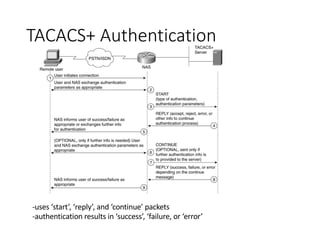
This document provides an overview of TACACS+ (Terminal Access Controller Access Control System Plus), which is a protocol and software that provides AAA (authentication, authorization, and accounting) services to network devices. It discusses how TACACS+ separates AAA functions, encrypts traffic between devices, and uses TCP port 49 for communication. Key aspects of TACACS+ authentication, authorization, and accounting are outlined. The document also demonstrates TACACS+ in action using Cisco IOS XR Virtual and CentOS and provides references for further information.