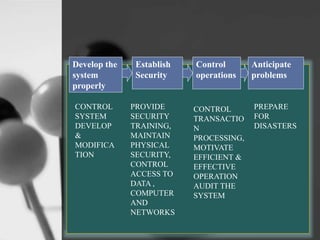
This document discusses information systems security. It begins by defining information systems and noting their importance for strategic advantage and decision making. It then discusses the risks of inadequate security management and the need to ensure integrity and safety of systems. The document goes on to explain basic principles of information security like confidentiality, integrity, availability, and others. It also discusses threats like computer crimes, accidents, vulnerabilities and methods to minimize risks like developing systems correctly, user training, physical security controls, and auditing.