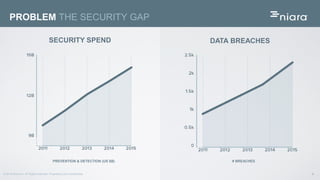
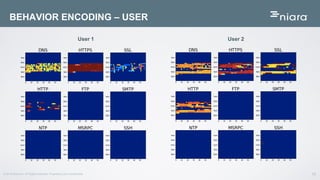
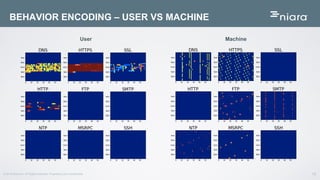
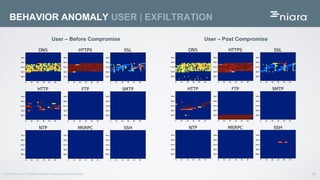
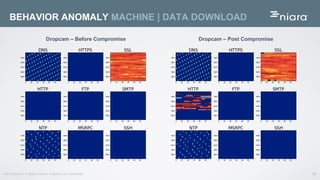
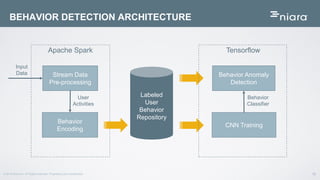
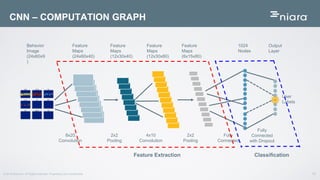
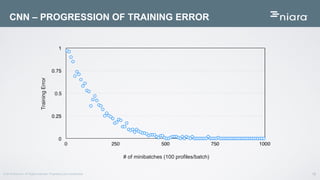
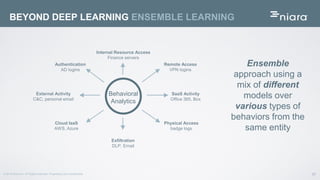
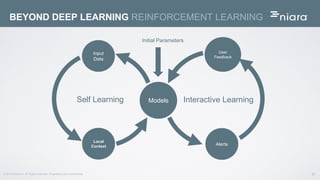
The document discusses the application of deep learning in User and Entity Behavior Analytics (UEBA) to enhance security by detecting anomalies in user behavior and identifying compromised accounts. It emphasizes the importance of adapting deep learning solutions to rapidly evolving security threats, particularly in a landscape dominated by IoT and cloud technologies. Real-world examples demonstrate how UEBA approaches have successfully identified significant security breaches, highlighting the need for a comprehensive solution that goes beyond traditional methods.