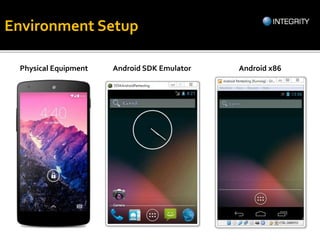
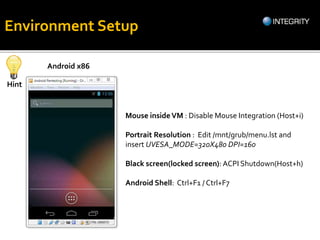
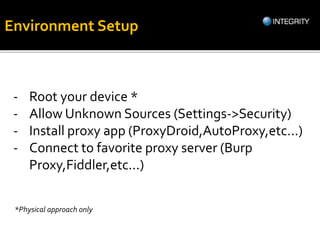
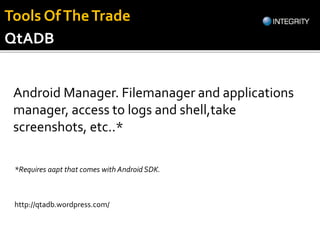
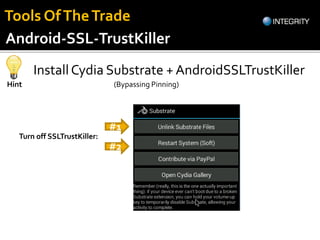
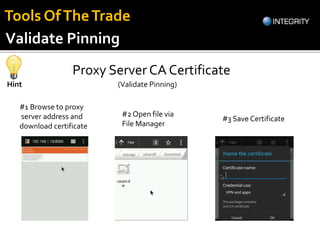
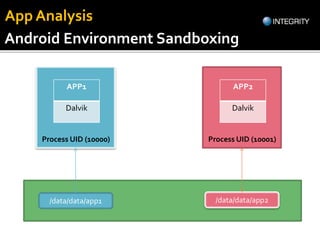
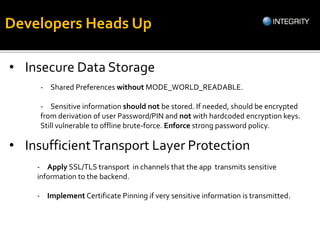
The document outlines essential tools and methods for penetration testing of Android applications, including environment setup and various debugging and analysis tools. Key tools mentioned include the Android Debug Bridge (ADB), Dalvik Debug Monitor Server (DDMS), and security testing frameworks like Drozer and Burp Suite. It also highlights key security risks and best practices for developers to mitigate vulnerabilities in their apps.