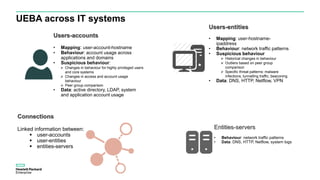
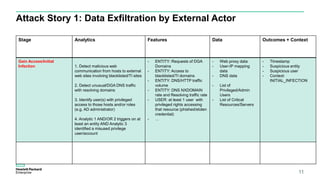
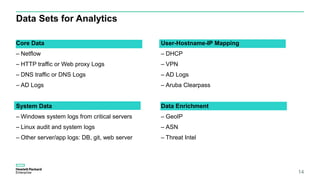
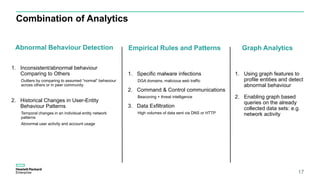
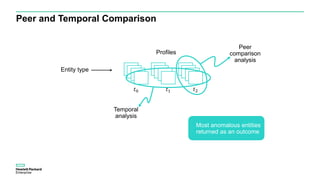
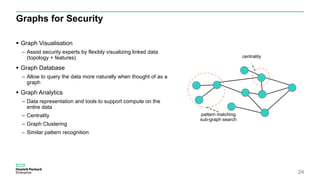
The document discusses User and Entity Behavior Analytics (UEBA) as a method for detecting malicious activities using machine learning and anomaly detection. Key components of an effective UEBA solution include data collection, abnormal behavior detection, and analytics capabilities to identify potential security threats. It also outlines various attack scenarios and the importance of correlating user and entity activities to enhance threat detection across IT systems.