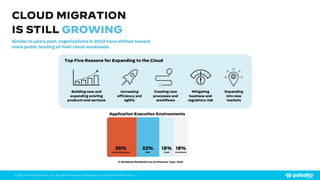
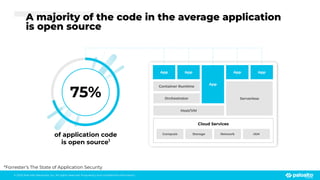
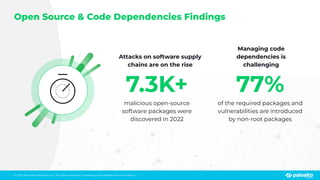
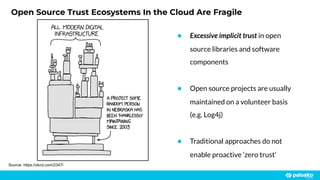
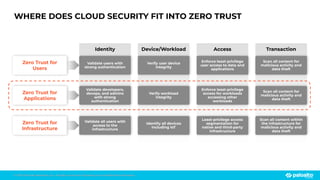
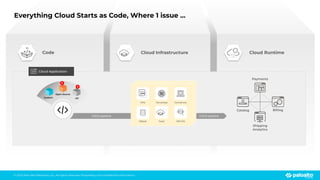
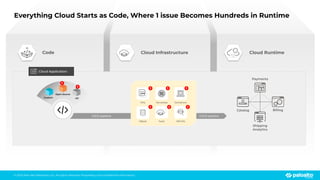
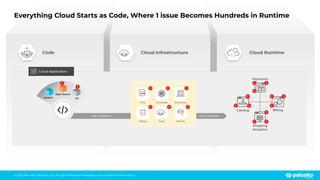
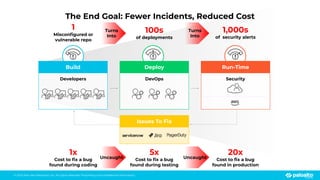
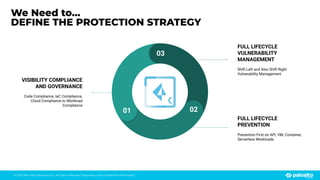
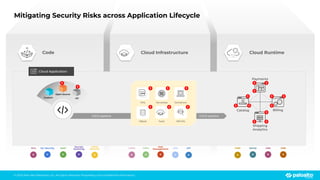
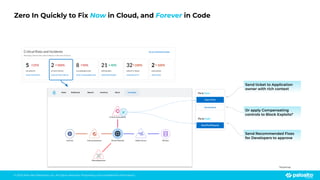
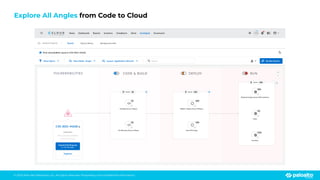
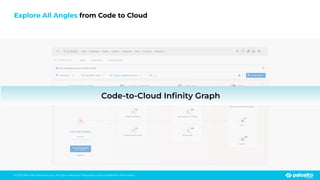
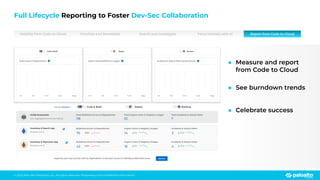
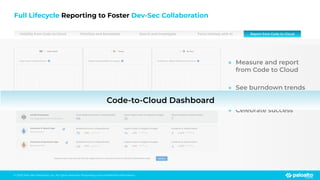
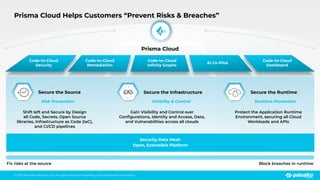
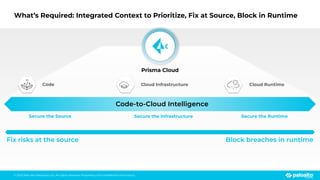
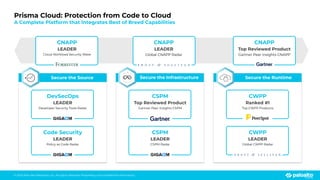
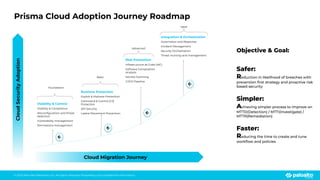
The document discusses the risks associated with open source code in cloud applications, highlighting that 75% of application code is open source and that 81% contain vulnerabilities. It advocates for a proactive zero trust strategy to secure applications, emphasizing the importance of risk prevention throughout the application lifecycle. Prisma Cloud offers solutions for comprehensive security across code, runtime, and infrastructure to manage vulnerabilities and incidents effectively.