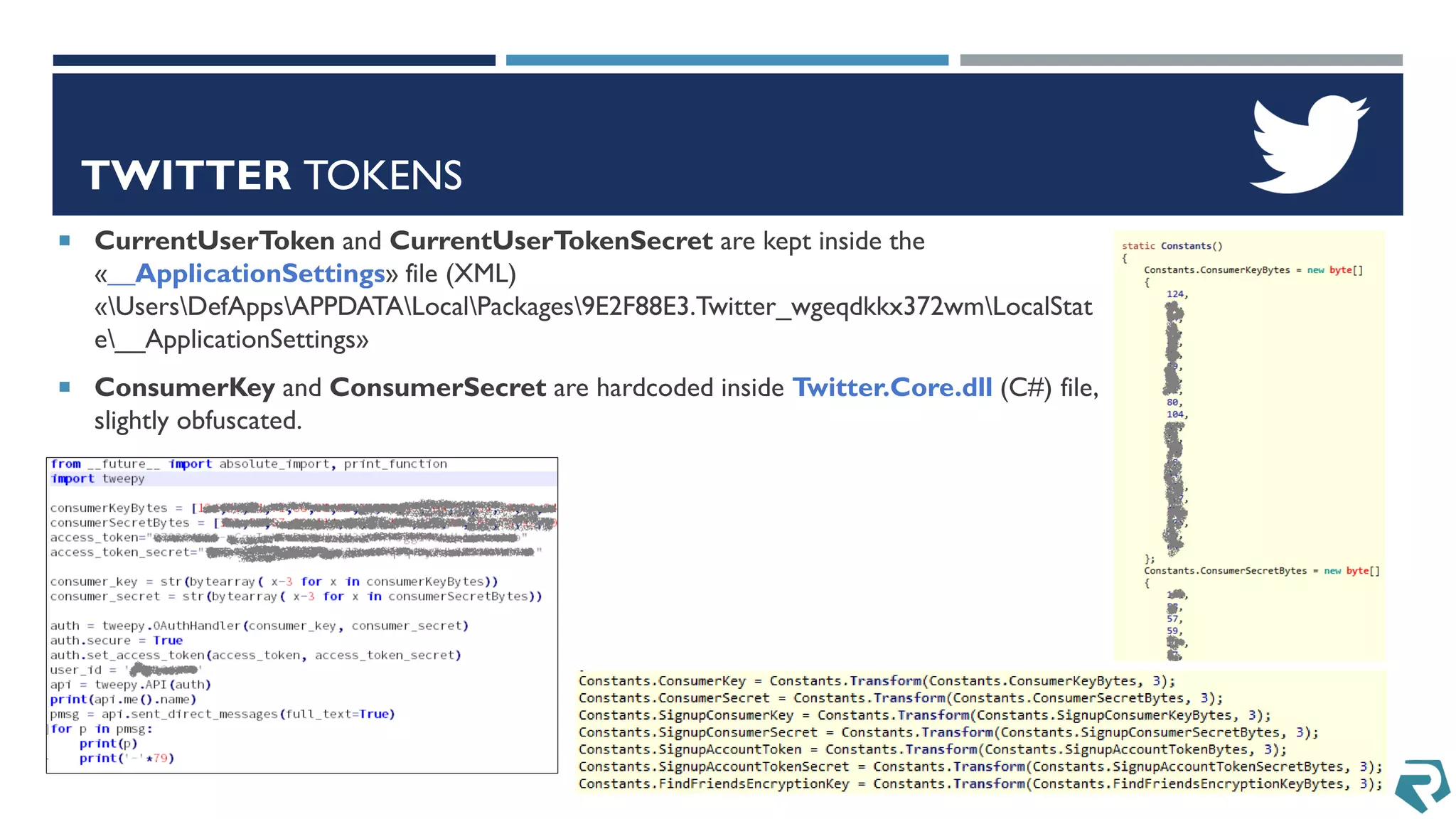
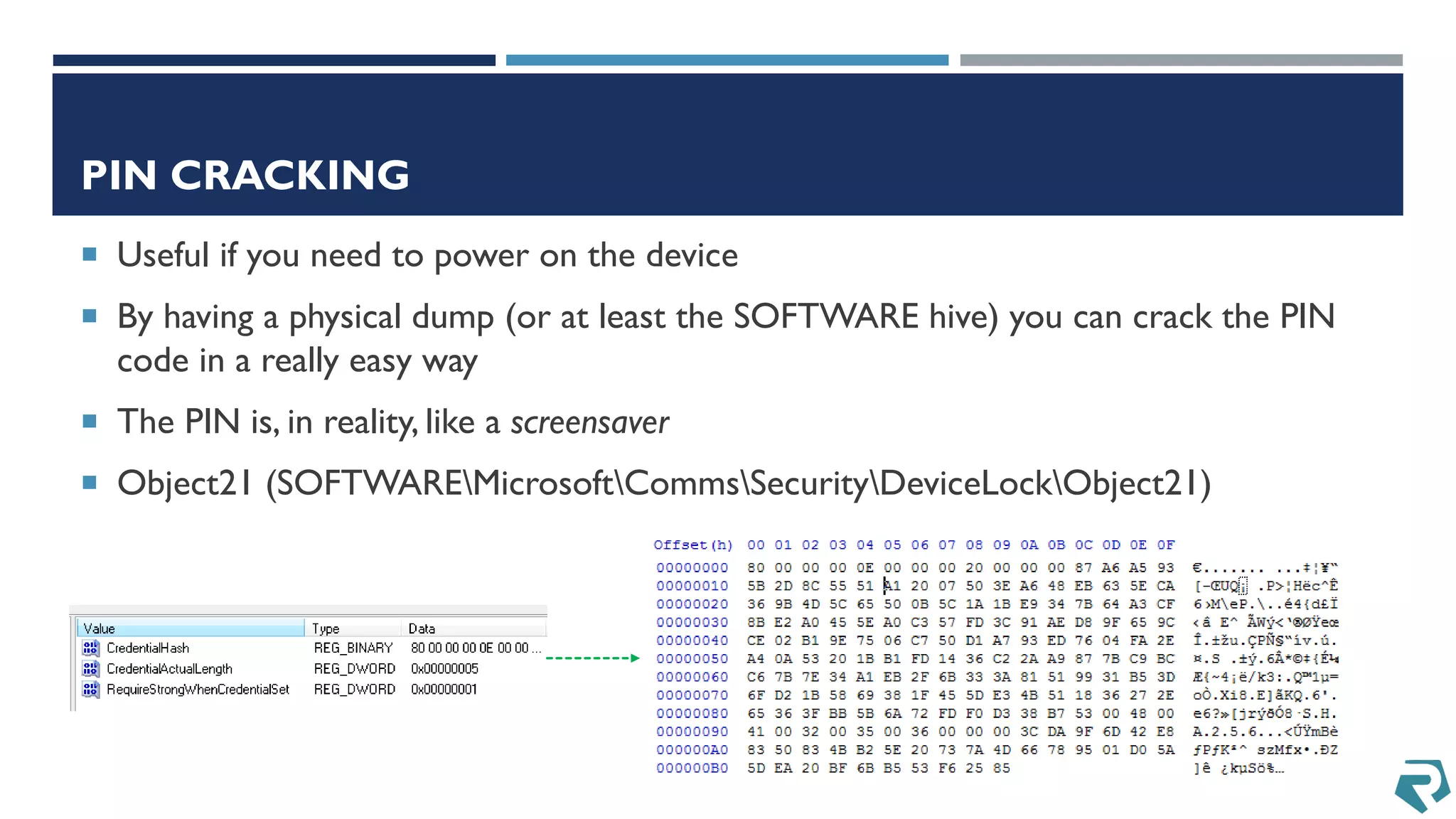
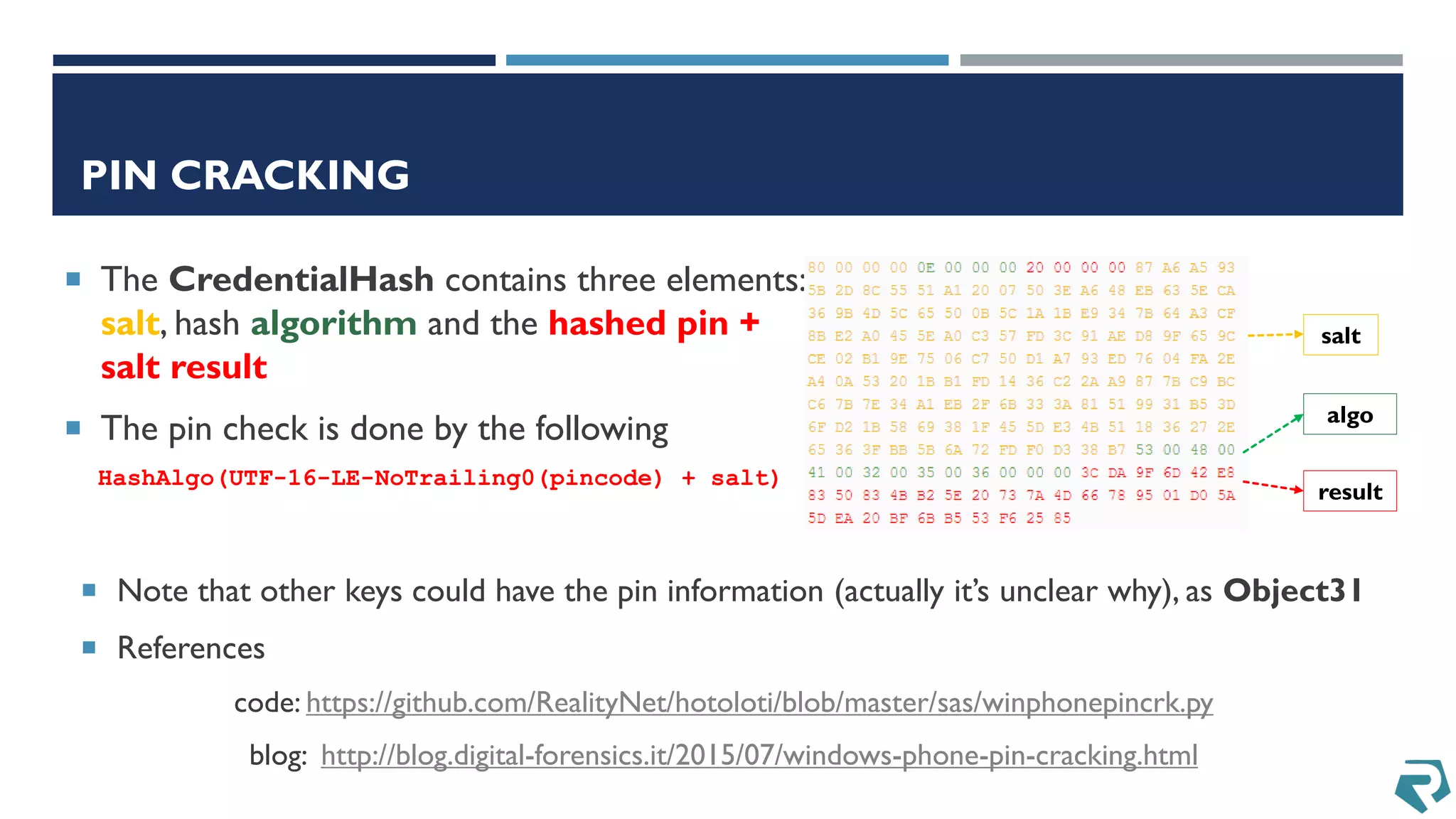
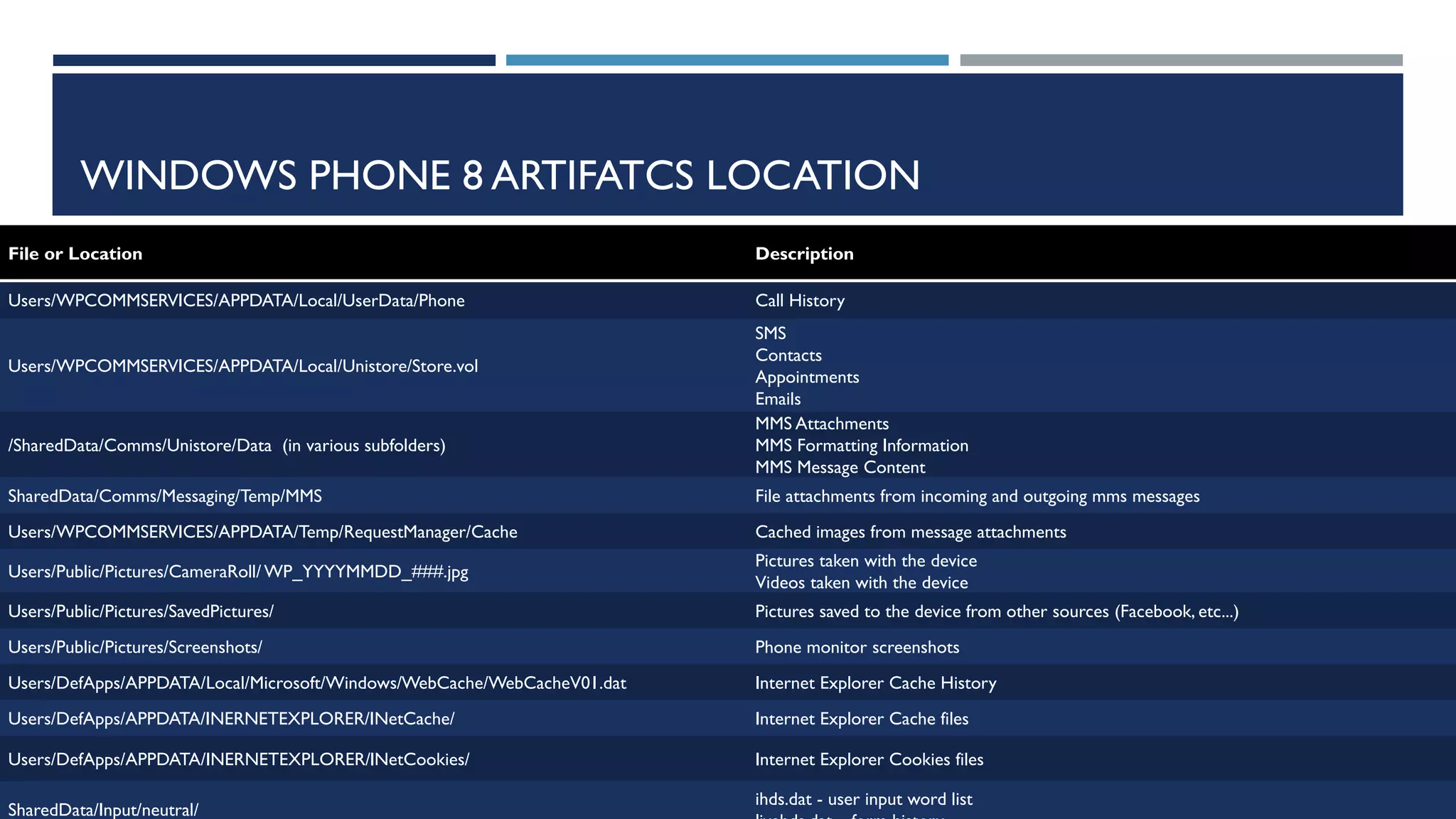
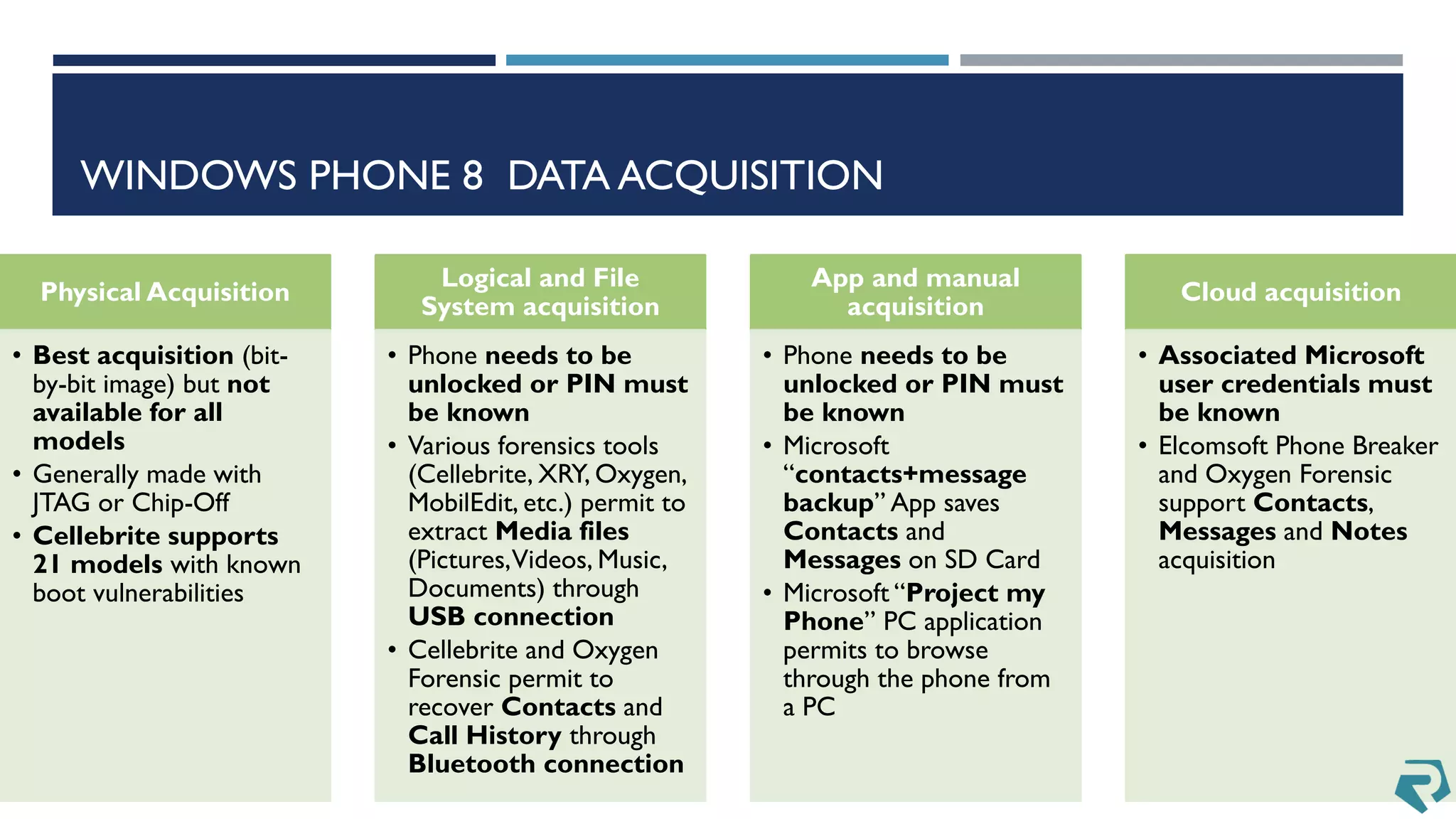
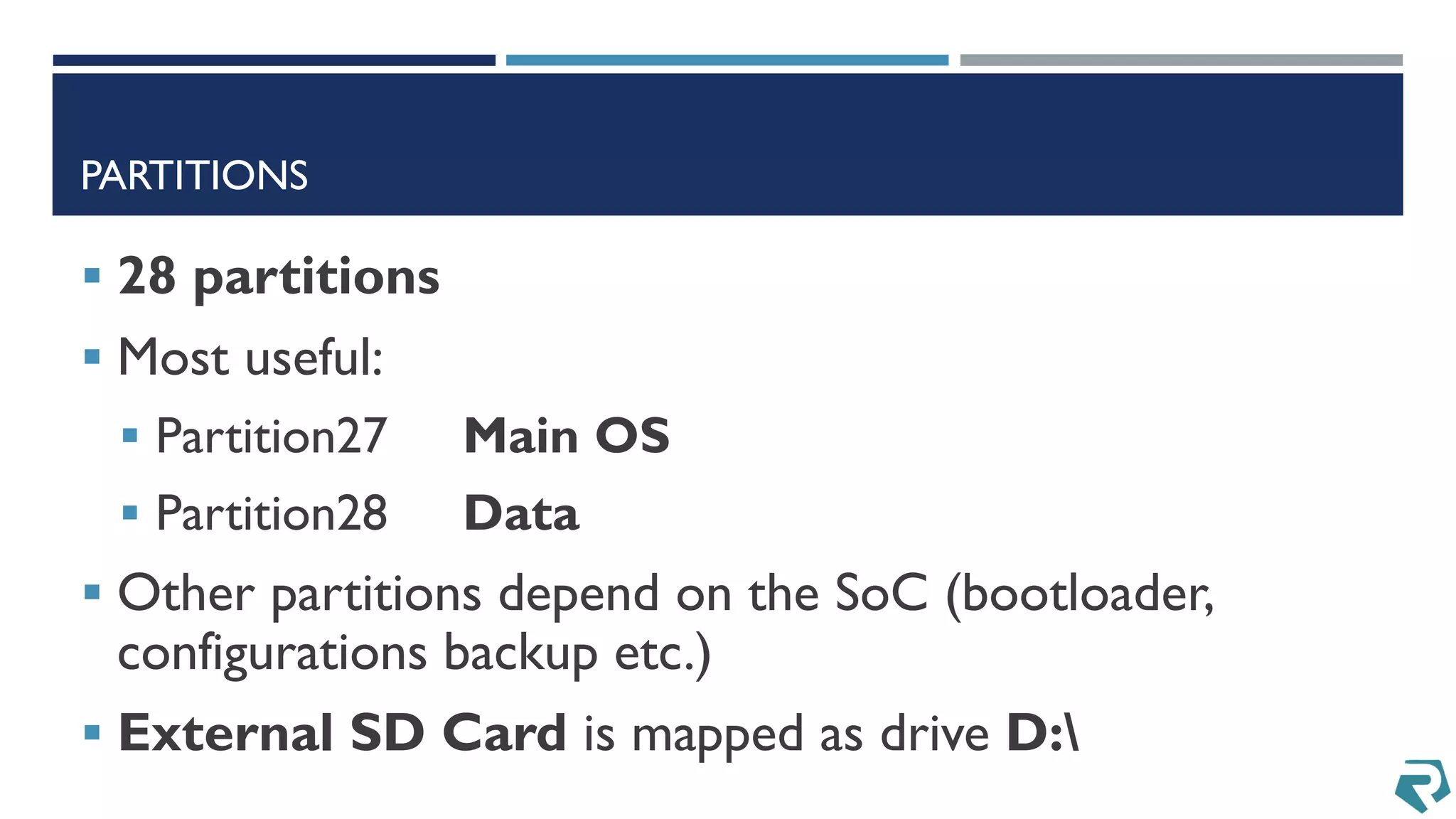
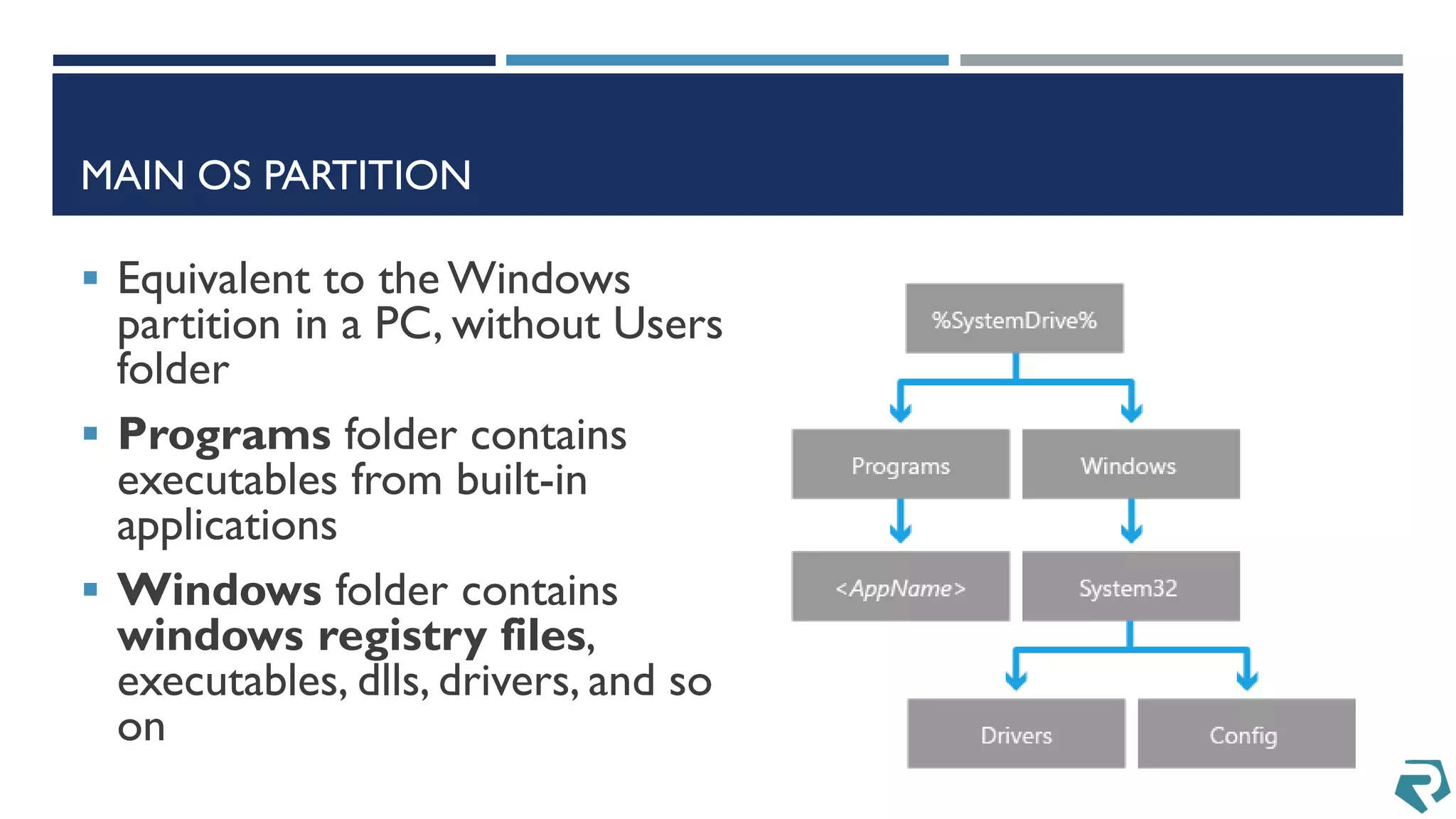
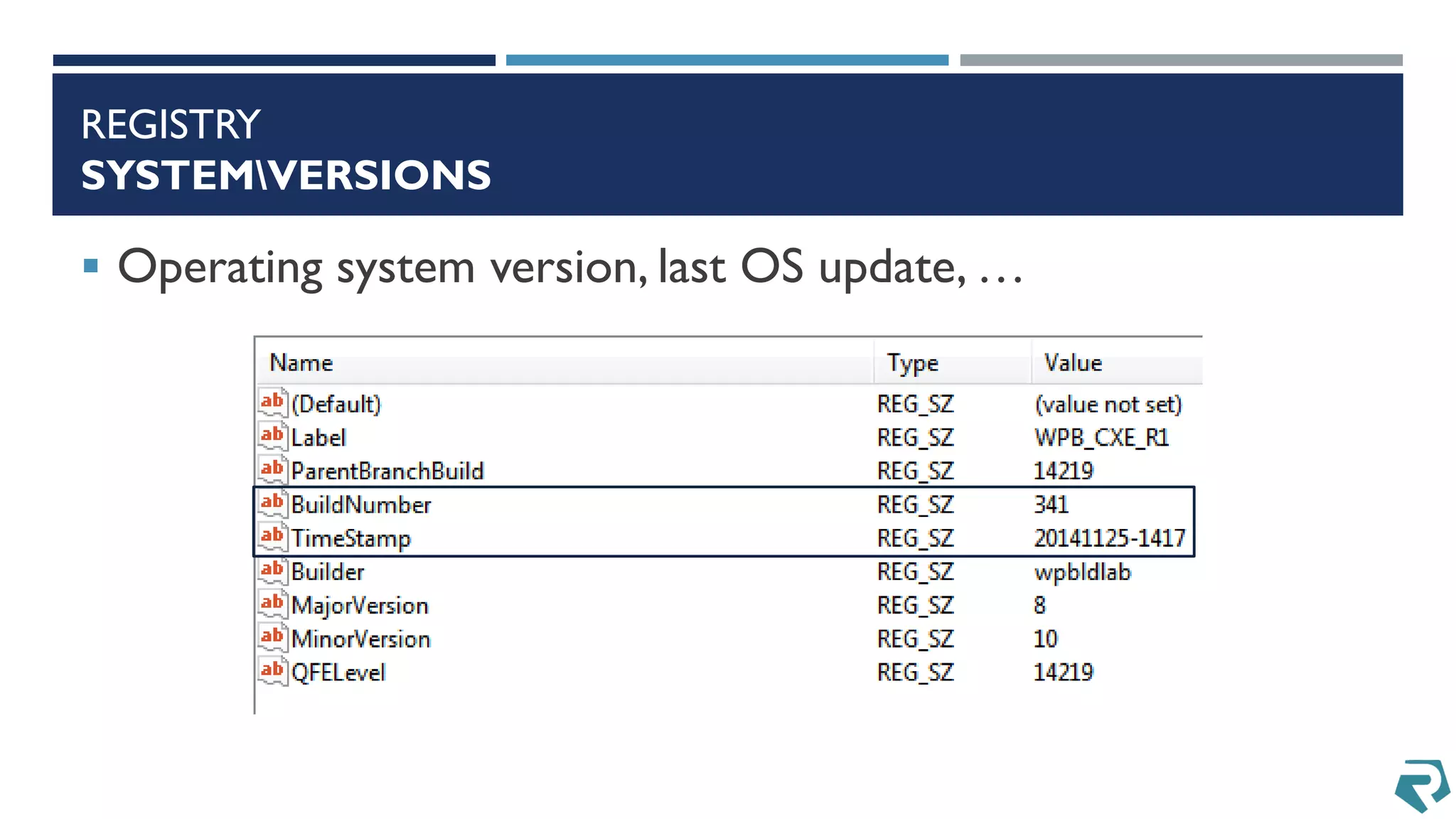
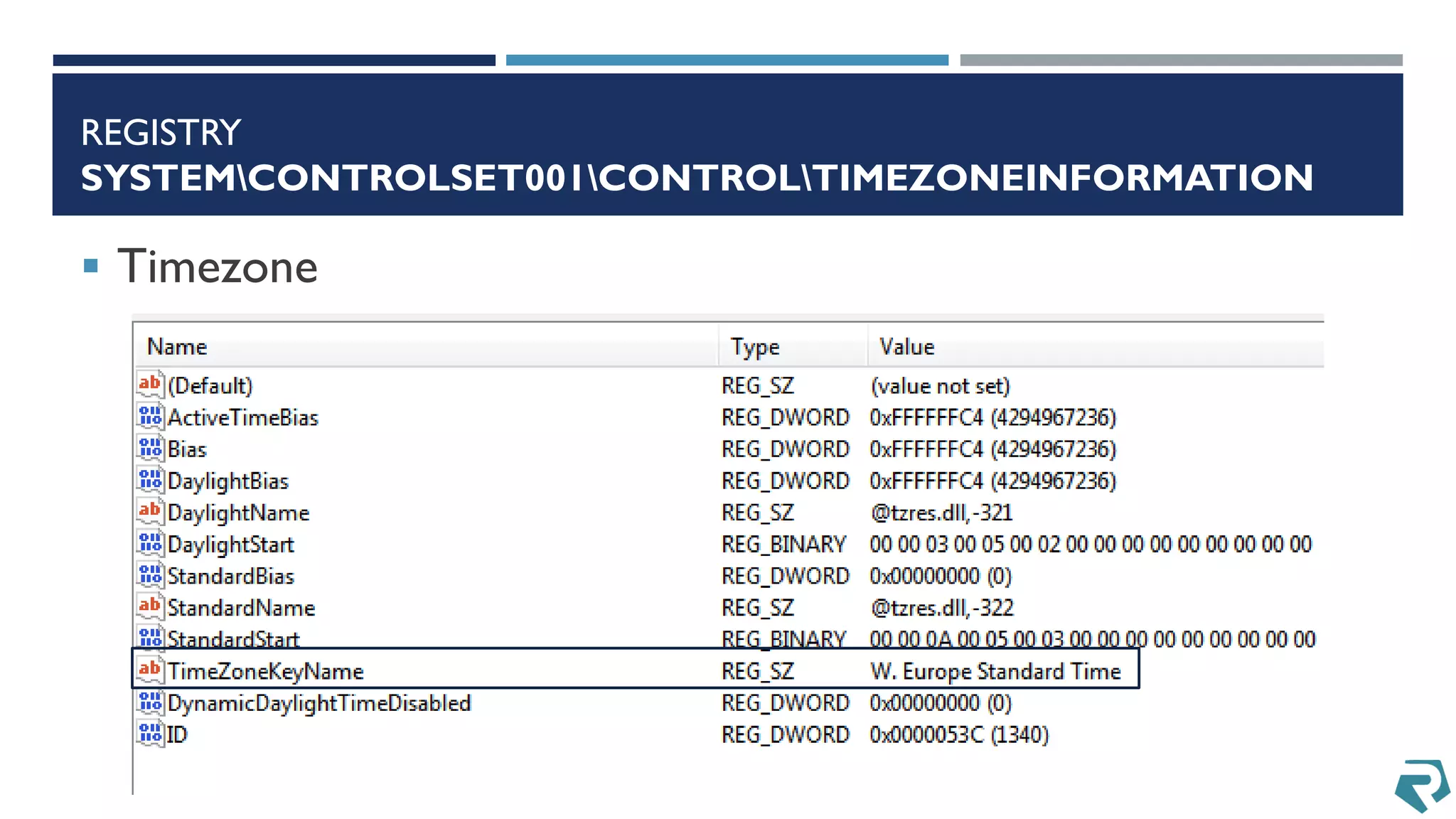
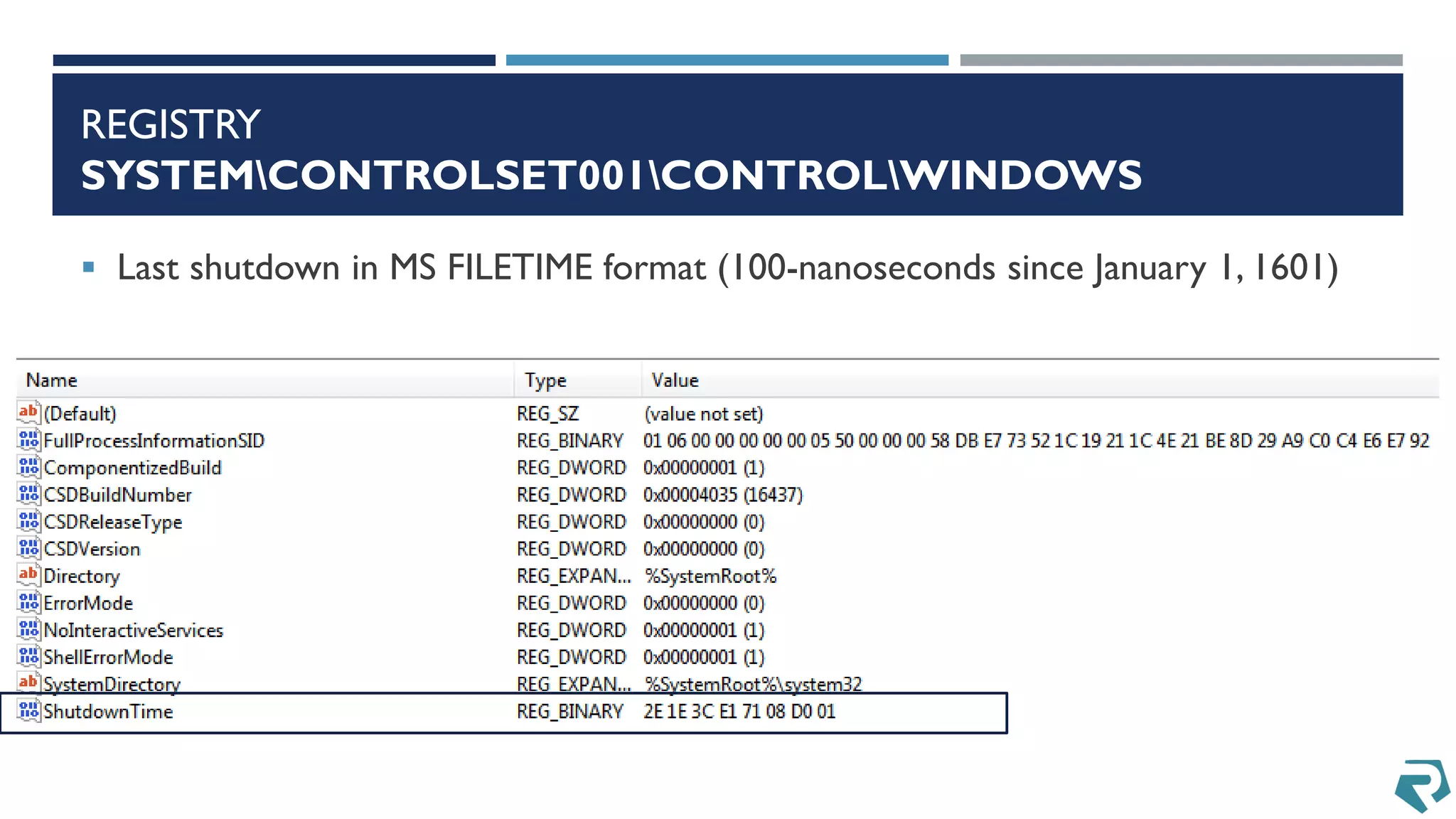
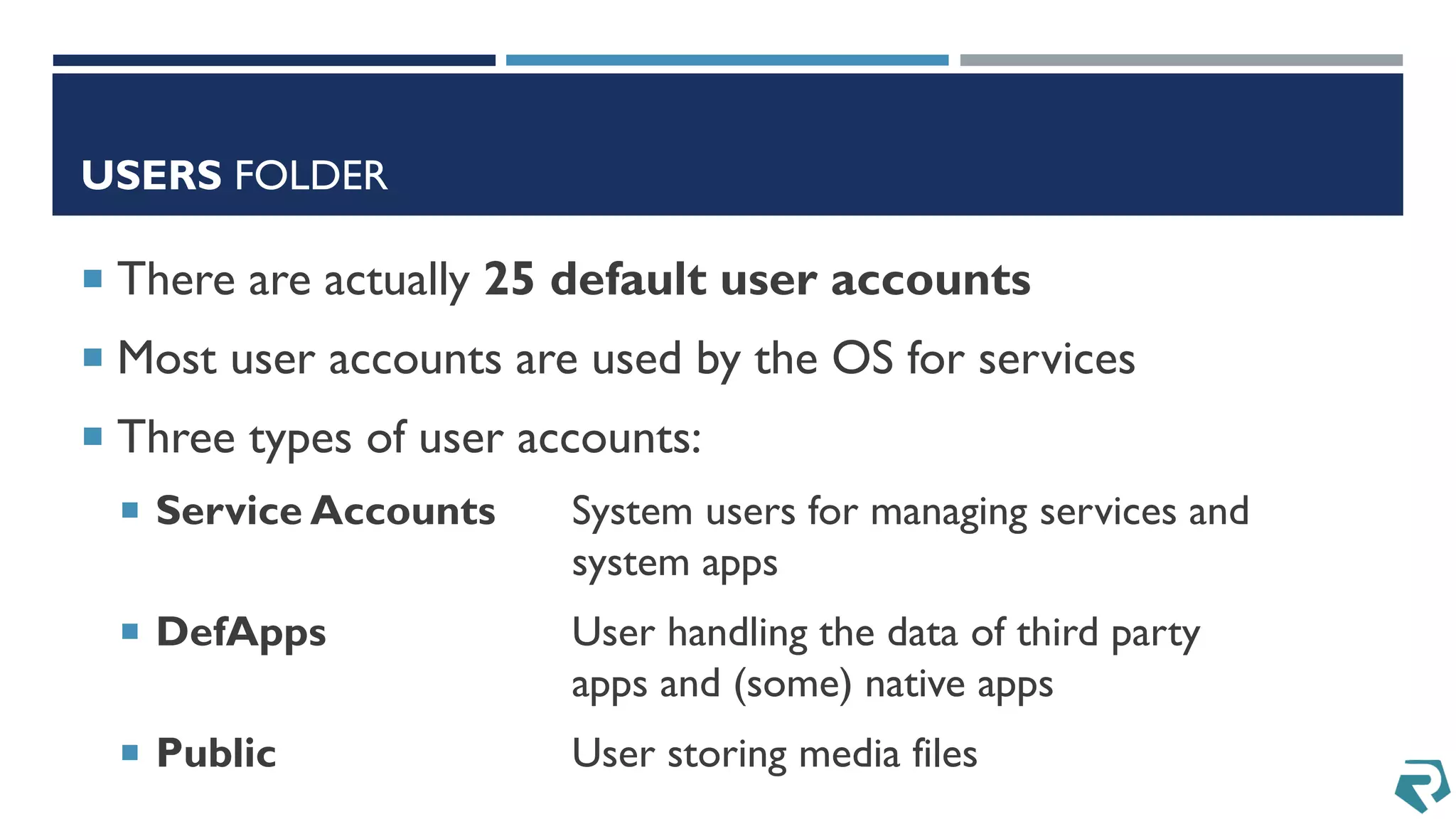
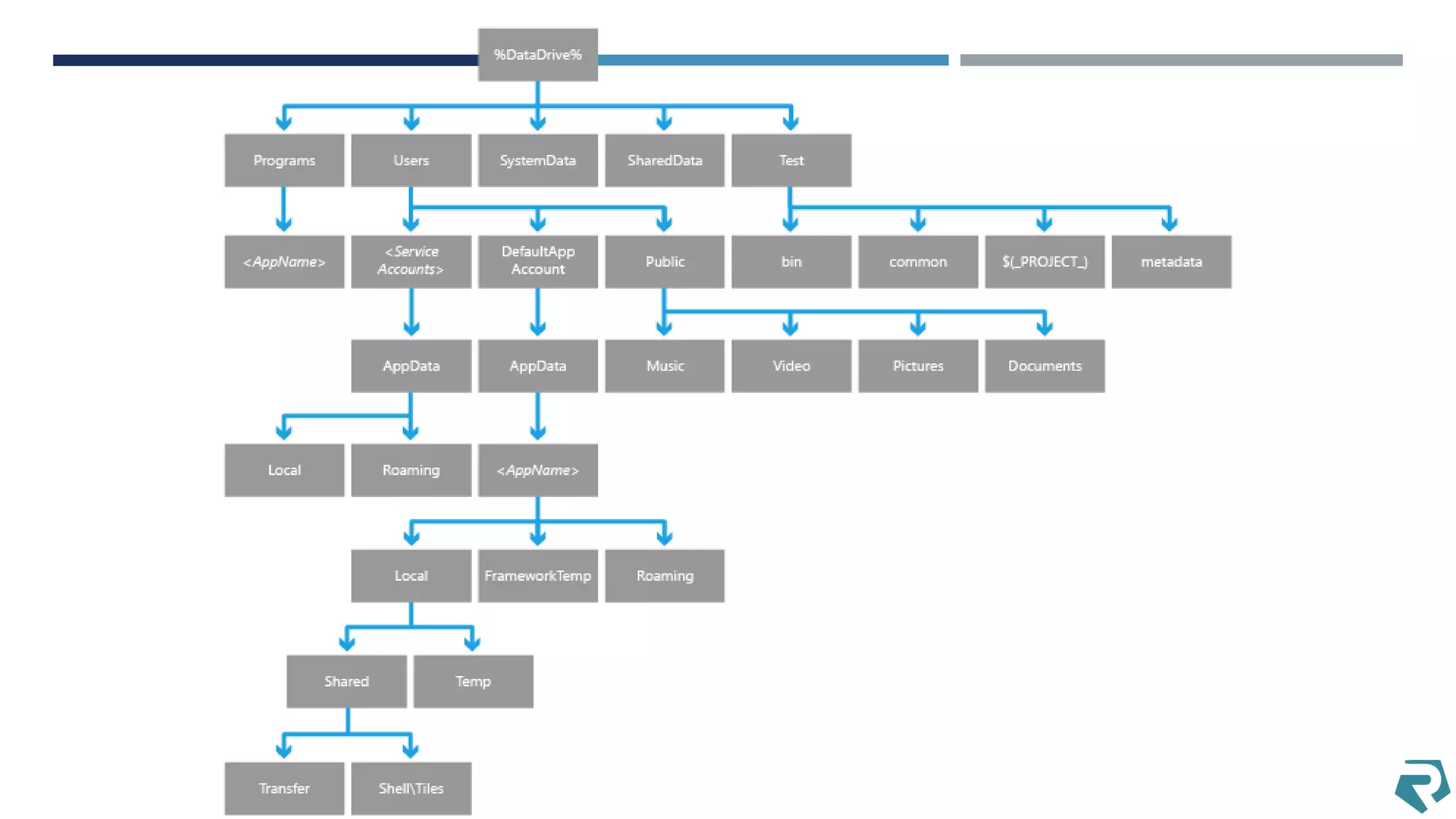
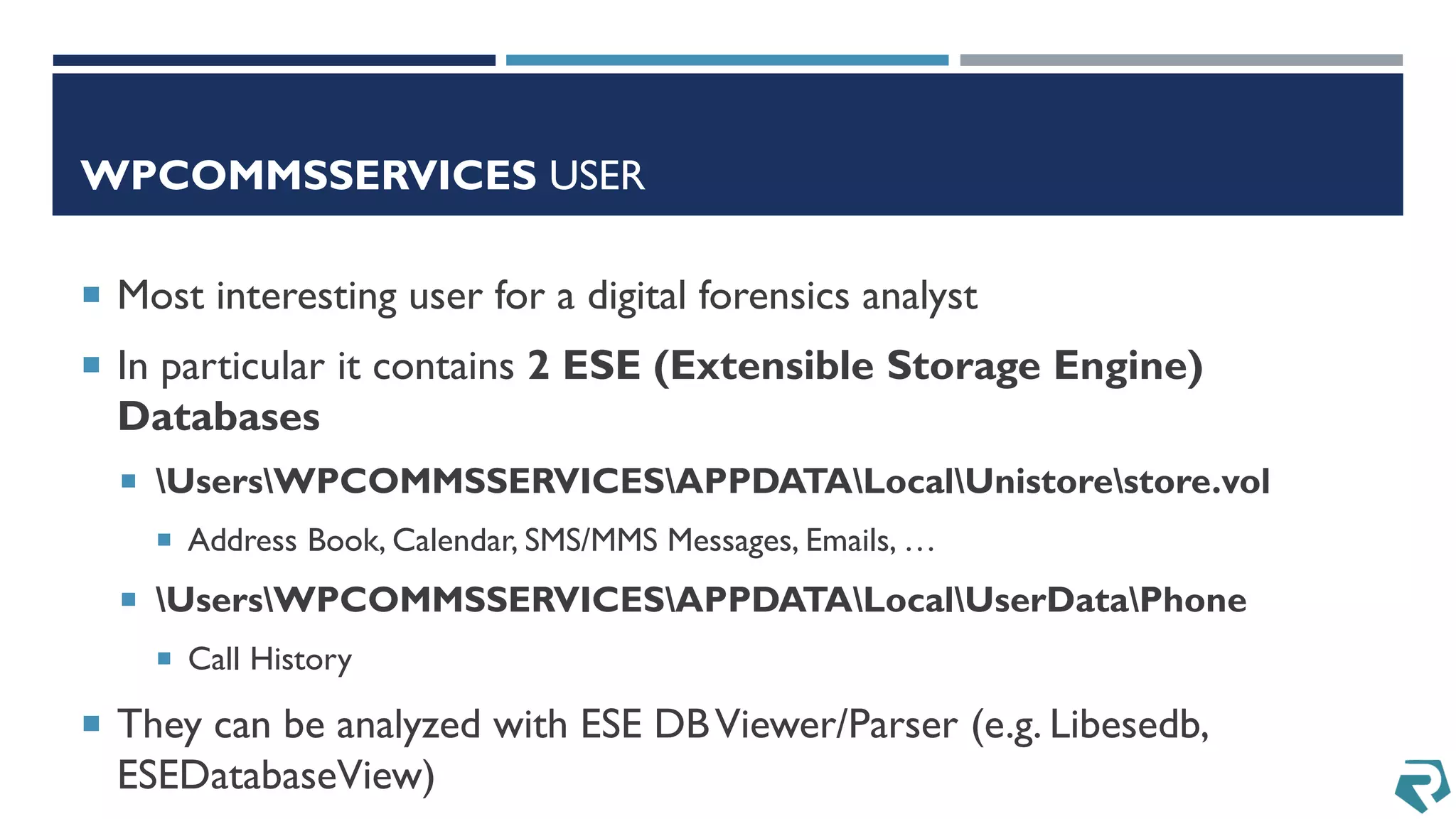
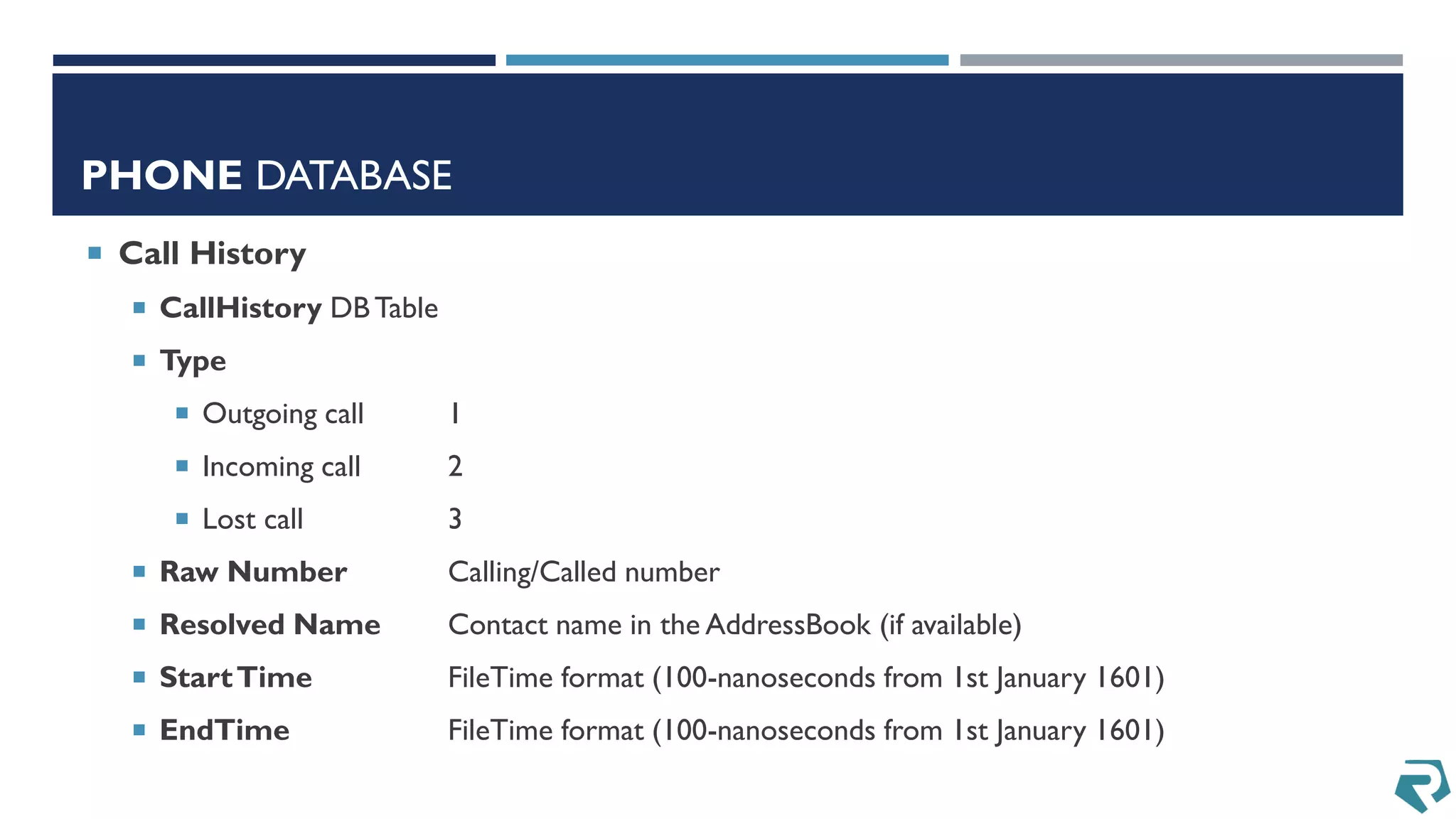
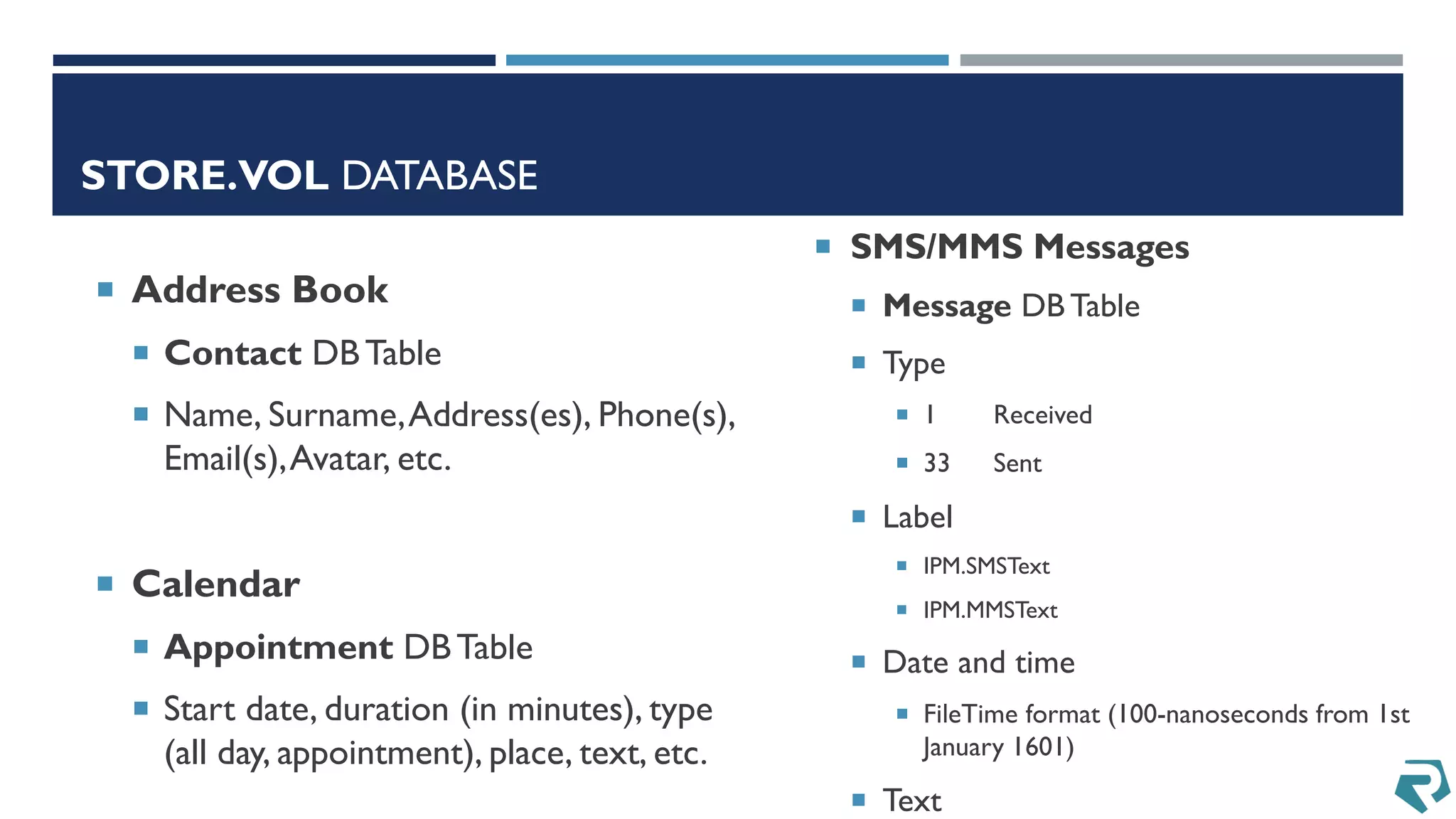
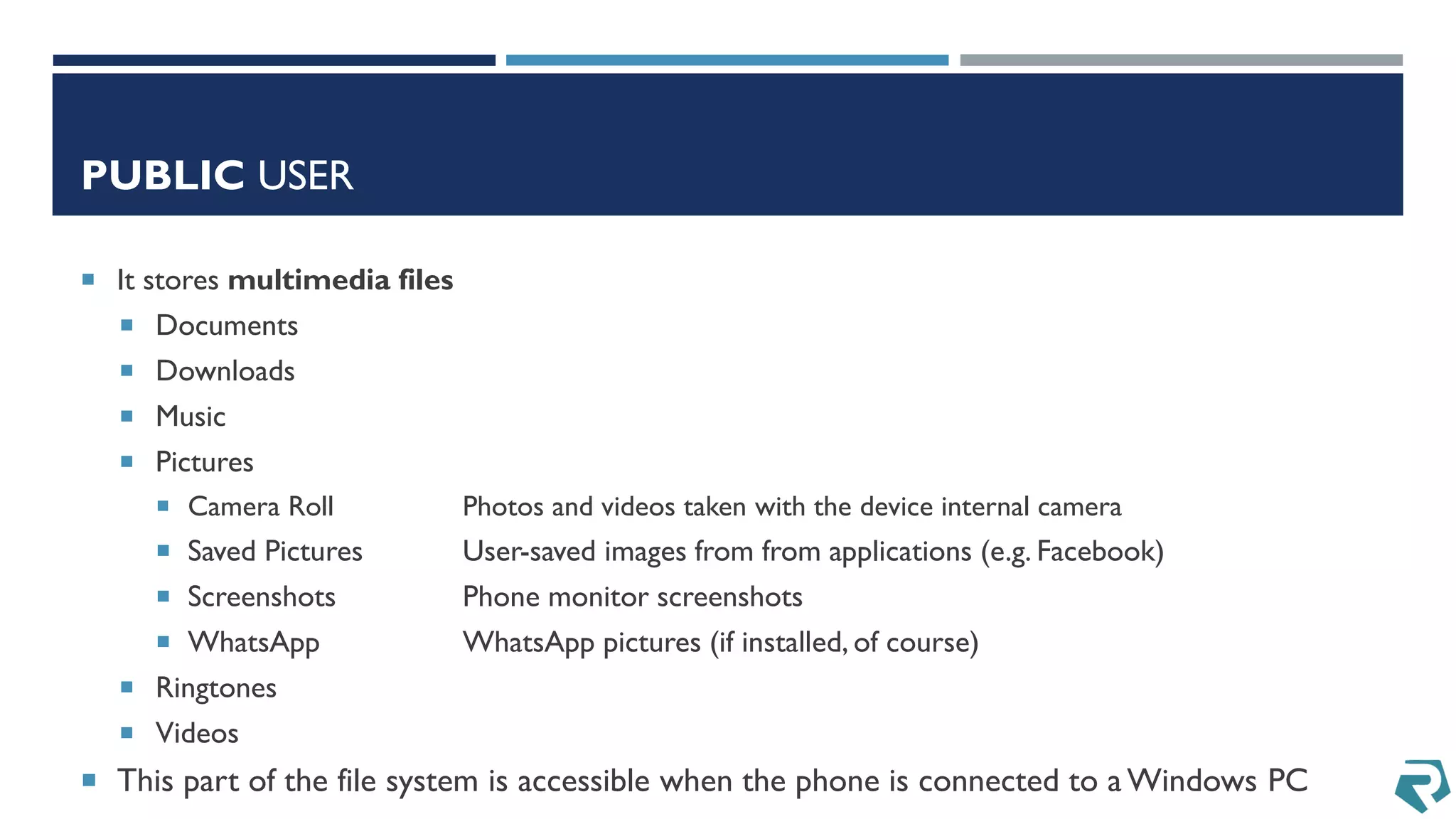
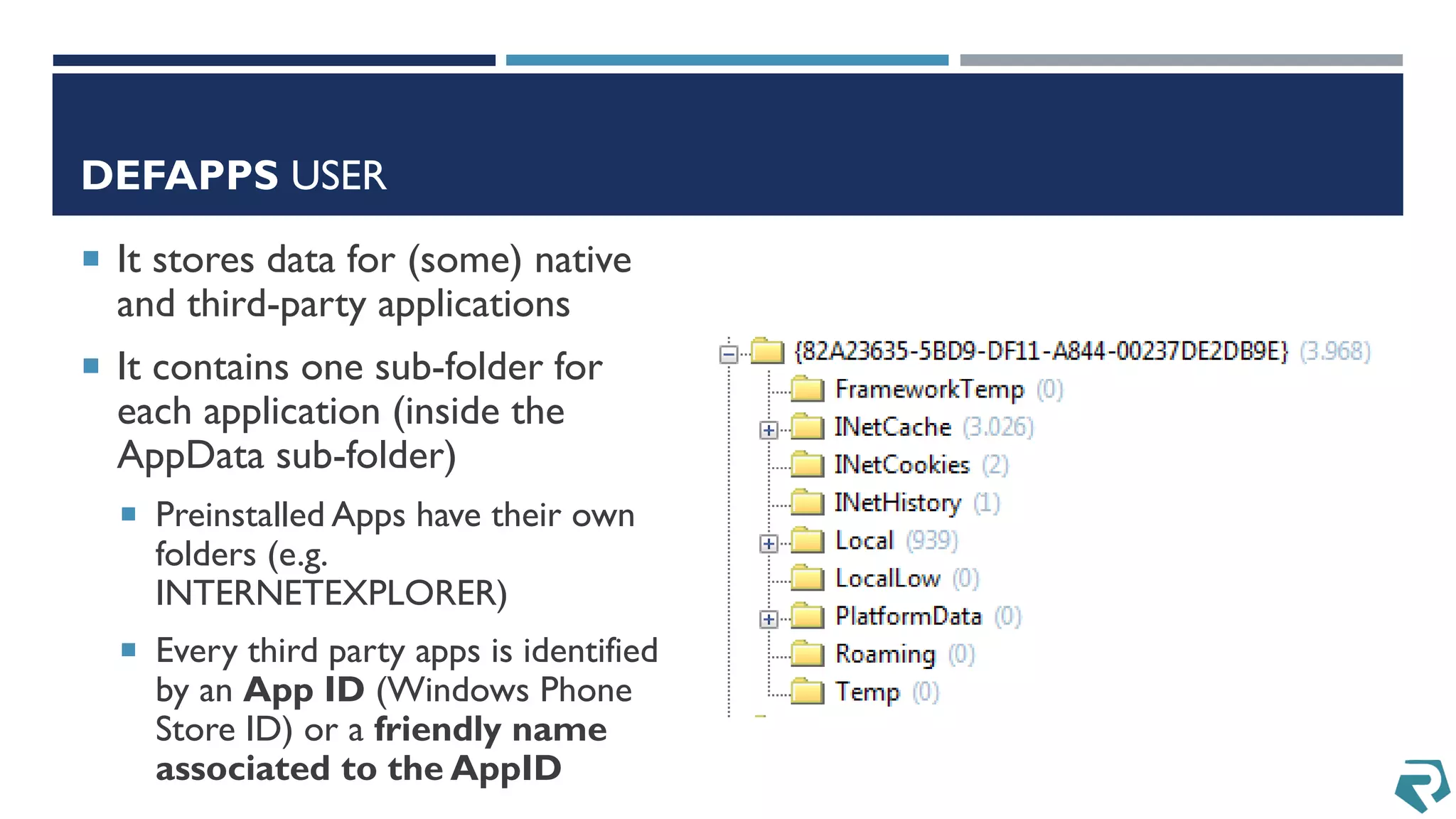
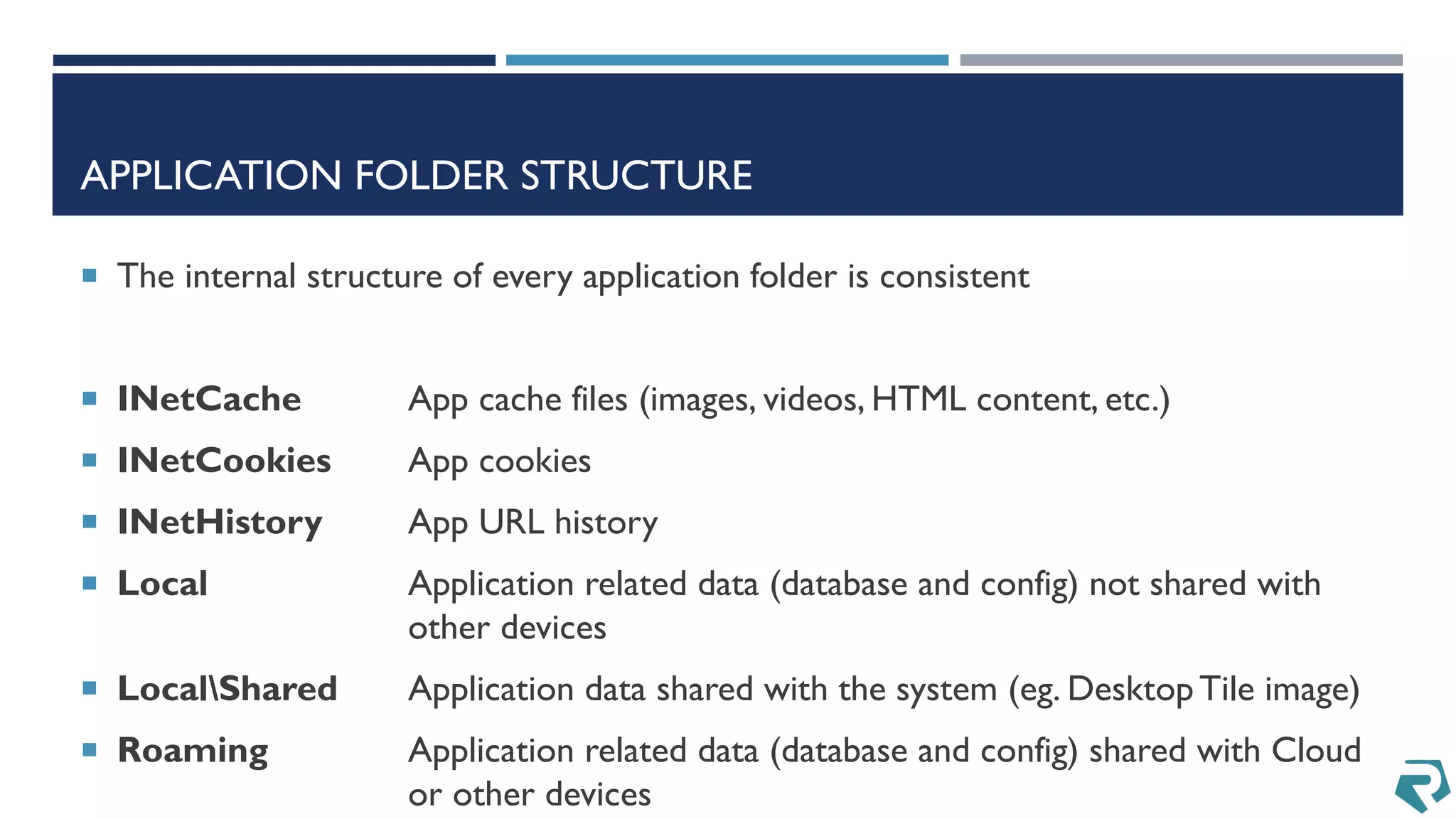
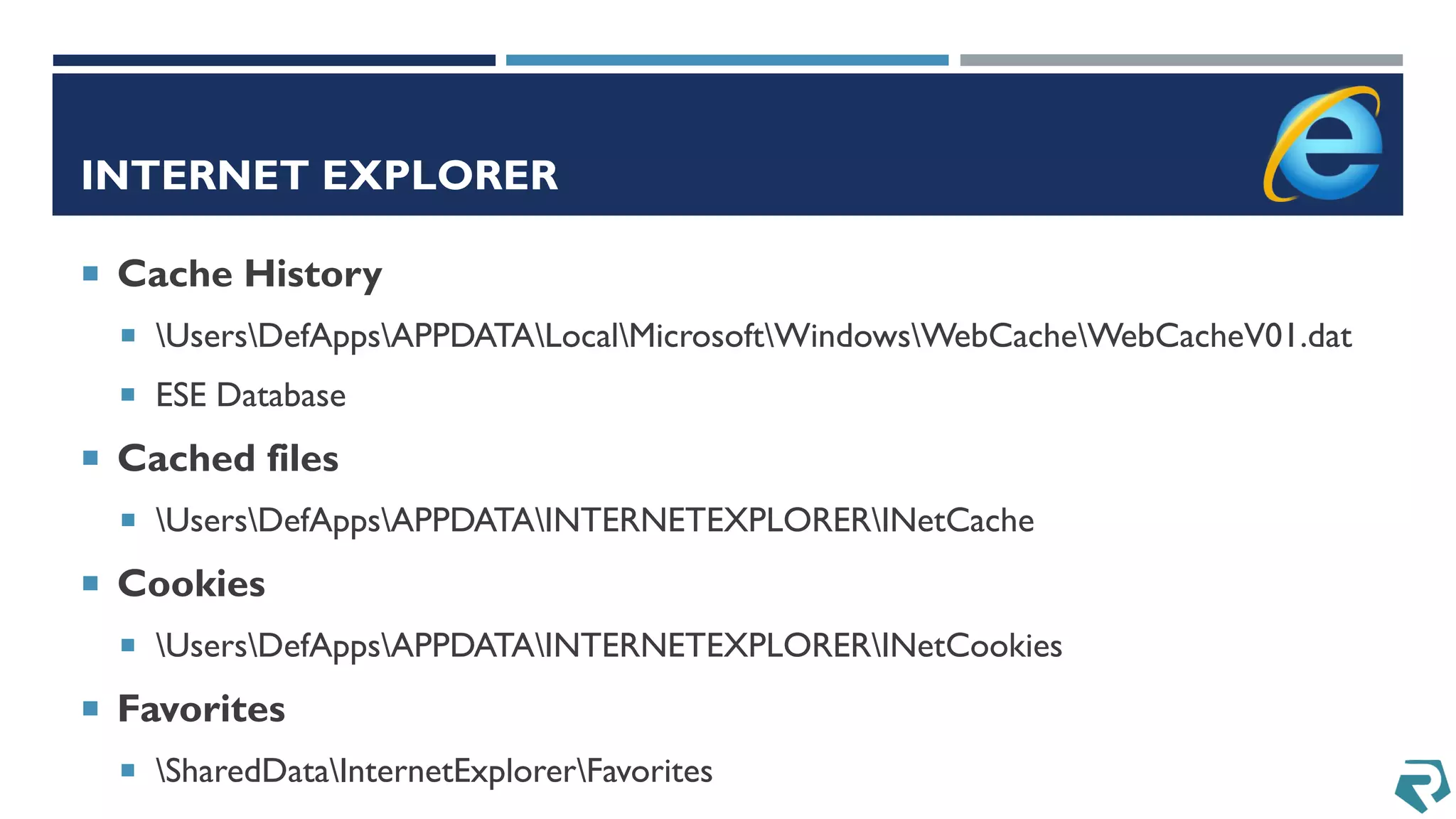
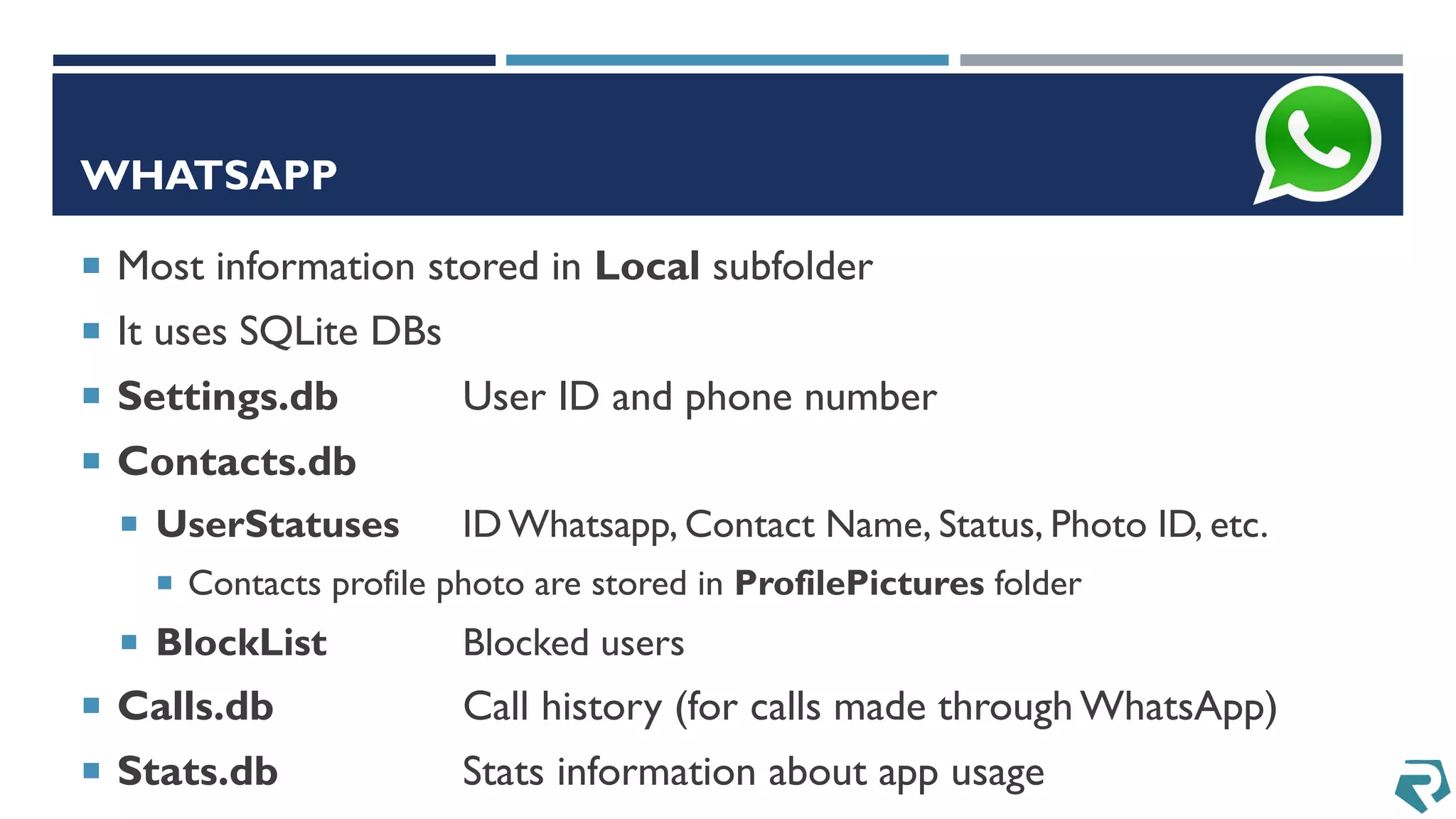
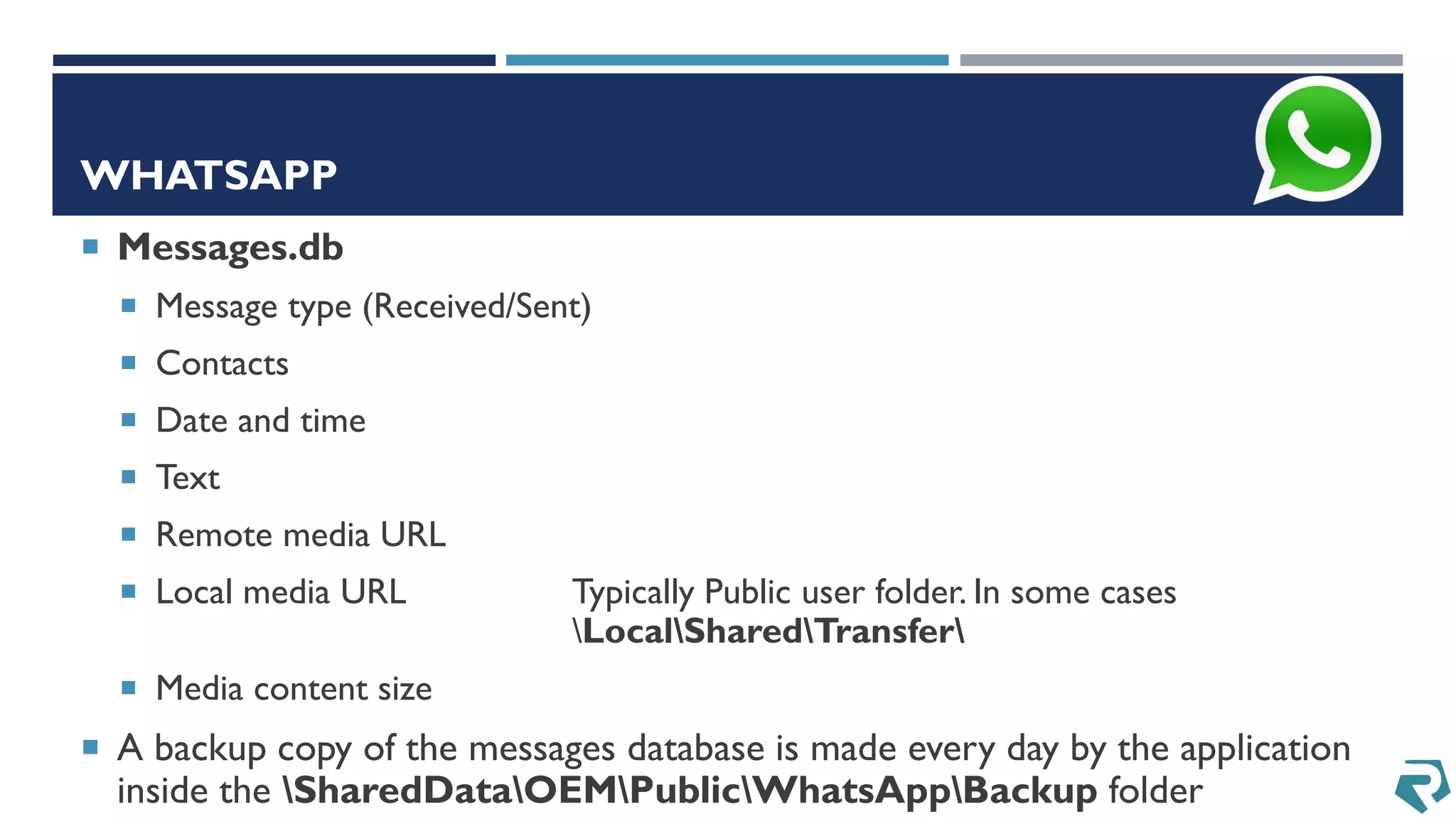
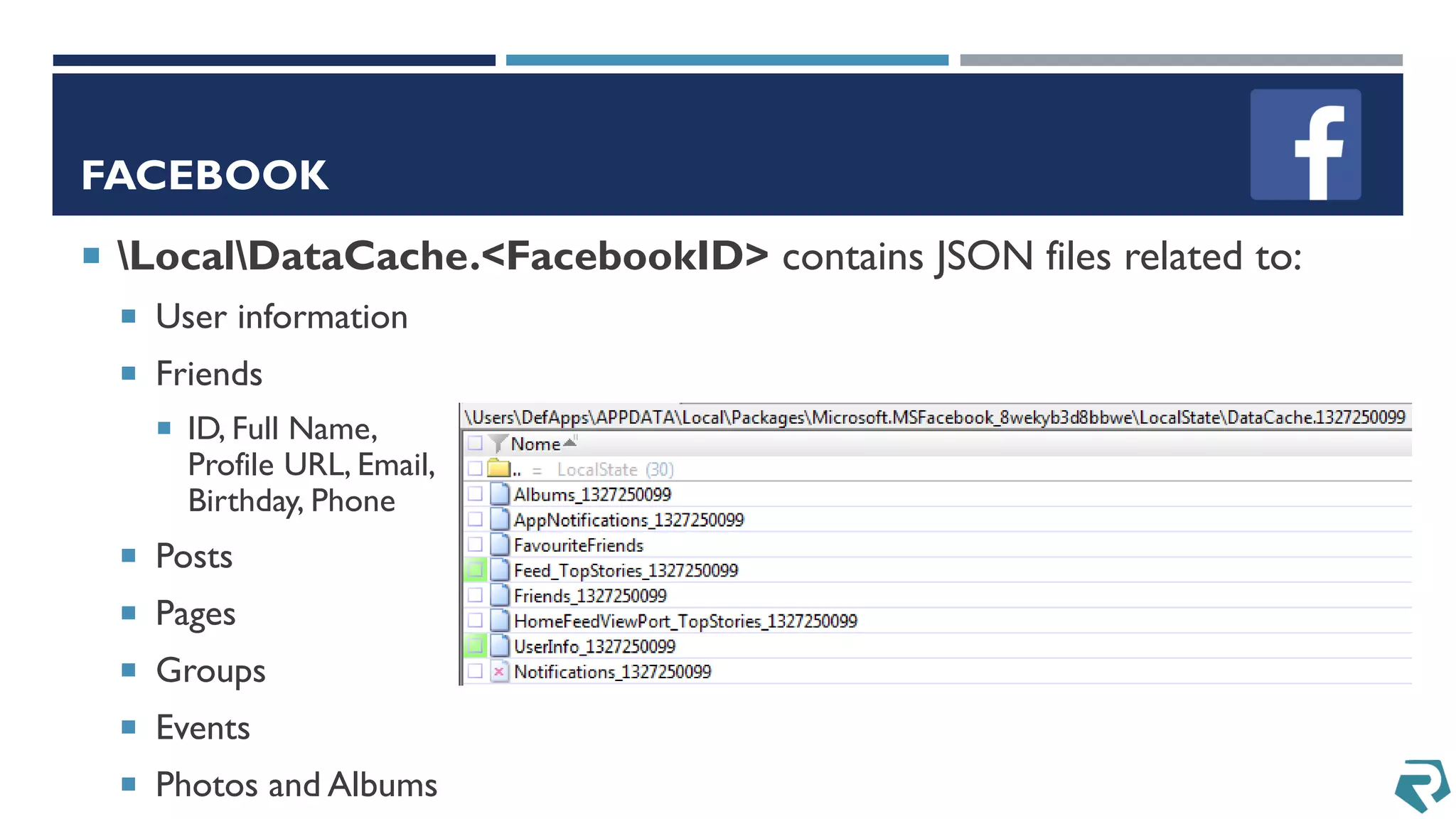
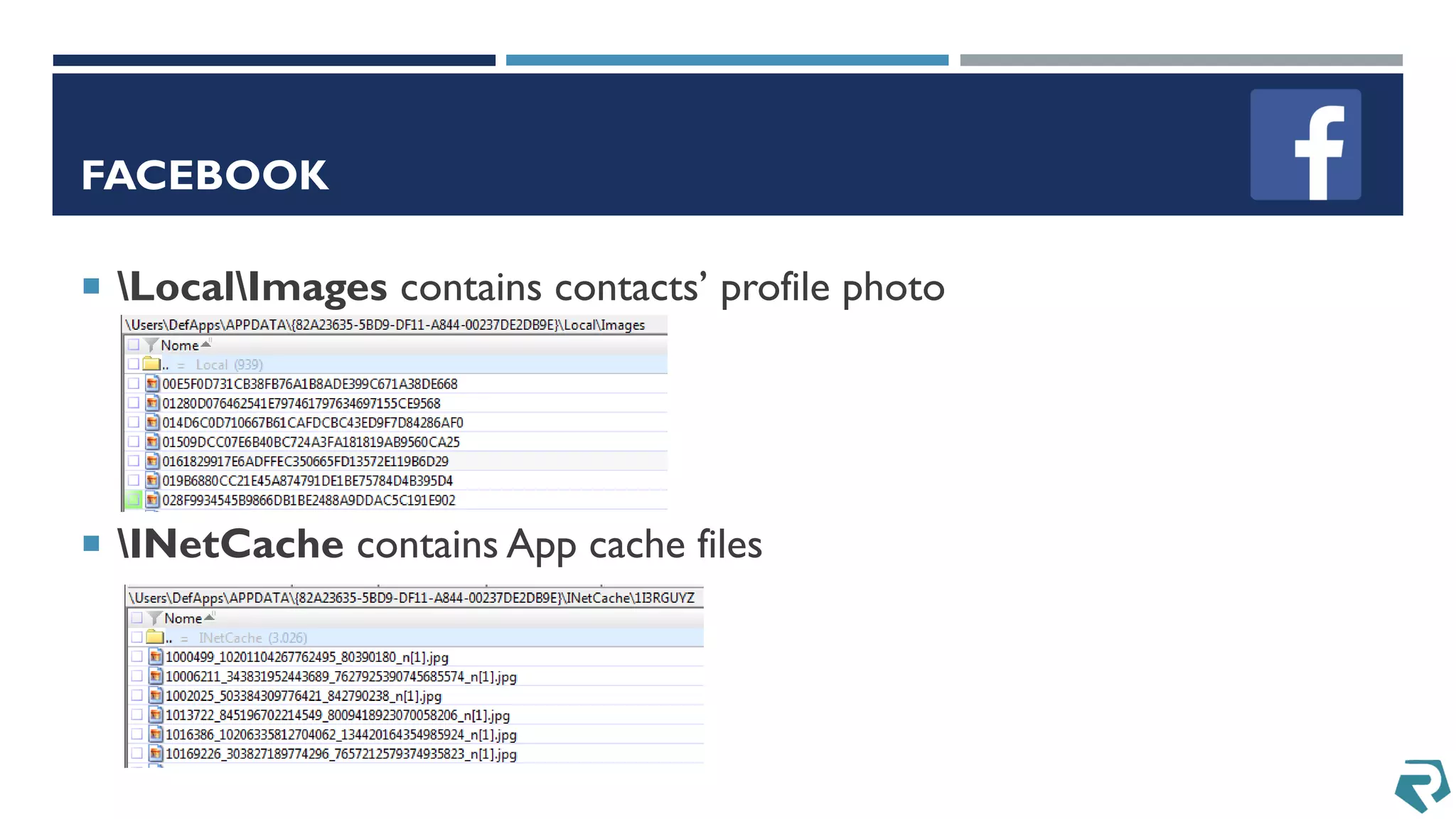
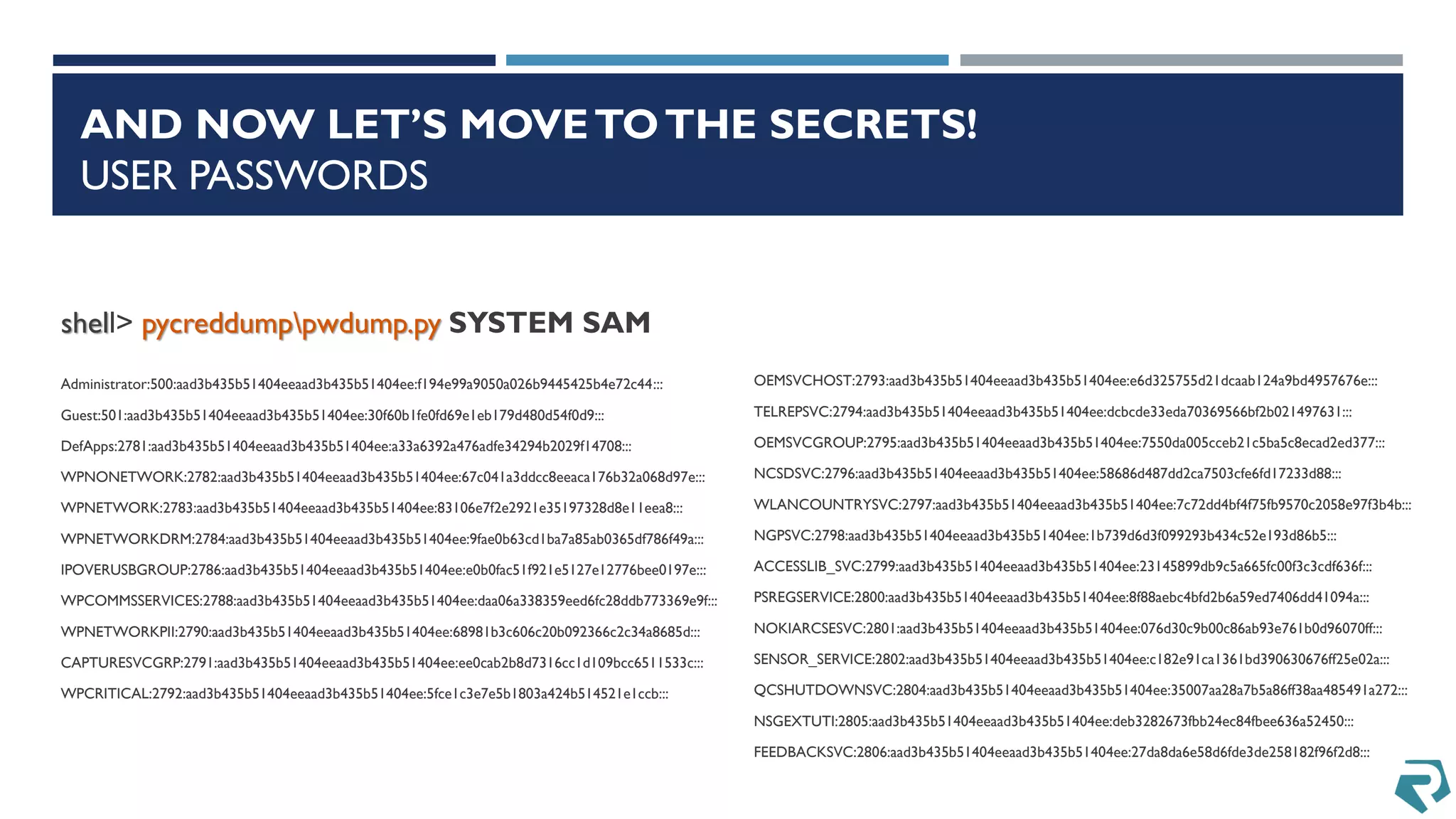
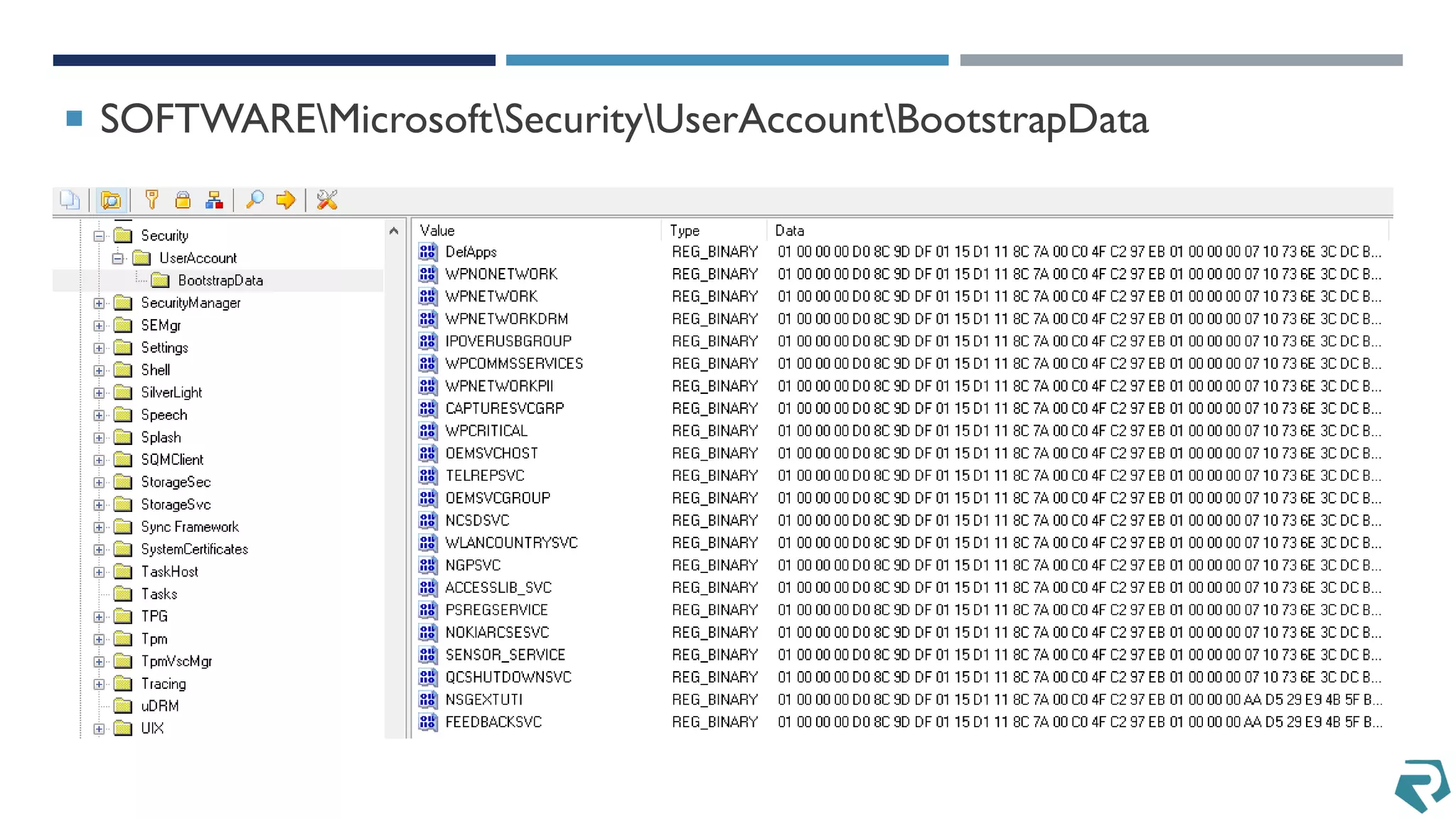
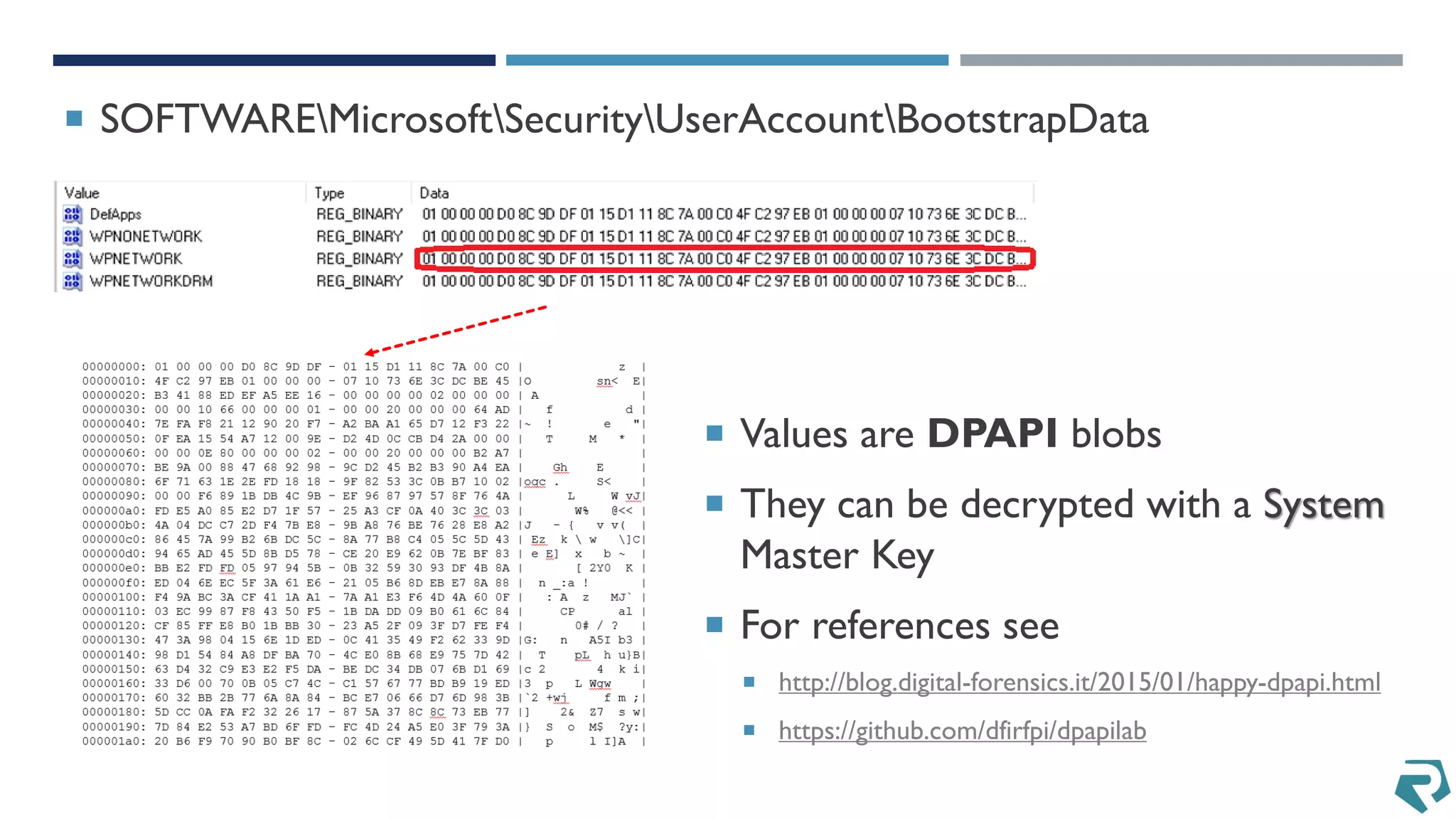
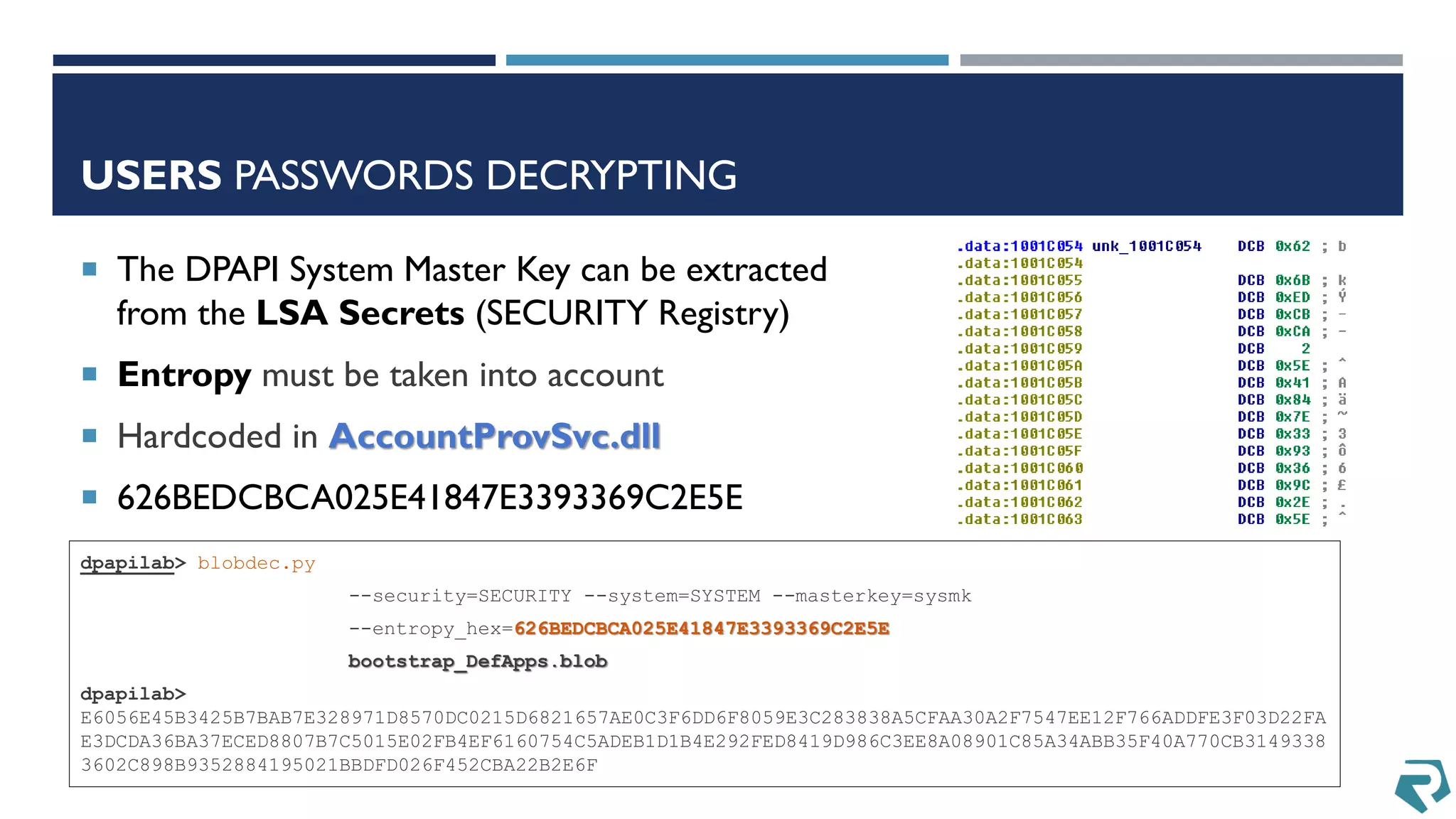
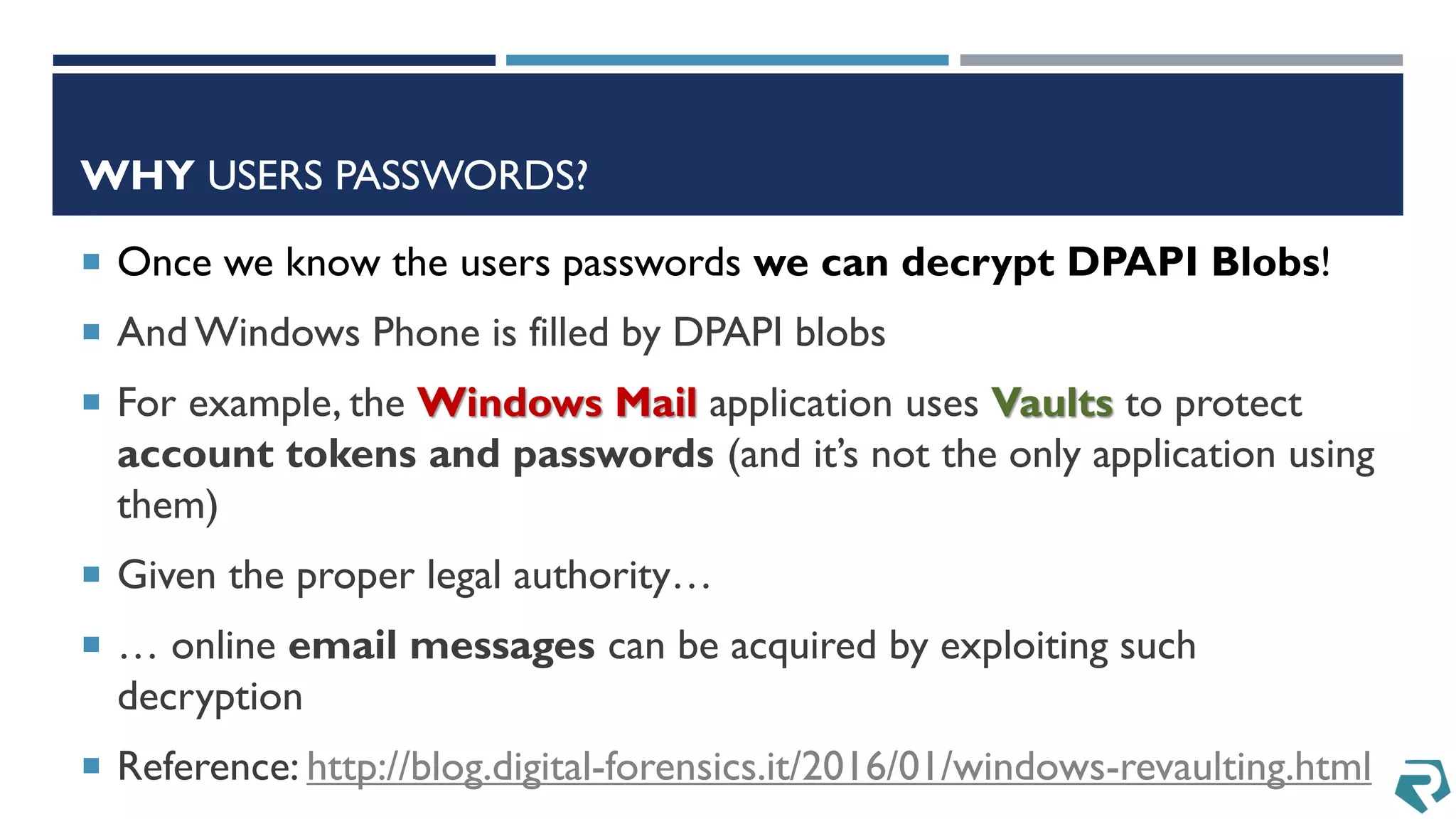
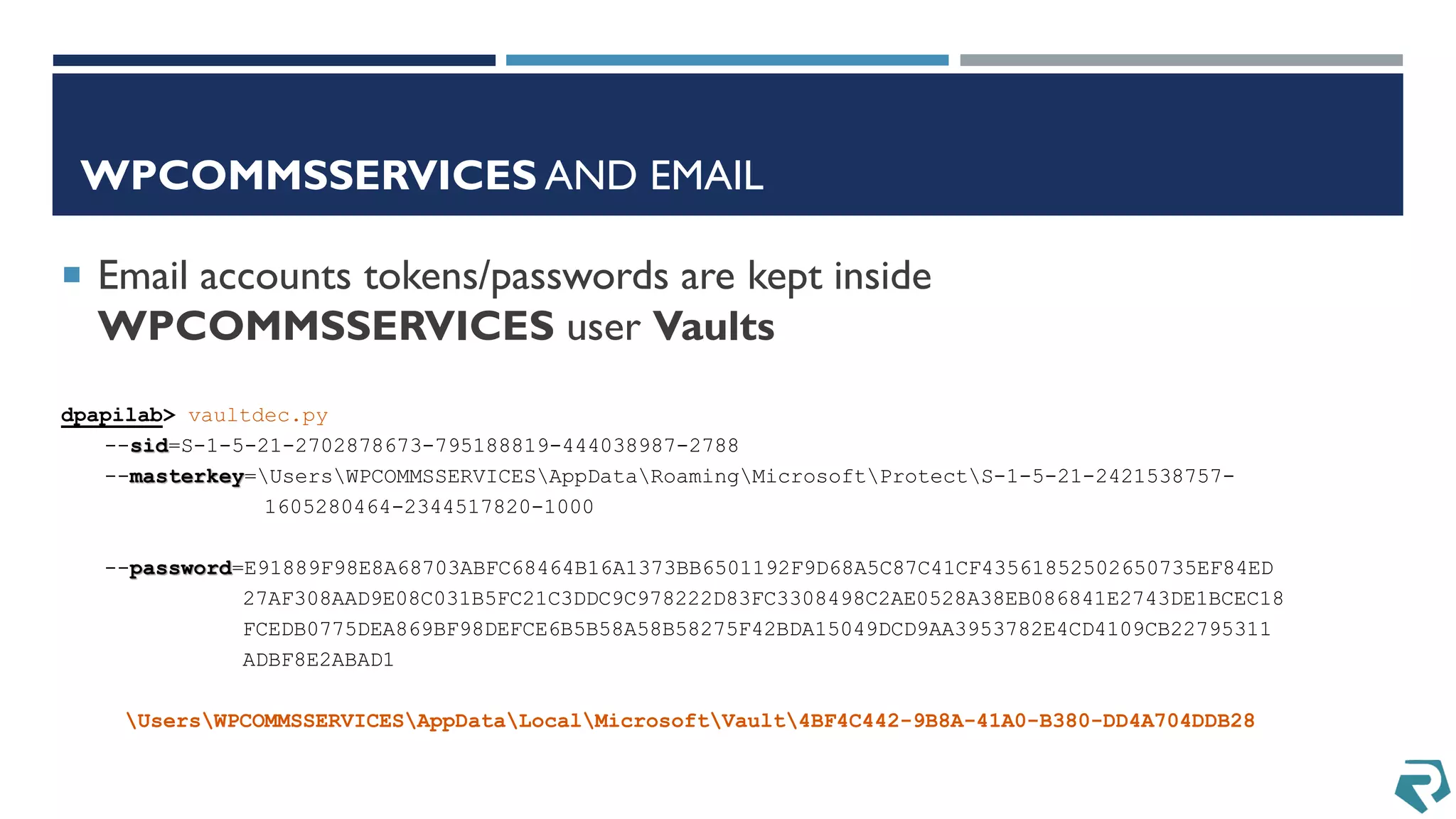
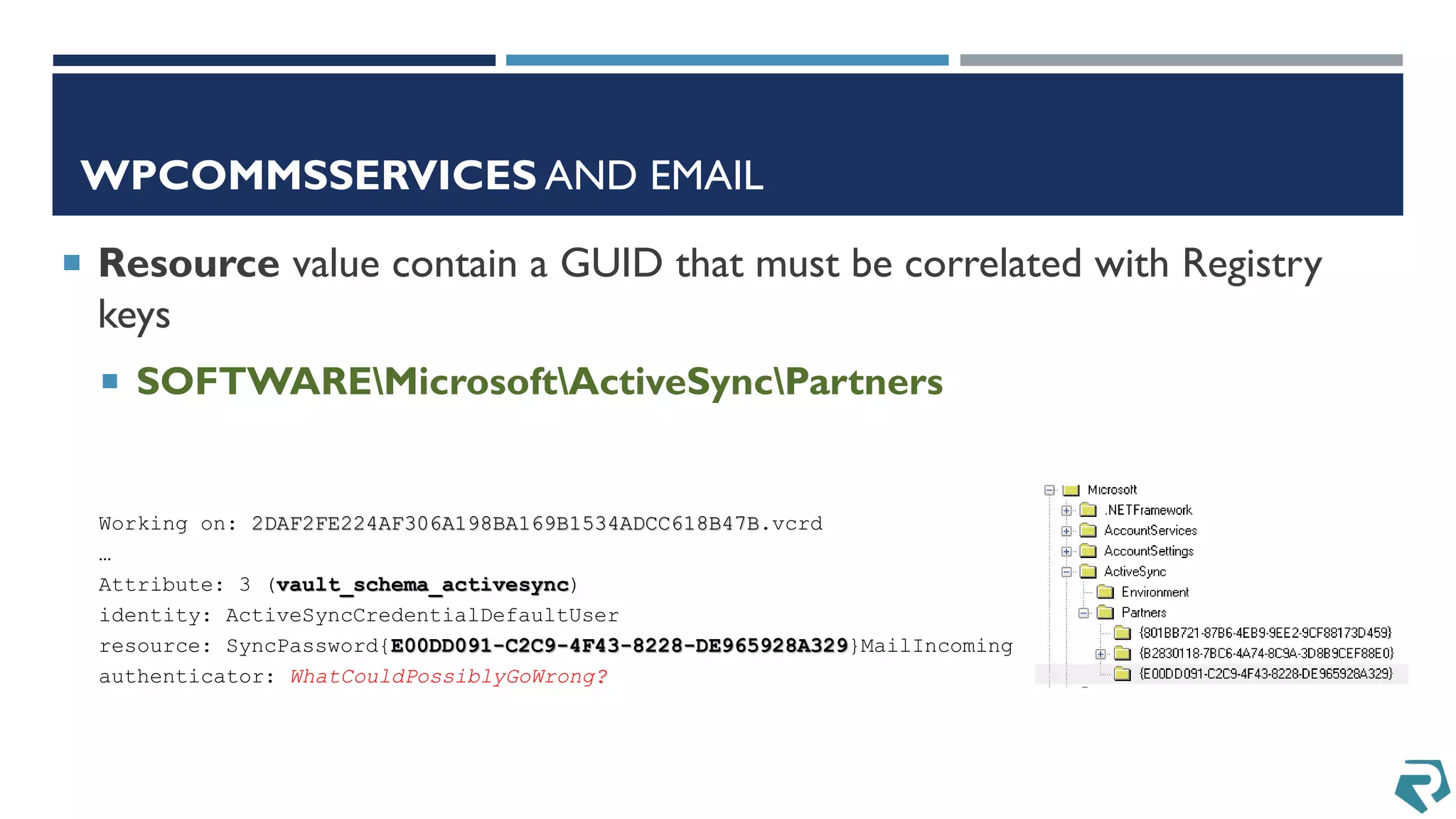
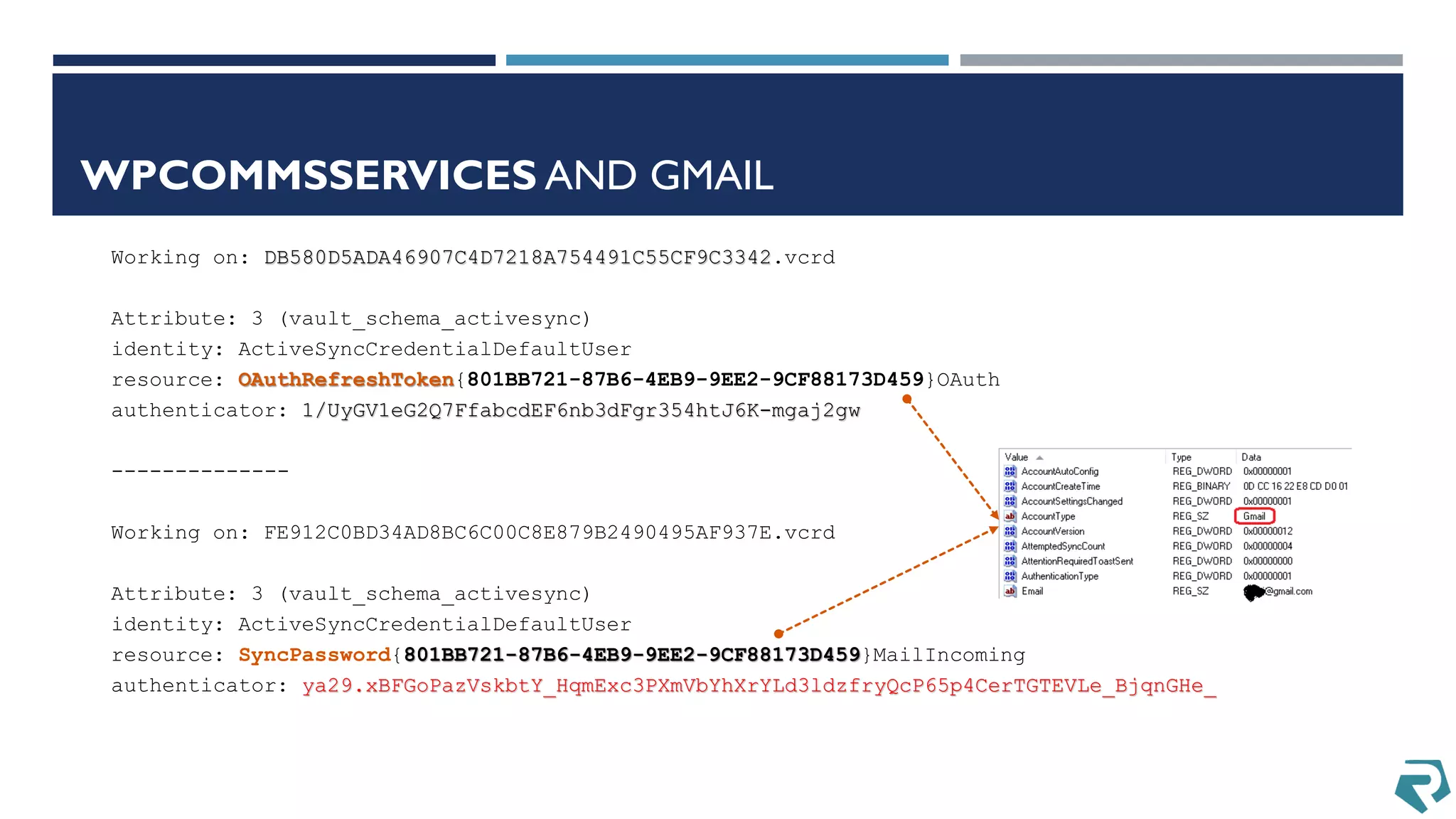
This document discusses methods for acquiring and analyzing data from Windows Phone 8 devices through physical acquisition, logical acquisition from connected devices, and analyzing application data and secrets stored on the devices. It describes partitioning the devices' storage and extracting useful data like contacts, call history, messages, and application data from databases and folders. It also details extracting decrypted user passwords from the registry and decrypting DPAPI blobs to potentially access encrypted vaults containing email passwords and tokens.







![FACEBOOK TOKENS
AuthToken in «[data]UsersDefAppsAPPDATALocalPackagesMicrosoft.MSFacebook_8wekyb3d8bbweSettings»
ApiKey in «[os] WindowsSystem32configSOFTWARE»
By using these information with (for
example)
https://github.com/pythonforfacebook/facebook-sdk
you can access online data](https://image.slidesharecdn.com/discoveringwindowsphone8artifactsandsecretsdfrwsfinal-160601131036/75/Discovering-Windows-Phone-8-Artifacts-and-Secrets-35-2048.jpg)