The document provides an overview of BGA Bilgi Güvenliği A.Ş, a Turkish cybersecurity company that offers strategic security consulting and training. It then outlines BGA's mobile application penetration testing methodology, which involves information gathering, static analysis, dynamic analysis, and examining authentication, authorization, and session management. The methodology describes steps to analyze the mobile app's permissions, network usage, data storage, APIs, libraries, and more to identify potential vulnerabilities.













































































![@BGASecurity
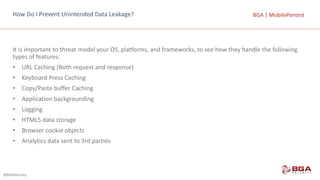
BGA | MobilePentestBGA | MobilePentestiOS Specific Best Practices:
• SQLite Injection: When designing queries for SQLite be sure that user supplied data is being passed to a
parameterized query. This can be spotted by looking for the format specifier used. In general, dangerous user
supplied data will be inserted by a “%@” instead of a proper parameterized query specifier of “?”.
• JavaScript Injection (XSS, etc): Ensure that all UIWebView calls do not execute without proper input validation.
Apply filters for dangerous JavaScript characters if possible, using a whitelist over blacklist character policy before
rendering. If possible call mobile Safari instead of rending inside of UIWebkit which has access to your
application.
• Local File Inclusion: Use input validation for NSFileManager calls.
• XML Injection: use libXML2 over NSXMLParser
• Format String Injection: Several Objective C methods are vulnerable to format string attacks:
• NSLog, [NSString stringWithFormat:], [NSString initWithFormat:], [NSMutableString appendFormat:], [NSAlert
informativeTextWithFormat:], [NSPredicate predicateWithFormat:], [NSException format:], NSRunAlertPanel.
• Do not let sources outside of your control, such as user data and messages from other applications or web
services, control any part of your format strings.
• Classic C Attacks: Objective C is a superset of C, avoid using old C functions vulnerable to injection such as: strcat,
strcpy, strncat, strncpy, sprint, vsprintf, gets, etc.](https://image.slidesharecdn.com/mobilepentest-160926194850/85/Mobile-Application-Penetration-Testing-82-320.jpg)
























































![@BGASecurity
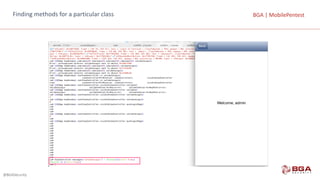
BGA | MobilePentestBGA | MobilePentestiOS Application Security – Jailbreak Detection and Evasion
Most of the jailbreak softwares install Cydia on the device after jailbreaking. Hence just a simple check for
the file path of Cydia can determine whether the device is jailbroken or not.
NSString *filePath = @"/Applications/Cydia.app";
if ([[NSFileManager defaultManager] fileExistsAtPath:filePath])
{
//Device is jailbroken
}](https://image.slidesharecdn.com/mobilepentest-160926194850/85/Mobile-Application-Penetration-Testing-141-320.jpg)
![@BGASecurity
BGA | MobilePentestBGA | MobilePentest
Not all devices that are jailbreaked have Cydia installed on them. In fact, most hackers can just change the
location of the Cydia App
+(BOOL)isJailbroken{
if ([[NSFileManager defaultManager] fileExistsAtPath:@"/Applications/Cydia.app"]){
return YES;
}else if([[NSFileManager defaultManager] fileExistsAtPath:@"/Library/MobileSubstrate/MobileSubstrate.dylib"]){
return YES;
}else if([[NSFileManager defaultManager] fileExistsAtPath:@"/bin/bash"]){
return YES;
}else if([[NSFileManager defaultManager] fileExistsAtPath:@"/usr/sbin/sshd"]){
return YES;
}else if([[NSFileManager defaultManager] fileExistsAtPath:@"/etc/apt"]){
return YES;
}
return NO;
}
iOS Application Security – Jailbreak Detection and Evasion](https://image.slidesharecdn.com/mobilepentest-160926194850/85/Mobile-Application-Penetration-Testing-142-320.jpg)
![@BGASecurity
BGA | MobilePentestBGA | MobilePentest
A good way to check for it would be to see if we can modify a file in some other location outside the
application bundle.
NSError *error;
NSString *stringToBeWritten = @"This is a test.";
[stringToBeWritten writeToFile:@"/private/jailbreak.txt" atomically:YES
encoding:NSUTF8StringEncoding error:&error];
if(error==nil){
//Device is jailbroken
return YES;
} else {
//Device is not jailbroken
[[NSFileManager defaultManager] removeItemAtPath:@"/private/jailbreak.txt" error:nil];
}
iOS Application Security – Jailbreak Detection and Evasion](https://image.slidesharecdn.com/mobilepentest-160926194850/85/Mobile-Application-Penetration-Testing-143-320.jpg)


![@BGASecurity
BGA | MobilePentestBGA | MobilePentest
• TextFields that have inputs as passwords should be used with Secure option.
• Clear the Pasteboard once the application enters background.
- (void)applicationDidEnterBackground:(UIApplication *)application
{
[UIPasteboard generalPasteboard].items = nil;
}
• The input to the URL scheme should also be validated.
- (BOOL)application:(UIApplication *)application handleOpenURL:(NSURL *)url {
//Validate input from the url
return YES;
}
• A developer should make sure that the content he loads into the UIWebview is not malicious
iOS Application Security – Secure Coding Practices for iOS
Development](https://image.slidesharecdn.com/mobilepentest-160926194850/85/Mobile-Application-Penetration-Testing-146-320.jpg)








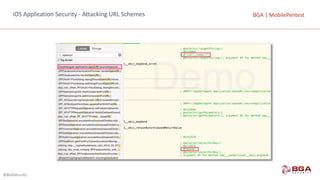
![@BGASecurity
BGA | MobilePentestBGA | MobilePentest
function tryPrintIvars(a){ var x={}; for(i in *a){ try{ x[i] = (*a)[i]; }
catch(e){} } return x; }
iOS Application Security – Sensitive Information in Memory](https://image.slidesharecdn.com/mobilepentest-160926194850/85/Mobile-Application-Penetration-Testing-156-320.jpg)