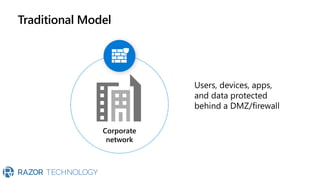
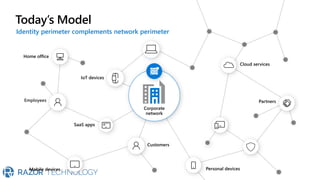
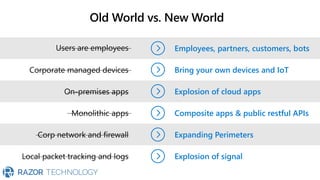
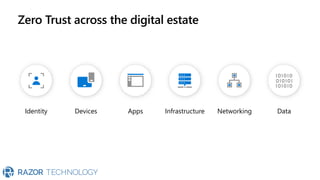
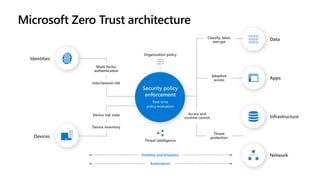
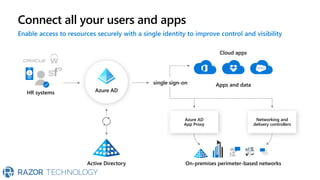
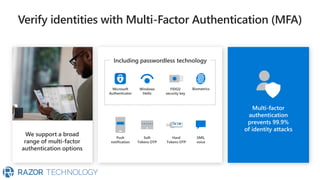
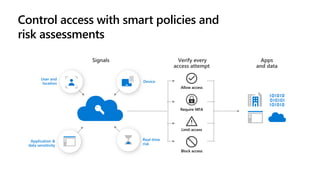
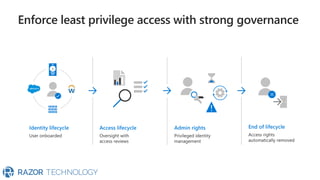
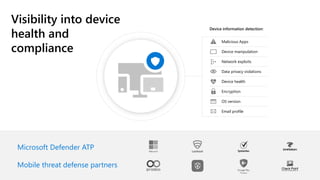
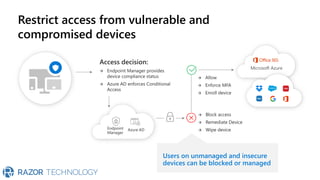
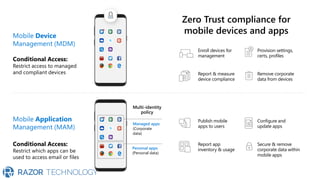
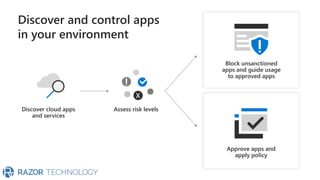
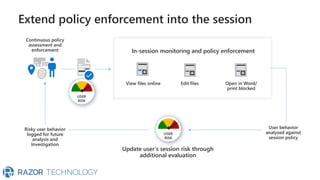
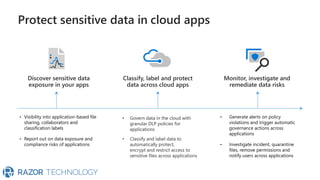
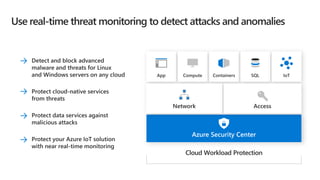
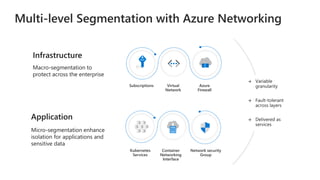
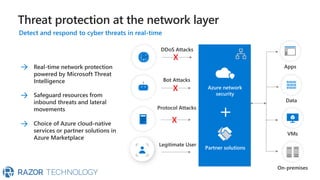
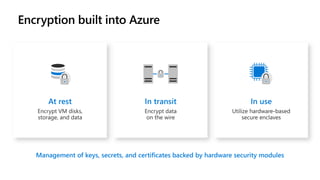
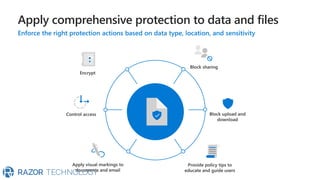
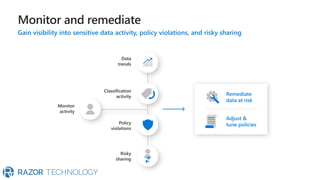
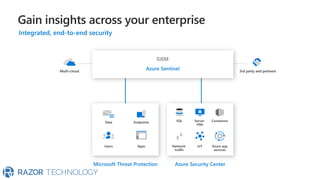
The document discusses Microsoft's zero trust architecture, which emphasizes verifying identities and securing access across a digital estate in response to the evolving landscape of cloud apps and mobile devices. It outlines various strategies for device compliance, application control, and data protection, aiming to enhance security through real-time threat monitoring, segmentation strategies, and robust policies. The zero trust model focuses on establishing secure connections for users and applications while enforcing strict access controls and compliance measures.