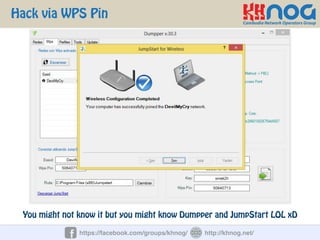
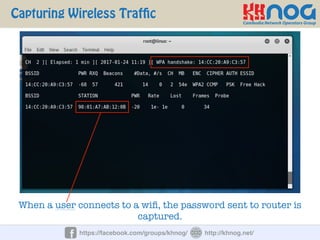
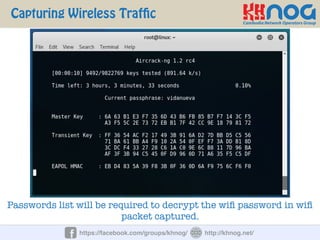
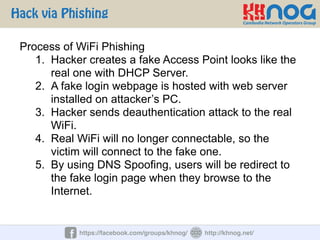
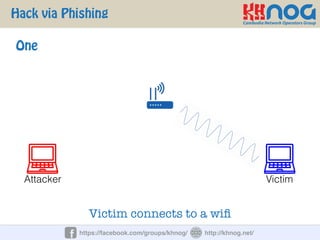
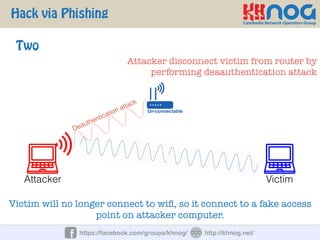
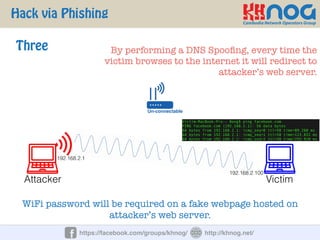
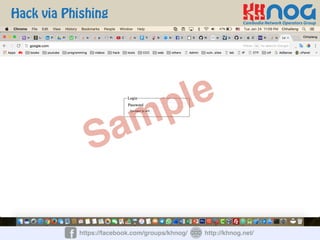
The document discusses wireless penetration testing and how to hack WiFi networks. It describes three main methods for hacking WiFi: using WPS PINs, capturing wireless traffic to obtain passwords, and performing phishing attacks. It provides step-by-step explanations of how to hack using these methods and concludes with some tips to secure wireless networks like changing default passwords, disabling SSID broadcast, using encryption, and turning off networks when not in use.