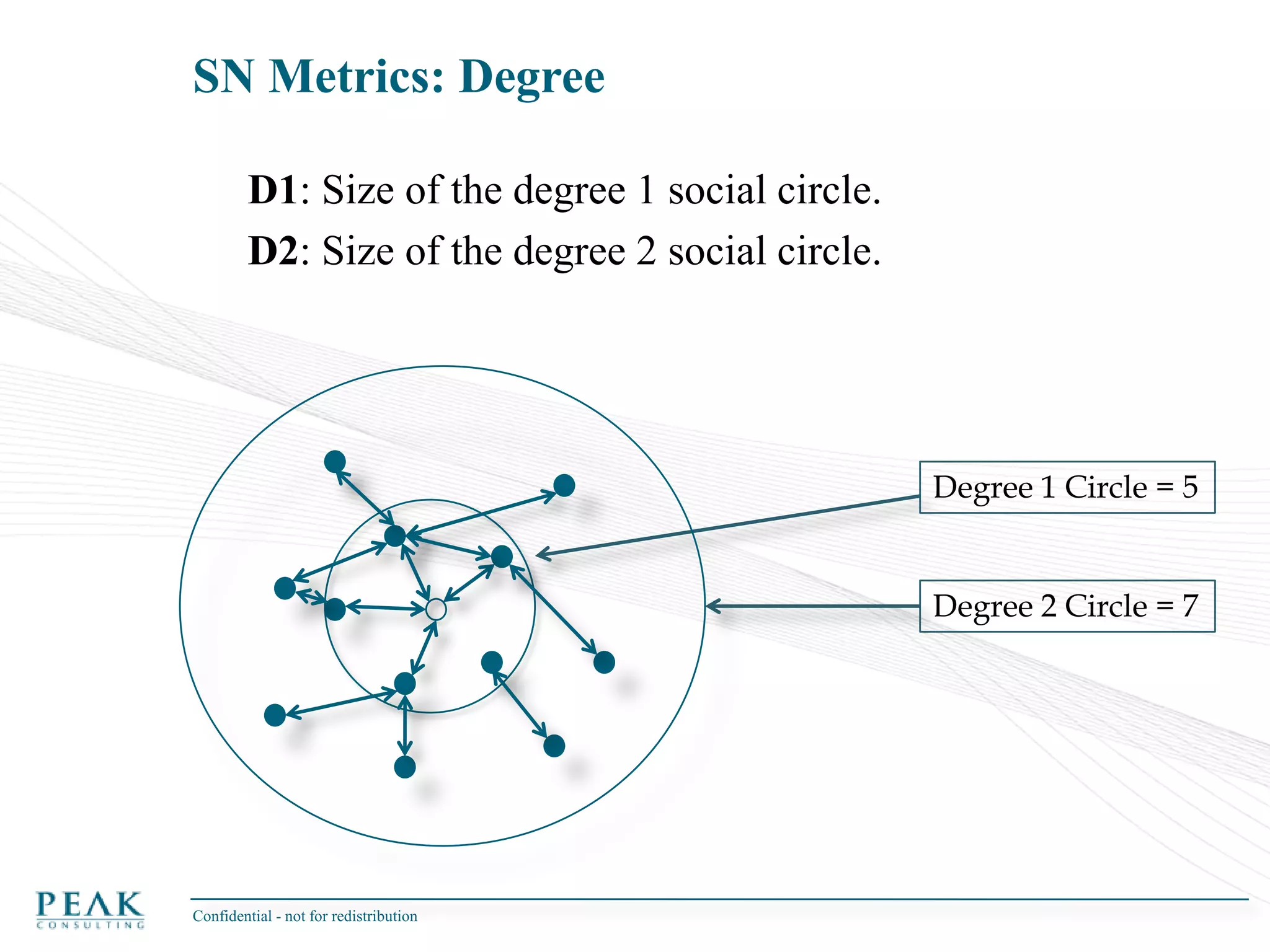
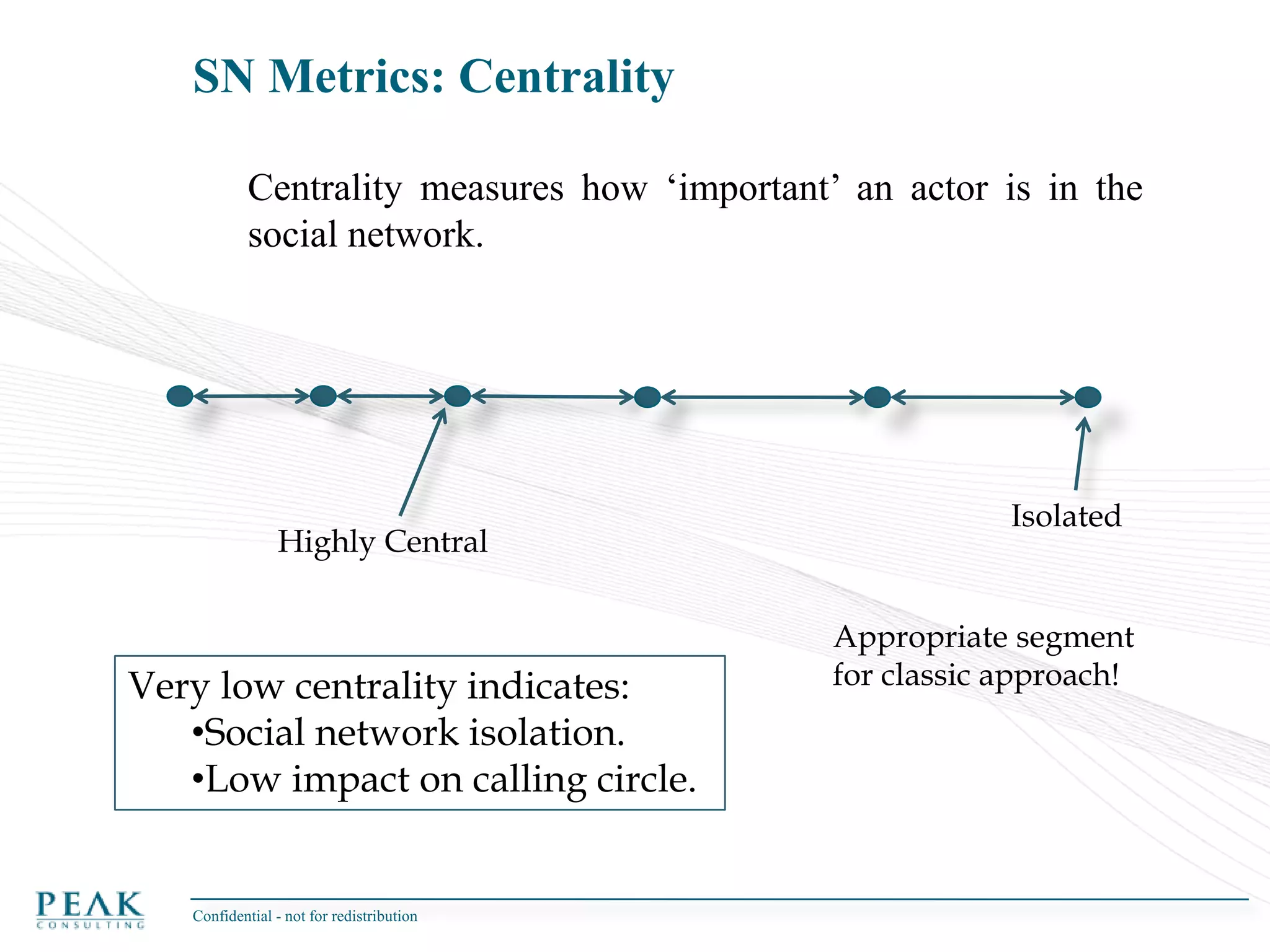
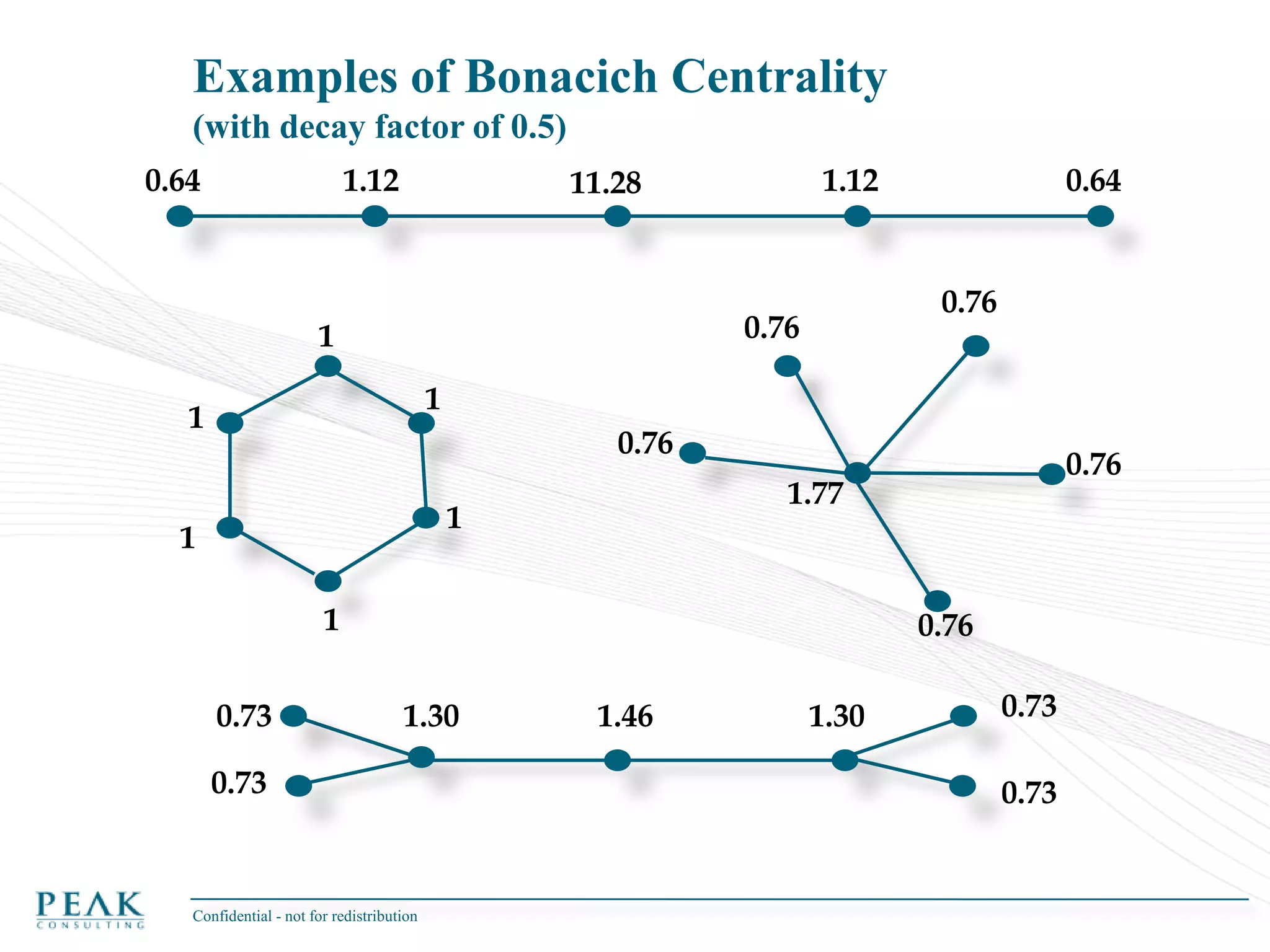
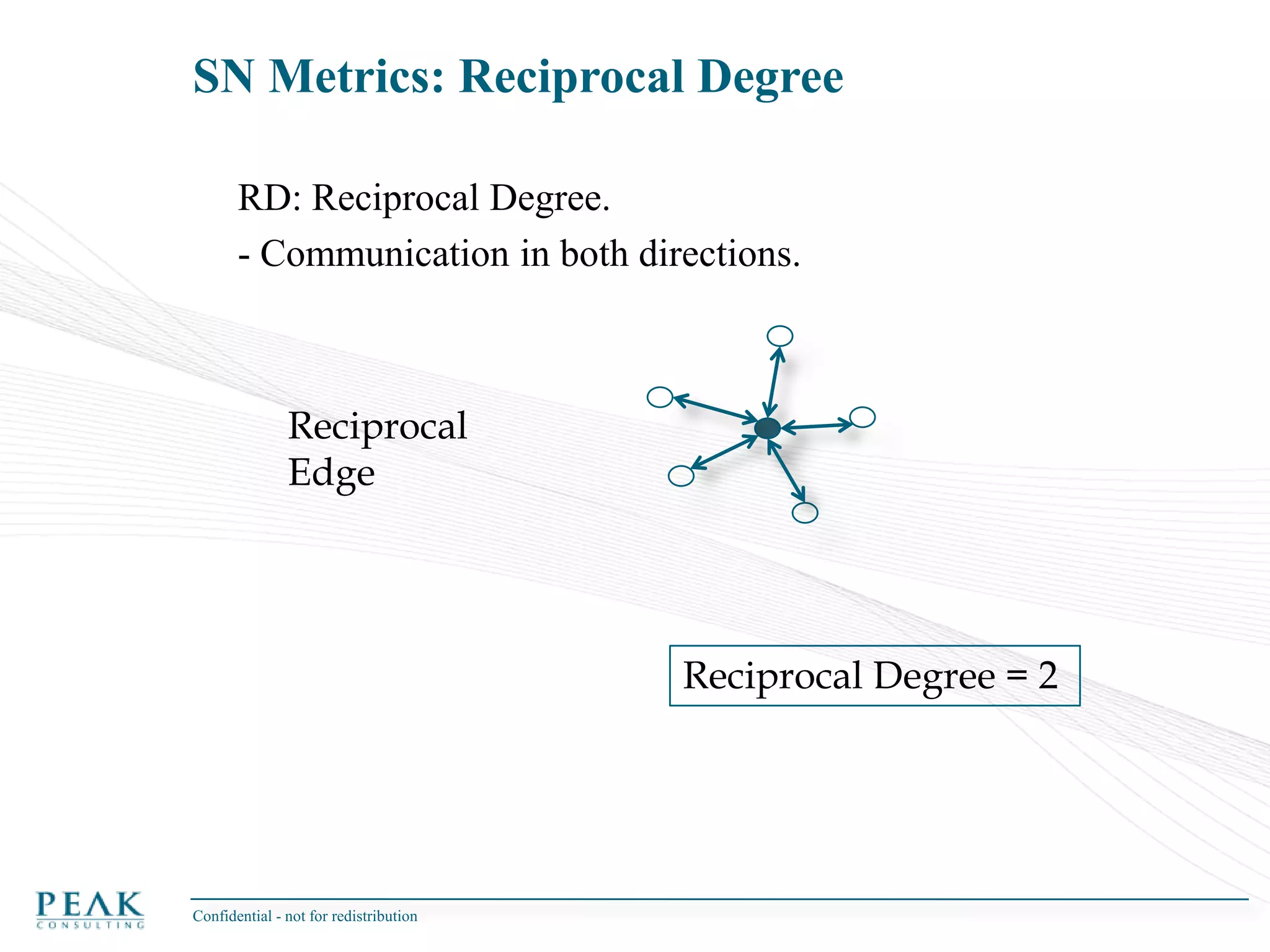
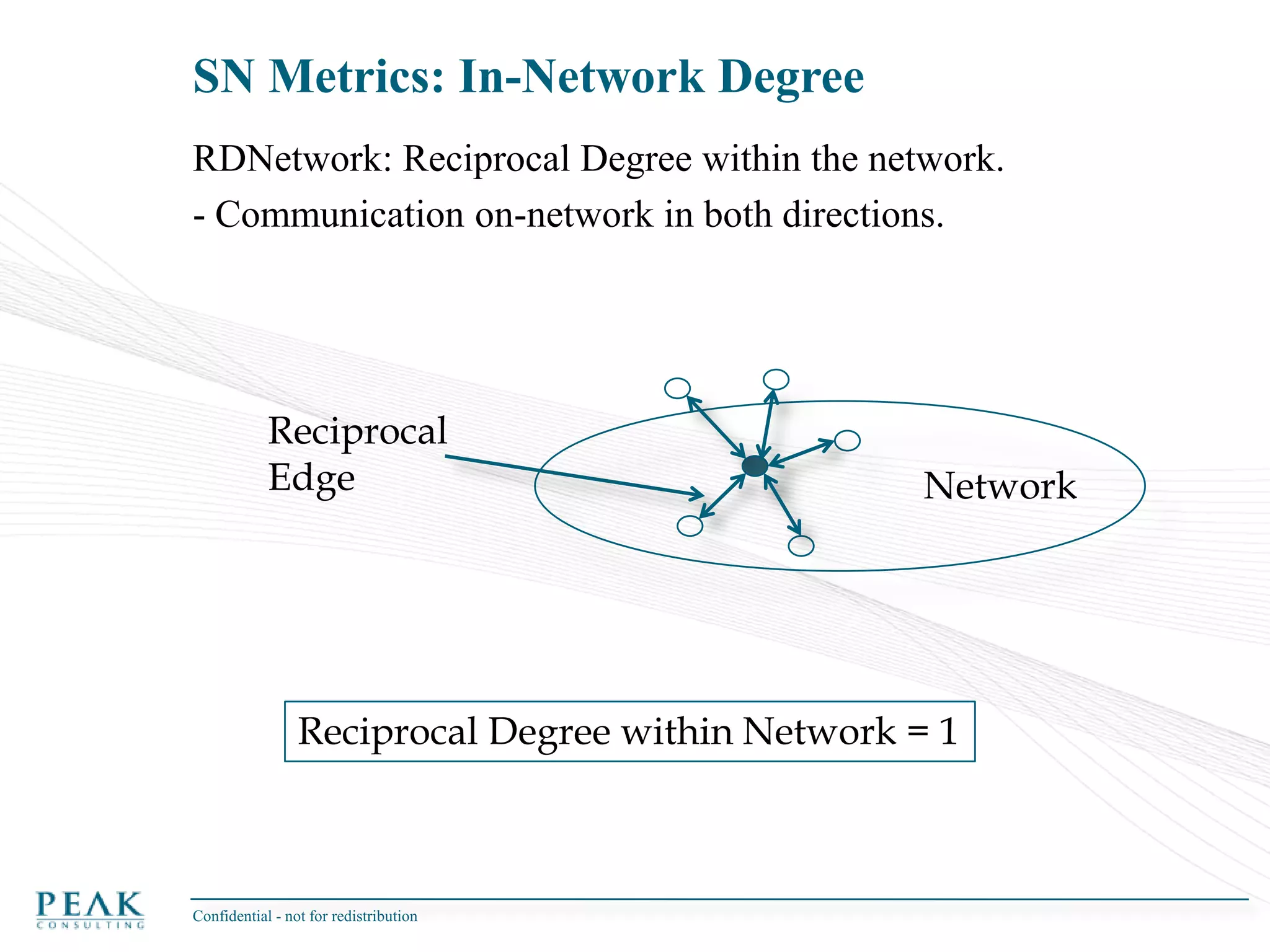
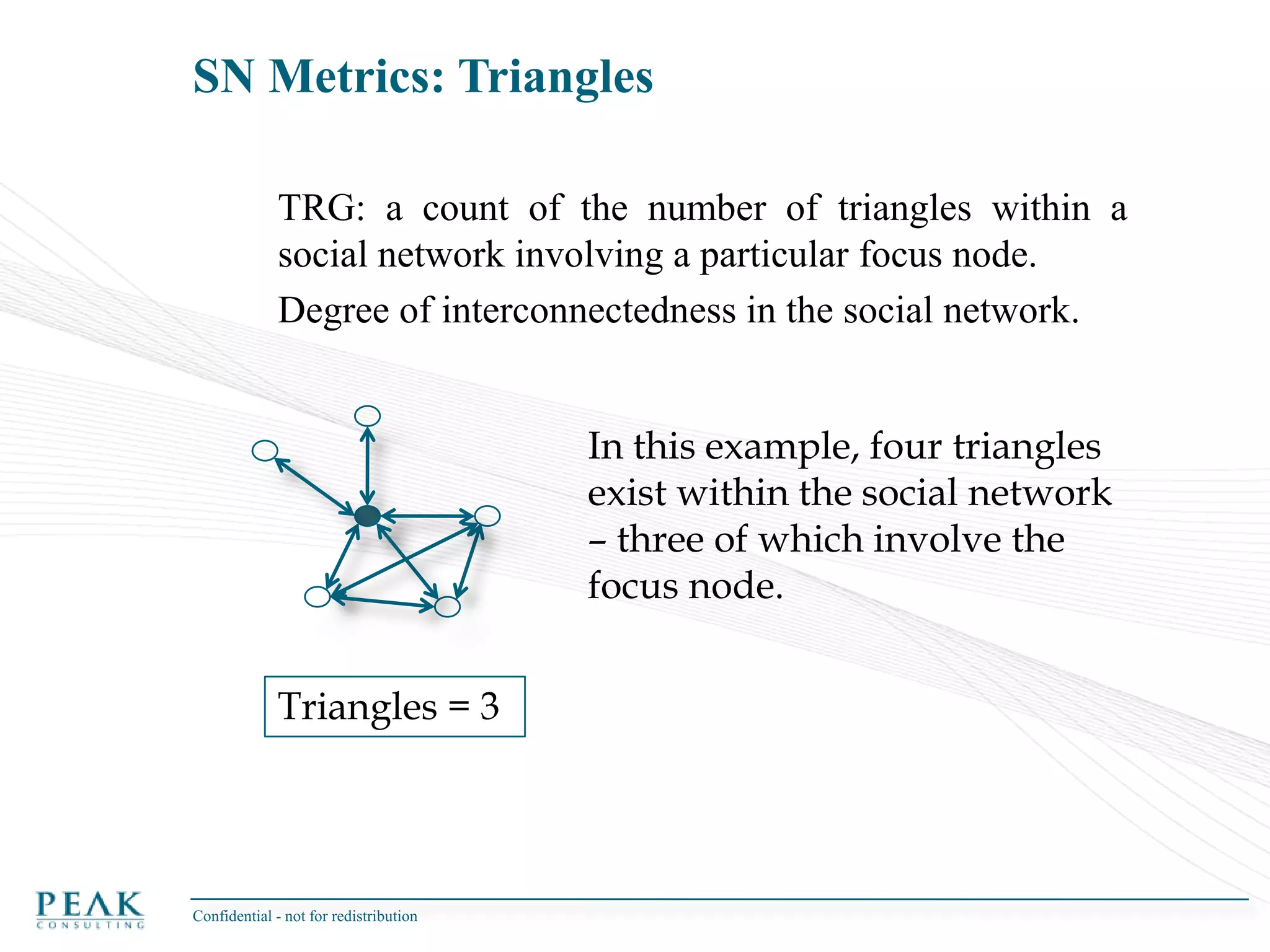
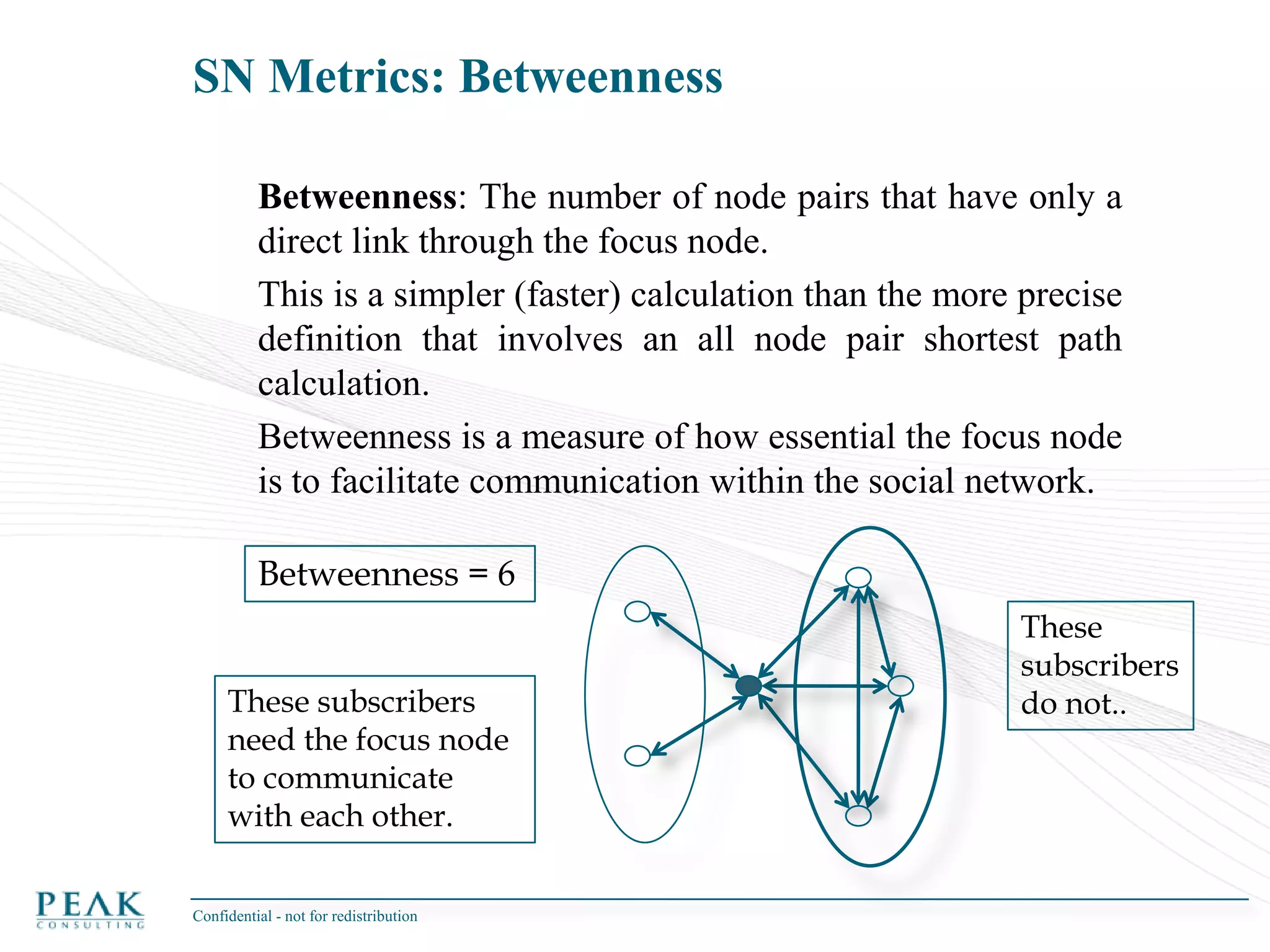
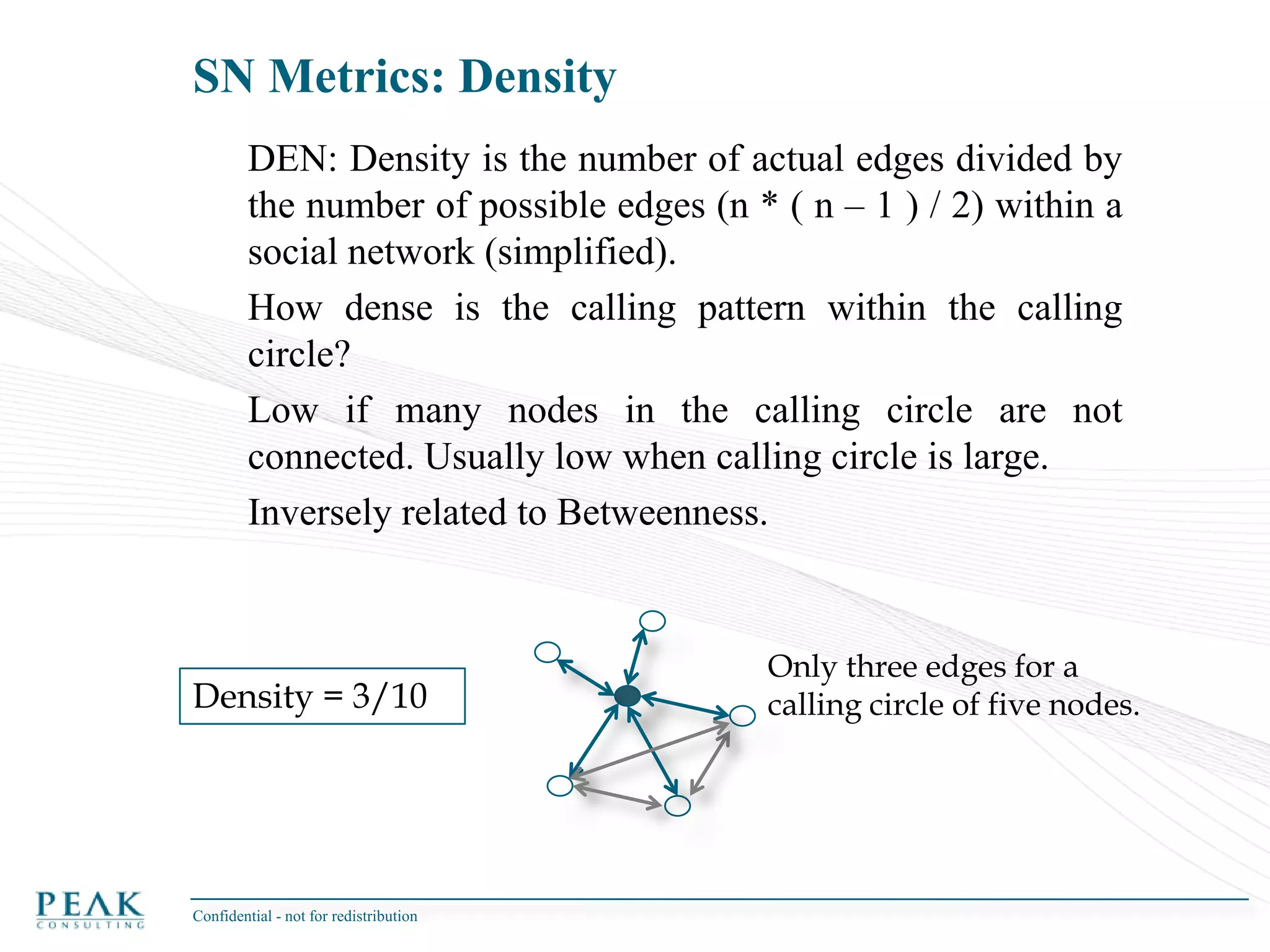
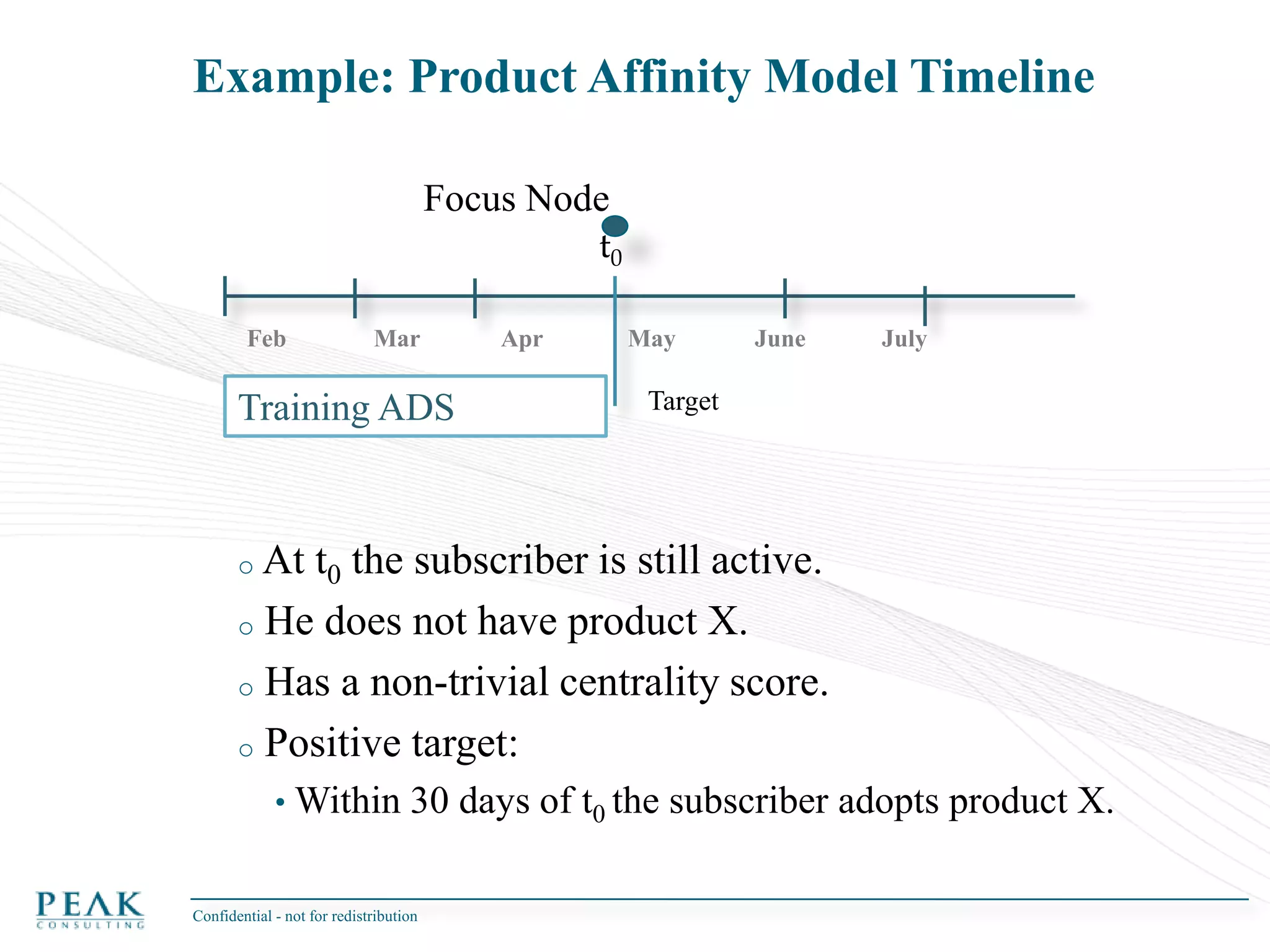
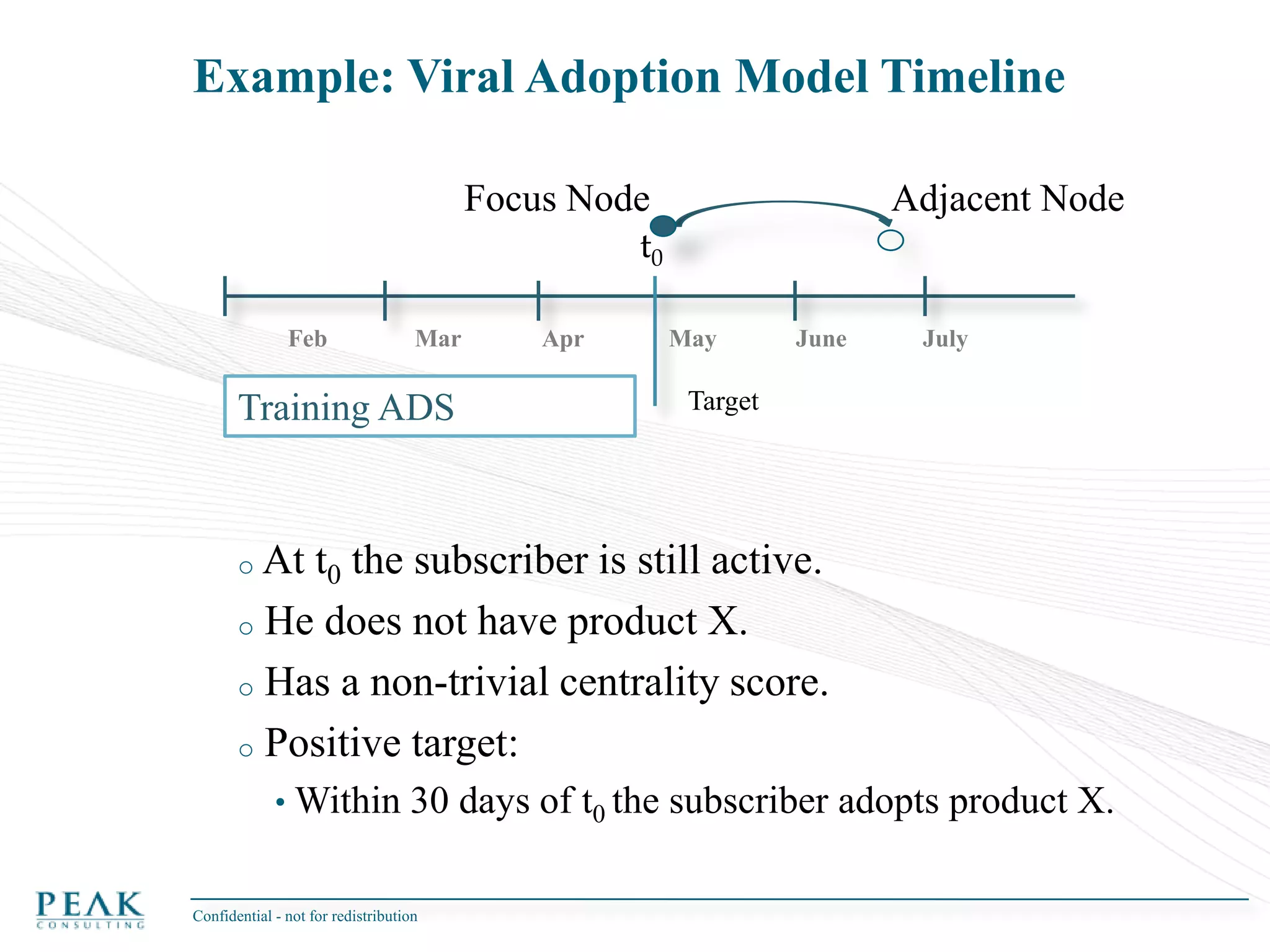
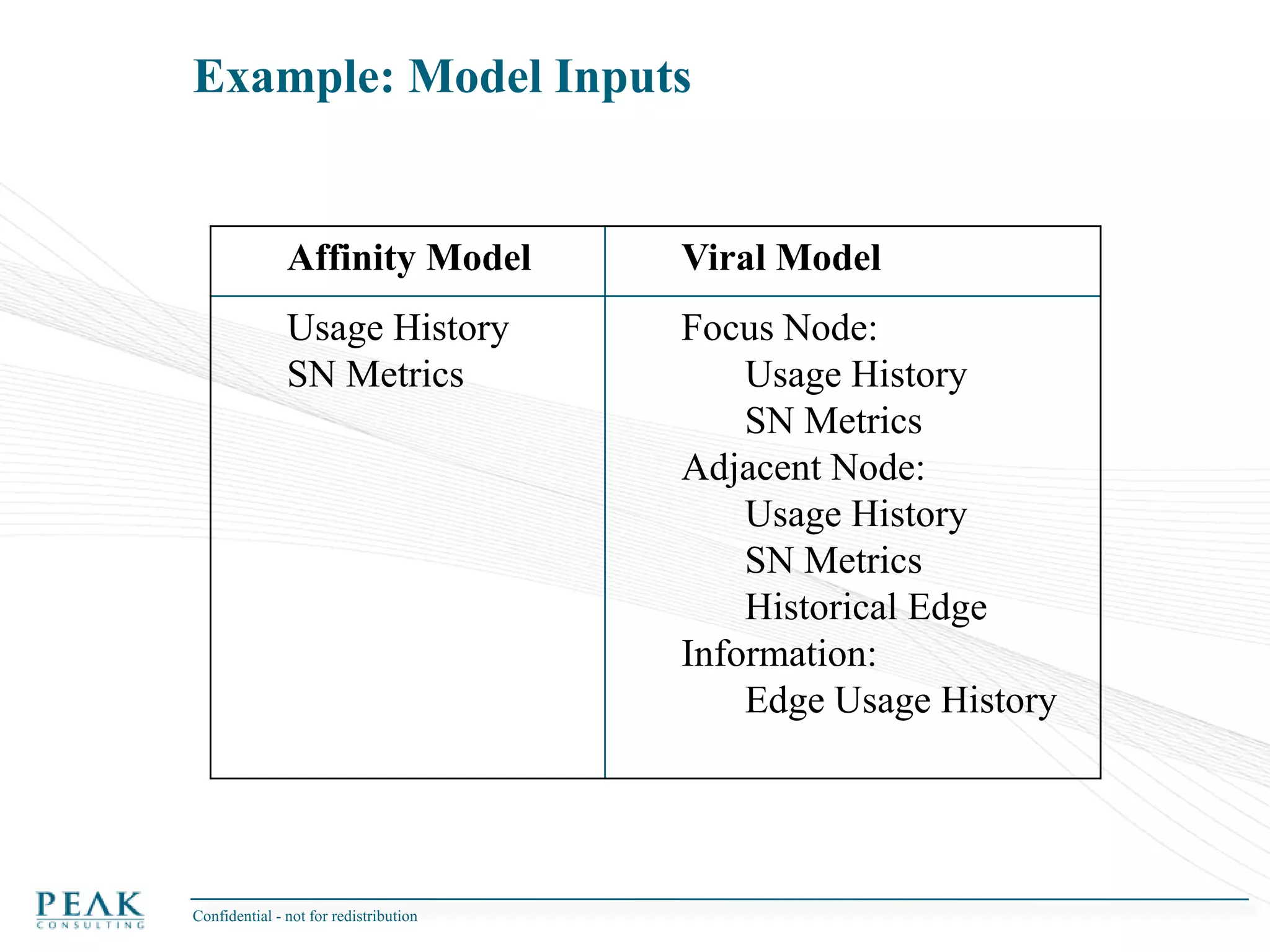
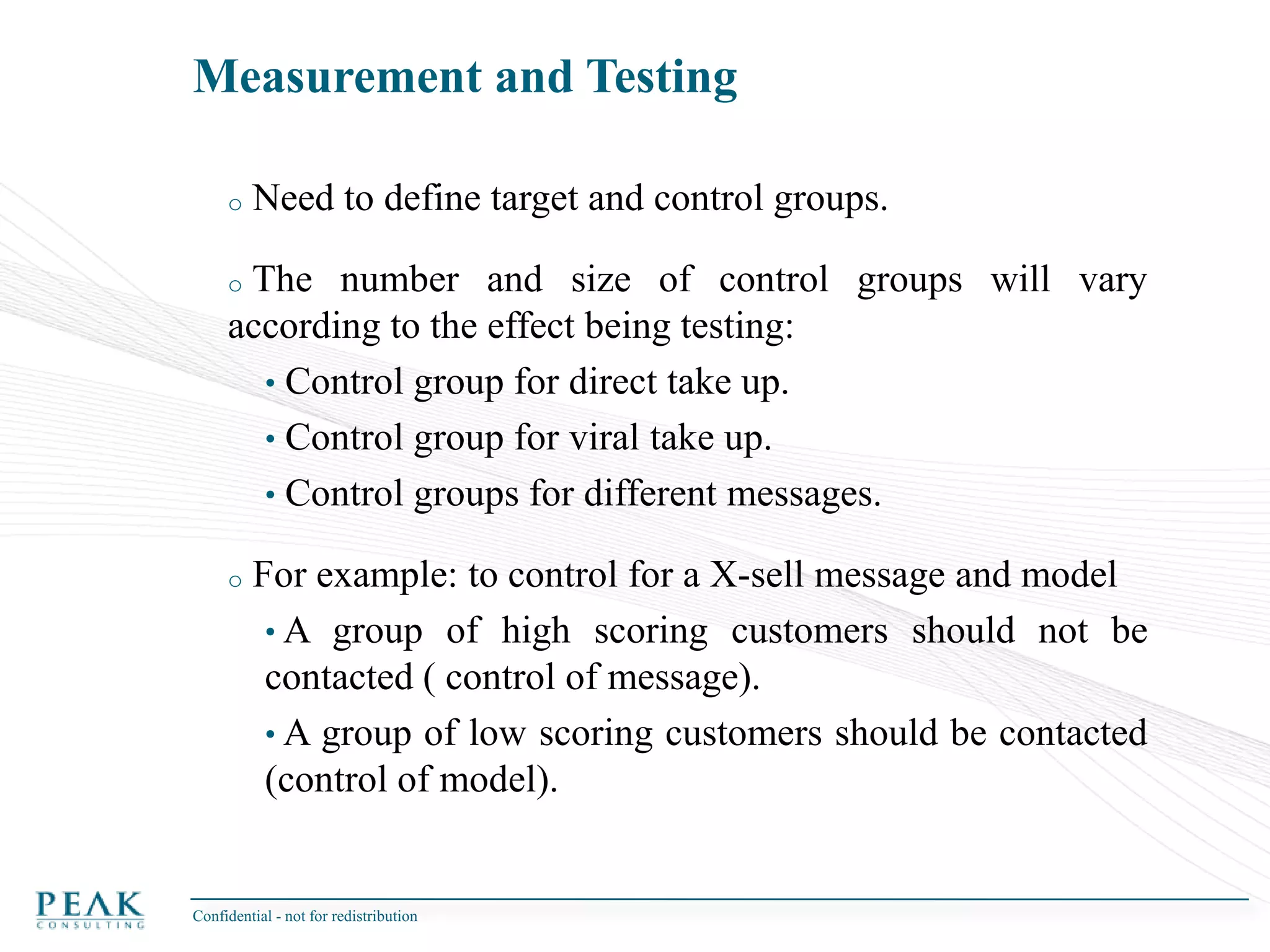
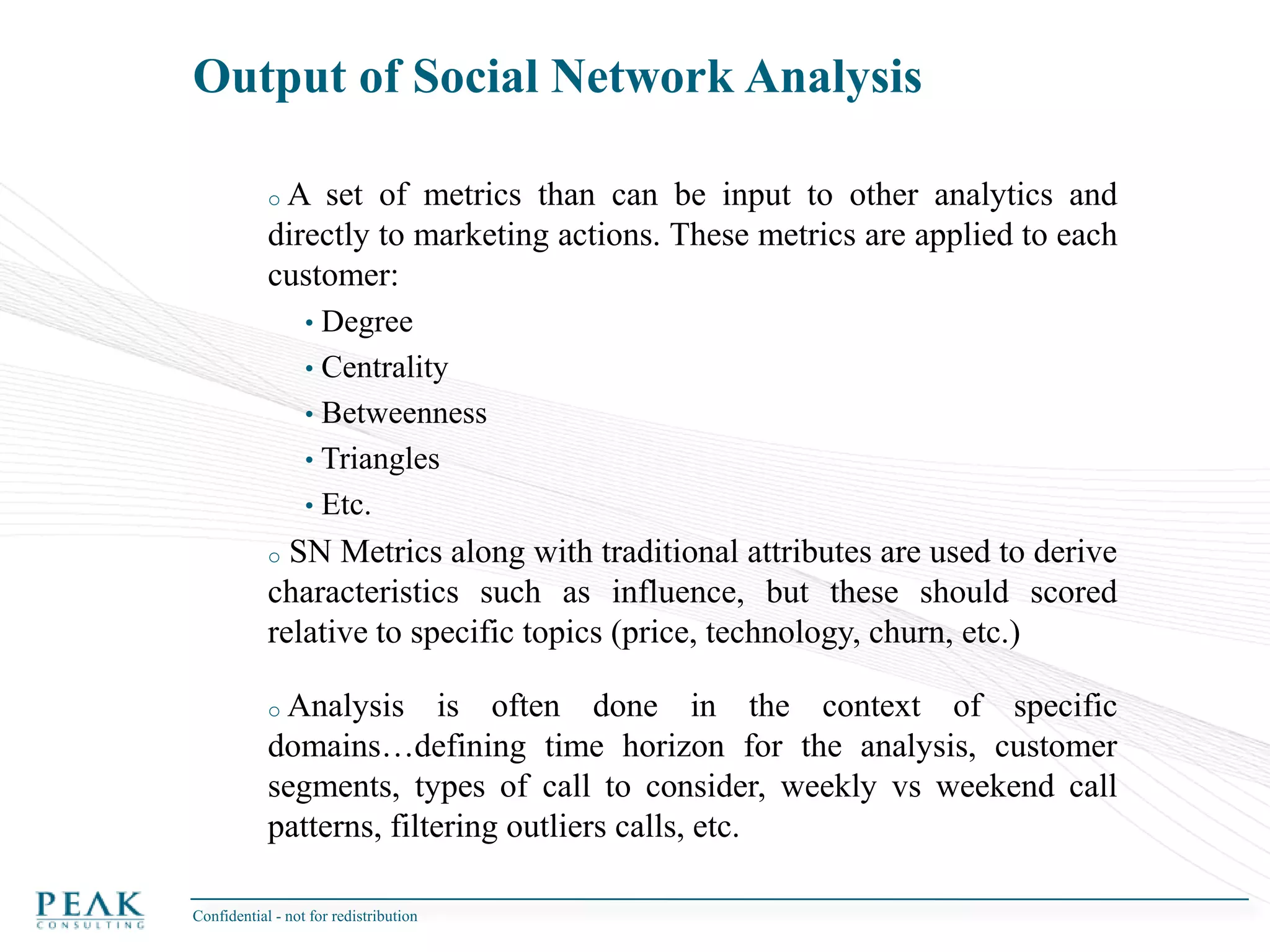
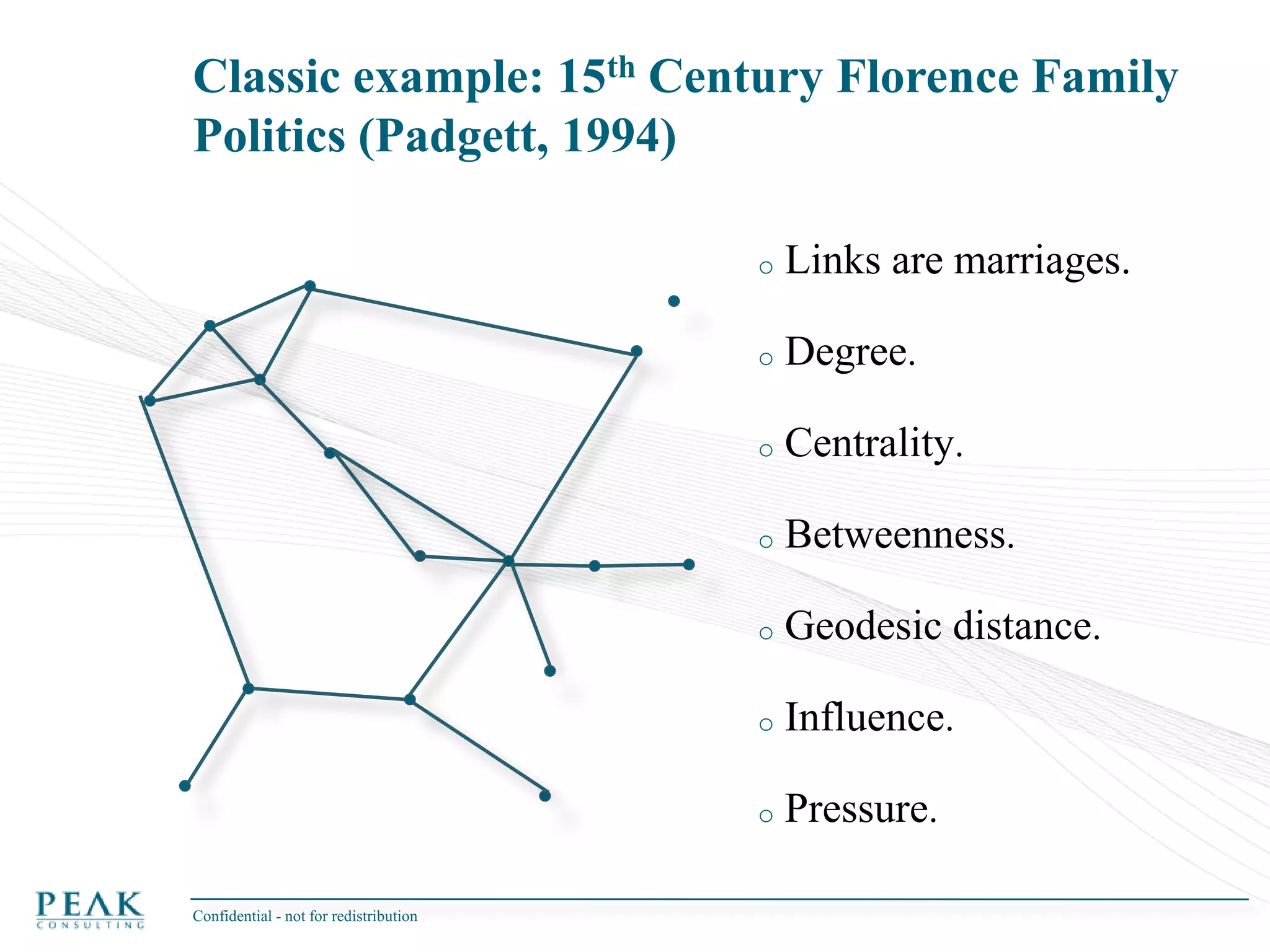
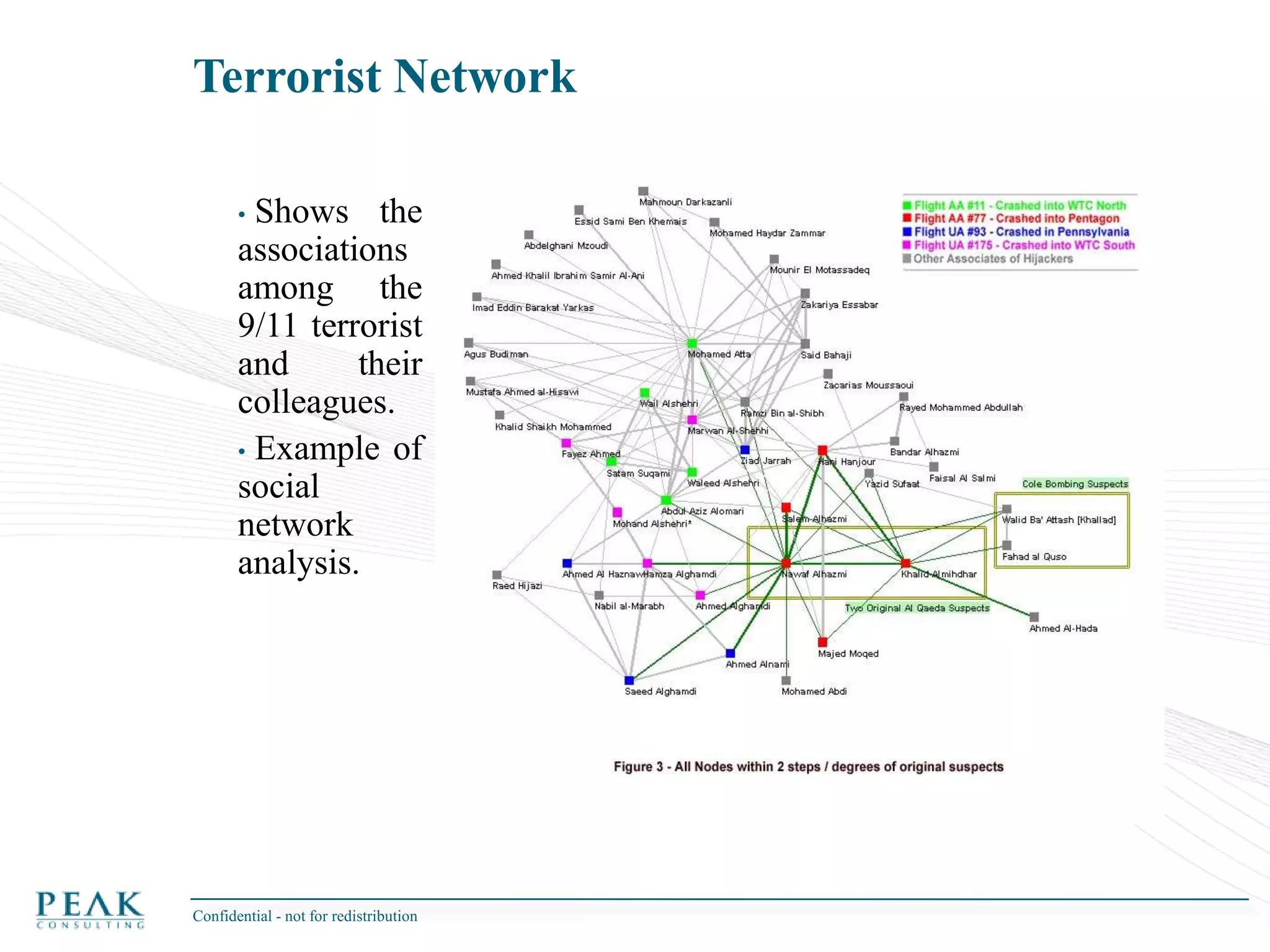
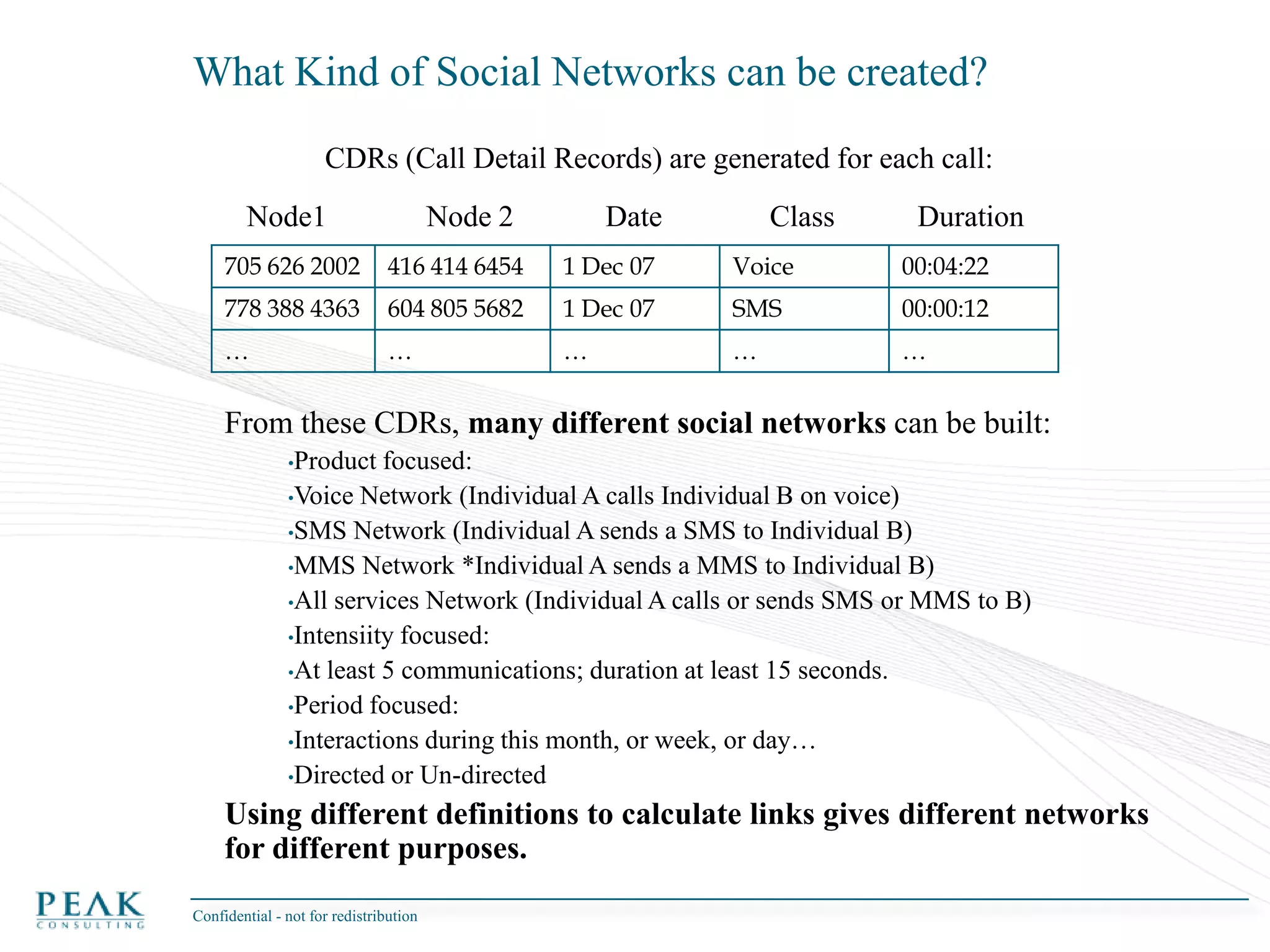
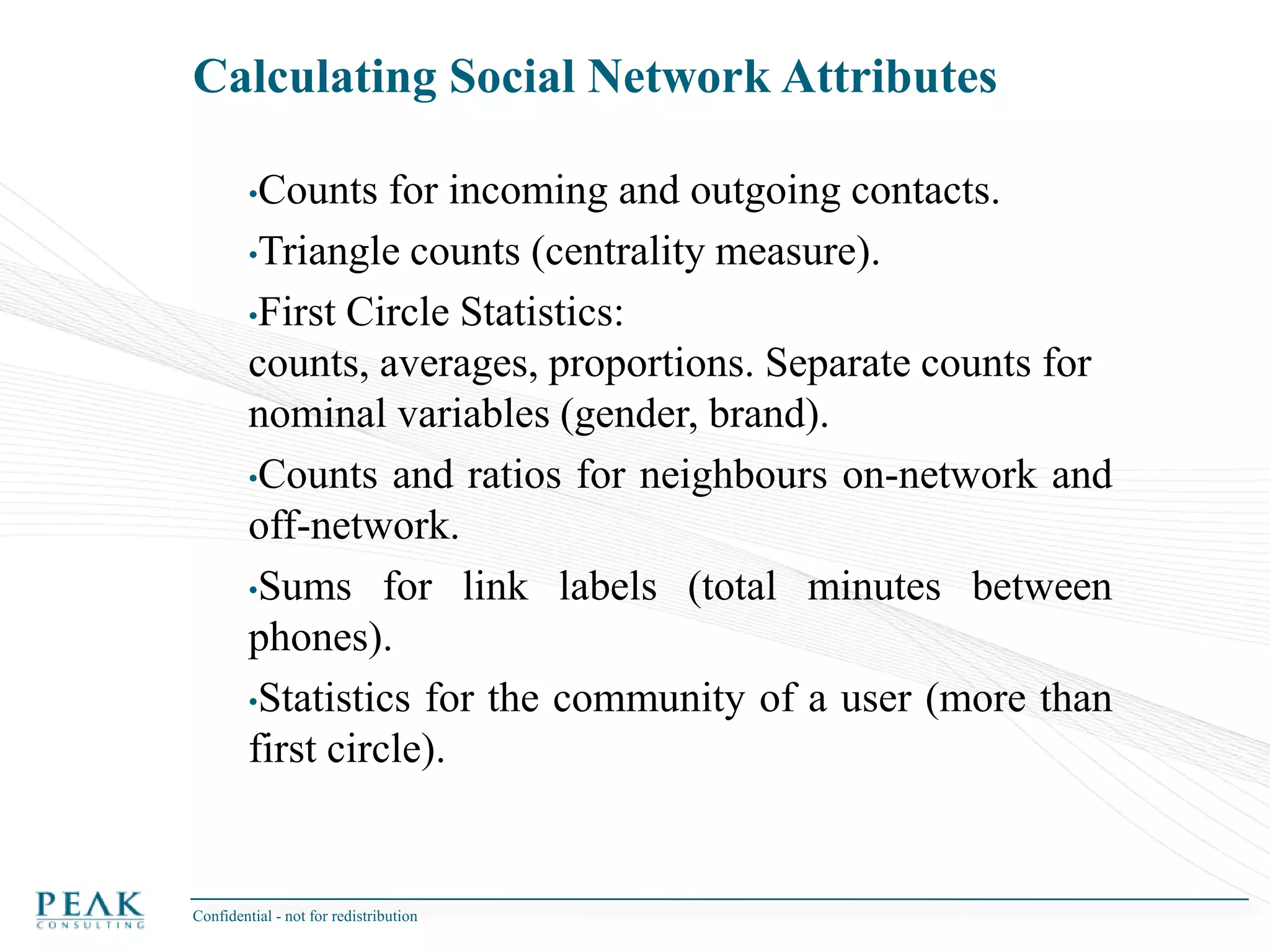
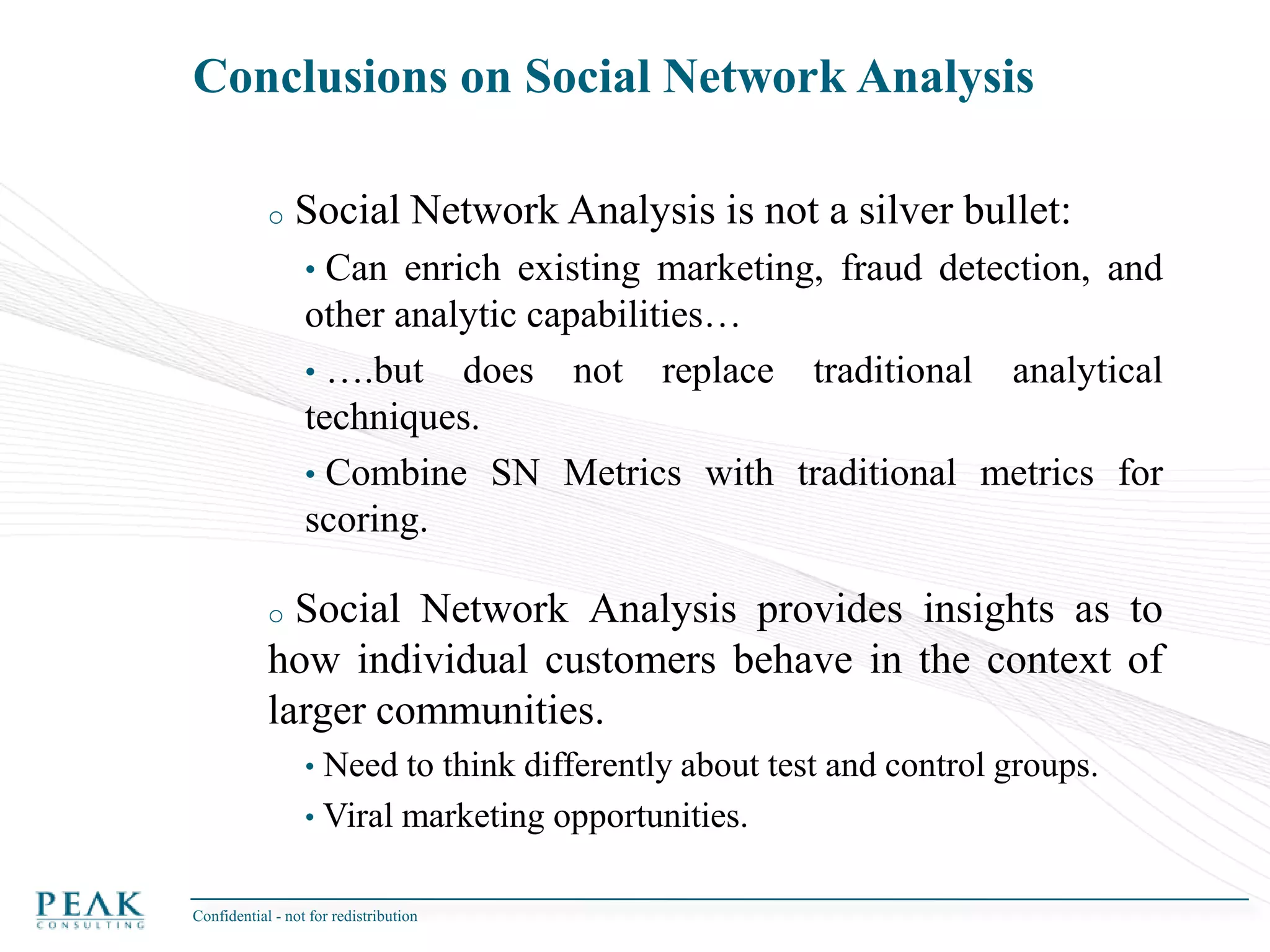
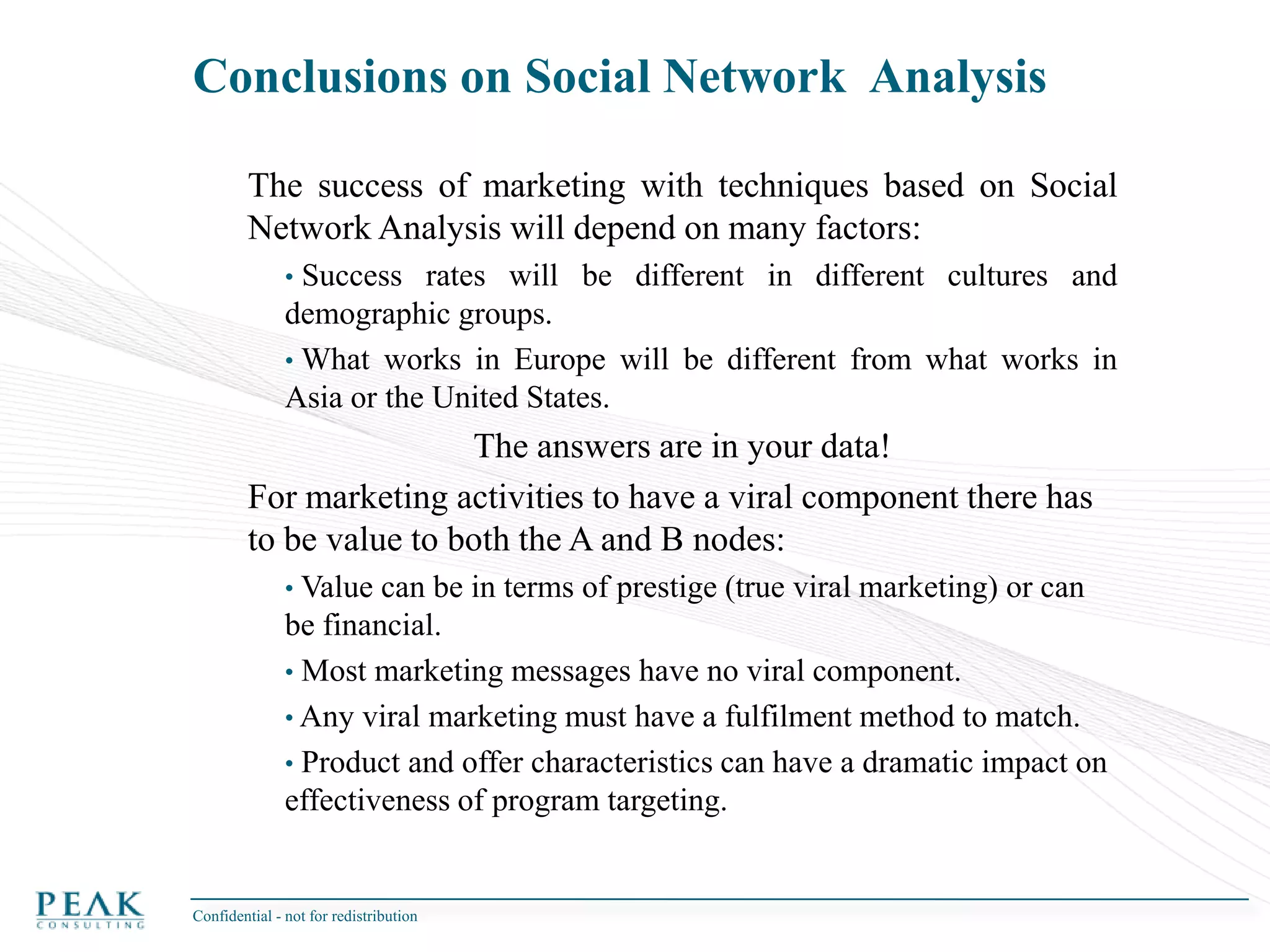
This document discusses social network analysis and its practical uses and implementation. It begins with definitions of key terms like social network and social network analysis. It then covers graph theory concepts used in social network analysis like nodes, edges, directed/undirected edges, scale-free networks, and network shapes. The document recommends approaches to social network analysis including identifying the social network, influencers, communities, and social leaders. It also discusses calculating common metrics like degree, centrality, and betweenness centrality. Finally, it provides examples of data preparation and filtering for social network analysis.