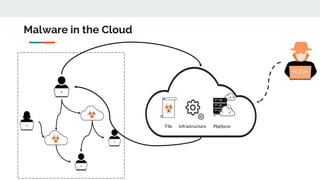
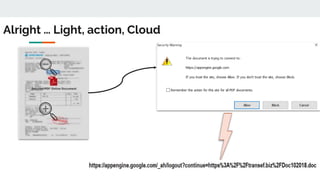
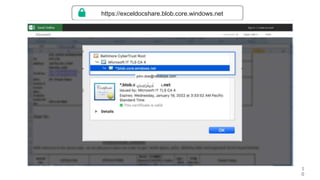
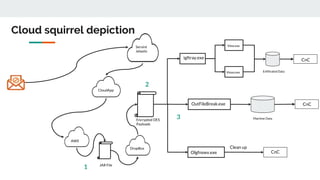
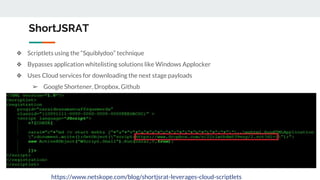
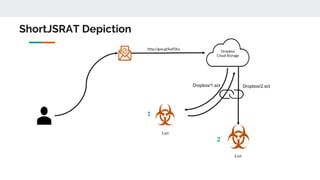
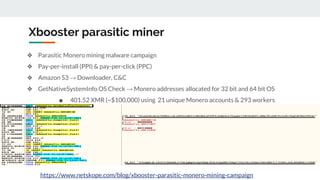
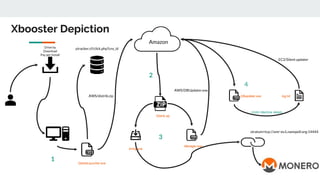
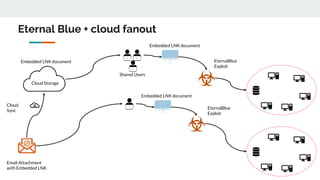
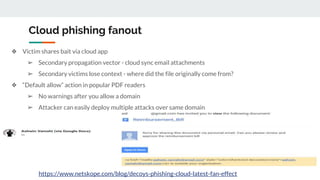
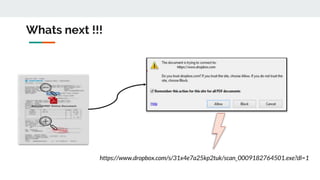
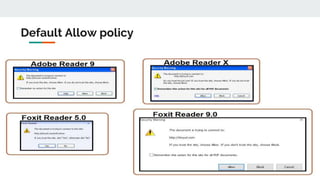
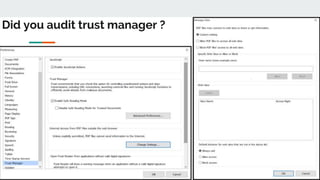
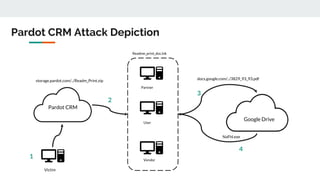
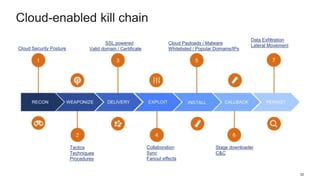
This document discusses how threat actors are increasingly using cloud services as an attack vector. It provides examples of malware campaigns that have used cloud services for hosting payloads, command and control, and spreading malware. Specifically, it outlines campaigns that have used Amazon S3, Dropbox, Google Drive and other cloud platforms at various stages of the attack lifecycle. The document recommends that organizations inspect cloud traffic, block unnecessary cloud services, and block unsanctioned instances of needed services to better protect their cloud security posture.