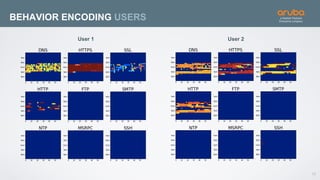
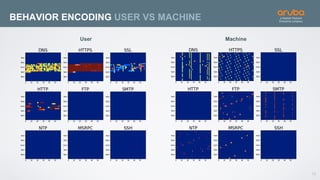
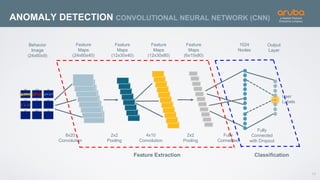
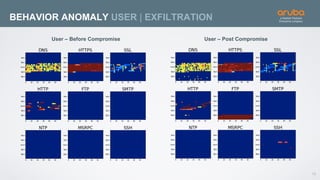
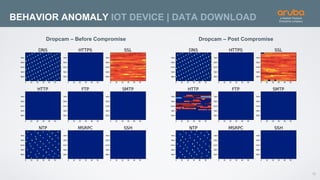
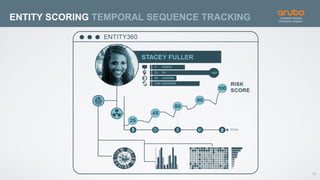
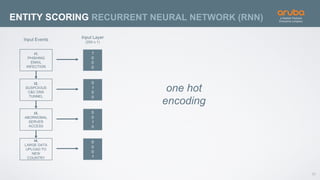
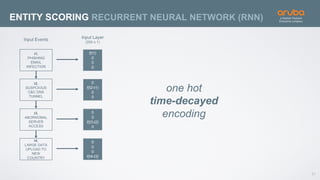
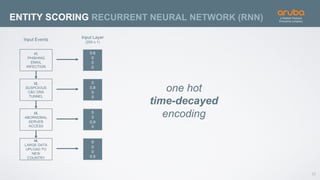
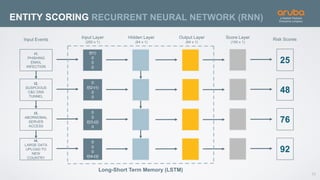
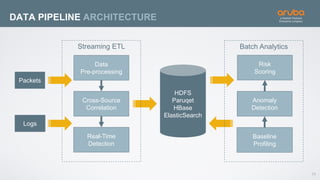
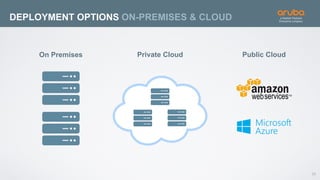
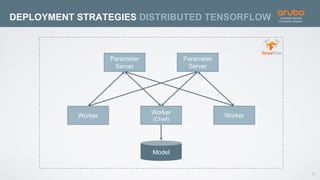
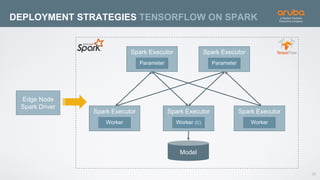
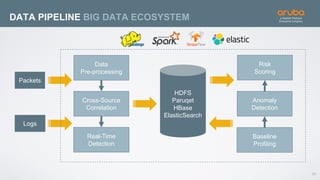
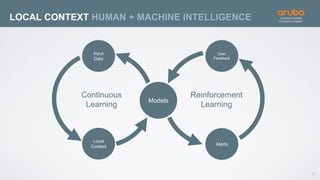
The document discusses the application of deep learning and User and Entity Behavior Analytics (UEBA) in enhancing security, particularly in combating innovative attackers in a borderless digital landscape. It presents various infrastructure designs, challenges, and real-world cases of security breaches, emphasizing the need for responsive and machine-driven detection systems. Solutions such as convolutional neural networks (CNN) and recurrent neural networks (RNN) are explored for behavior anomaly detection and risk scoring of users and devices.