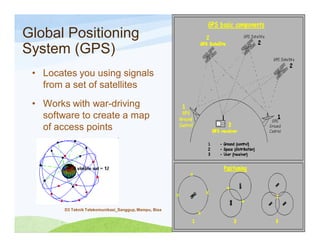
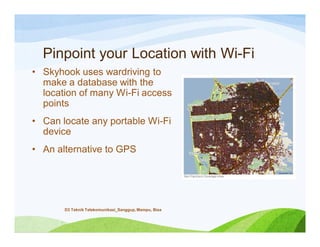
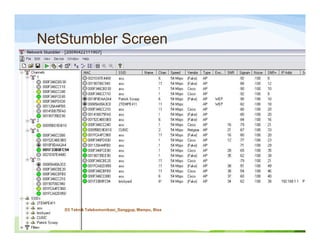
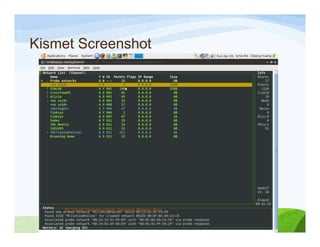
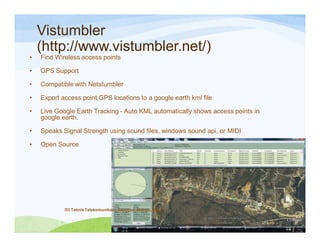
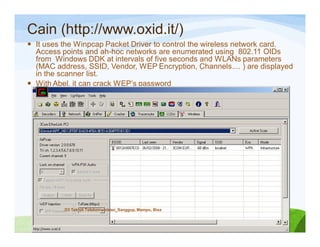
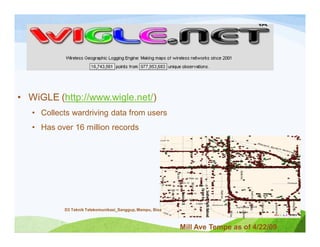
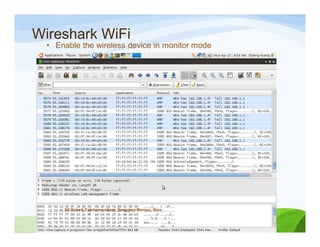
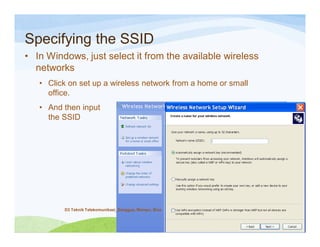
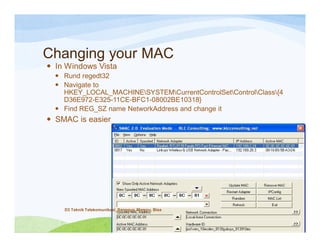
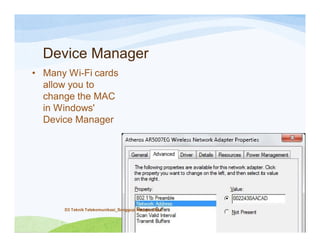
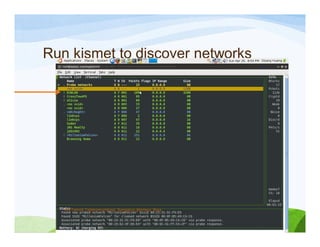
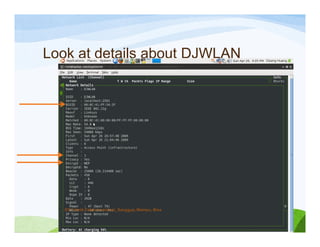
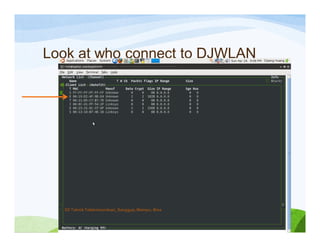
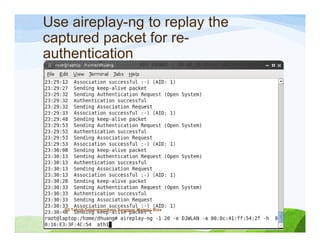
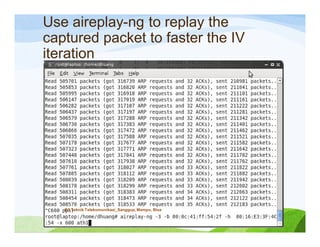
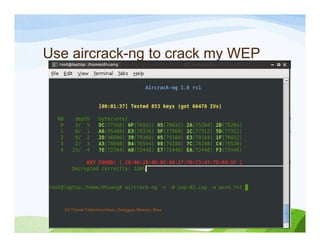
The document discusses various topics related to wireless hacking and security. It compares the advantages and disadvantages of using Windows versus Linux for wireless hacking. It also discusses wireless hacking tools like Kismet, NetStumbler, and OmniPeek. The document talks about different wireless network defenses that can be identified like SSID broadcasting and MAC address filtering. It also covers different attacks against wireless security protocols like WEP cracking using tools like Aircrack-ng. The vulnerabilities of wireless protocols like LEAP are explained along with tools to exploit them like Anwrap and Asleap. Finally, it discusses strong security protocols like WPA/WPA2 and denial of service attacks against wireless networks.