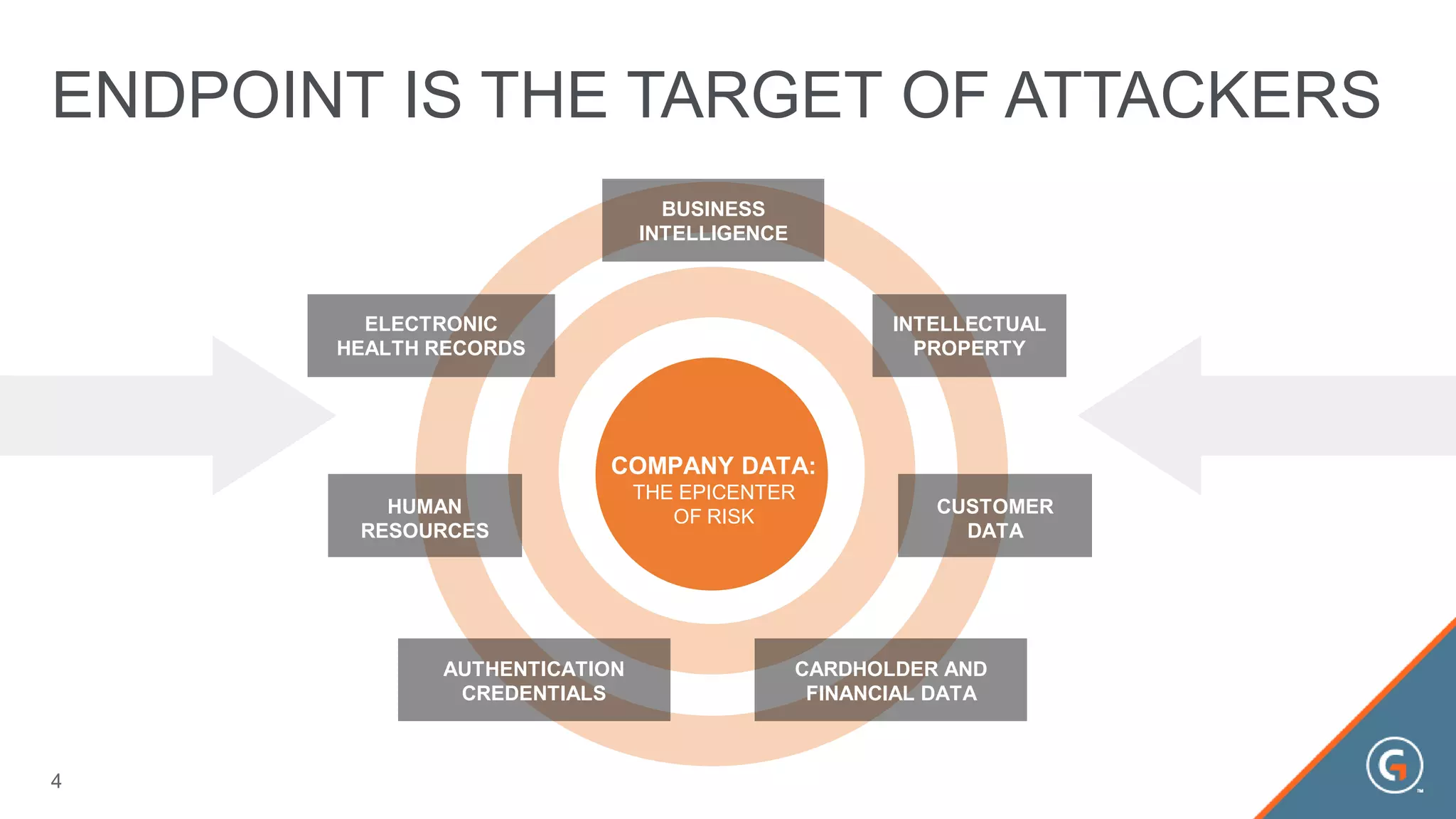
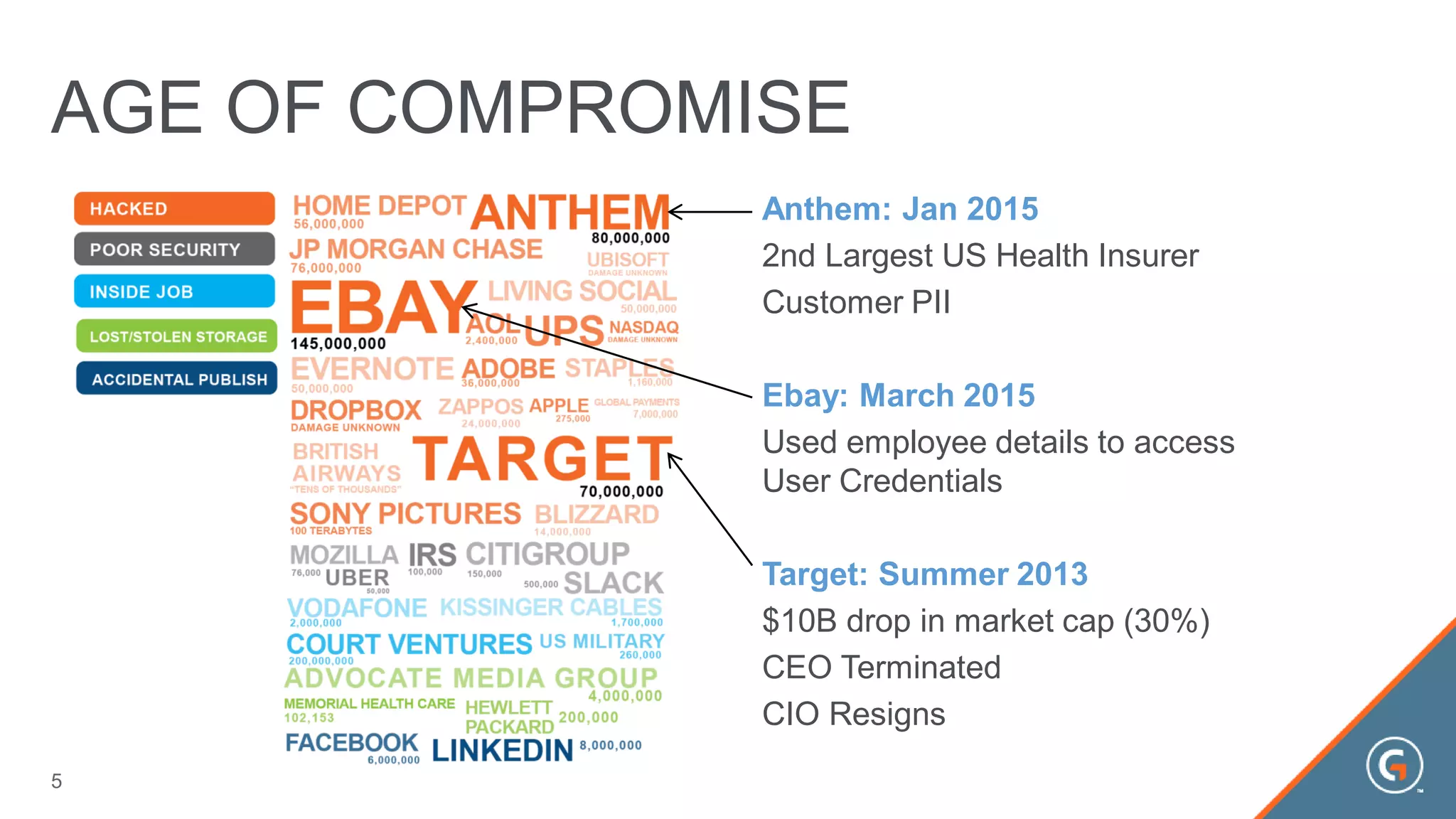
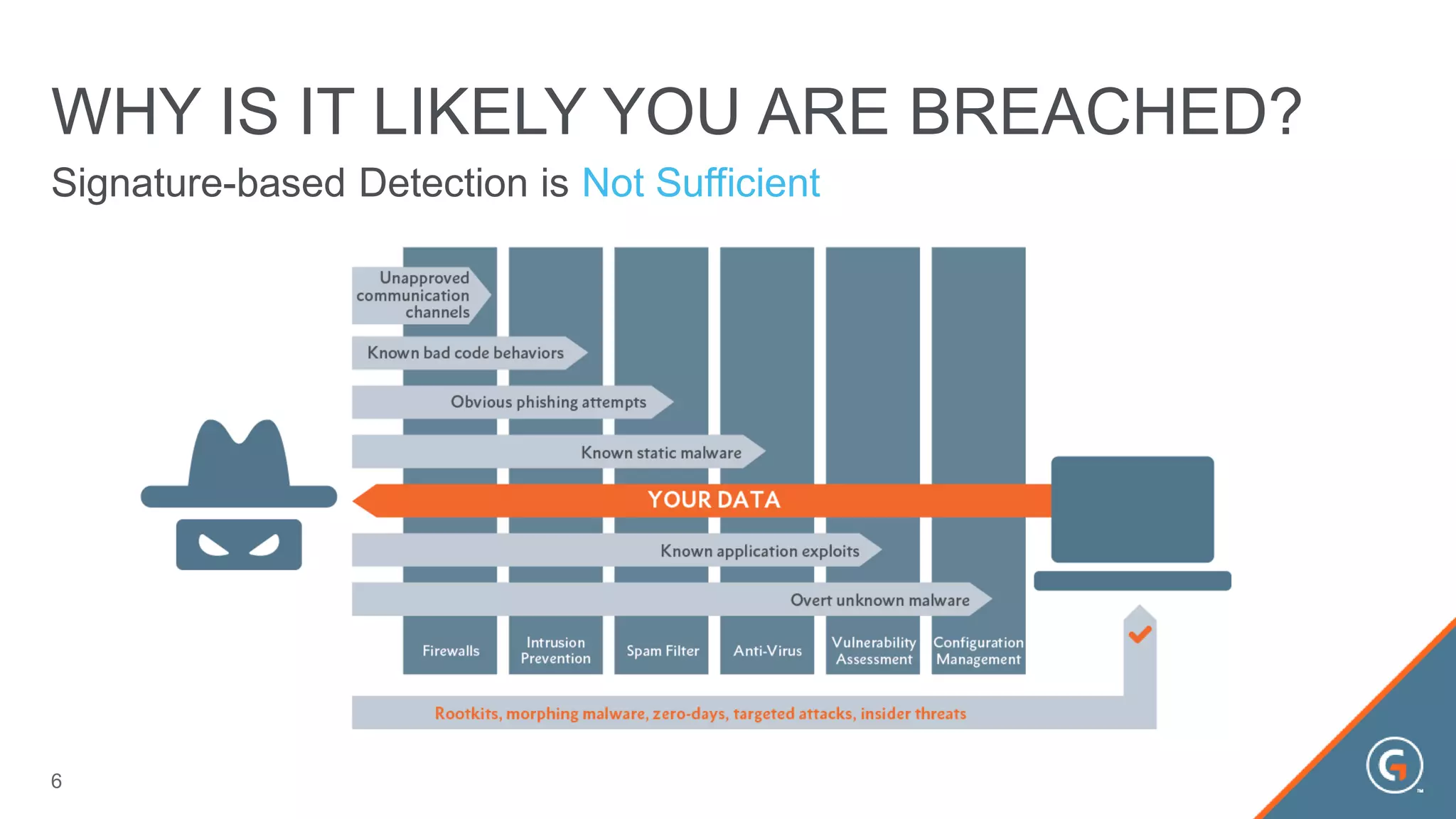
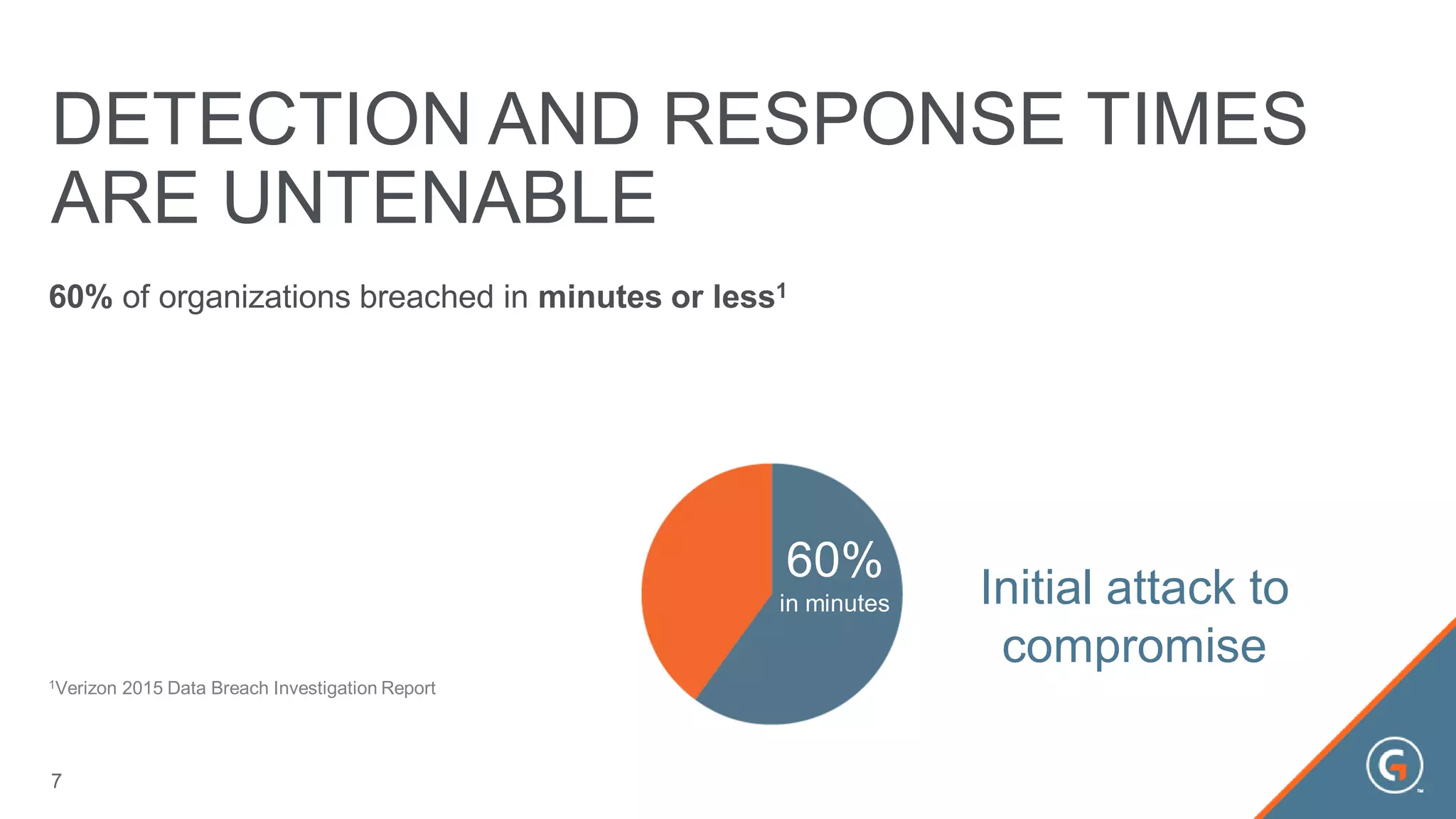
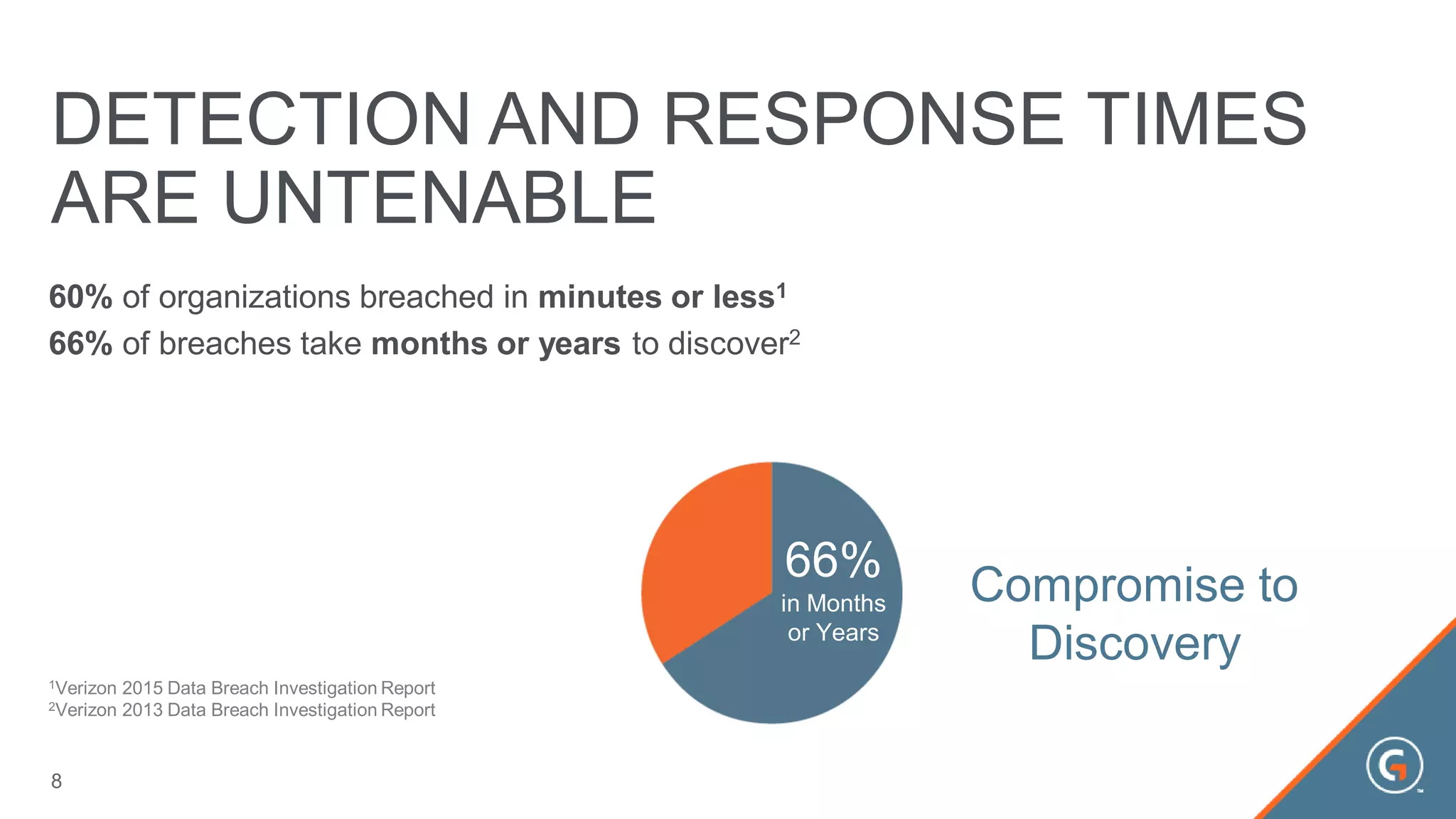
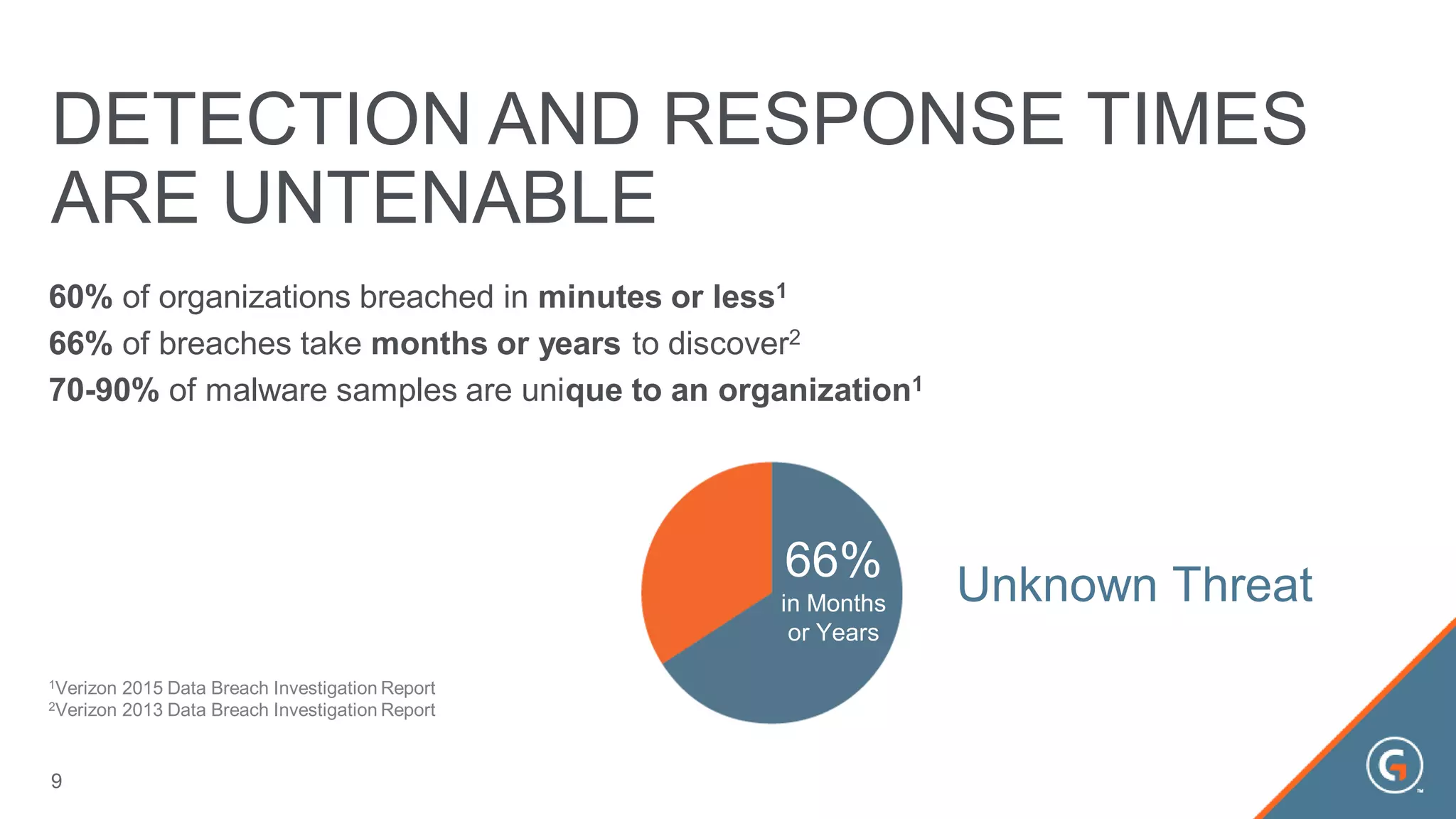
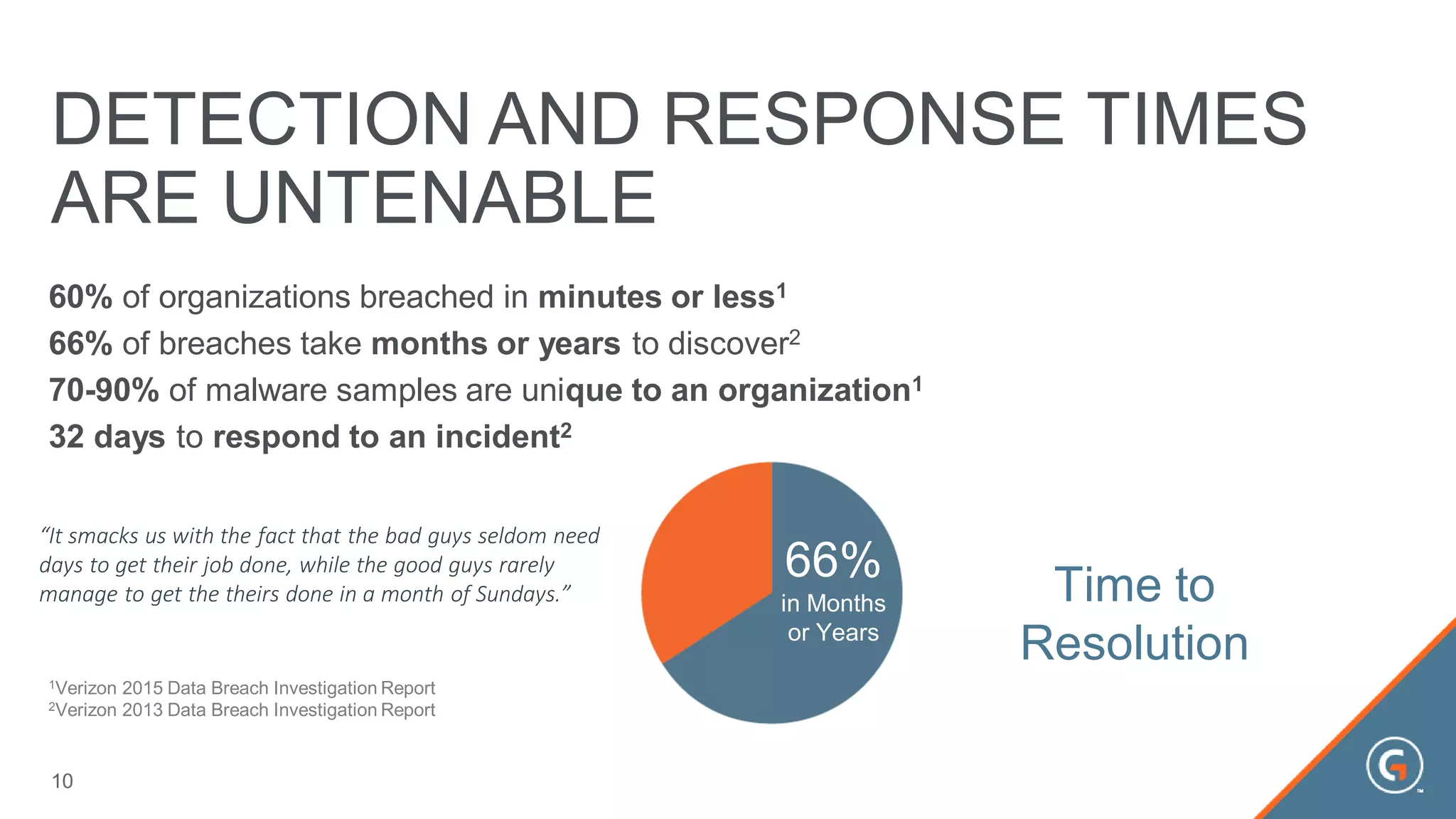
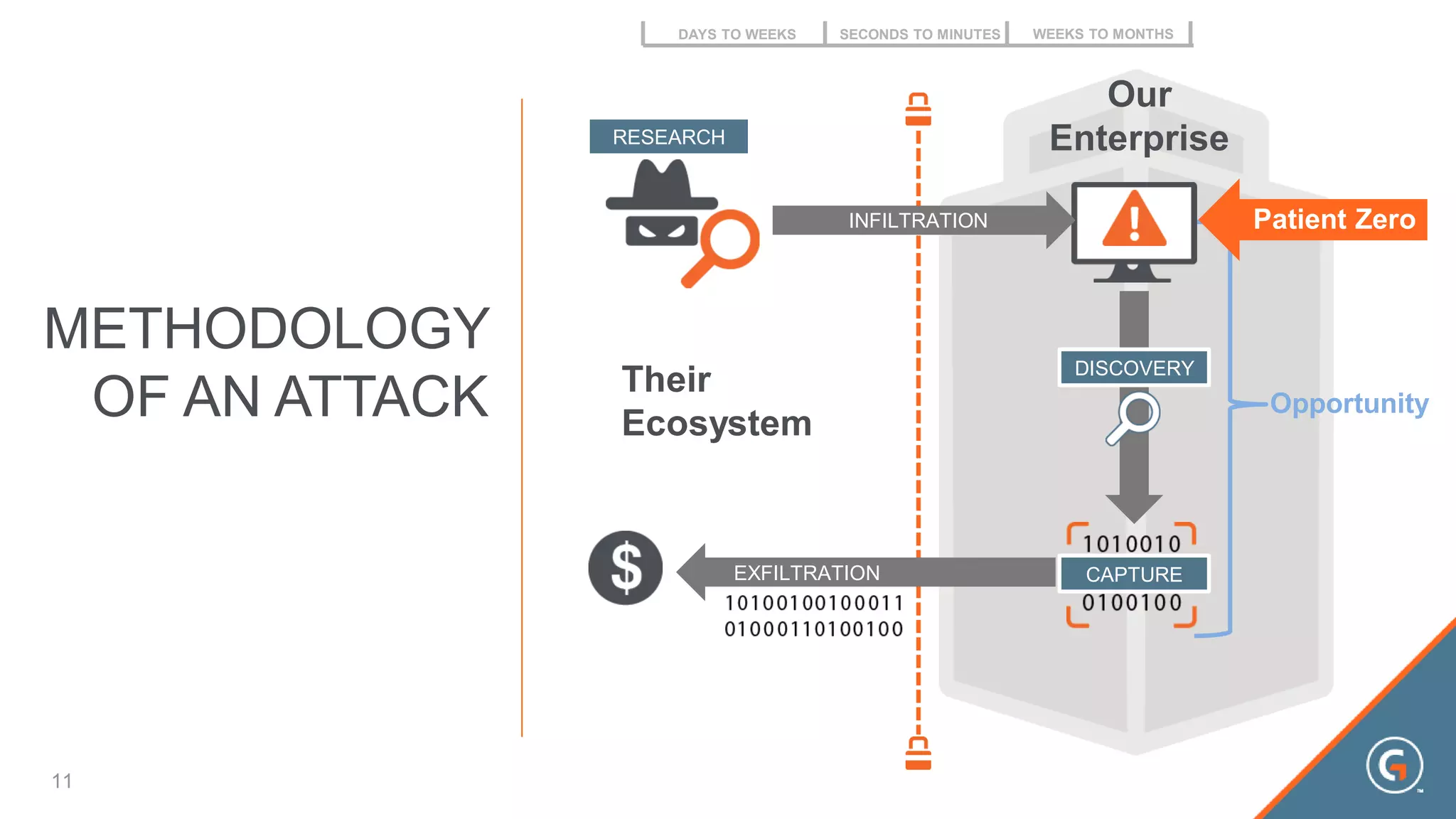
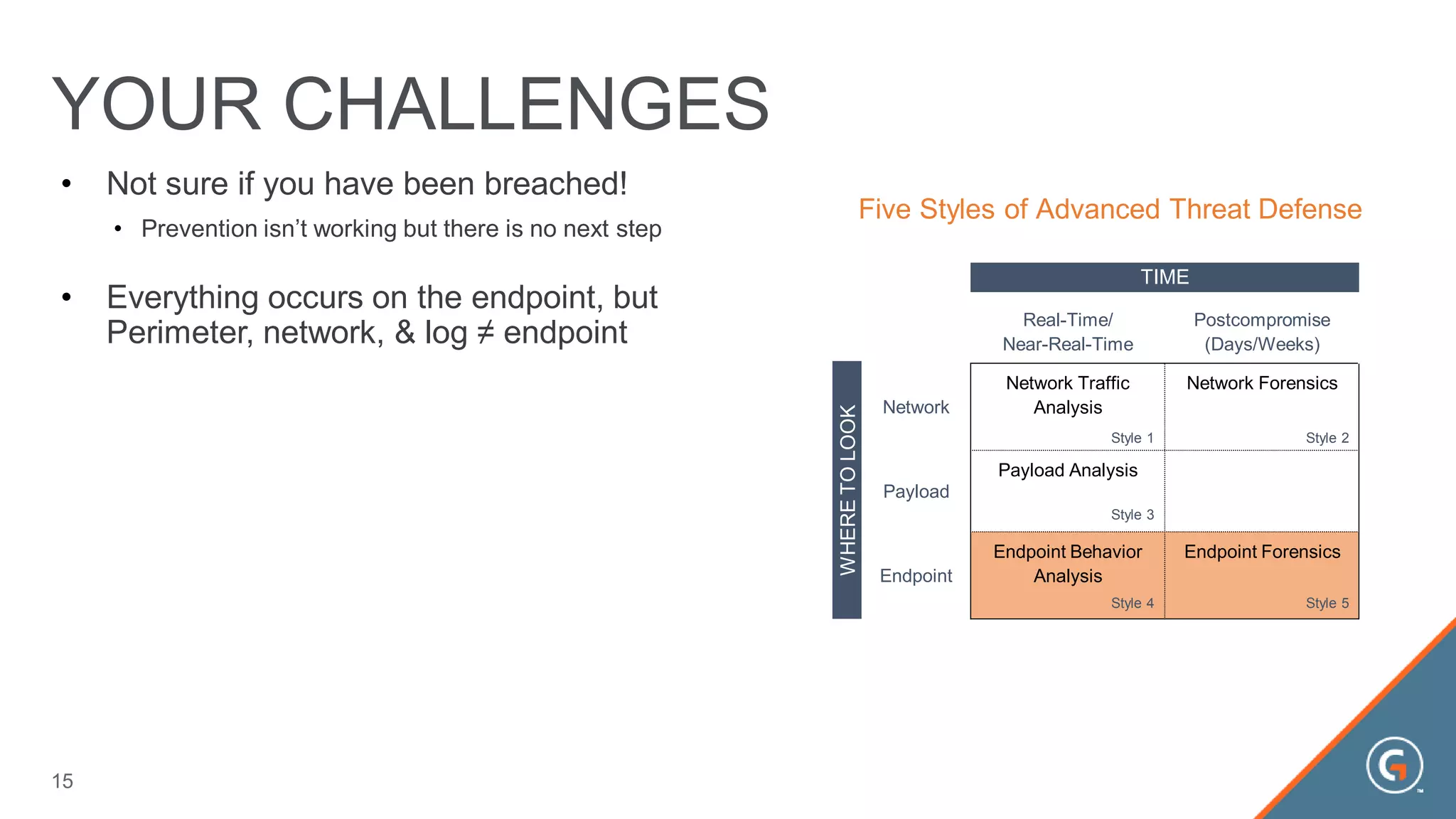
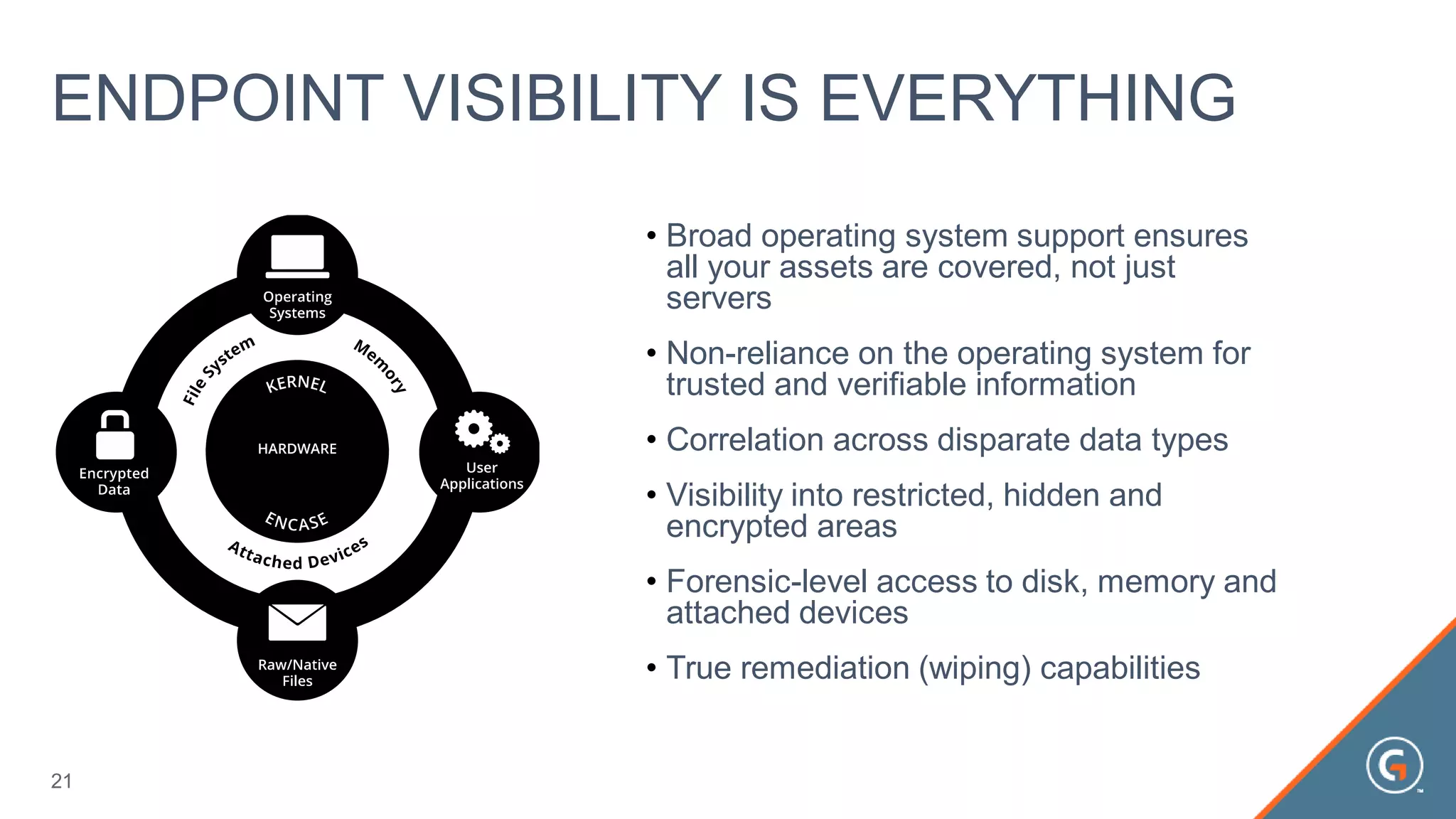
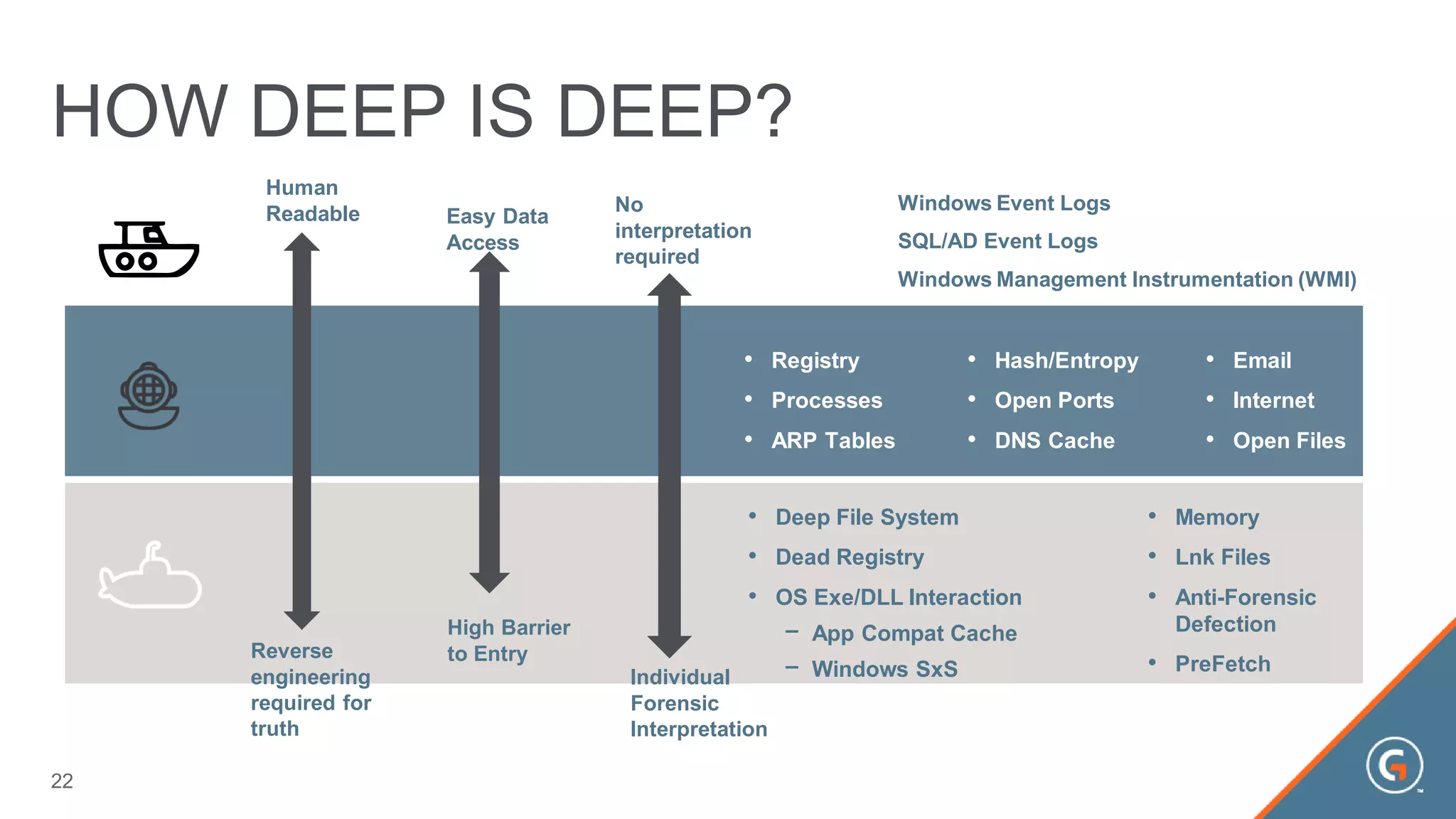
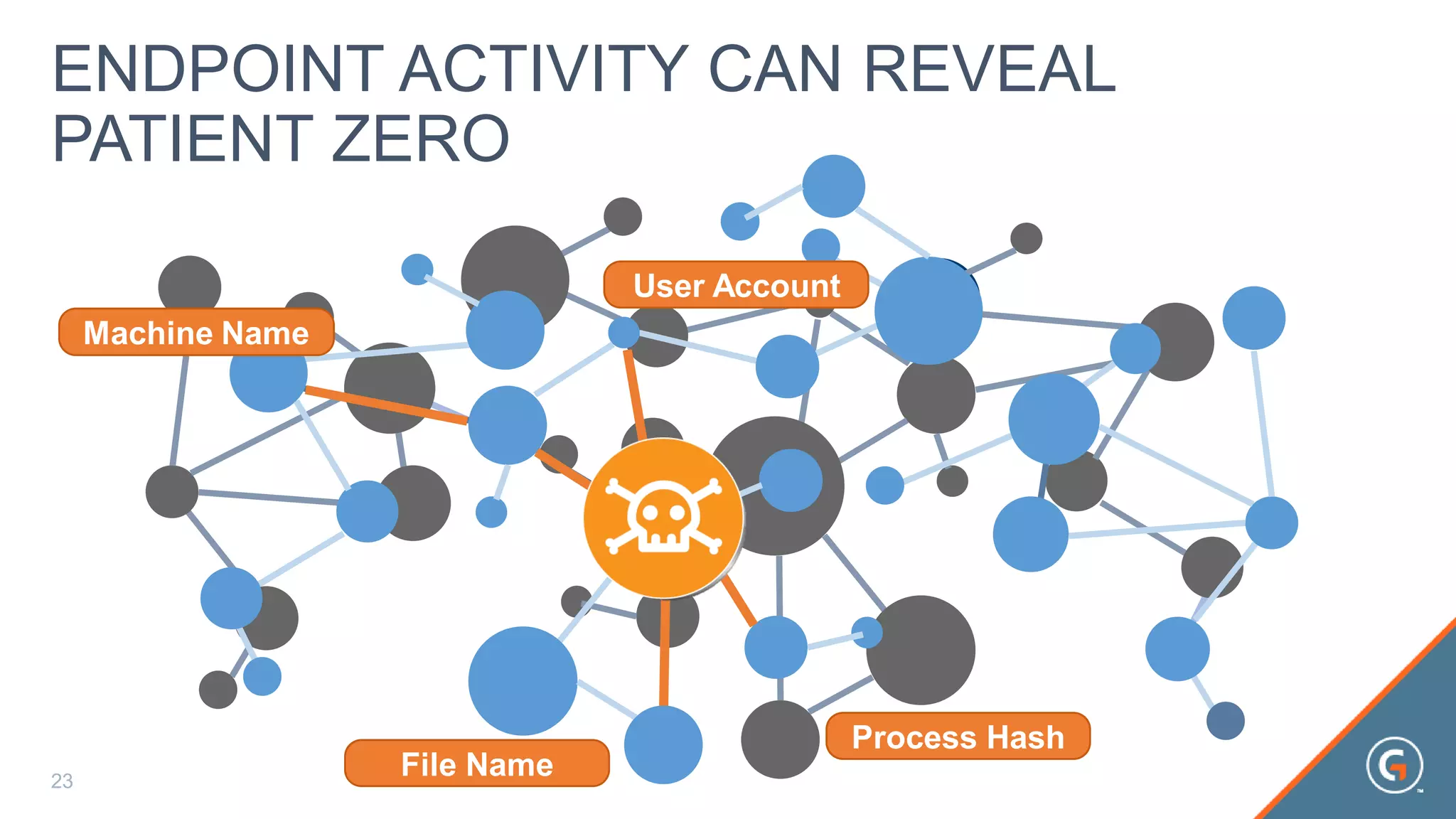
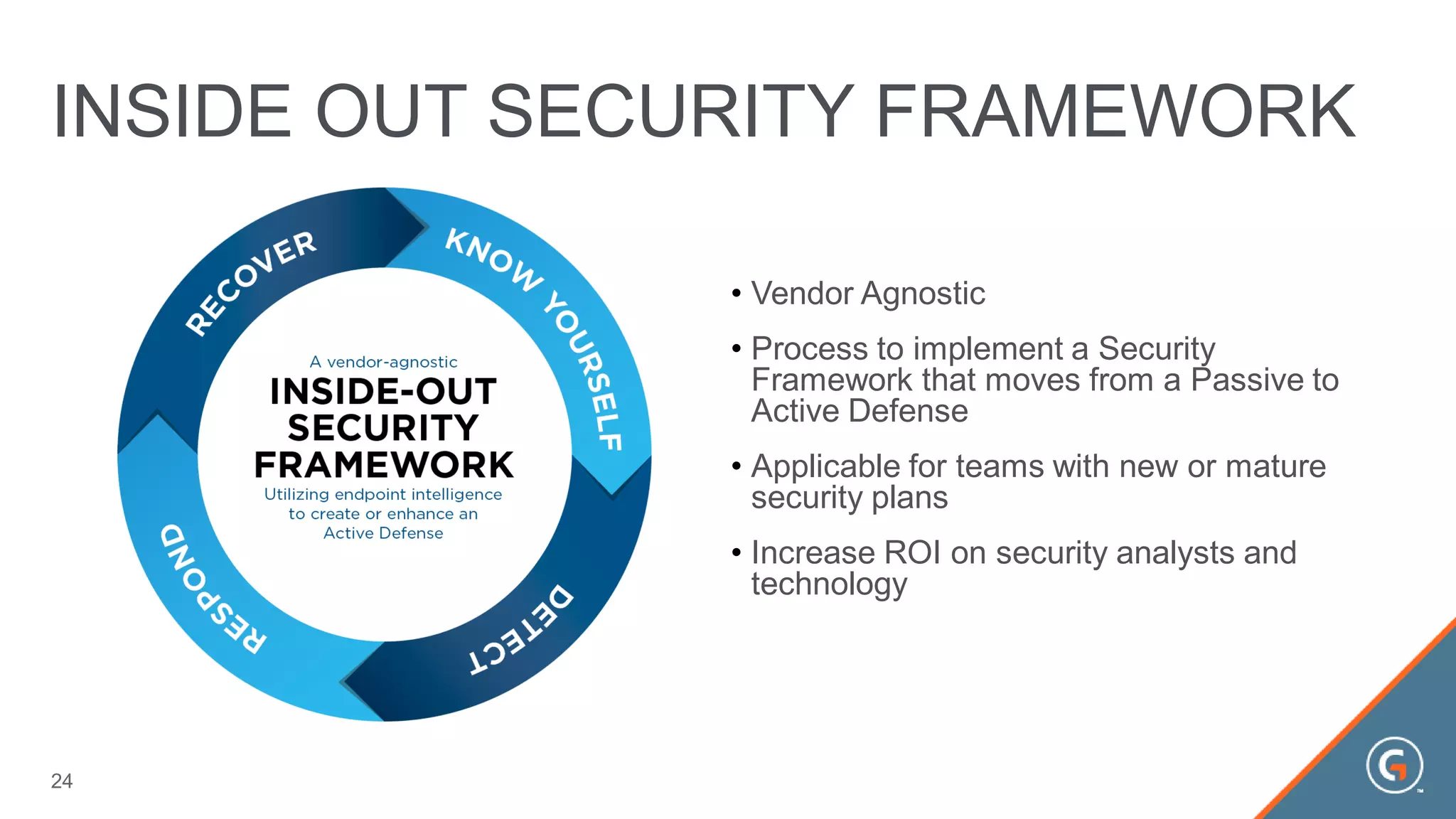
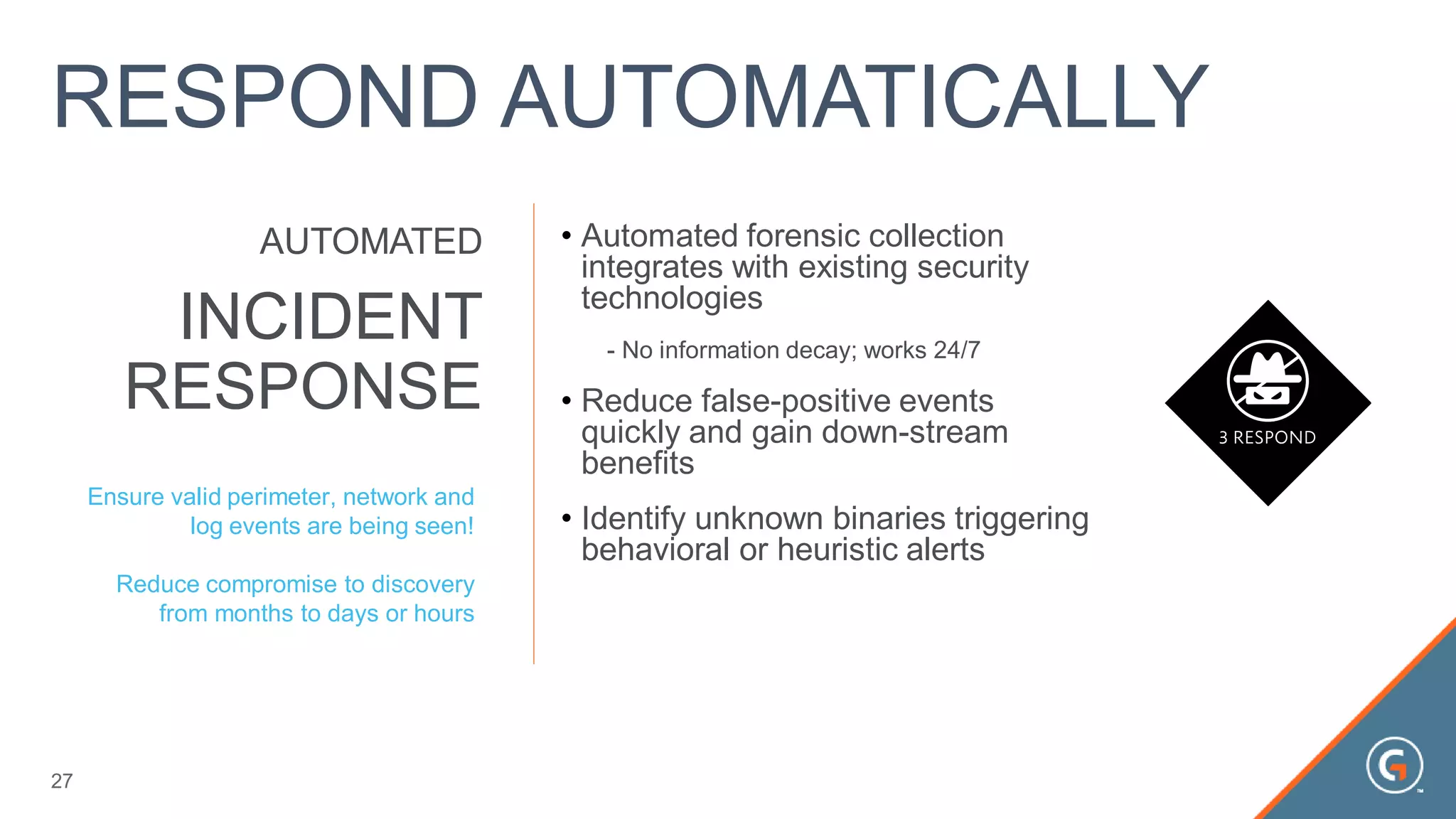
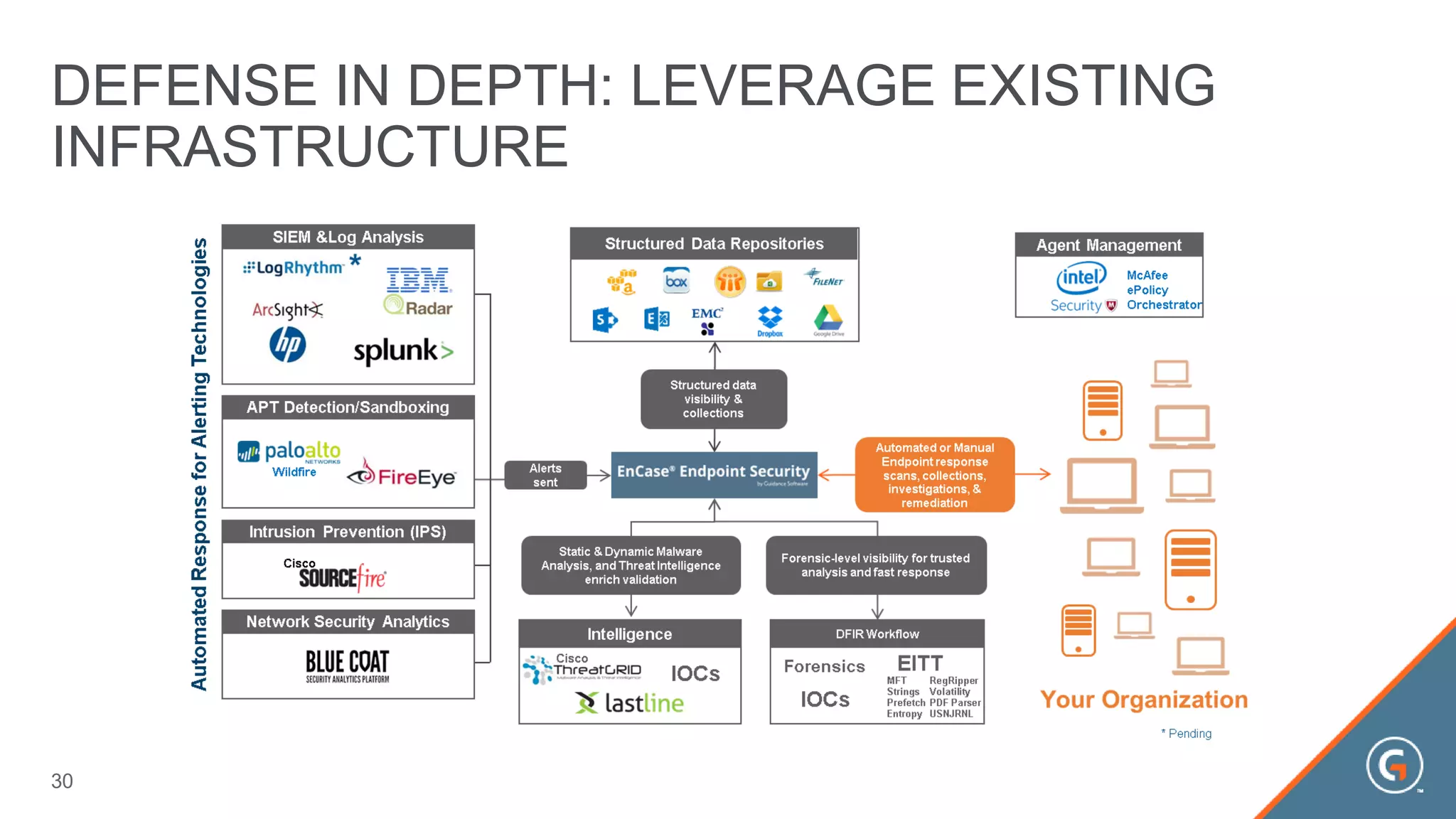
This document summarizes a presentation on leveraging big data in cybersecurity. It discusses how current security challenges include breaches occurring within minutes while most go undiscovered for months or years. Inside-out security is proposed to detect both known and unknown threats using deep endpoint visibility and activity correlation. This allows proactive detection, assessment of sensitive data and risks, automated incident response, and recovery to reduce breach discovery times.