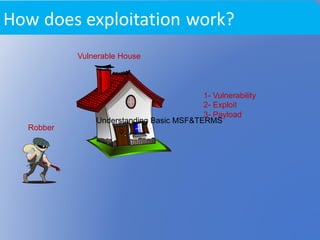
This document provides an overview of network exploitation and the Metasploit framework. It begins with definitions of key terms like vulnerability, exploit, and payload. It then explains the basic process of exploitation as using an exploit to trigger a payload after a vulnerability is triggered. The document outlines common steps attackers use like port scanning and service identification. It introduces the Metasploit framework as an open-source tool for penetration testing and exploit development with over 770 tested exploits and 228 payloads. It concludes with examples of using tools like nmap for port scanning and compiling exploits to demonstrate exploitation of a known vulnerability.








![Commands detail in
Demontration(Vulnerability on RPC
DCOM(MS03_026))
- Scan a machine using tools like “nmap”
root@khnog#nmap –v –n [Target-IP]
root@khnog#nmap –sV –n [Target-IP]
- root@khnog#gcc dcom -0 dcom (compile
file)
- root@khnog#./dcom [target-ID] [target-IP]](https://image.slidesharecdn.com/network-exploitation-161028015841/85/Network-Exploitation-10-320.jpg)
