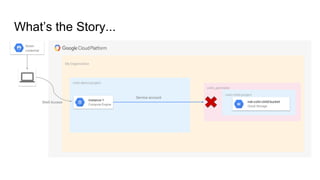
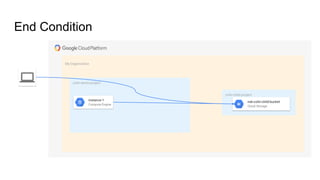
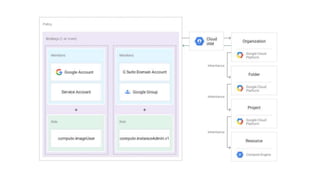
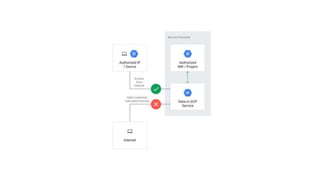
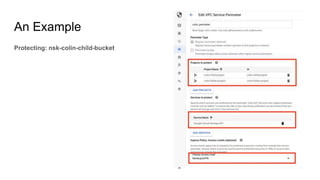
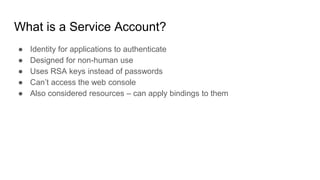
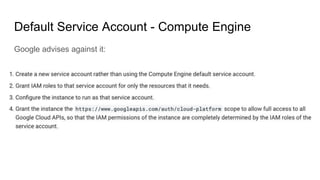
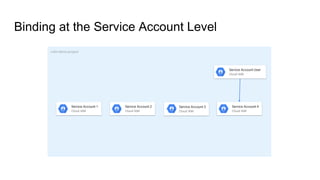
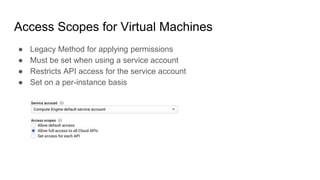
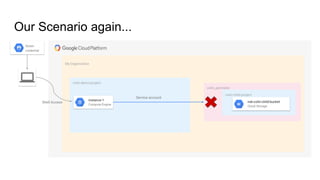
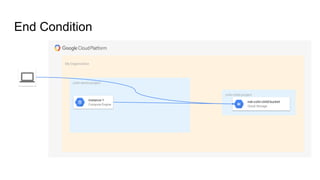
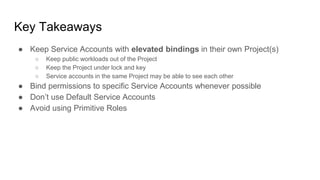
The document discusses exploiting identity and access management (IAM) in Google Cloud Platform (GCP). It begins with an introduction of the presenter and agenda. It then covers the key concepts of IAM in GCP, including role types, VPC service controls to control data flows, and access context manager. A deep dive on service accounts explains what they are, how bindings work, and the risk of impersonating service accounts. The demo illustrates a scenario where a stolen credential is used to impersonate a service account and access a storage bucket. Key takeaways recommend separating privileged service accounts, binding permissions at the account level, avoiding default accounts and primitive roles.