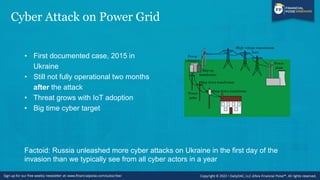
This webinar aims to guide businesses on building and implementing effective information security programs to protect valuable data from unauthorized access. It discusses the importance of cybersecurity in the current environment, compliance with various regulations, and key elements of a security program such as risk management and employee training. The series includes informative episodes designed for professionals across legal, financial, and business sectors, emphasizing practical, engaging insights into data privacy and cybersecurity.