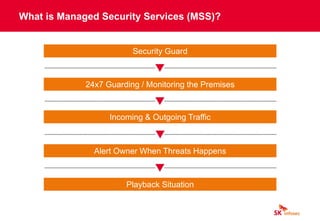
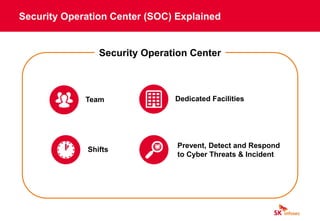
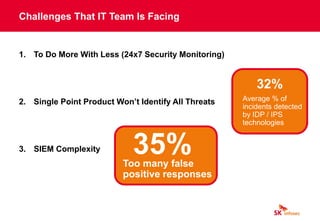
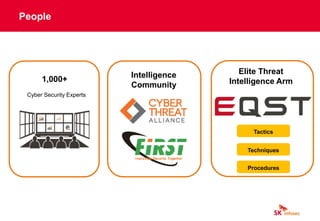
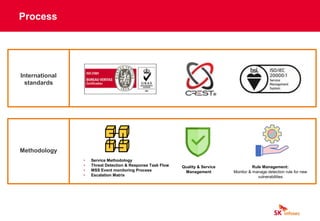
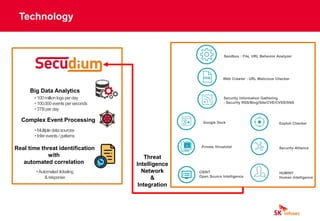
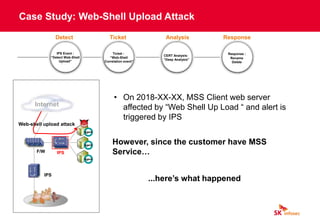
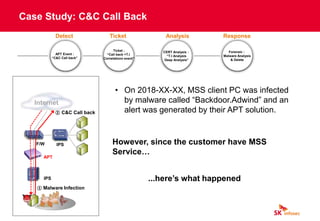
The document discusses cybersecurity threats like ransomware, phishing, and data theft that can disrupt business operations and cause monetary or reputational losses. It then describes how a managed security services provider like SK infosec can monitor networks and systems 24/7, detect and respond to cyber threats through security analytics and a security operations center, and help organizations facing challenges with limited security resources. Case studies are provided showing how SK infosec's managed security services protected clients from a web-shell upload attack and C&C callback as part of an advanced persistent threat.