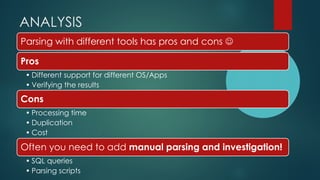
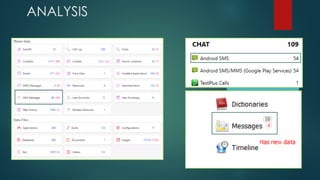
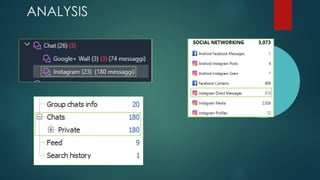
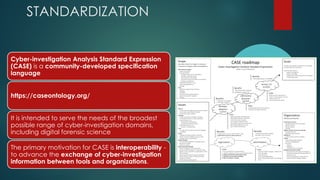
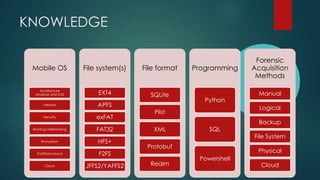
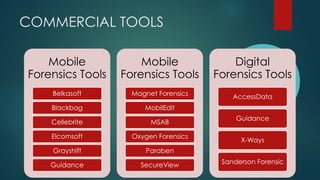
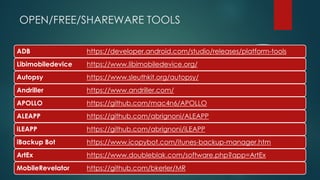
This document provides guidance on building your own mobile forensics methodology (BYOM). It discusses the needs, knowledge, tools, and suggested readings required for mobile forensics. The document outlines knowledge required about mobile operating systems, file systems, file formats, and programming. It also lists commercial, open-source, and hardware tools that can be used and provides information on training resources, best practices, workflows, and standardization in mobile forensics. The goal is to help practitioners develop their own customized mobile forensics methodology.















![PREPARATION
DEFINE THE EXTRACTION METHOD
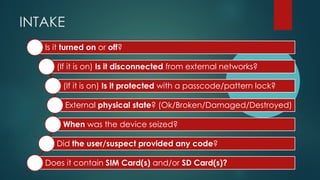
Check your «Case History» [NEXT SLIDE]
Check what was requested during the intake
•If you need just only a specific SMS/Picture/WhatsApp chat, do you really need to acquire everything?
Check support by your Mobile Forensics Toolkit(s)
Ask the community
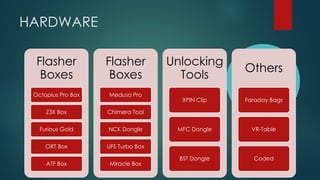
Check for custom recoveries/engineering bootloader/flasher boxes
Verify support by specific external services
Identify specific vulnerabilities
A physical approach is feasible?
Think outside the box…
•Cloud
•Local backup
•Provider requests
•Connected/synced devices (Smartwatch, Smart TV, Home Assistants, …)](https://image.slidesharecdn.com/byomforensic-220104160806/85/BYOM-Build-Your-Own-Methodology-in-Mobile-Forensics-22-320.jpg)