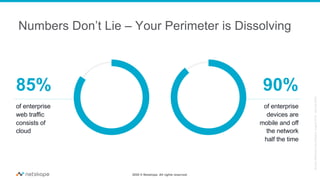
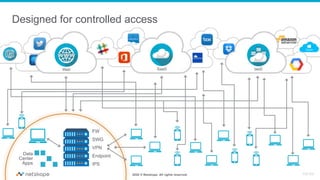
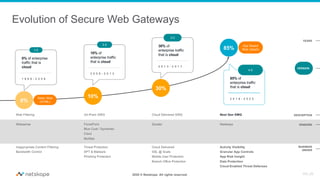
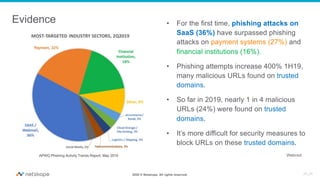
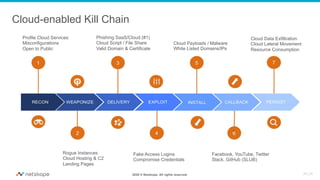
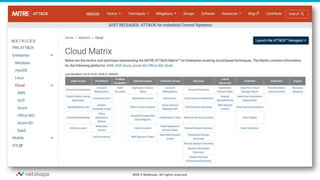
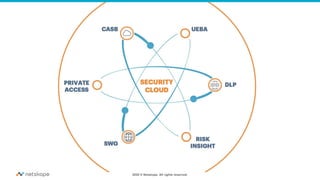
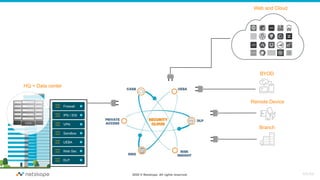
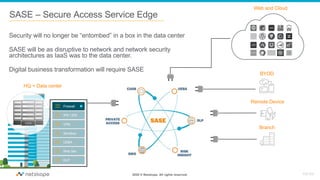
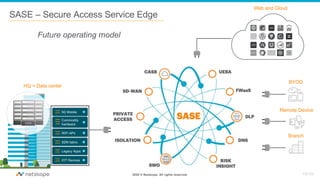
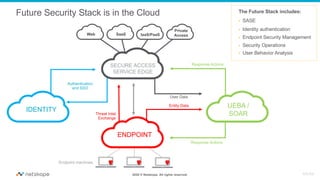
The document discusses the transformation of network security due to the increasing use of cloud services and the shift towards a cloud-first security approach. It highlights that 85% of enterprise web traffic is now cloud-based, leading to rising concerns around phishing and security misconfigurations. The recommended solution is the adoption of Secure Access Service Edge (SASE) architecture to better secure cloud and mobile environments.