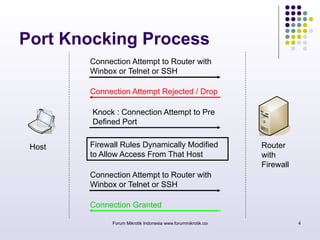
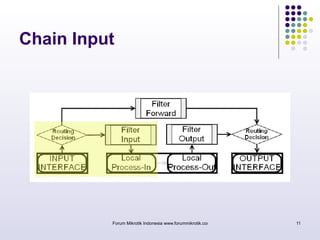
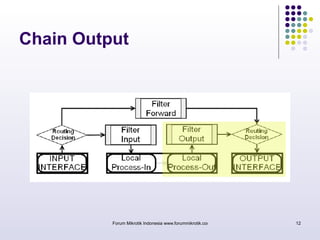
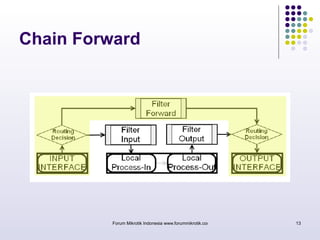
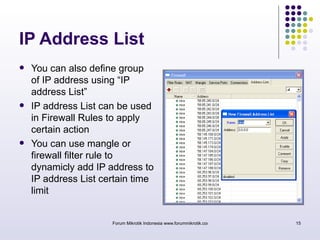
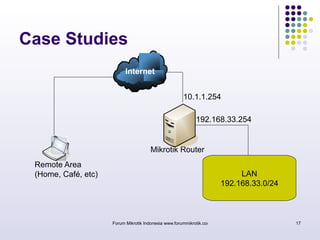
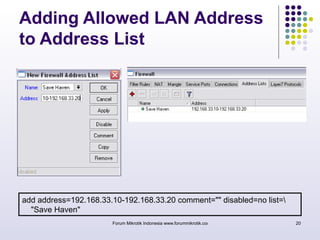
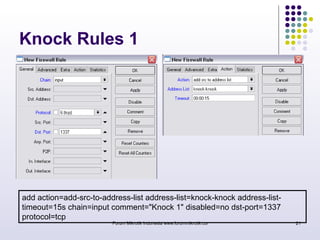
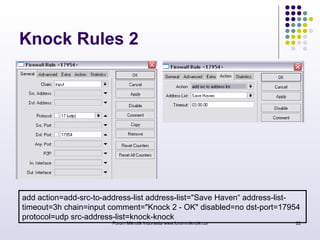
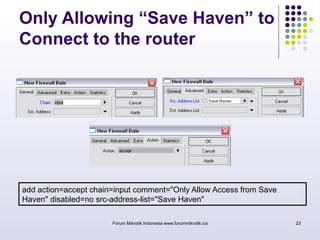
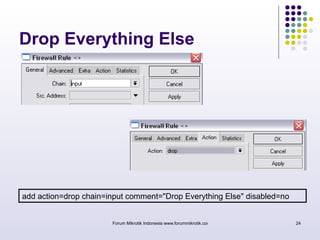
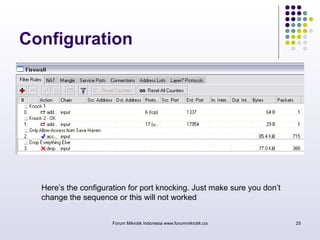
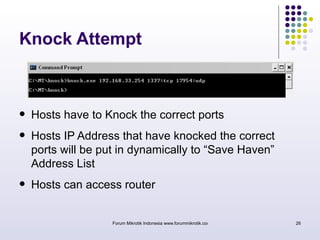
The document discusses port knocking as a security method for routers, allowing access only after a correct sequence of connection attempts on closed ports. It outlines the implementation process in MikroTik, including configuring firewall filters and address lists, and details on how to use the knock application. While effective in preventing unauthorized access, it also notes potential weaknesses such as susceptibility to sequence sniffing and the need for specialized clients.