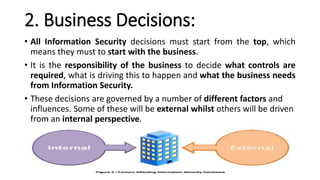
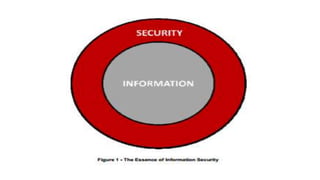
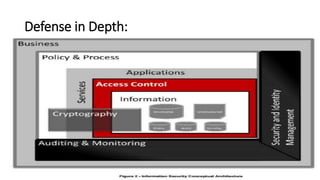
The document covers comprehensive information security policies and practices, including the history, principles, architecture, and lifecycle of information security. It emphasizes the importance of protecting organizational data through structured policies, legal regulations, and adherence to standards to prevent unauthorized access and information breaches. The lifecycle of creating and implementing security policies includes management support, policy writing, implementation, monitoring, and ensuring compliance within organizations.