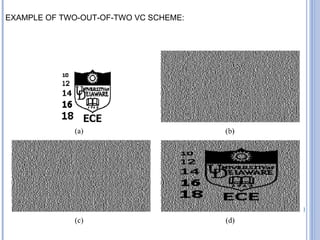
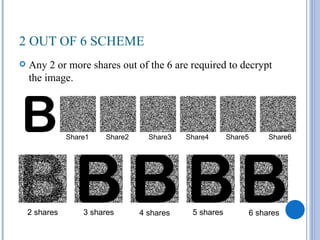
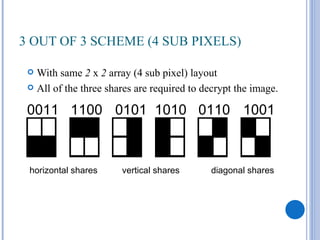
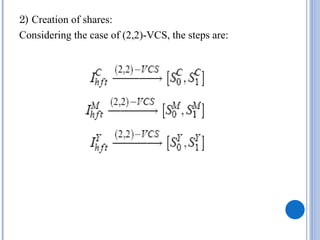
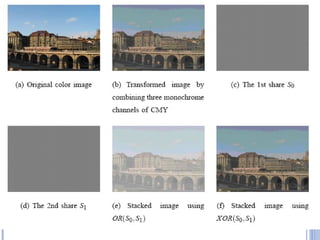
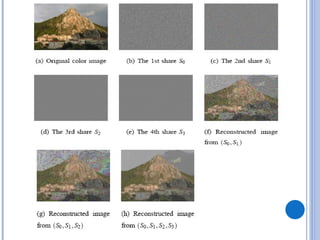
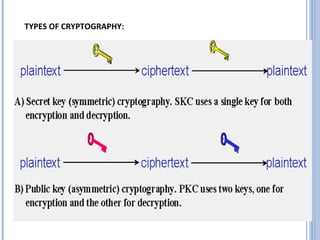
This document provides an overview of visual cryptography, including its introduction, types, implementation methods, advantages, disadvantages, and applications. Visual cryptography allows visual information like pictures and text to be encrypted in a way that can be decrypted by the human visual system. It was pioneered in 1994 and works by splitting an image into shares such that stacking a sufficient number of shares reveals the original image. The document discusses various visual cryptography schemes and their properties.







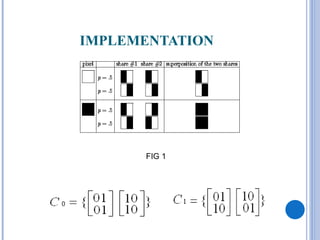
![BASIS MATRICES
The two matrices S0,S1 are called basis matrices,
if the two collections C0,C1 as defines in [1] are
obtained by rearranging the columns of S0,S1
satisfy the following condition:
the row vectors V0,V1 obtained by performing
OR operation on rows i1,i2,…..iv of S0,S1
respectively, satisfy
ω(V0) ≤ tX - α(m). m and ω(V1) ≥ tX](https://image.slidesharecdn.com/visualcryptography1-120502010920-phpapp02/85/Visual-cryptography1-9-320.jpg)