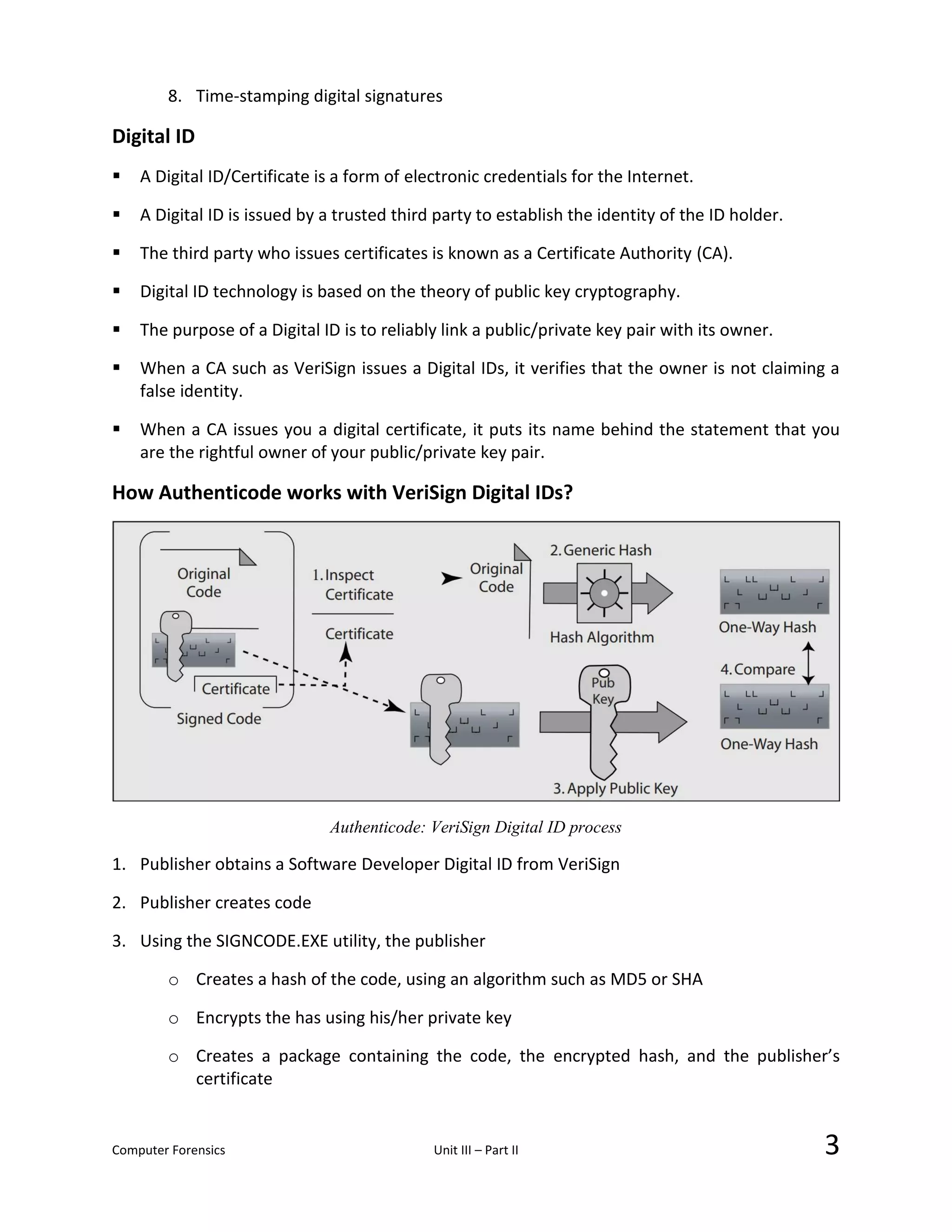
The document discusses digital image verification and authentication protocols used in computer forensics investigations. It describes how investigators can copy all information from a suspect computer system without altering the original. The copy must be authenticated to prove it has not been modified. This involves generating a cryptographic hash of the copy and storing it in a "safe box". All safe boxes for a case are grouped in a "vault" with a hash to verify integrity. Keys and procedures are described for verifying that a copy was properly authenticated and can be traced to a specific computer at a given time. The goal is to allow investigators to securely collect digital evidence while respecting the rights of innocent parties.