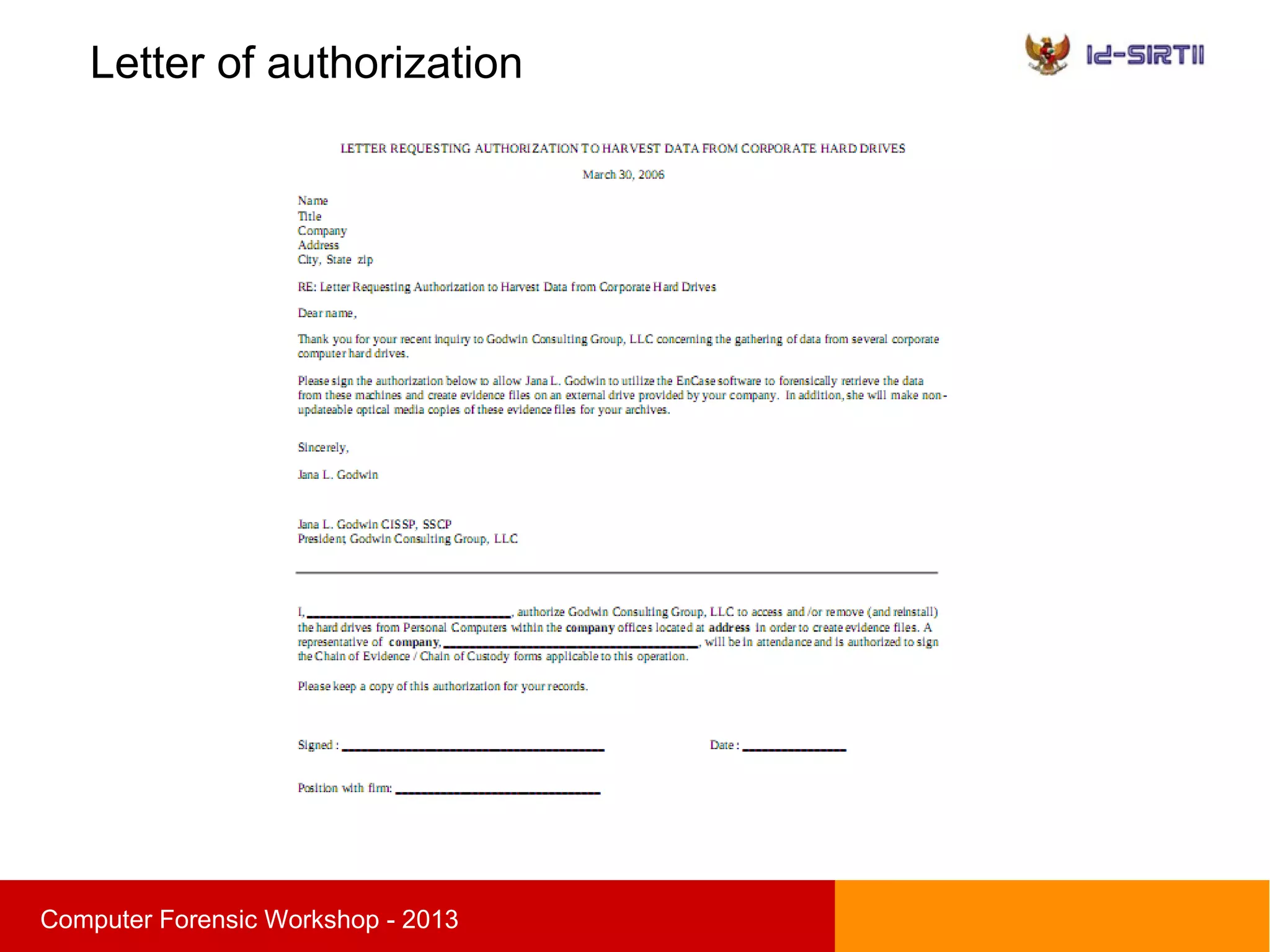
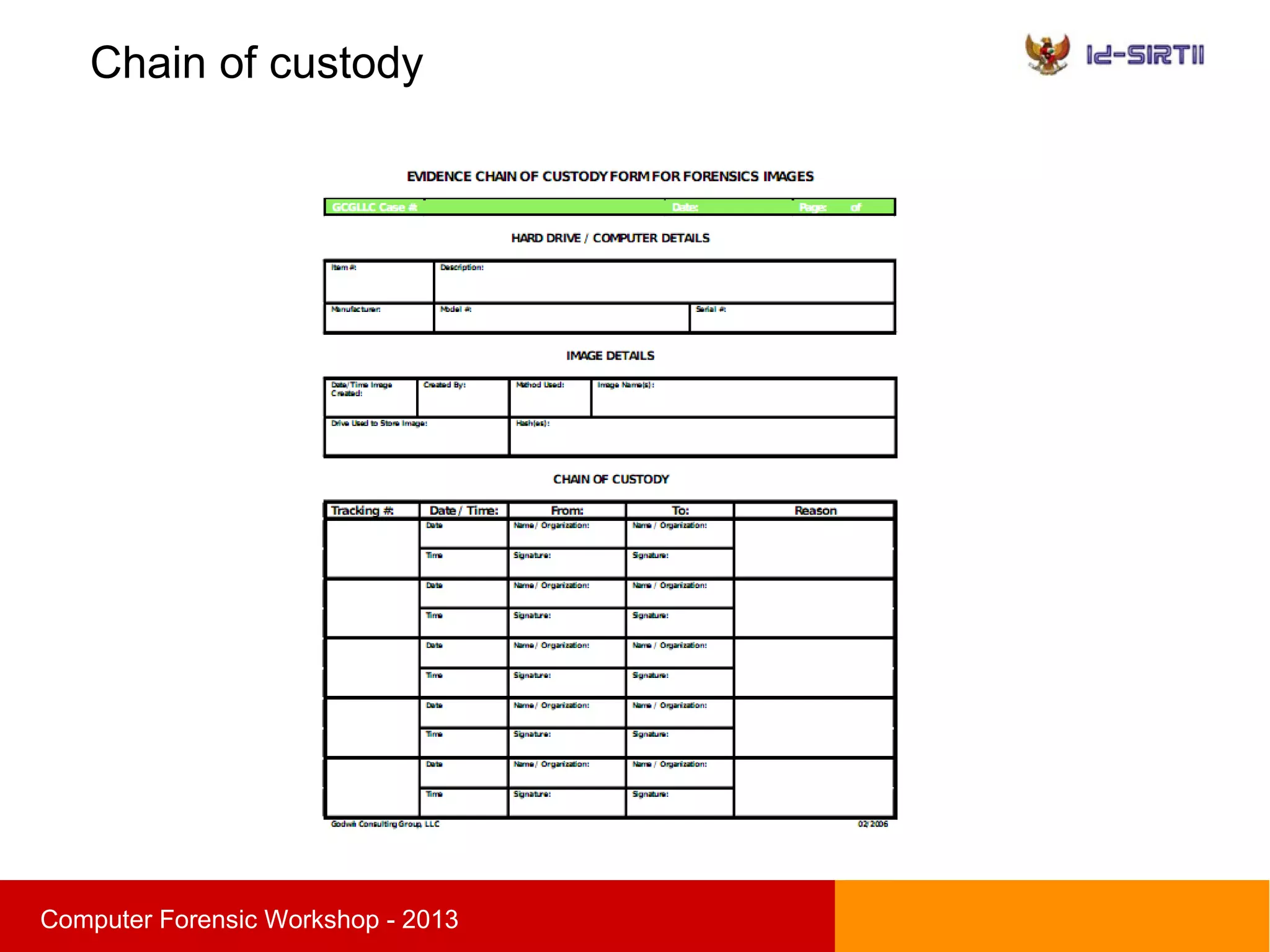
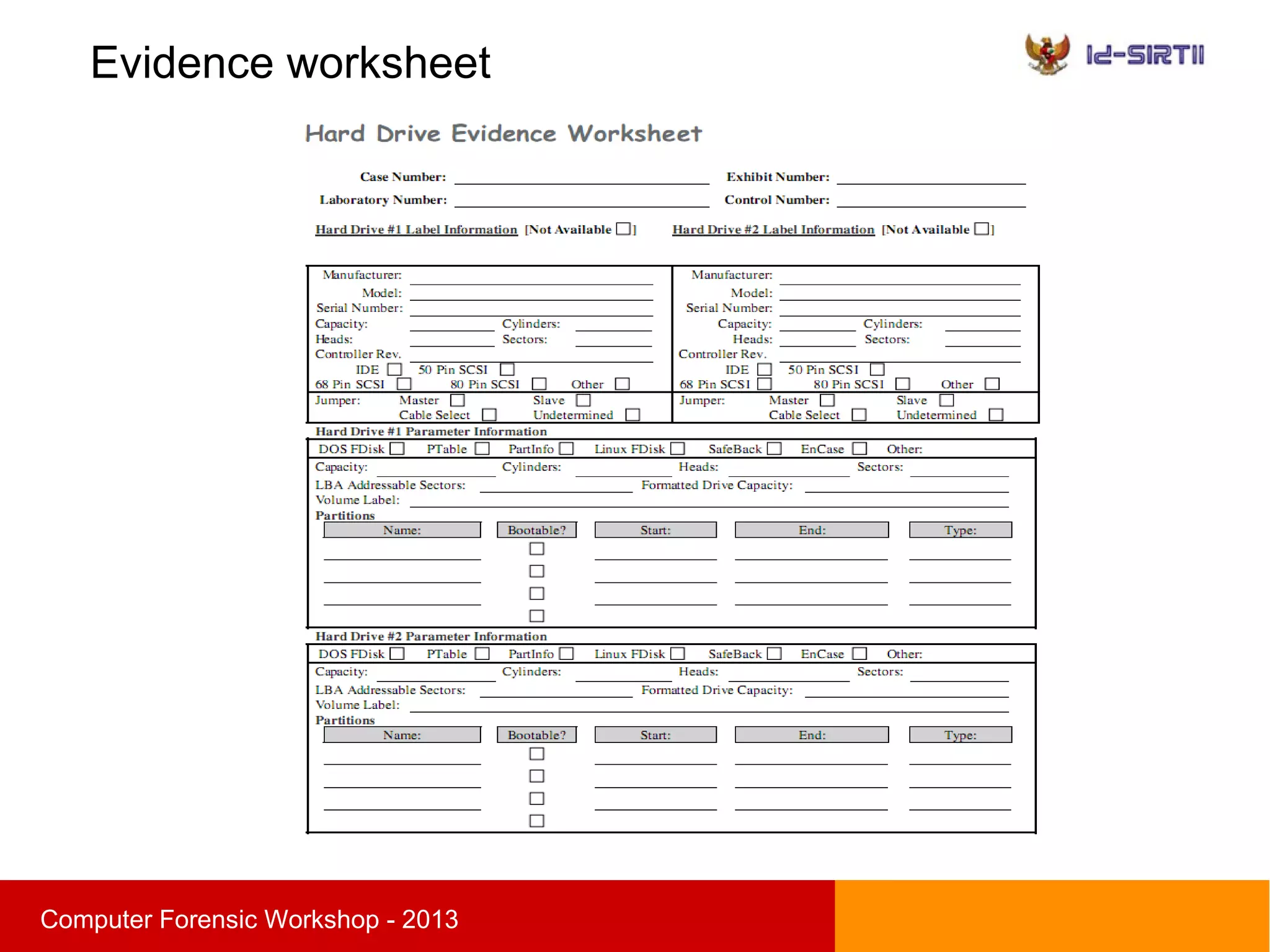
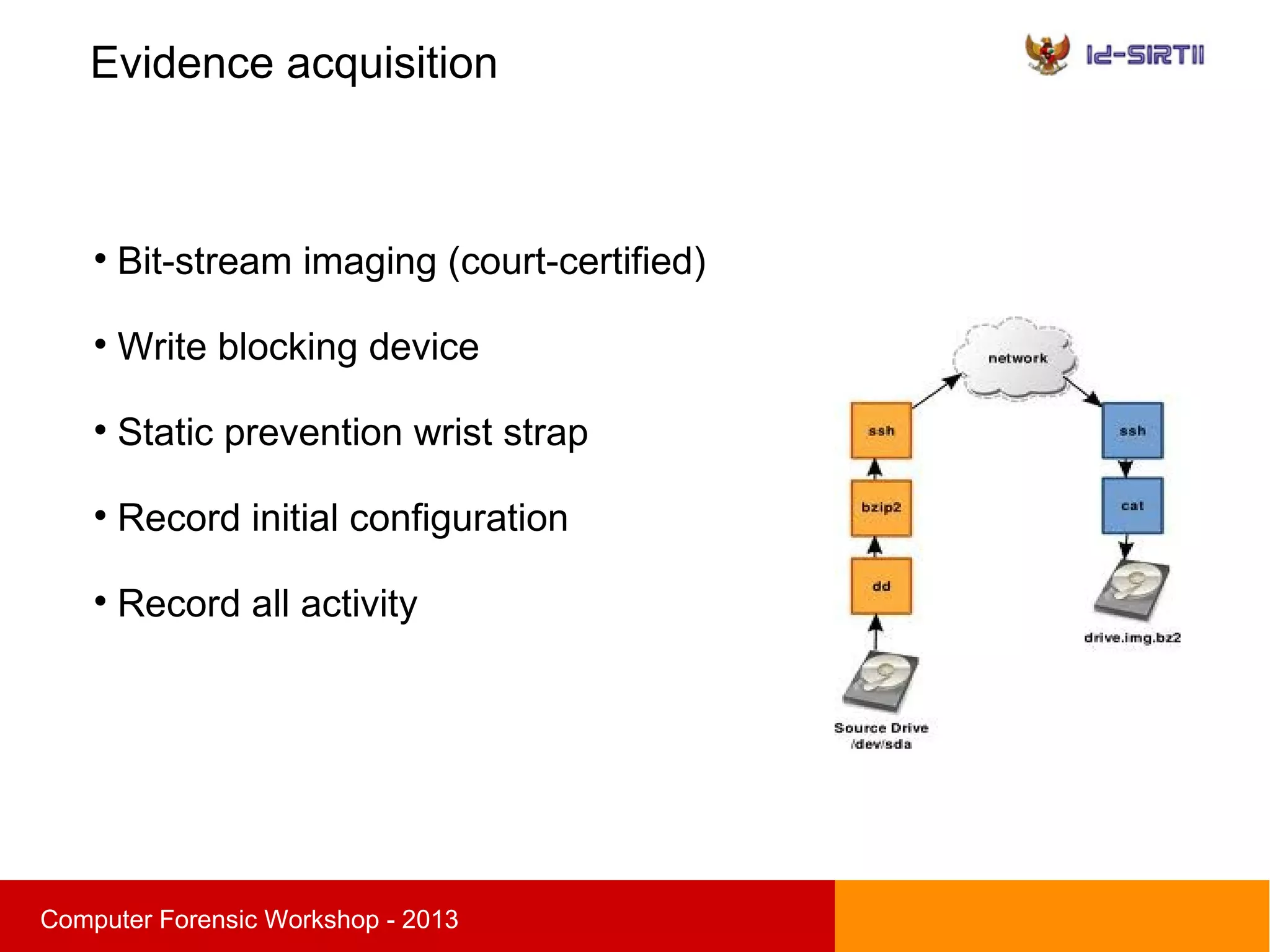
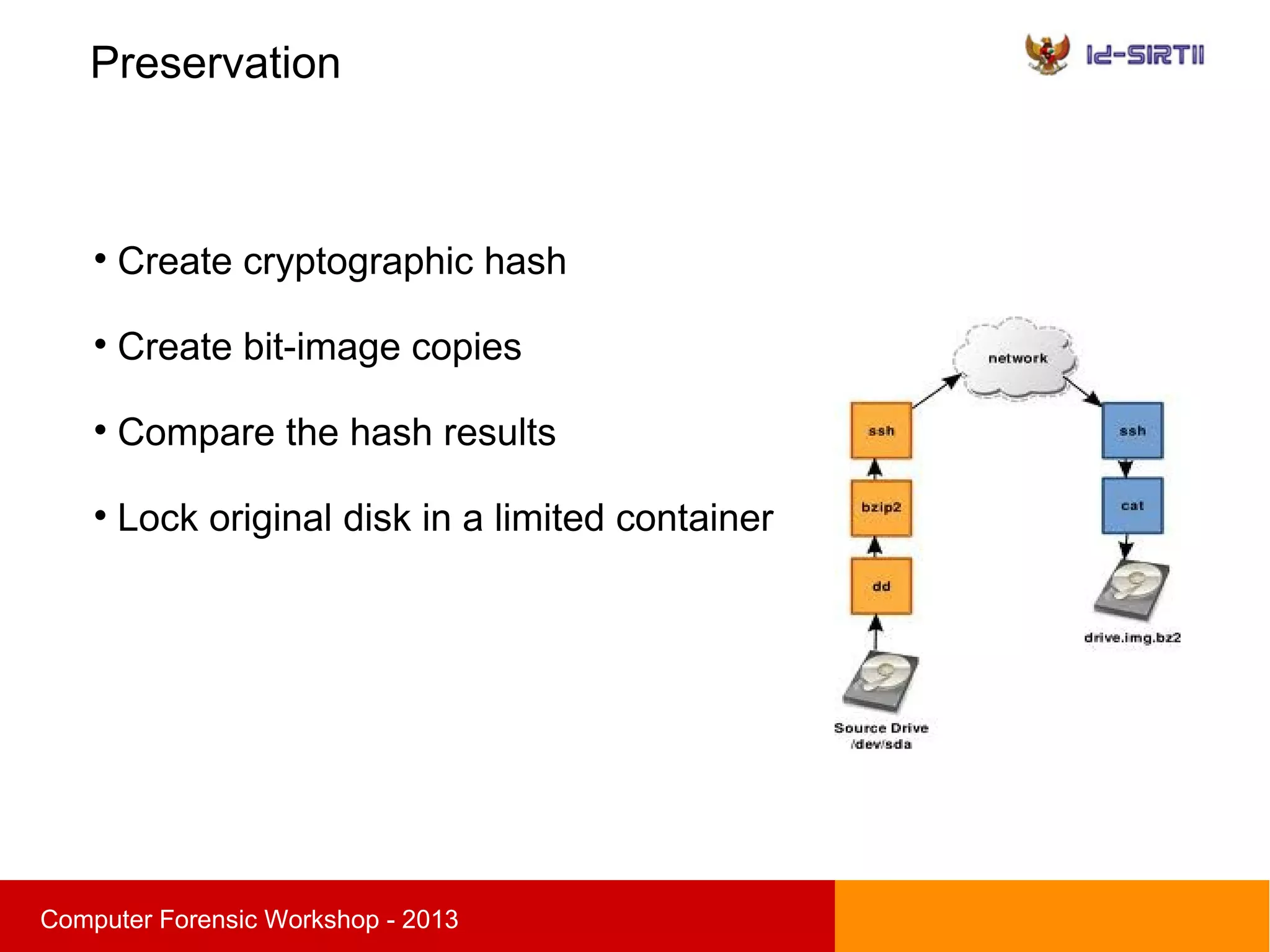
This document summarizes a computer forensic workshop presented by Ahmad Zaid Zam Zami. The workshop covered digital forensic procedures, including evidence acquisition through hardware, live CD, and live imaging methods. It also discussed preserving evidence through cryptographic hashing and creating bit-stream image copies. The analysis process examines forensic copies to build timelines, search media, and recover deleted data within the scope of the investigation.