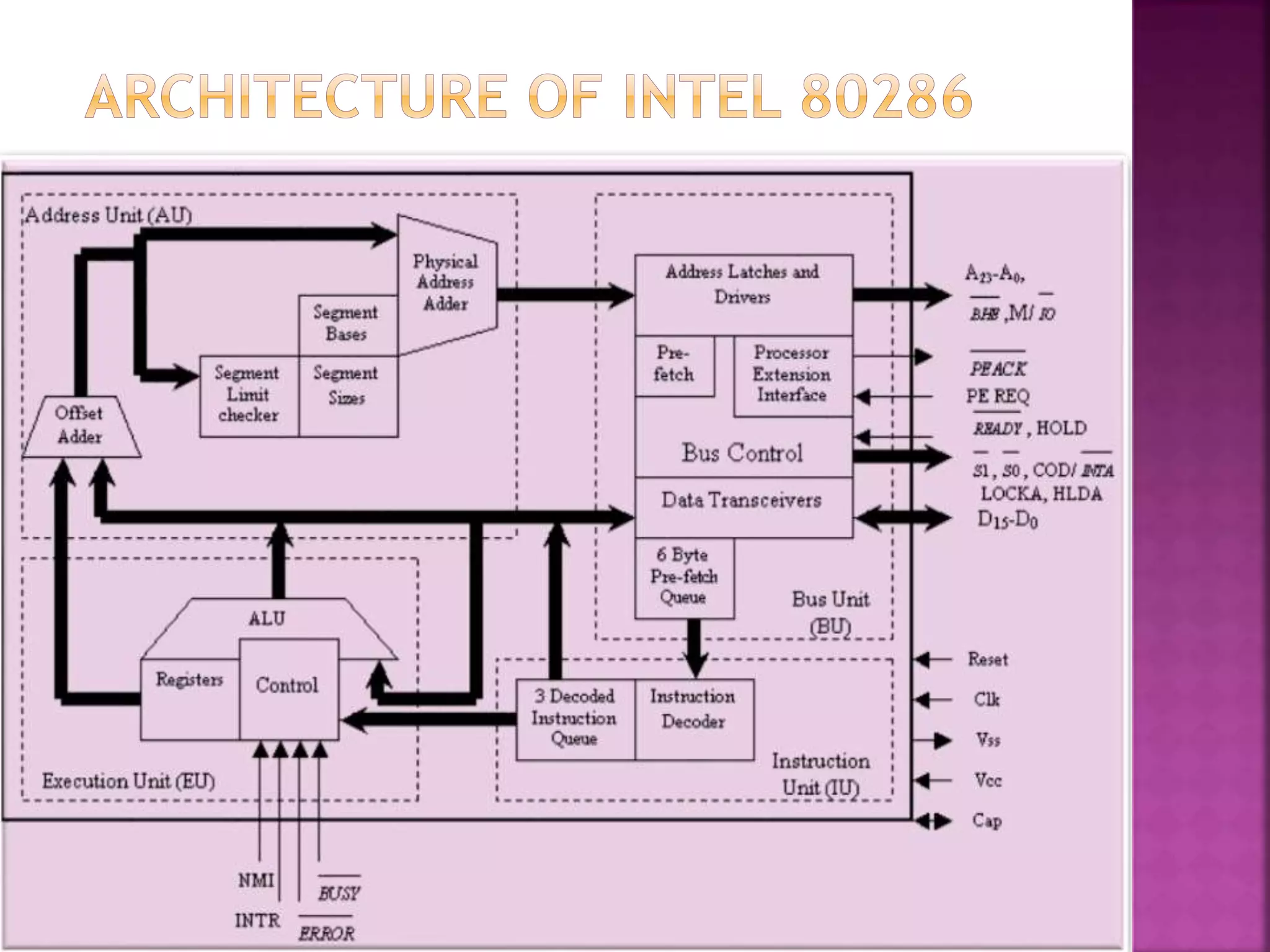
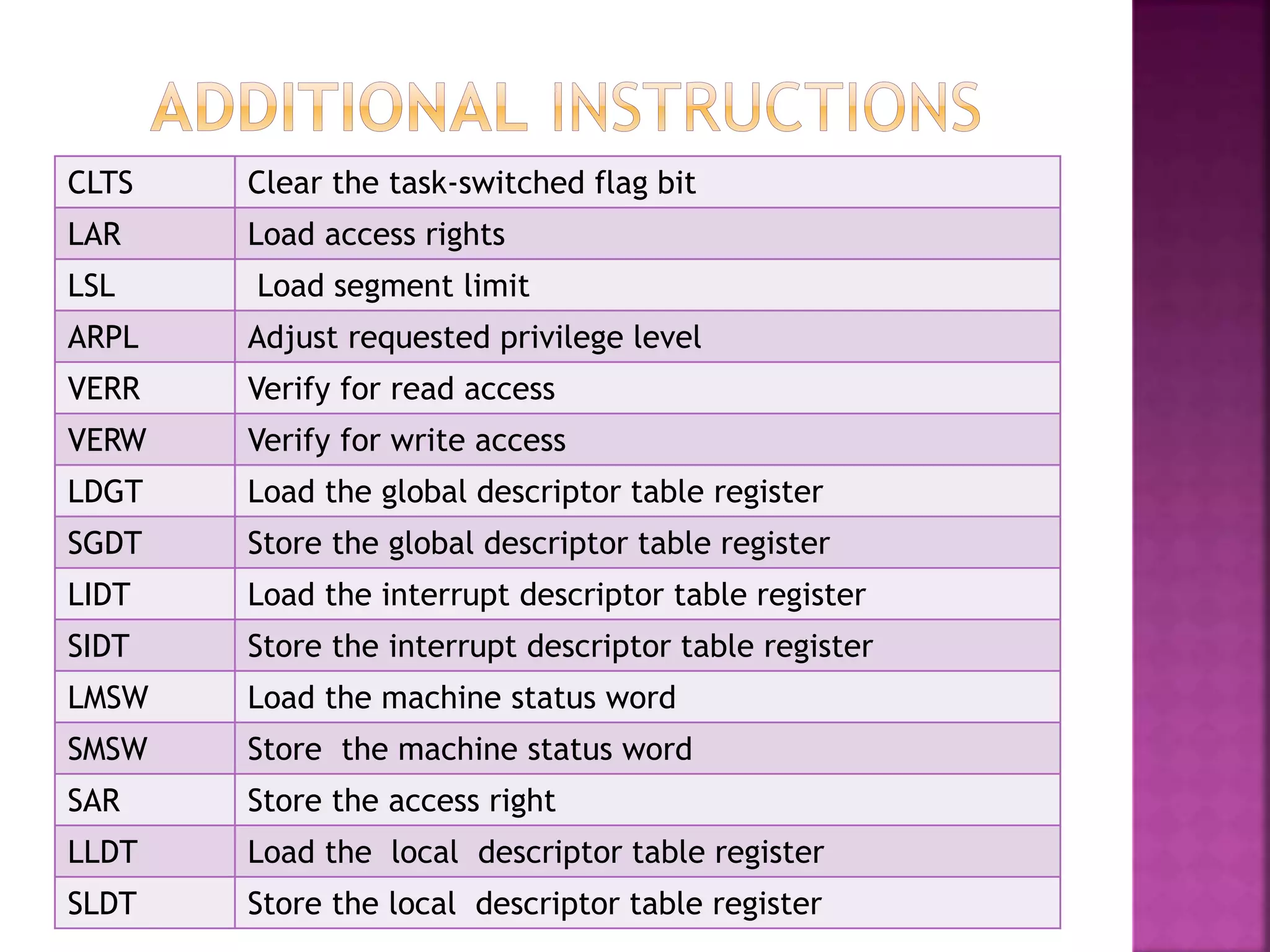
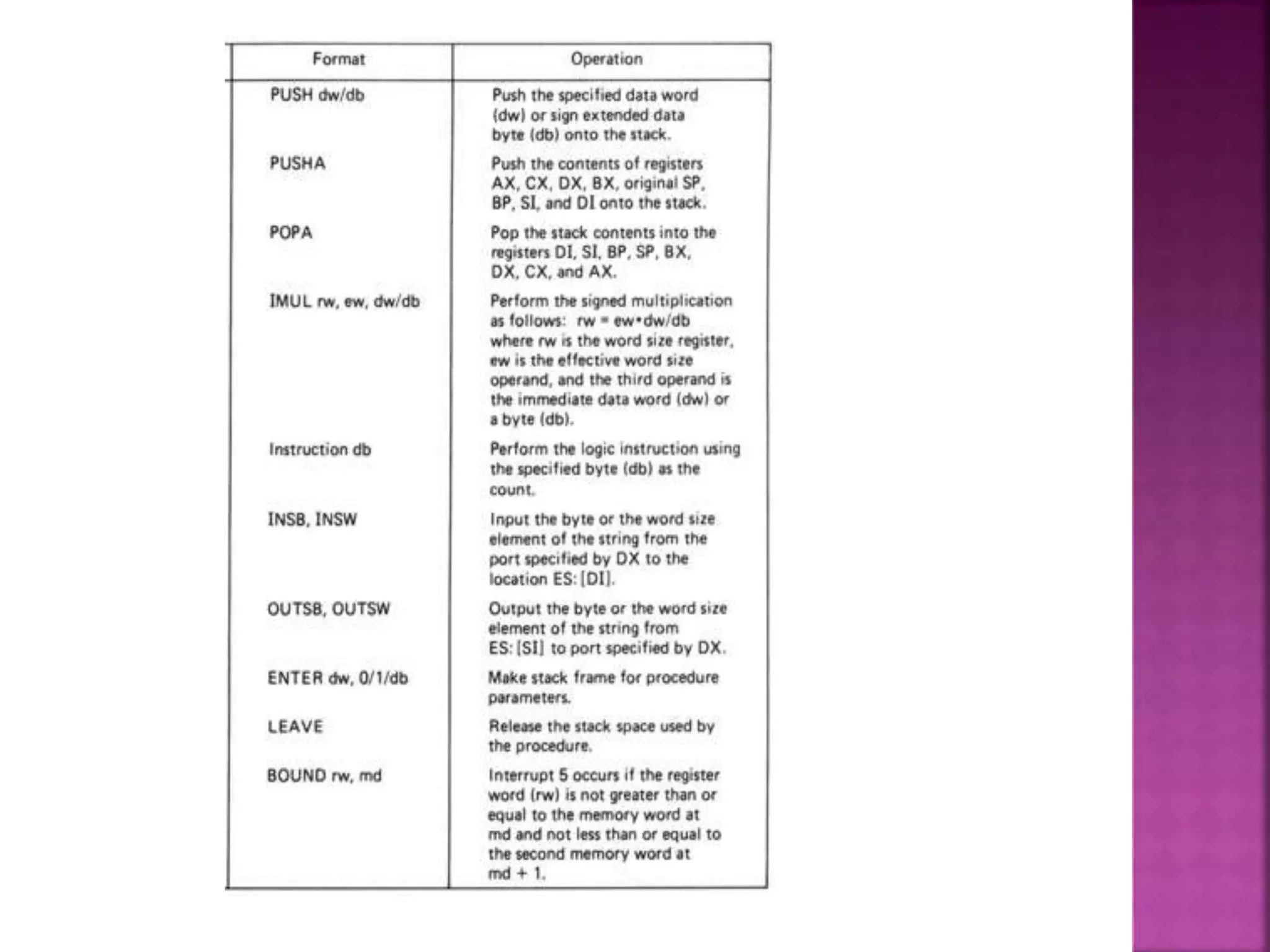
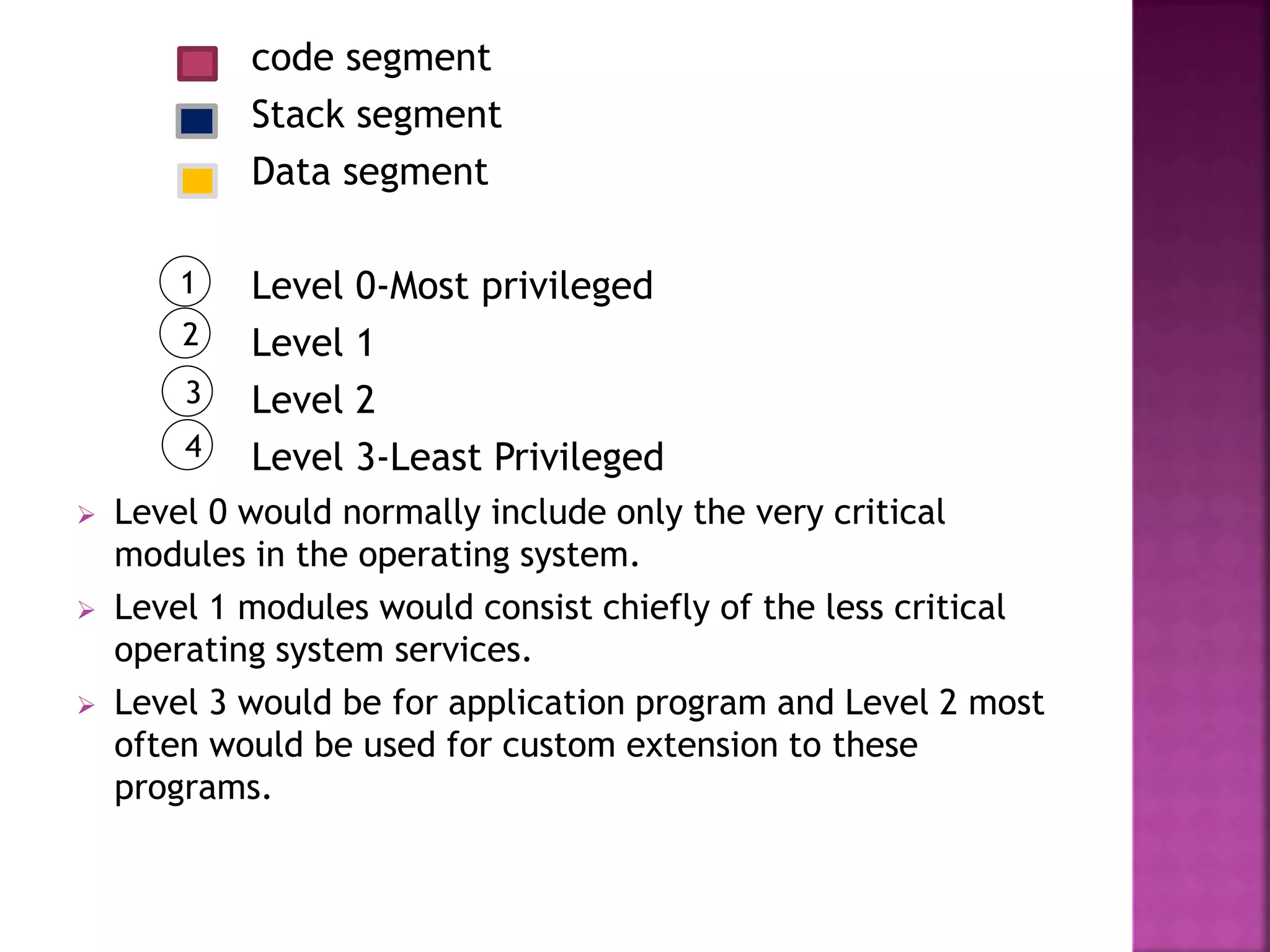
The Intel 80286, introduced on February 1, 1982, is a 16-bit x86 microprocessor known for its memory management and multitasking capabilities, featuring 134,000 transistors. It operates in two modes: real mode, which closely resembles its predecessor 8086, and protected mode, which supports multitasking and segment protection for improved system stability. The architecture includes four independent units that manage address calculation, instruction decoding, and execution to enhance overall performance.