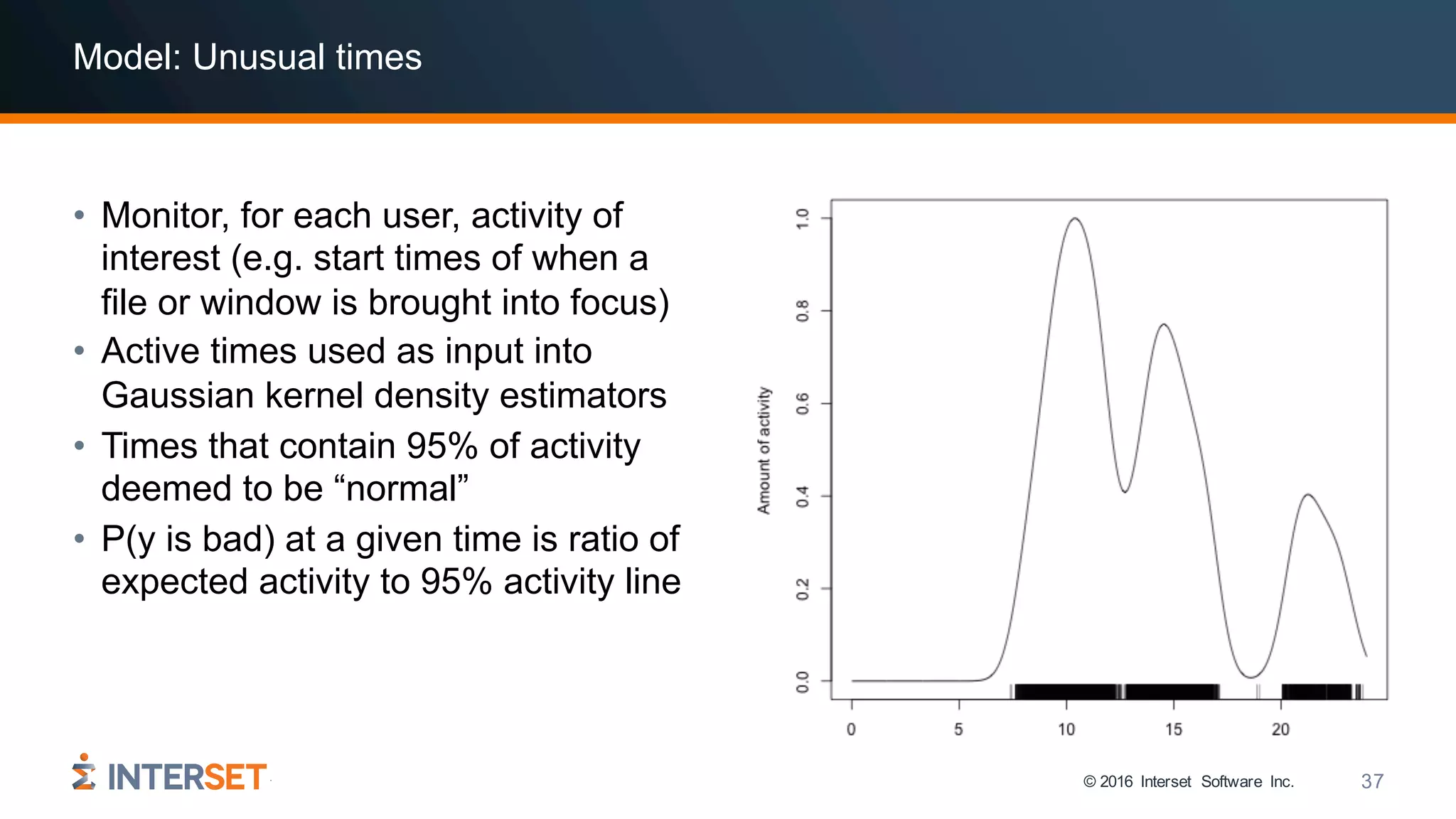
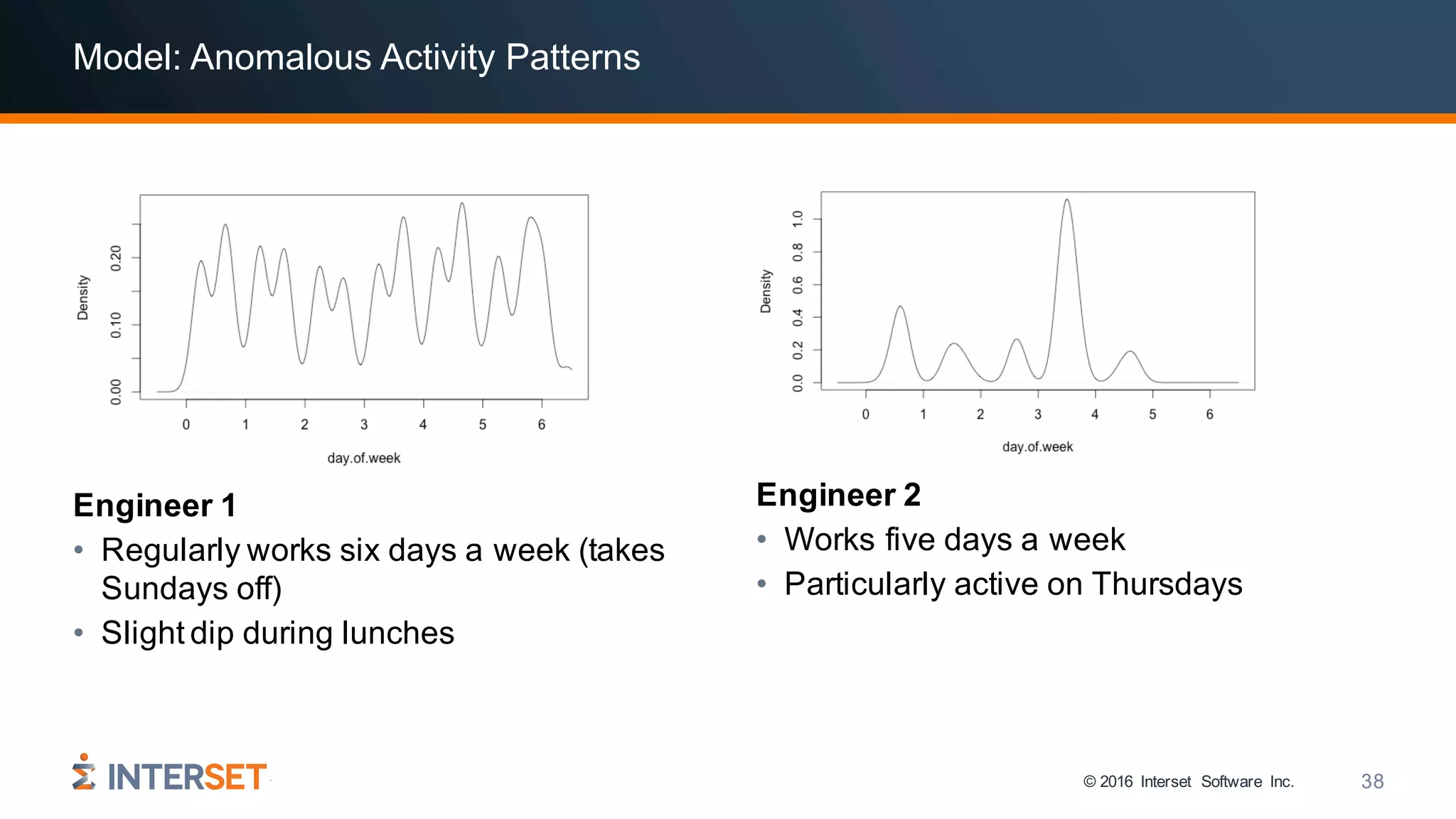
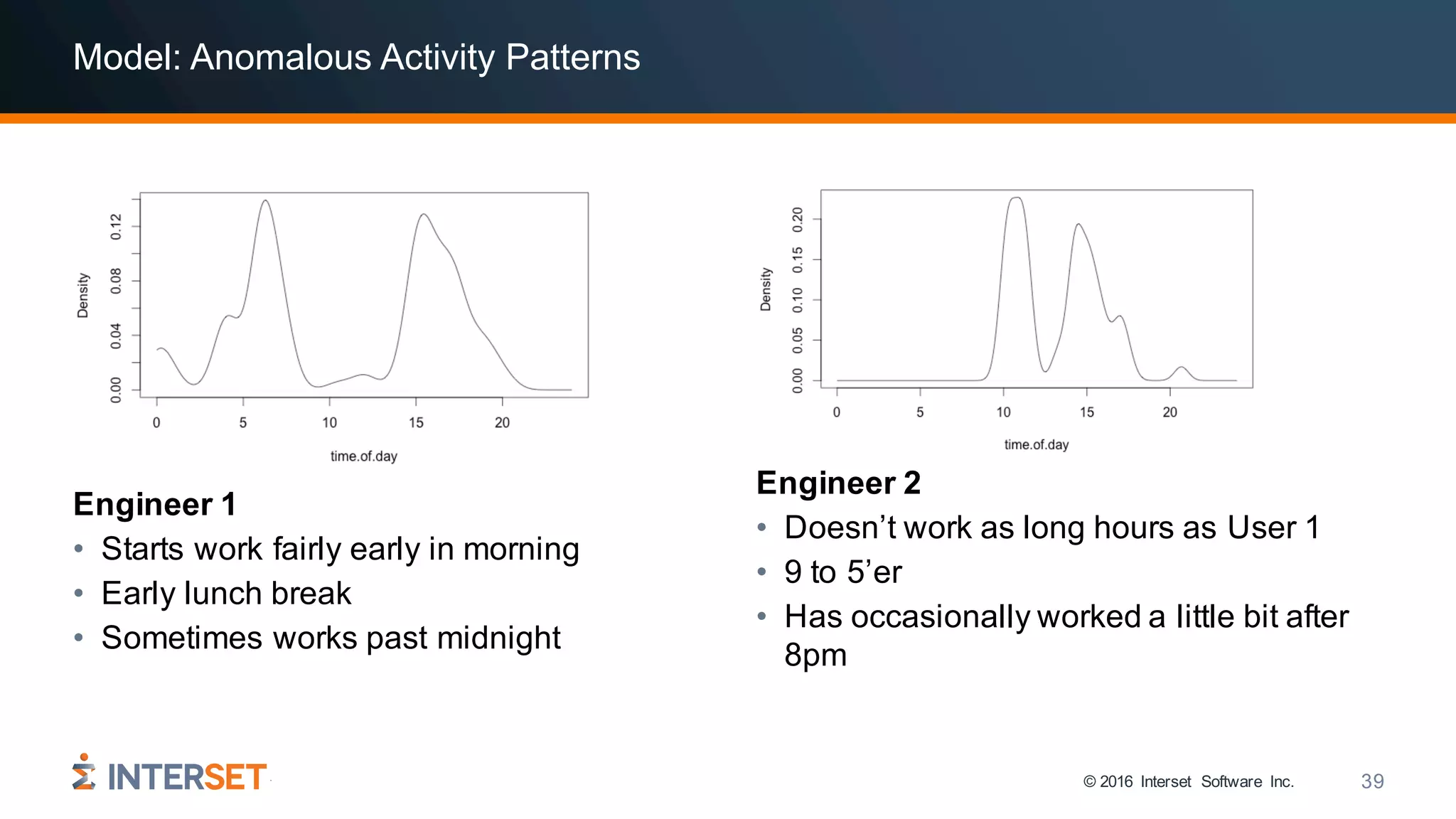
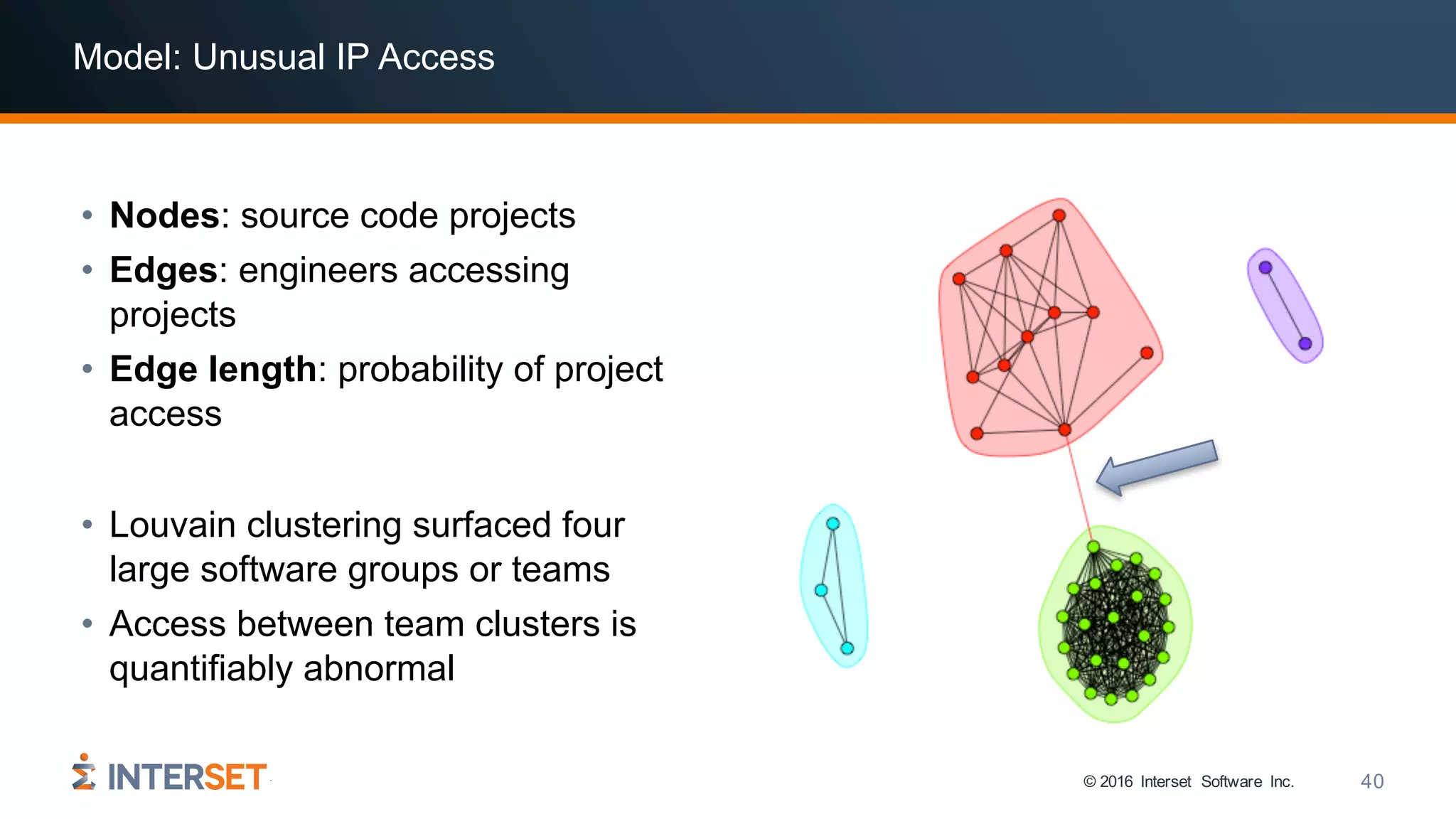
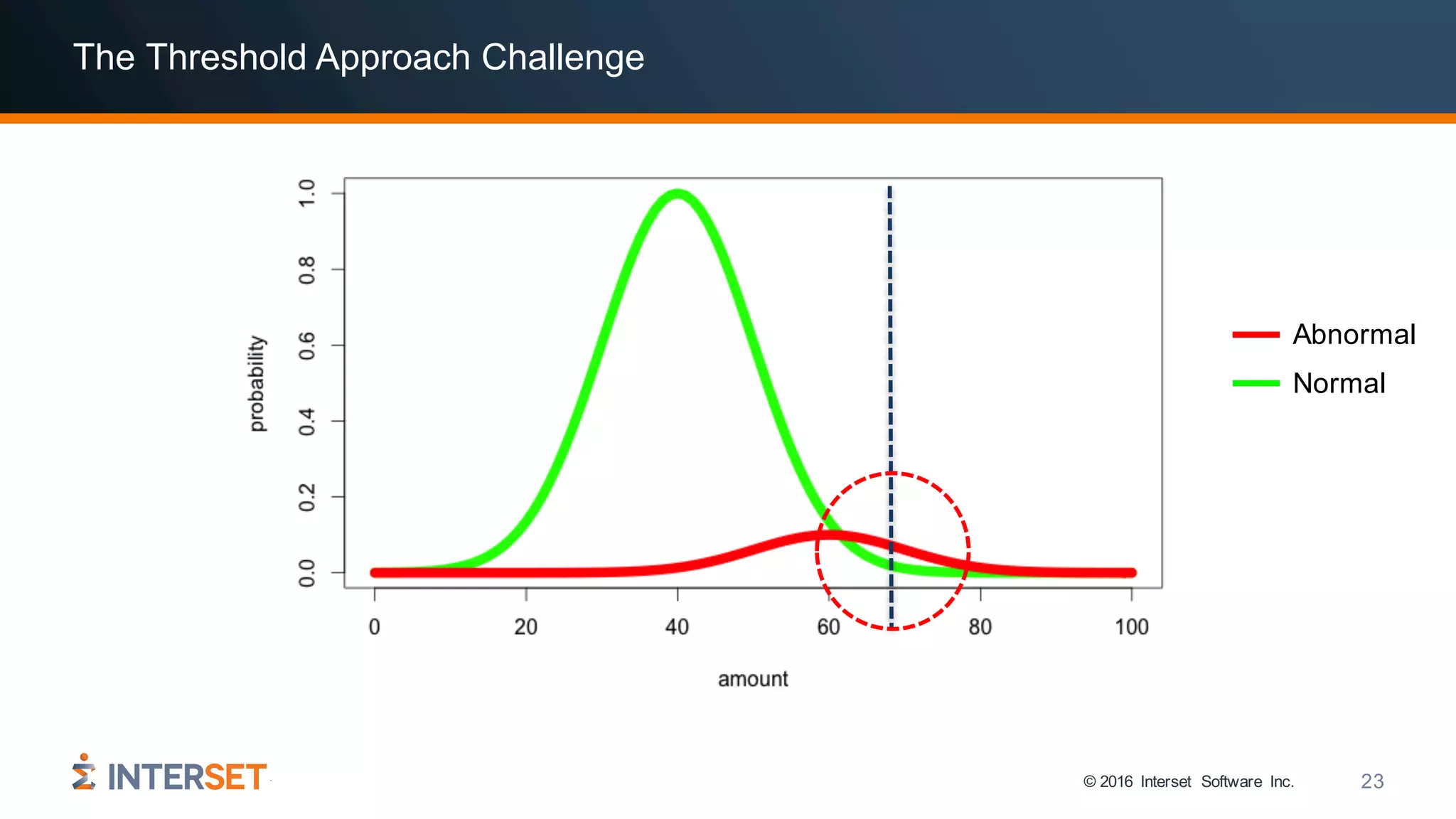
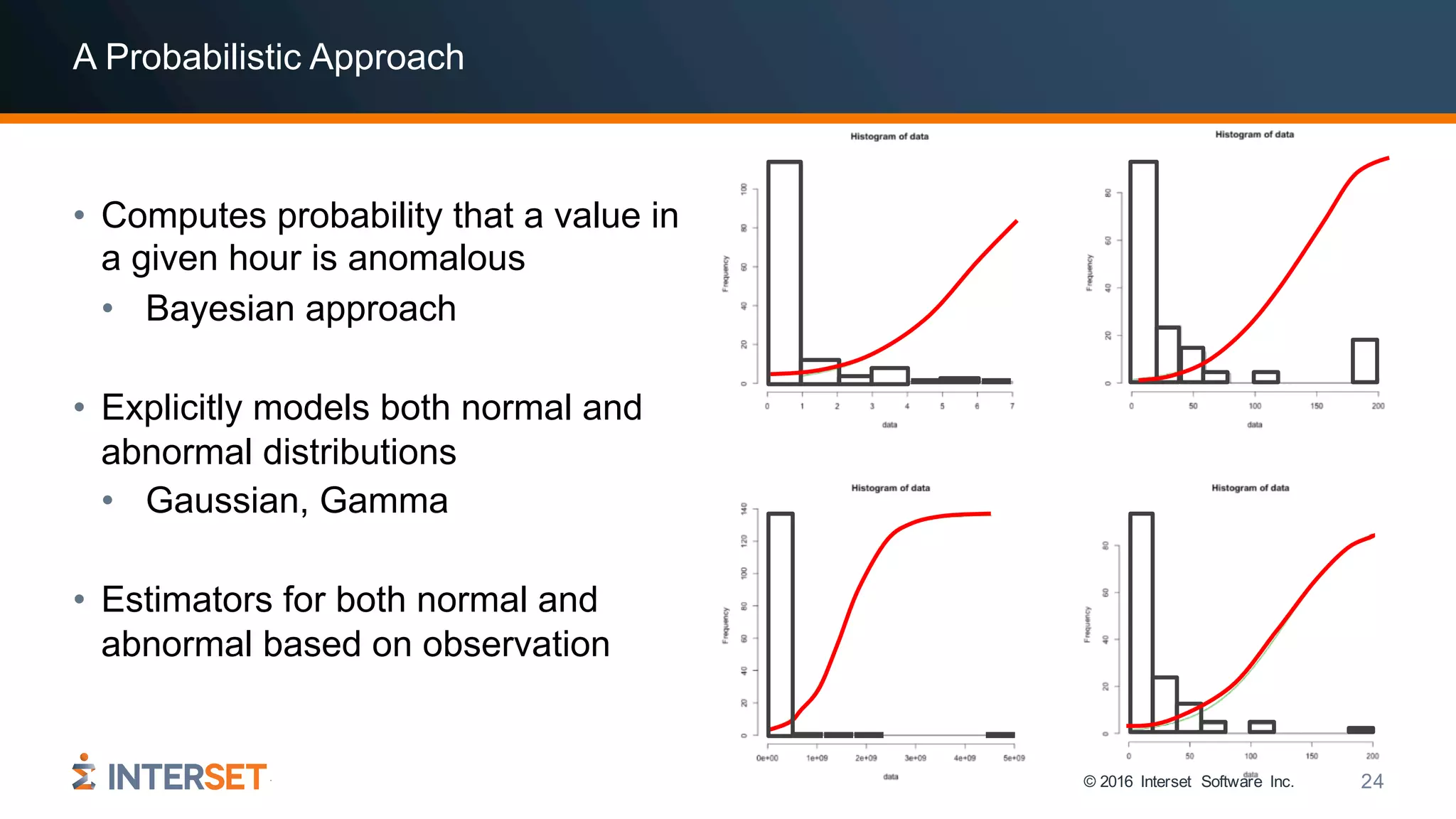
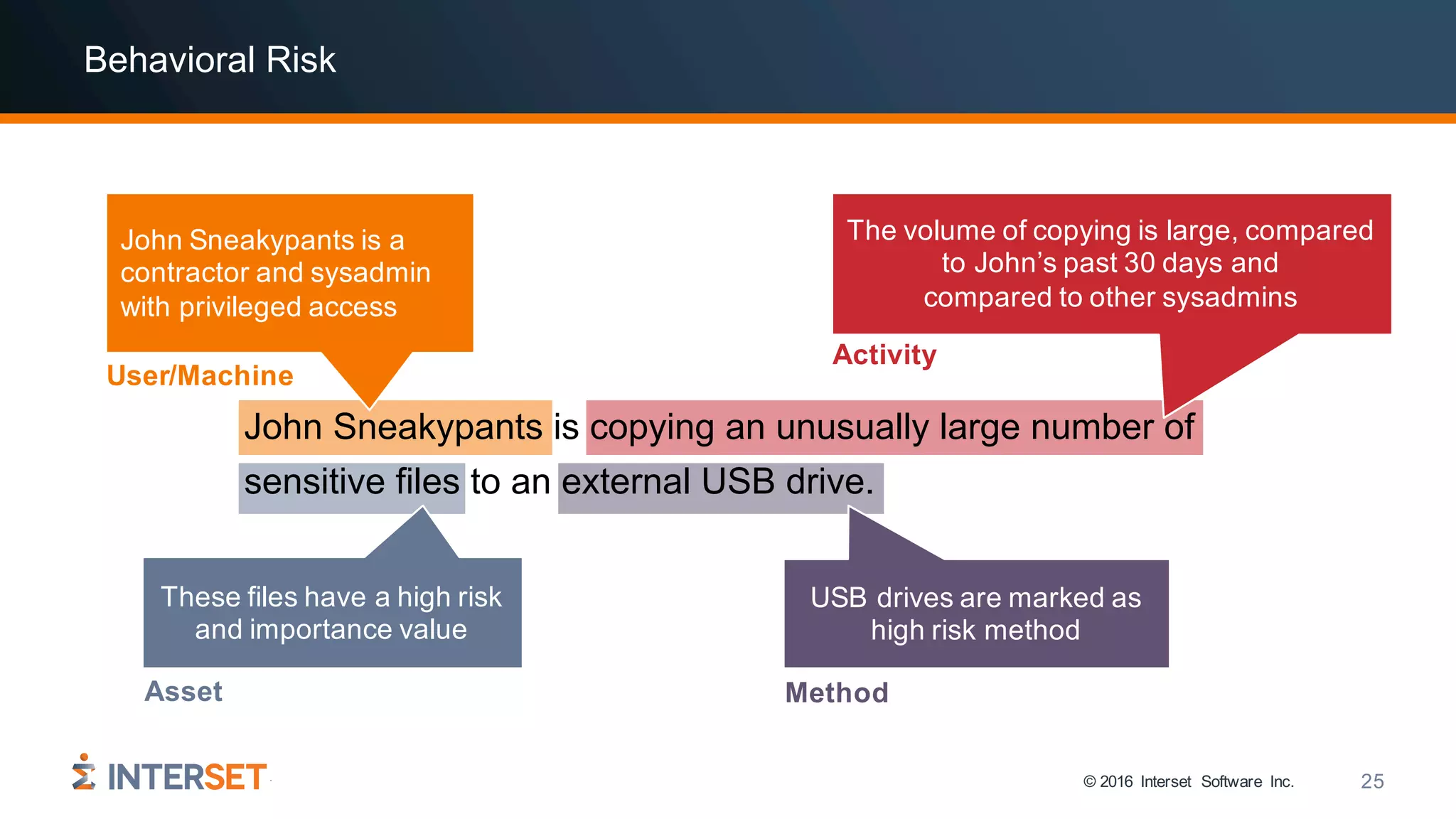
The document discusses the use of data science and machine learning in cybersecurity, specifically focusing on threat detection and prevention through behavioral analytics. It highlights various real-world use cases and the importance of detecting anomalies in user behavior to identify potential attacks. The presentation emphasizes the need for effective data analysis and an improved approach to monitor and respond to cybersecurity threats.






![© 2016 Interset Software Inc. 26
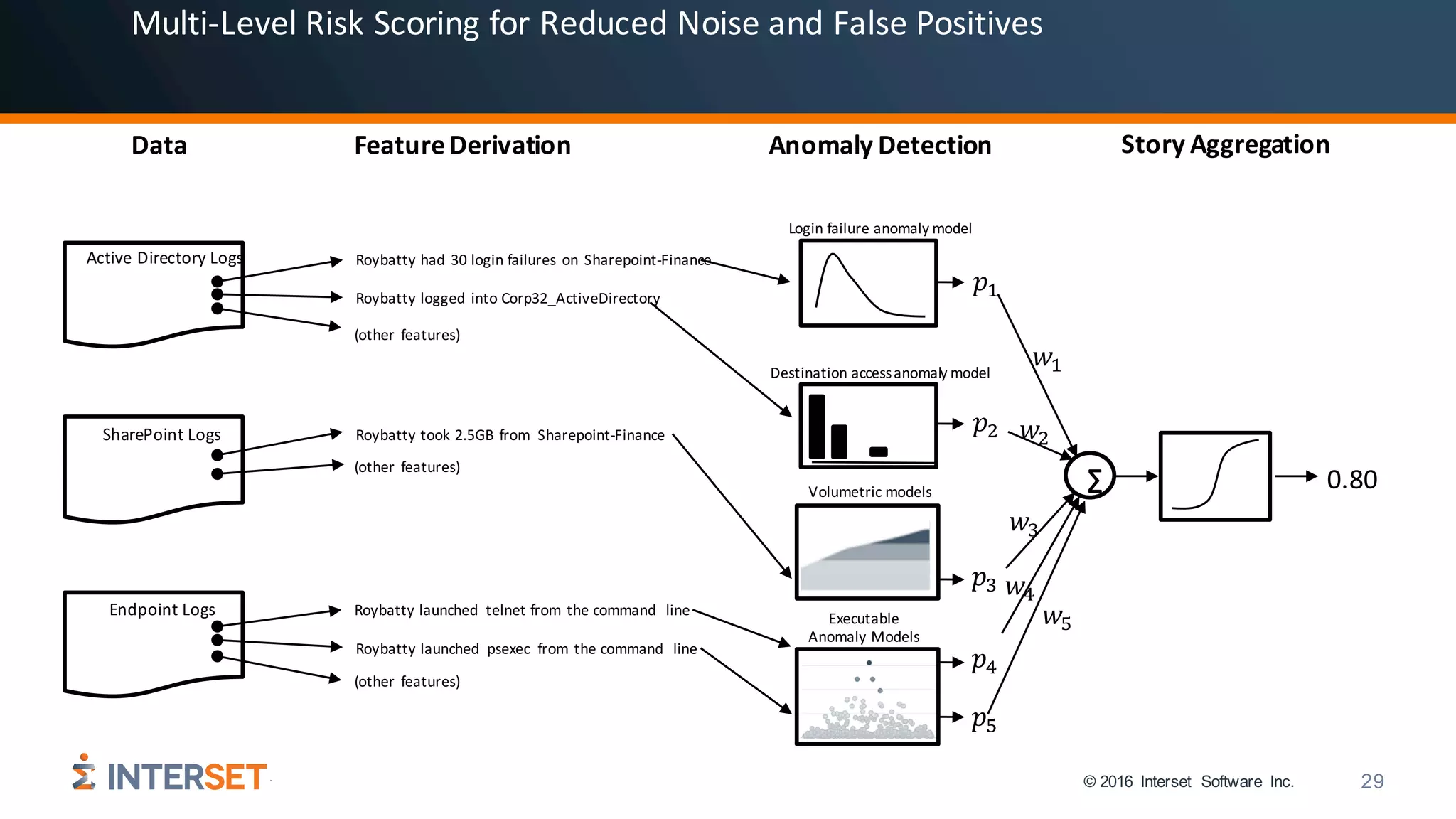
Aggregating Behaviors for Entity Risk
Activity
User/Machine Asset Method
Behavioral
Risk Score
Rentity = importance(t)×vulnerability(t)
User
Asset
Machine
Rbehavior = P(event | y)× wy ×
wu 2−i
⋅ Ru[i]
u∈U
∑ + wf 2− j
⋅ Rf [ j]
f ∈F
∑ + wm 2−k
⋅ Rm[k]
m∈M
∑
&
'
(
(
)
*
+
+
wu + wf + wm](https://image.slidesharecdn.com/2016-09-19-stephanjou-machinelearningmeetupv1-170720173228/75/2016-09-19-stephan-jou-machine-learning-meetup-v1-26-2048.jpg)
![© 2016 Interset Software Inc. 27
Activity
User/Machine Asset Method
Behavioral
Risk Score
Rentity = importance(t)×vulnerability(t)
User
Asset
Machine
Rbehavior = P(event | y)× wy ×
wu 2−i
⋅ Ru[i]
u∈U
∑ + wf 2− j
⋅ Rf [ j]
f ∈F
∑ + wm 2−k
⋅ Rm[k]
m∈M
∑
&
'
(
(
)
*
+
+
wu + wf + wm
Aggregating Behaviors for Entity Risk
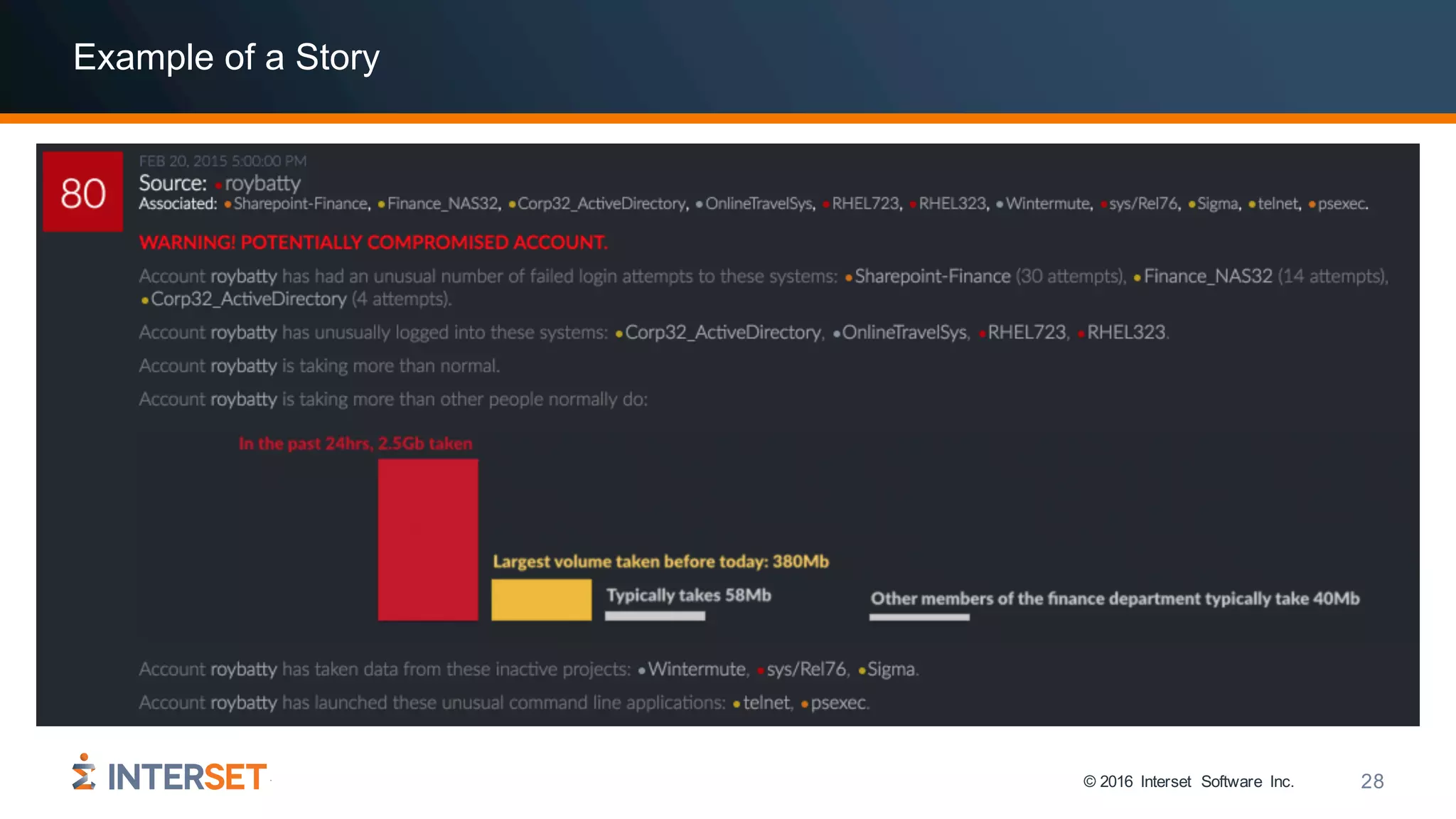
• John Compromised is accessing an unusual, important network share 25
• … at a time of day he was almost never active at before 46
• … and took from a source code project that has been inactive for months 80
• … and just copied an unusual amount of sensitive files to a cloud service 96](https://image.slidesharecdn.com/2016-09-19-stephanjou-machinelearningmeetupv1-170720173228/75/2016-09-19-stephan-jou-machine-learning-meetup-v1-27-2048.jpg)