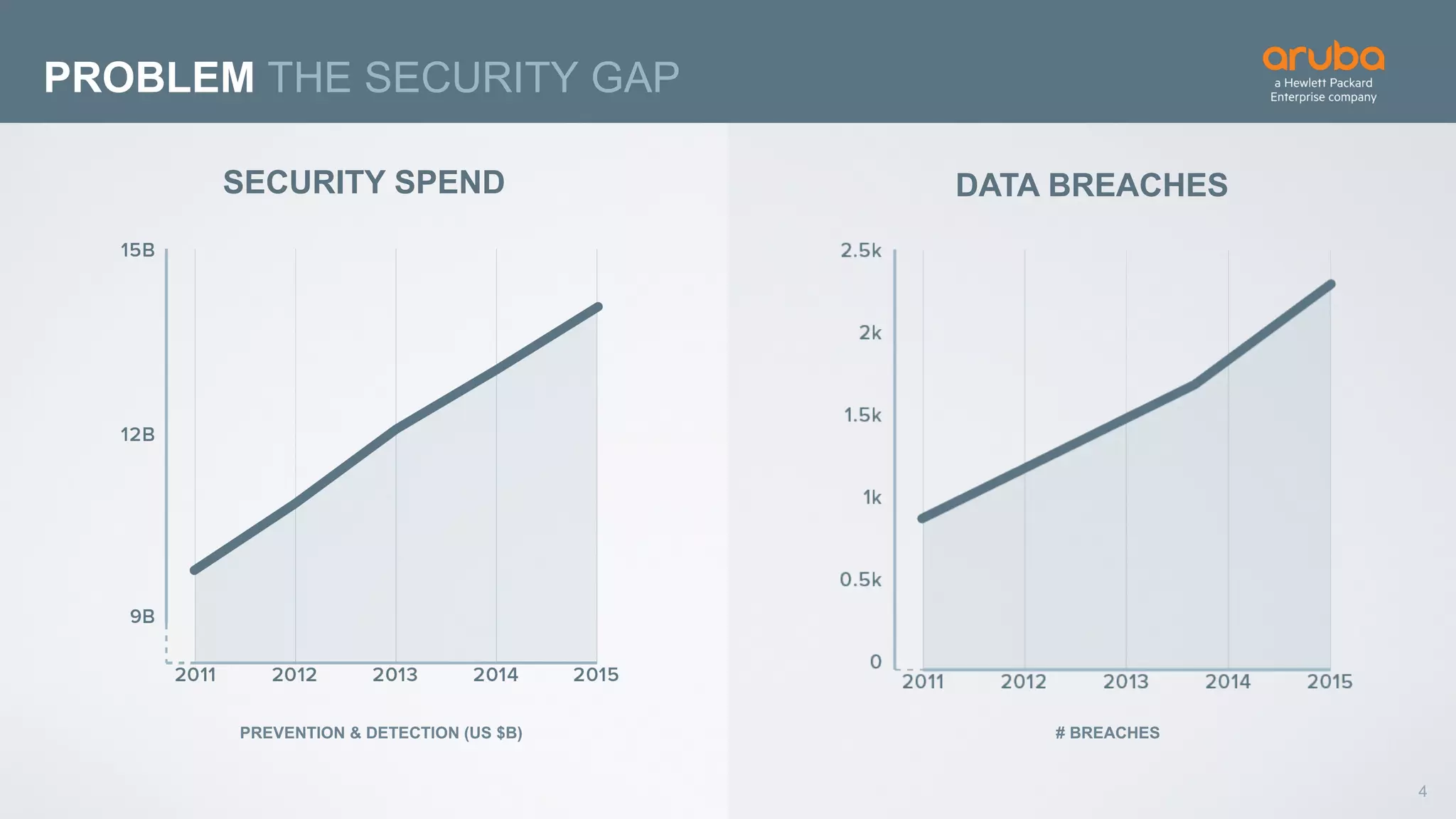
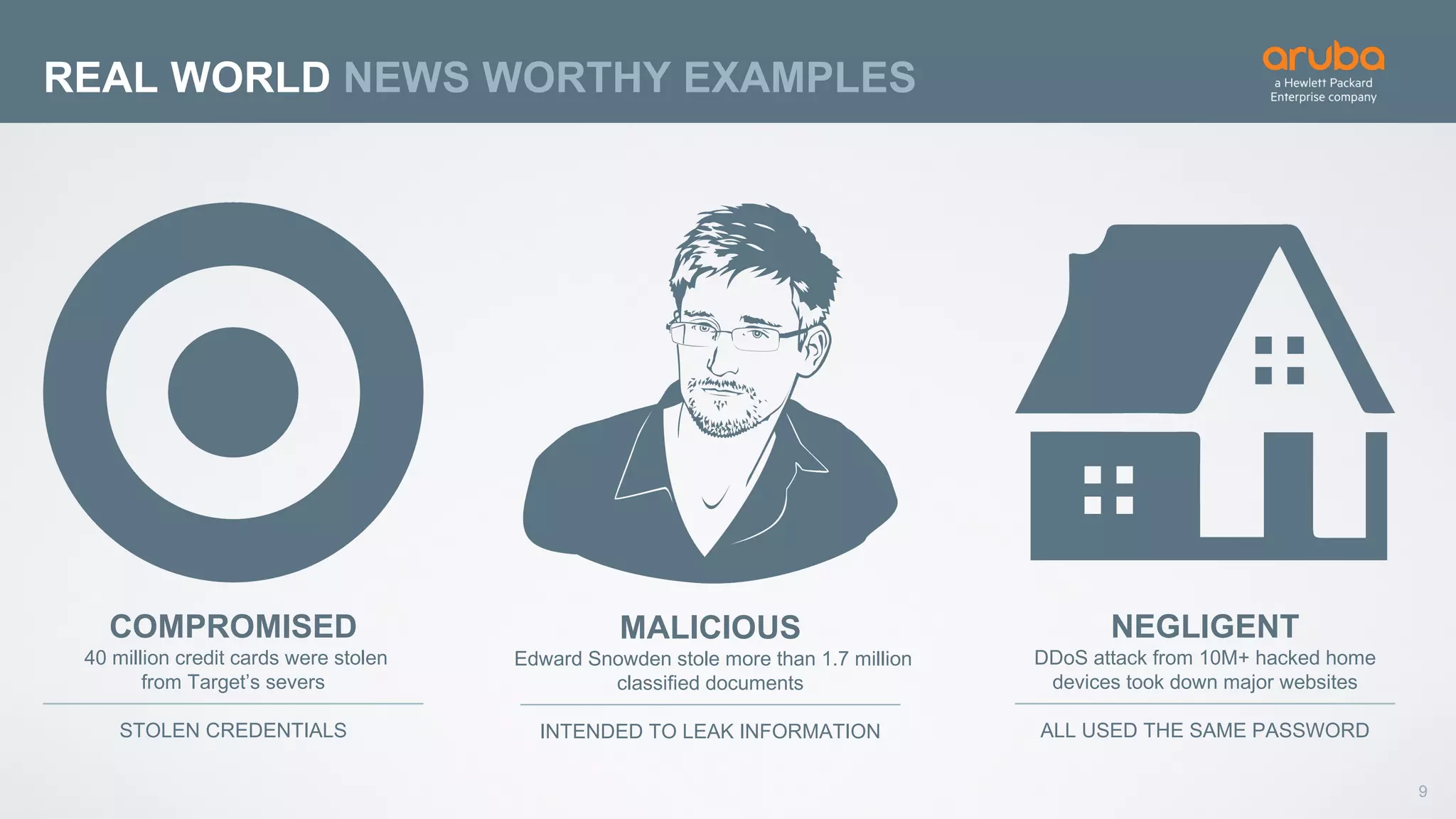
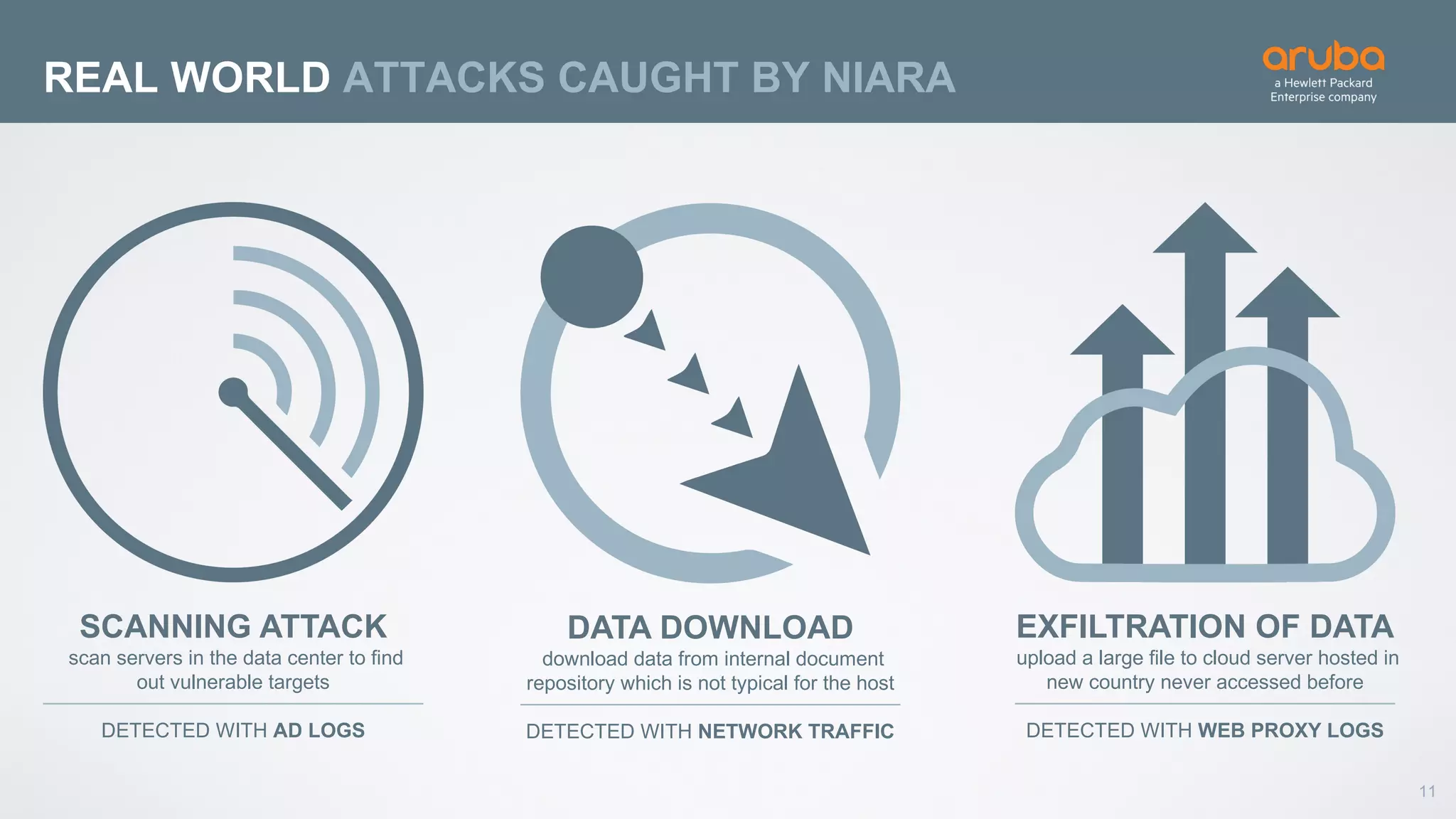
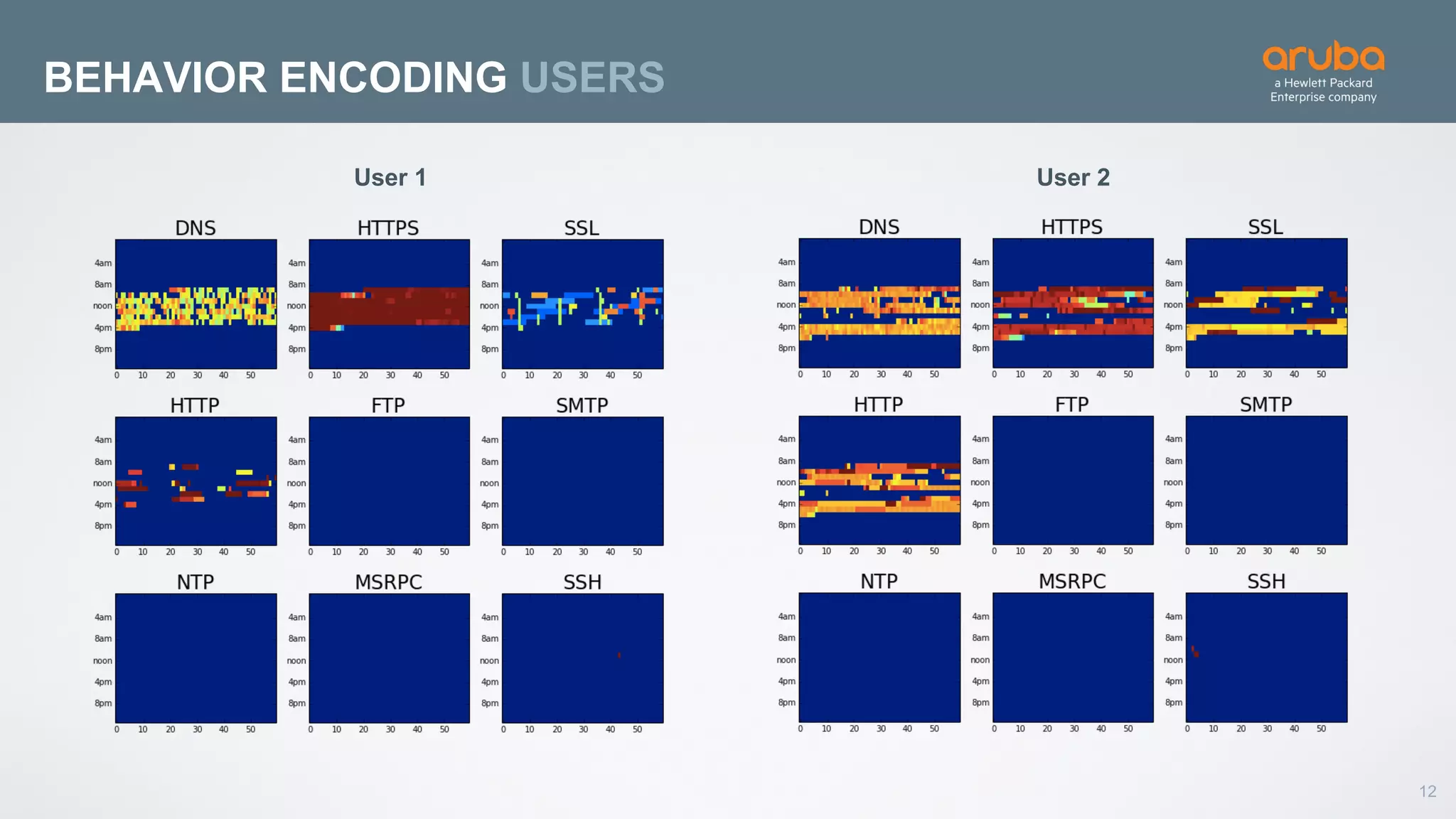
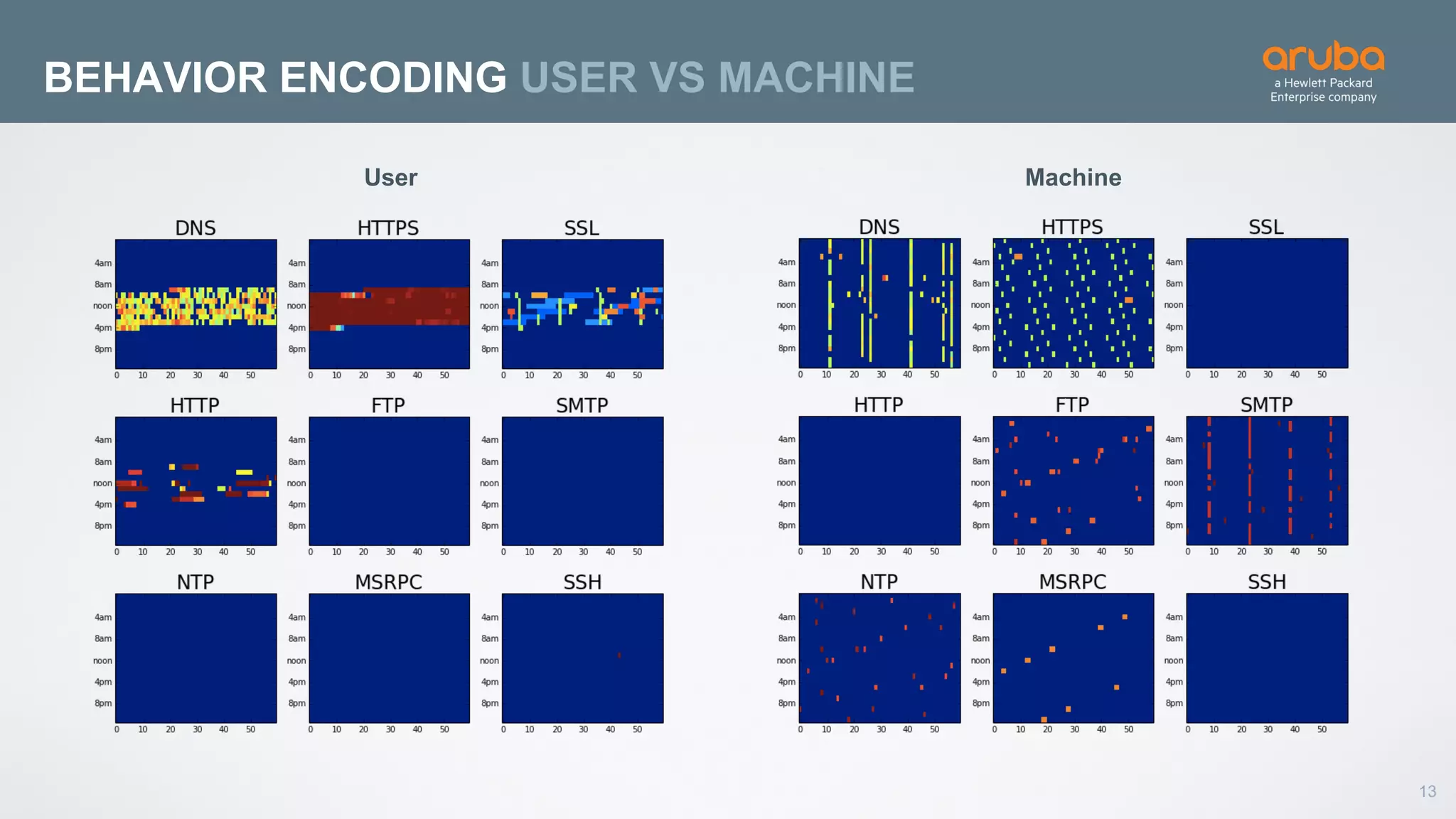
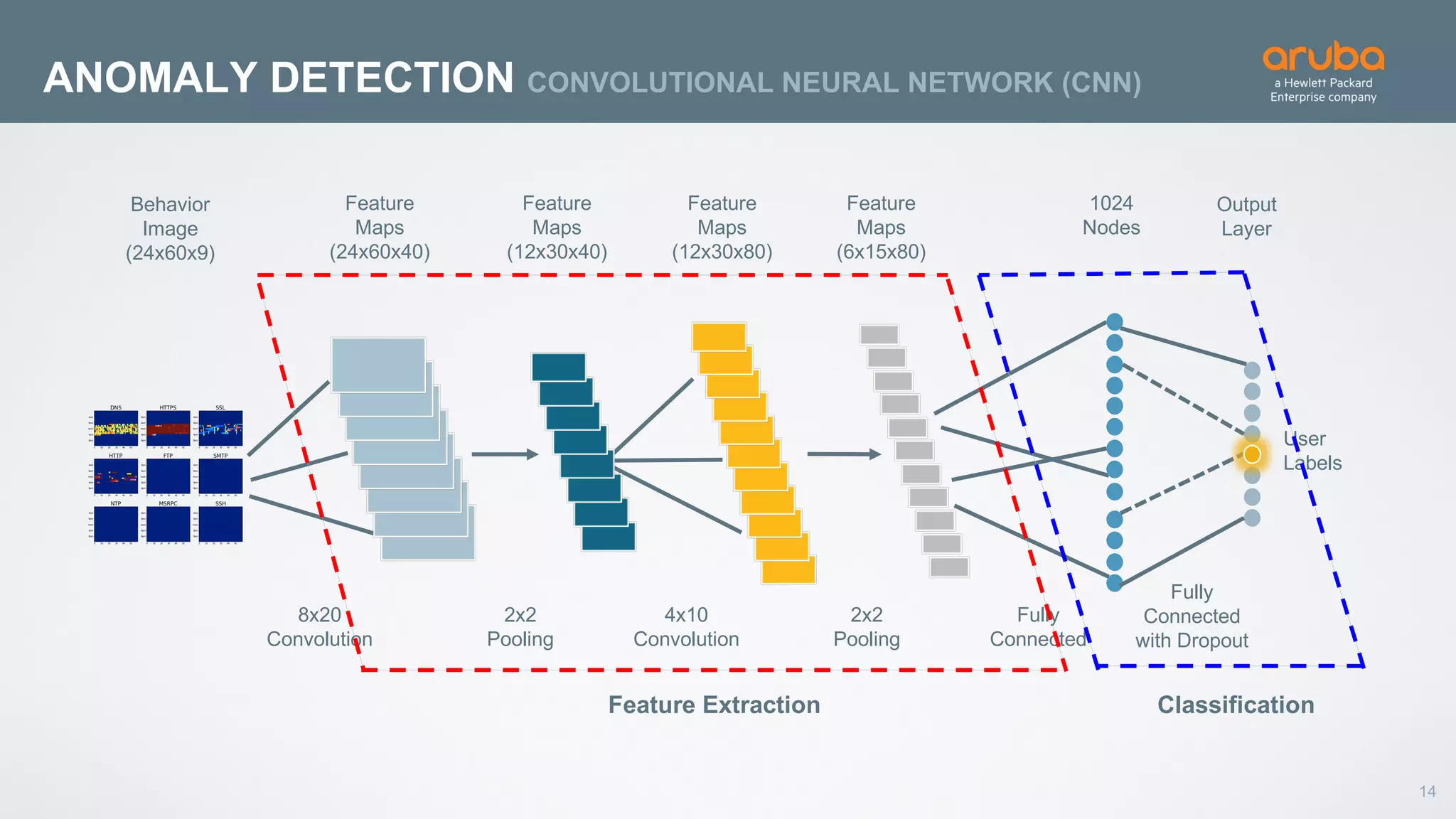
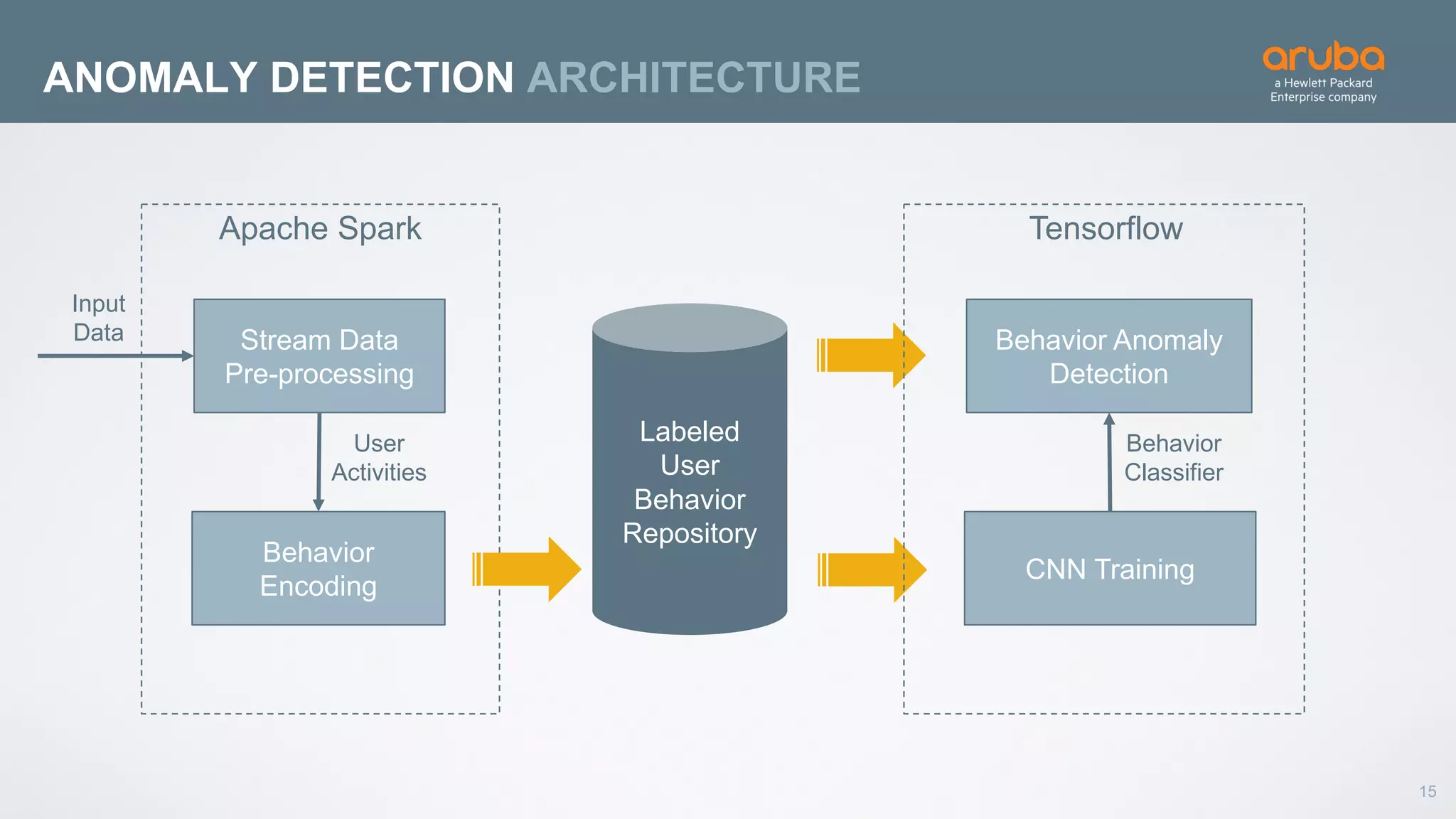
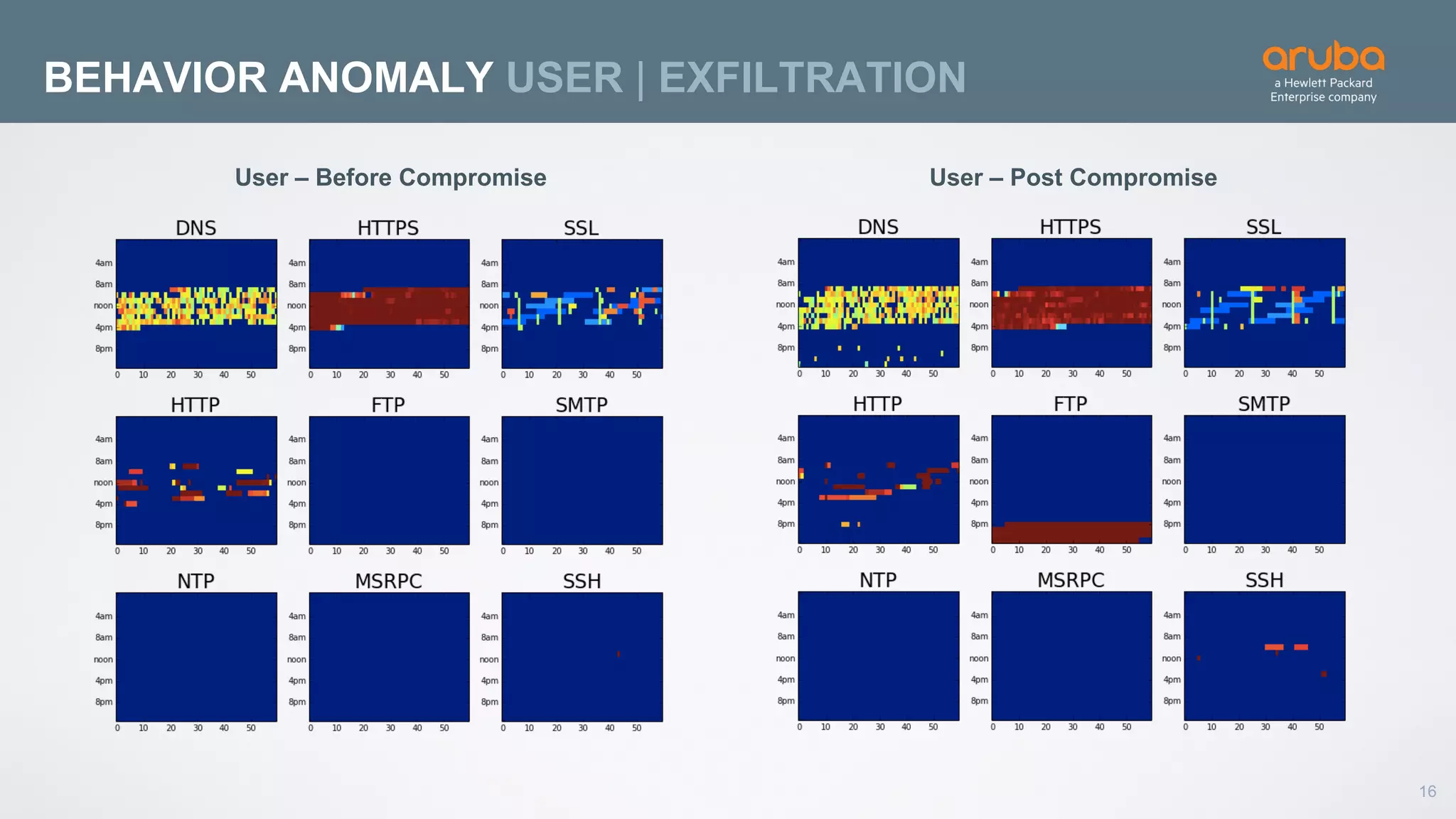
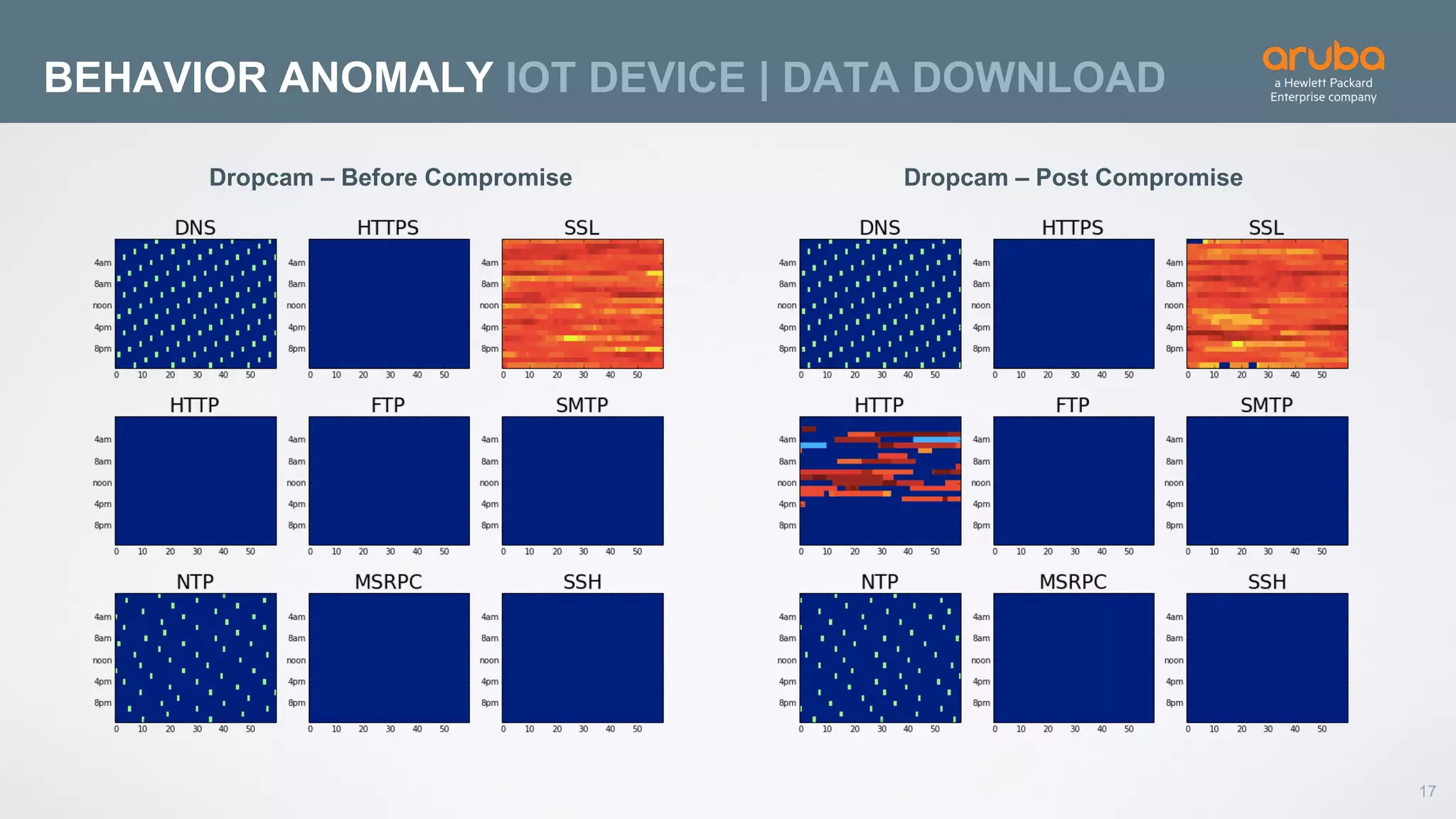
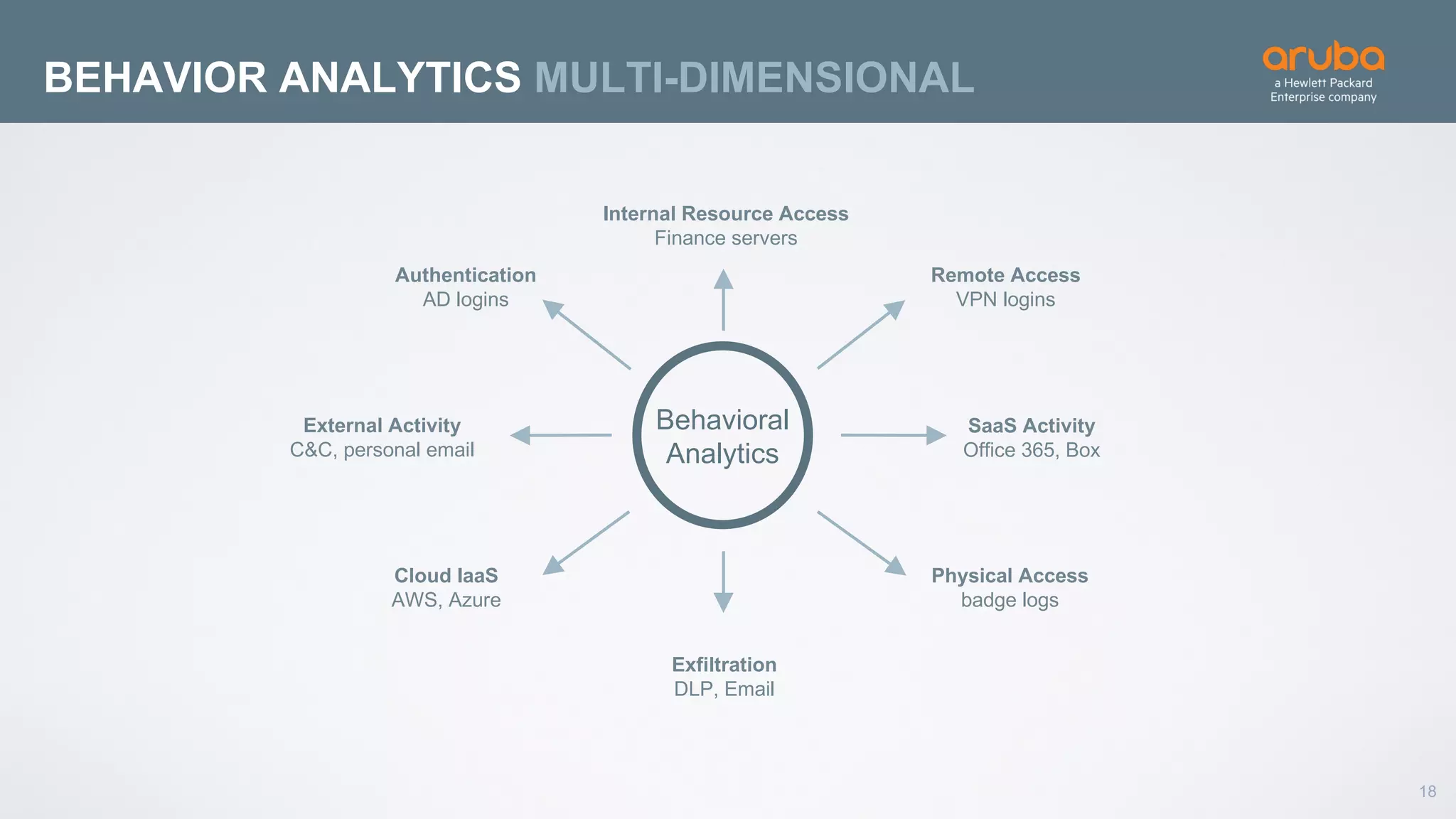
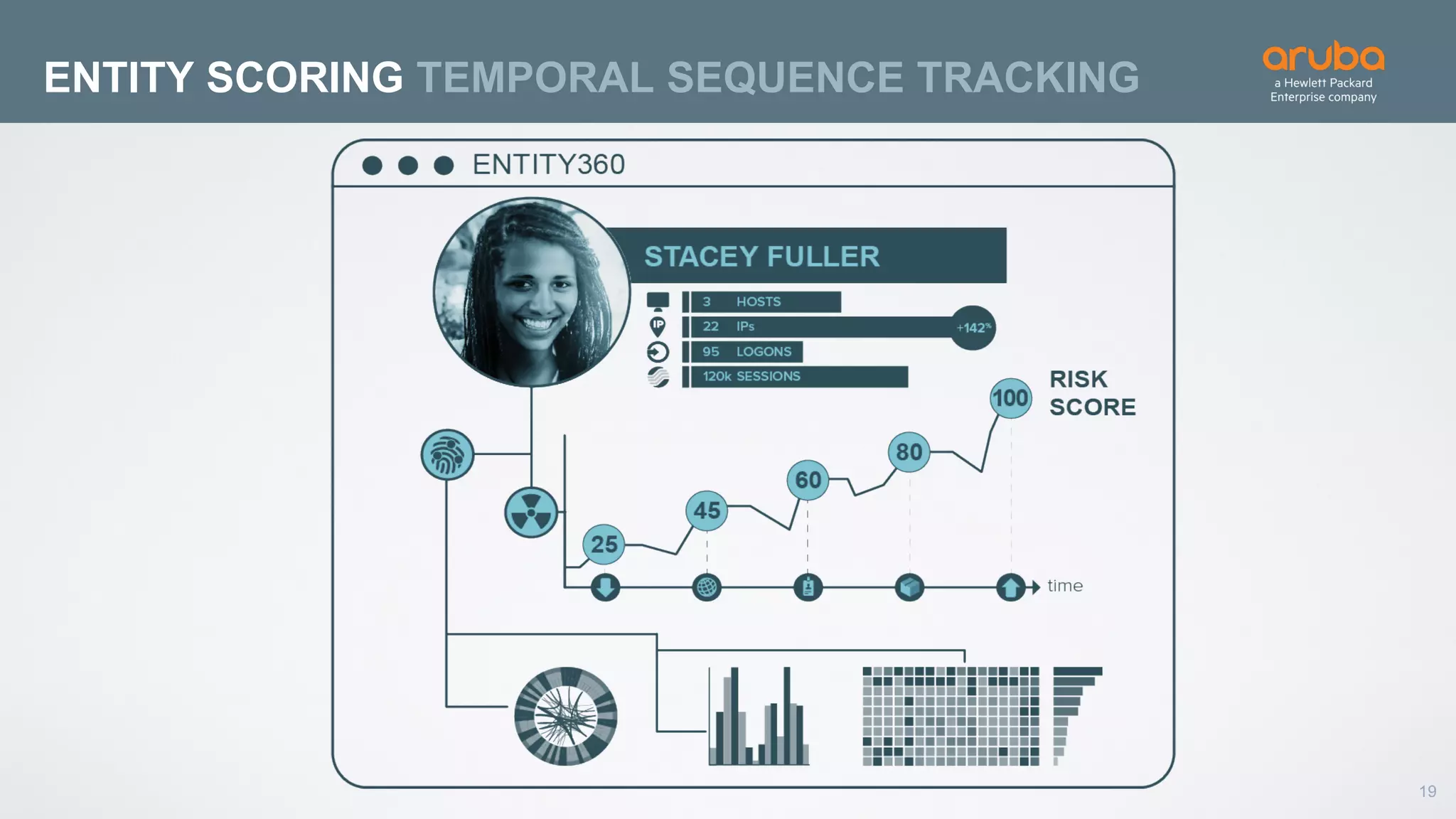
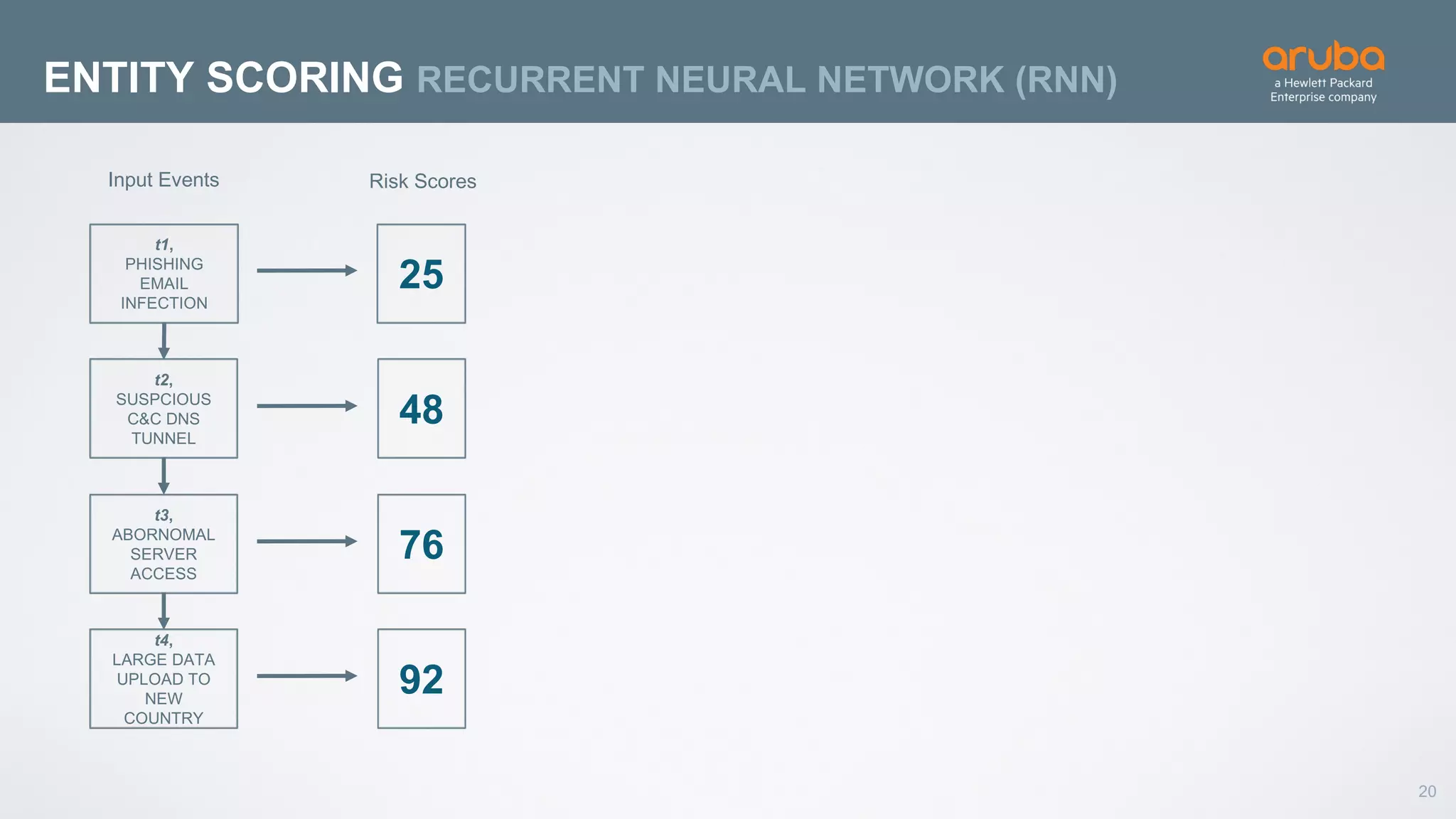
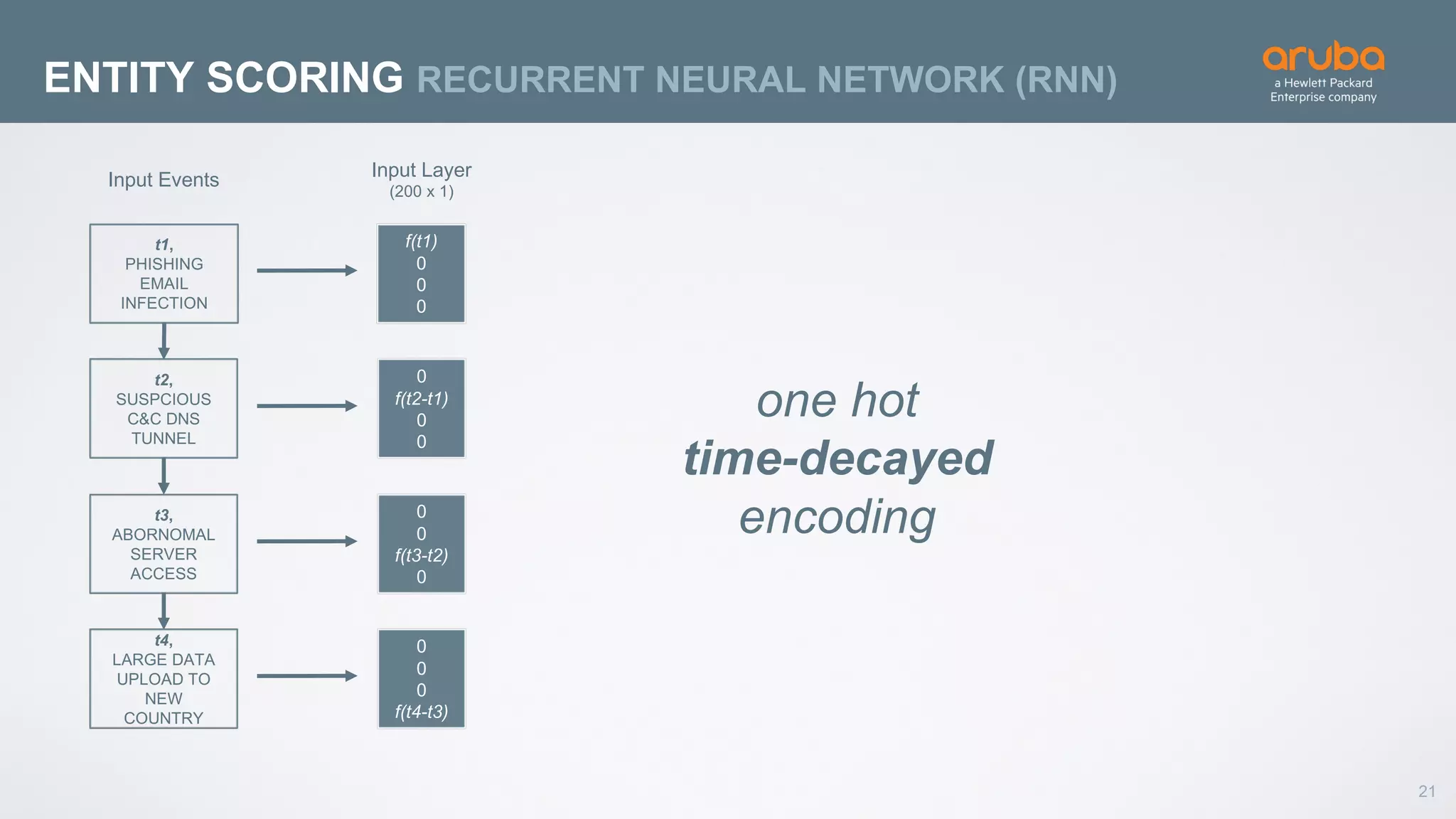
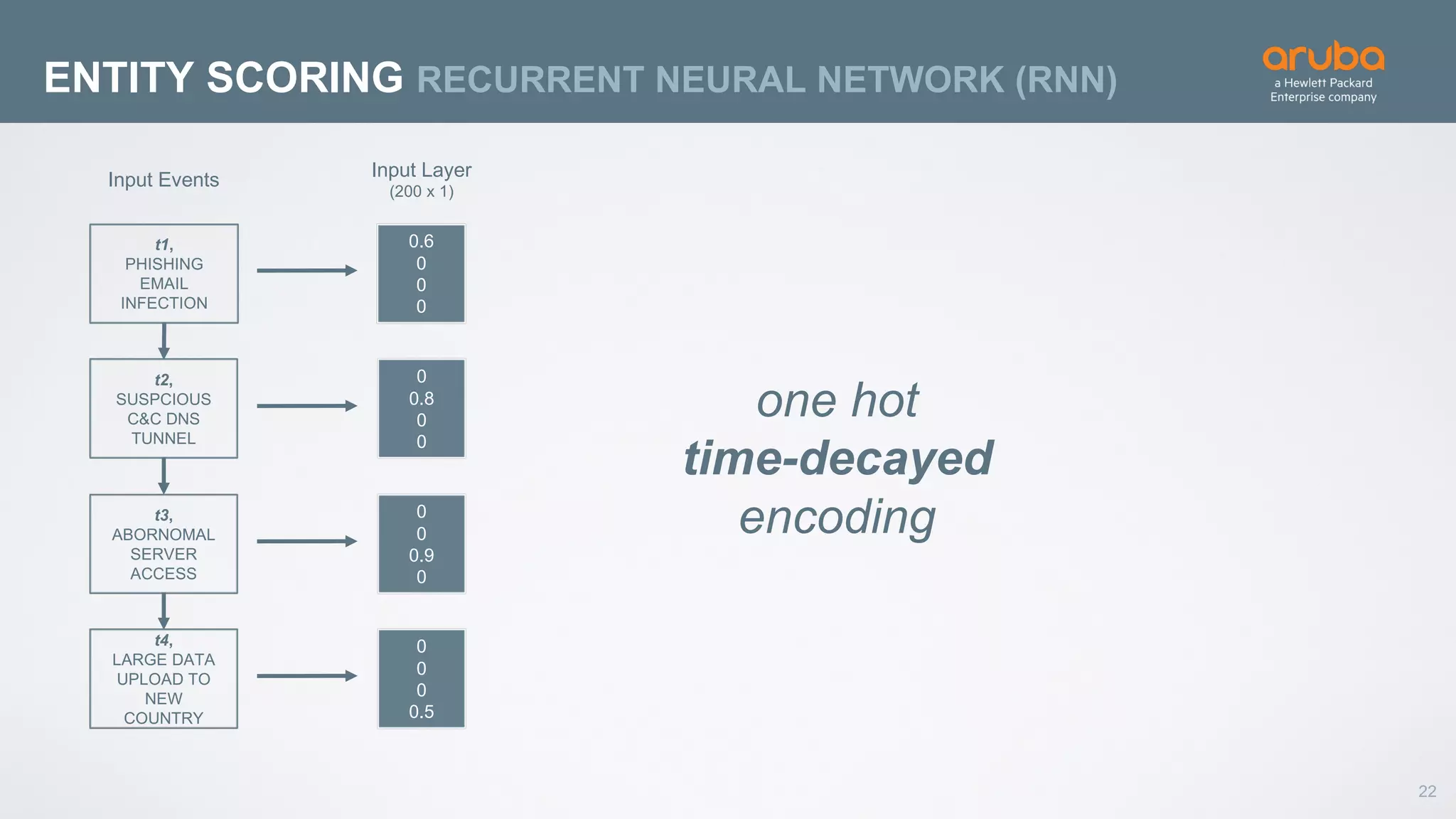
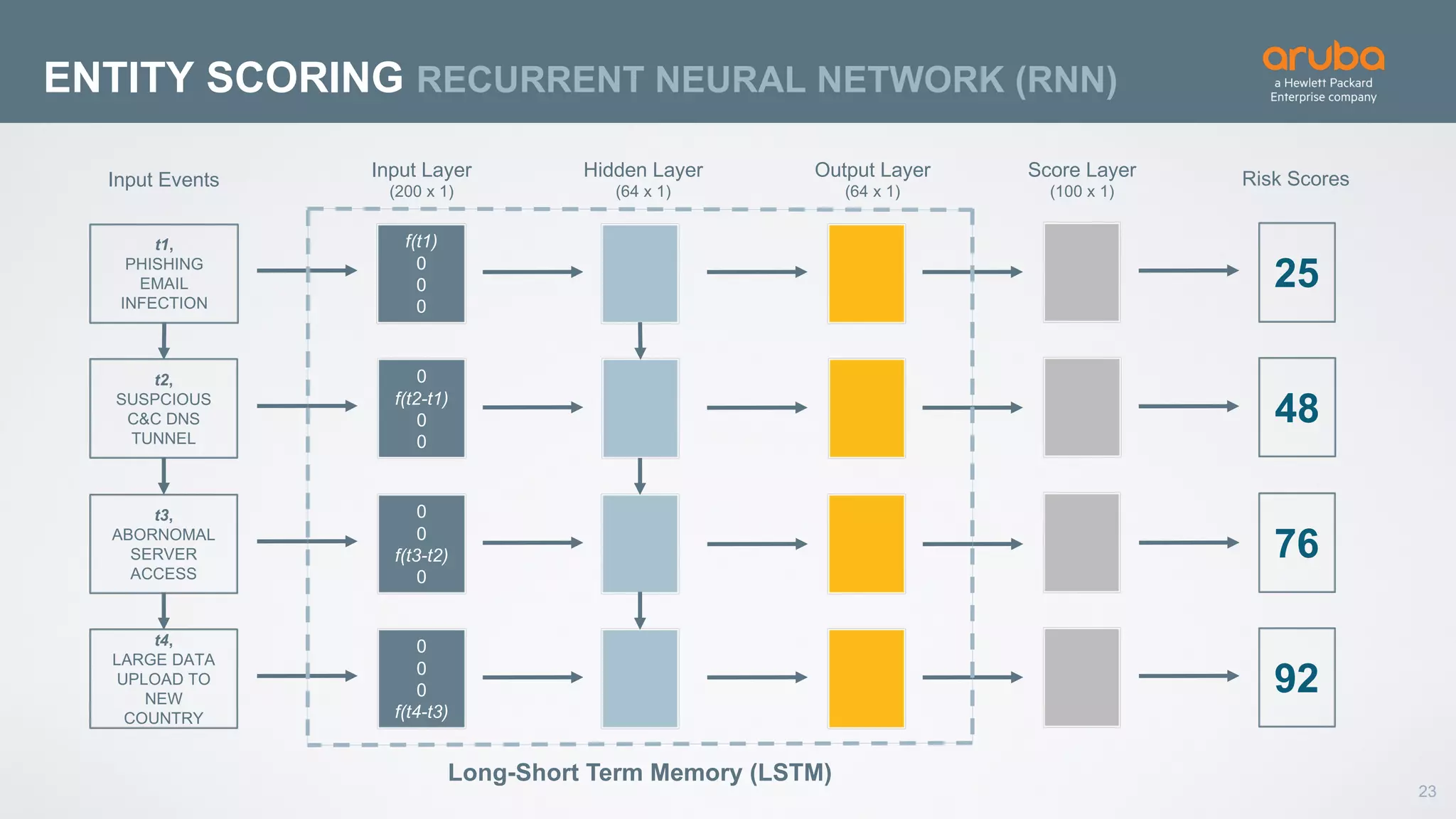
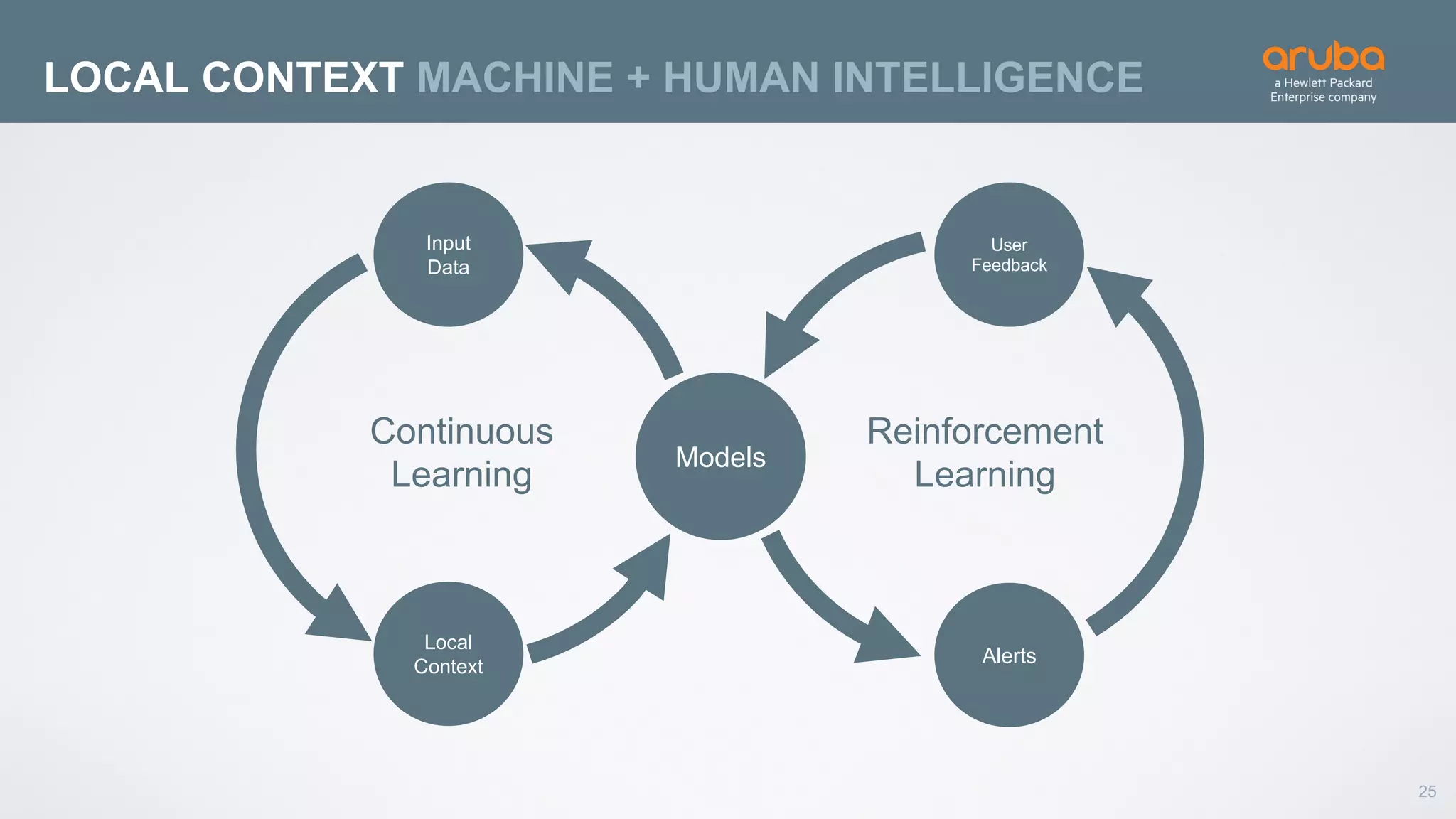
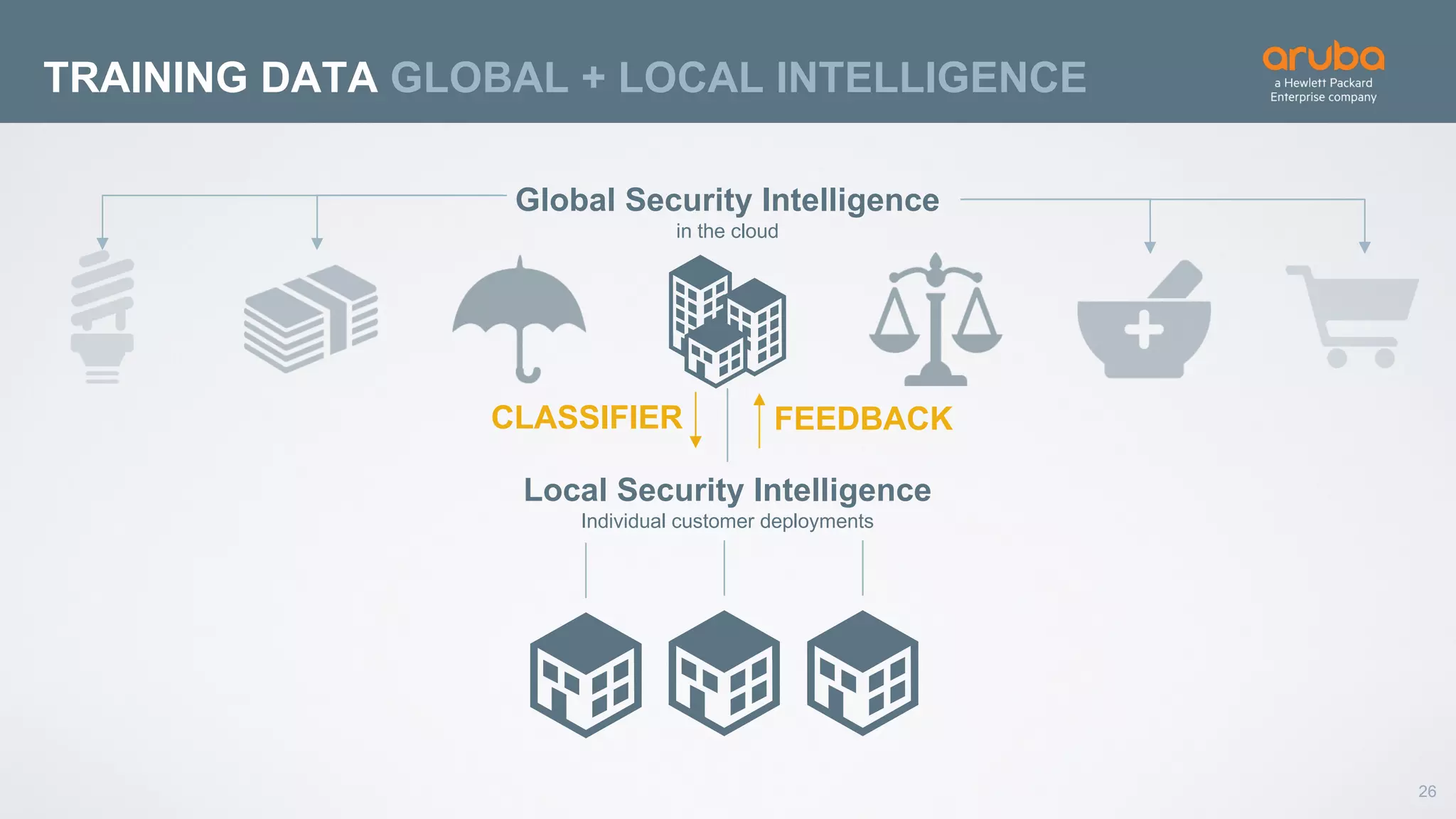
This document discusses using deep learning for user and entity behavior analytics (UEBA) security. It provides an example of how deep learning can be used to detect anomalies in user and entity behaviors to identify security threats like data exfiltration and malware infections. The document outlines how behavioral data from different sources can be encoded and analyzed using techniques like convolutional neural networks (CNNs) and recurrent neural networks (RNNs) to learn normal behavior patterns and detect anomalies. It also discusses how a UEBA solution combines machine learning models with local context and continuous feedback to improve detection of new threats.