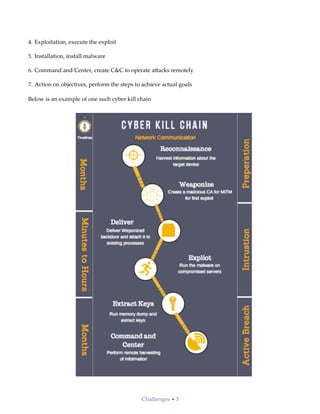
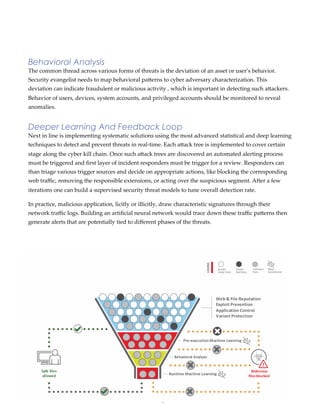
The document discusses the increasing challenges in cybersecurity, highlighting the projected costs of cybercrime and the complexity of identifying cyber threats due to evolving attack methods and the collaboration of hackers worldwide. It emphasizes the need for organizations to build a proactive security strategy involving adversary profiling, behavioral analysis, and advanced machine learning techniques to detect and respond to threats effectively. As cyber threats evolve, future cybersecurity solutions must adopt more intelligent models with self-learning capabilities to safeguard a broader attack surface including applications and IoT.