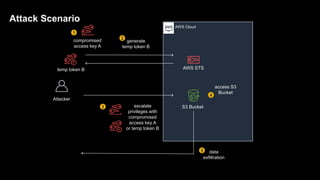
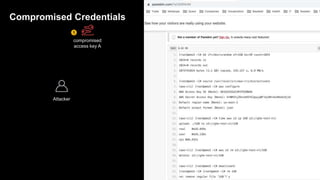
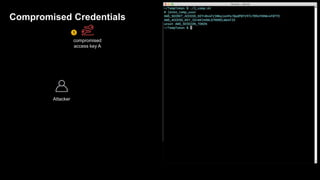
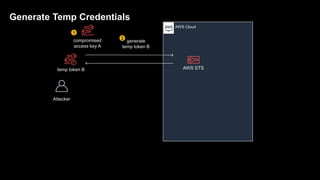
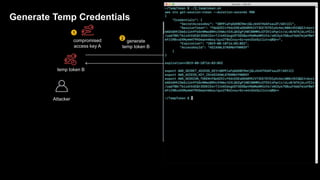
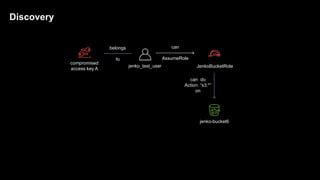
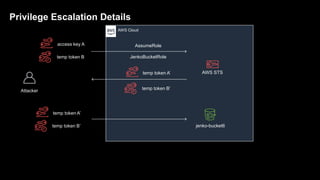
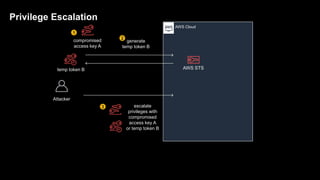
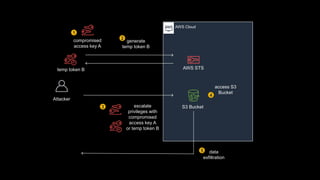
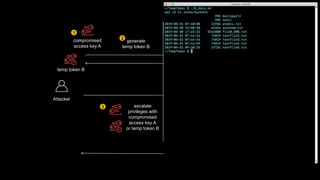
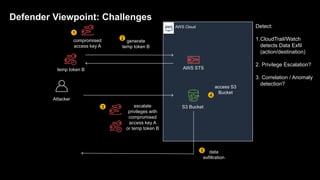
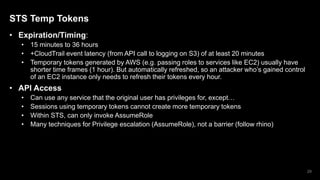
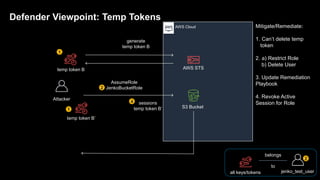
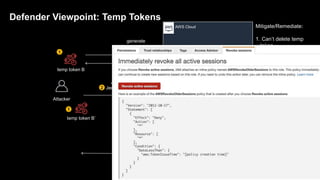
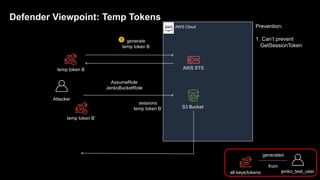
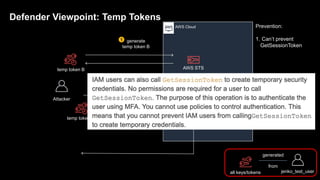
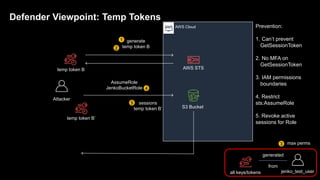
1. The document discusses how attackers can exploit AWS temporary credentials to escalate privileges and extract data from S3 buckets. It involves compromising an initial access key, generating a temporary token via STS, and using that token or the original key to assume roles or directly access resources.
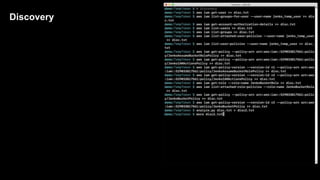
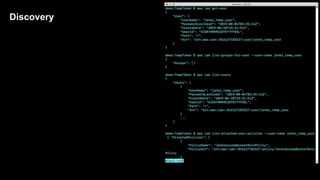
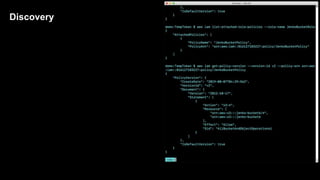
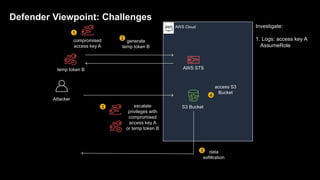
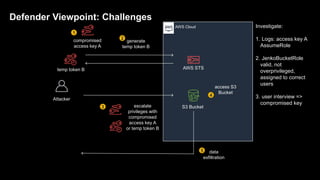
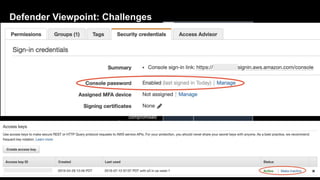
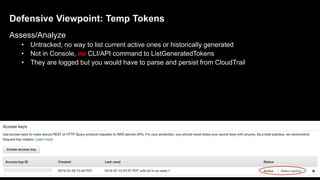
2. Defenders face challenges in detecting these attacks as temporary tokens are not tracked or listed, and privilege escalation may not be obvious from CloudTrail logs. Investigations require piecing together evidence from logs of the initial access key and assumed roles.
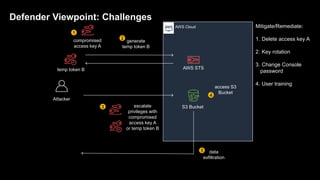
3. The document provides recommendations for defenders to better detect, prevent, and mitigate risks from temporary credentials, such as monitoring for their creation and usage, restricting permissions for credential roles,