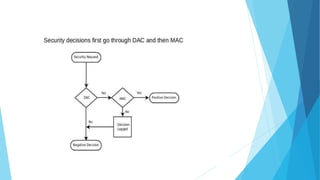
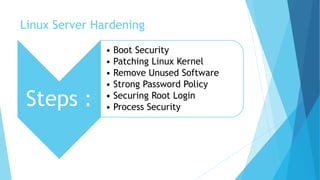
Linux is a free open-source operating system created in 1991, widely used in servers, desktops, and various devices, and allows users to modify its source code. Hardening is the process of securing a computer system by applying multiple layers of protection, while user and group permissions regulate access to files and resources. Effective Linux server hardening involves steps such as boot security, patching, removing unused software, enforcing strong password policies, and managing user access.













![Operating System
Patching and Software Updates: periodically patches are released for
included software either due to security flaws or to include additional
functionality.
File System Configuration:
Create Separate Partition for /tmp: grep “[[:Space:]]/tmp[[:space:]]” /etc/fstab
Create Separate Partition for /var: grep “[[:Space:]]/var[[:space:]]” /etc/fstab
Secure Boot Settings :
Set permissions on boot loader config: chmod og-rwx/boot/grub/grub.cfg
Set Boot Loader Password : grub-mkpasswd-pbkdf2
Os Services:
Ensure rsh server is not enabled
Ensure telnet server is not enabled](https://image.slidesharecdn.com/linuxsecurity-200102025445/85/Linux-security-17-320.jpg)