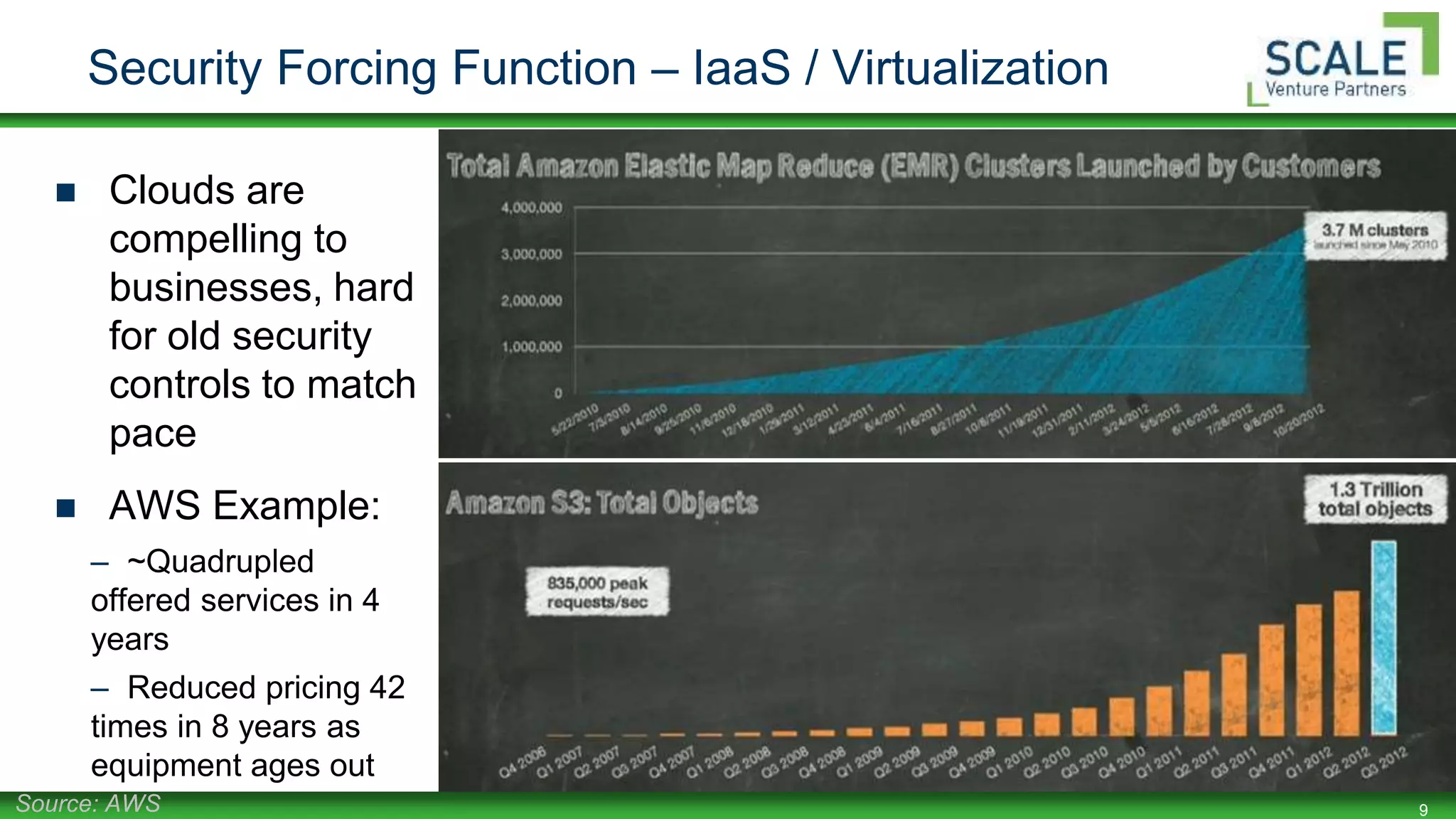
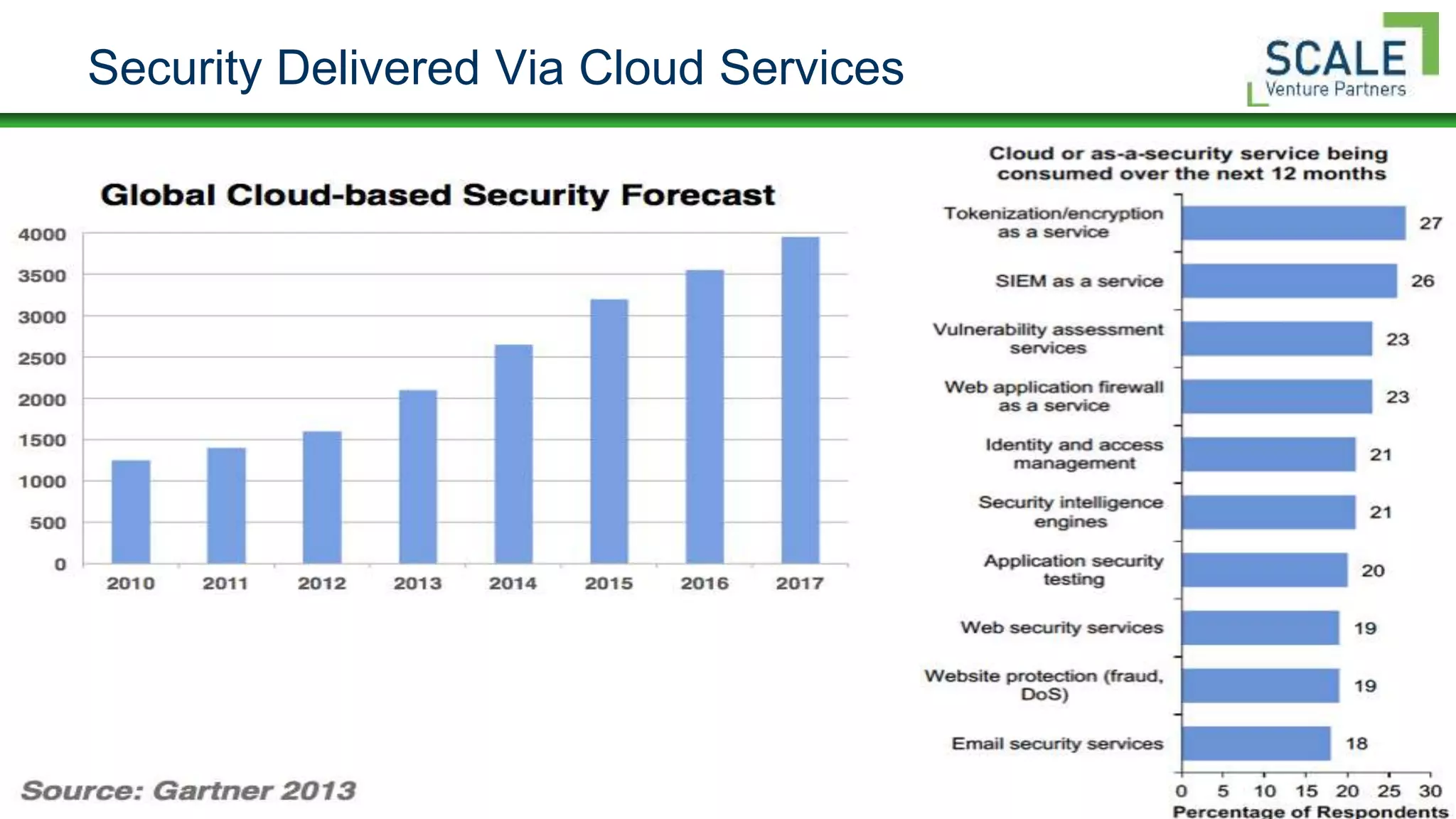
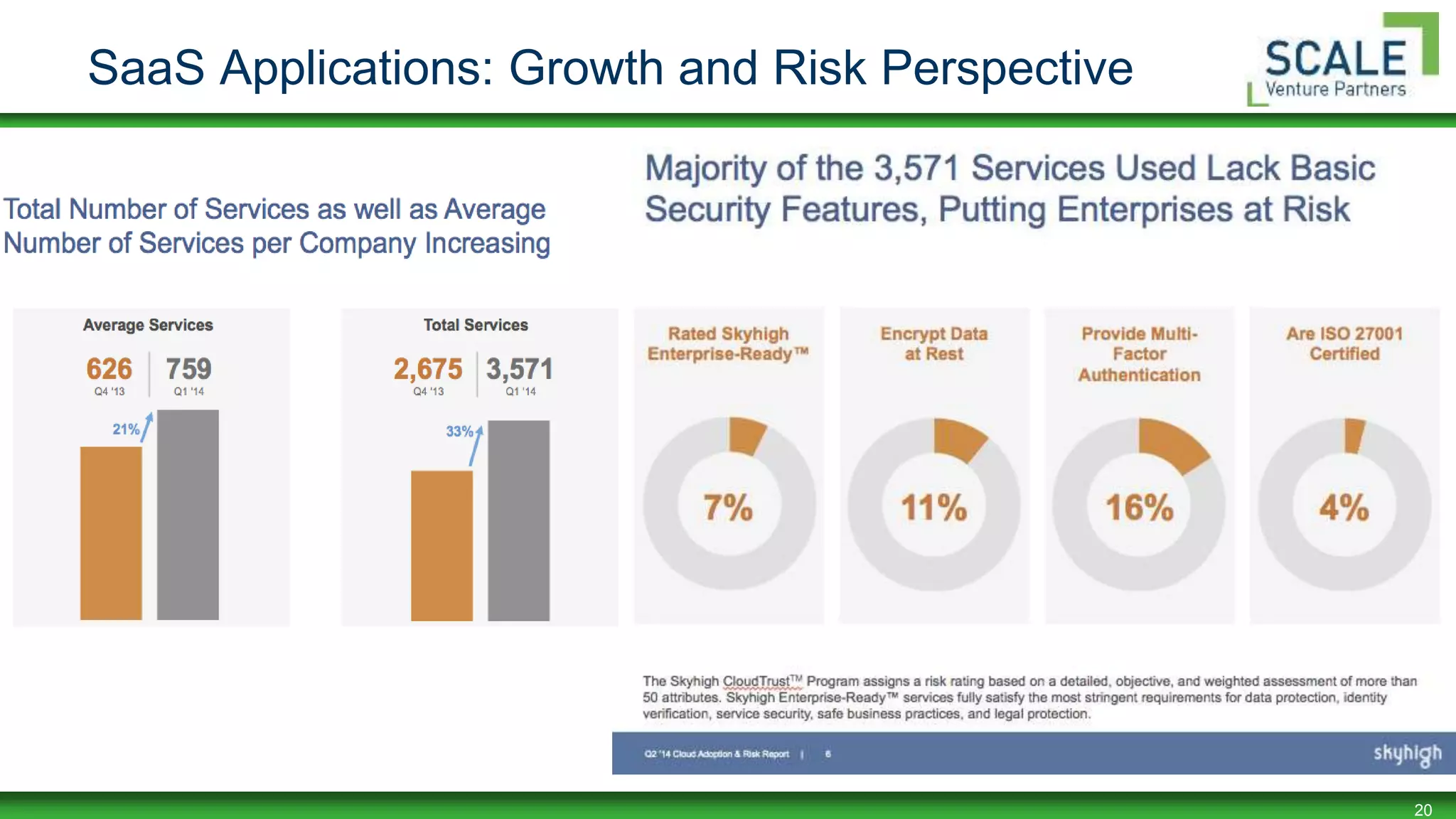
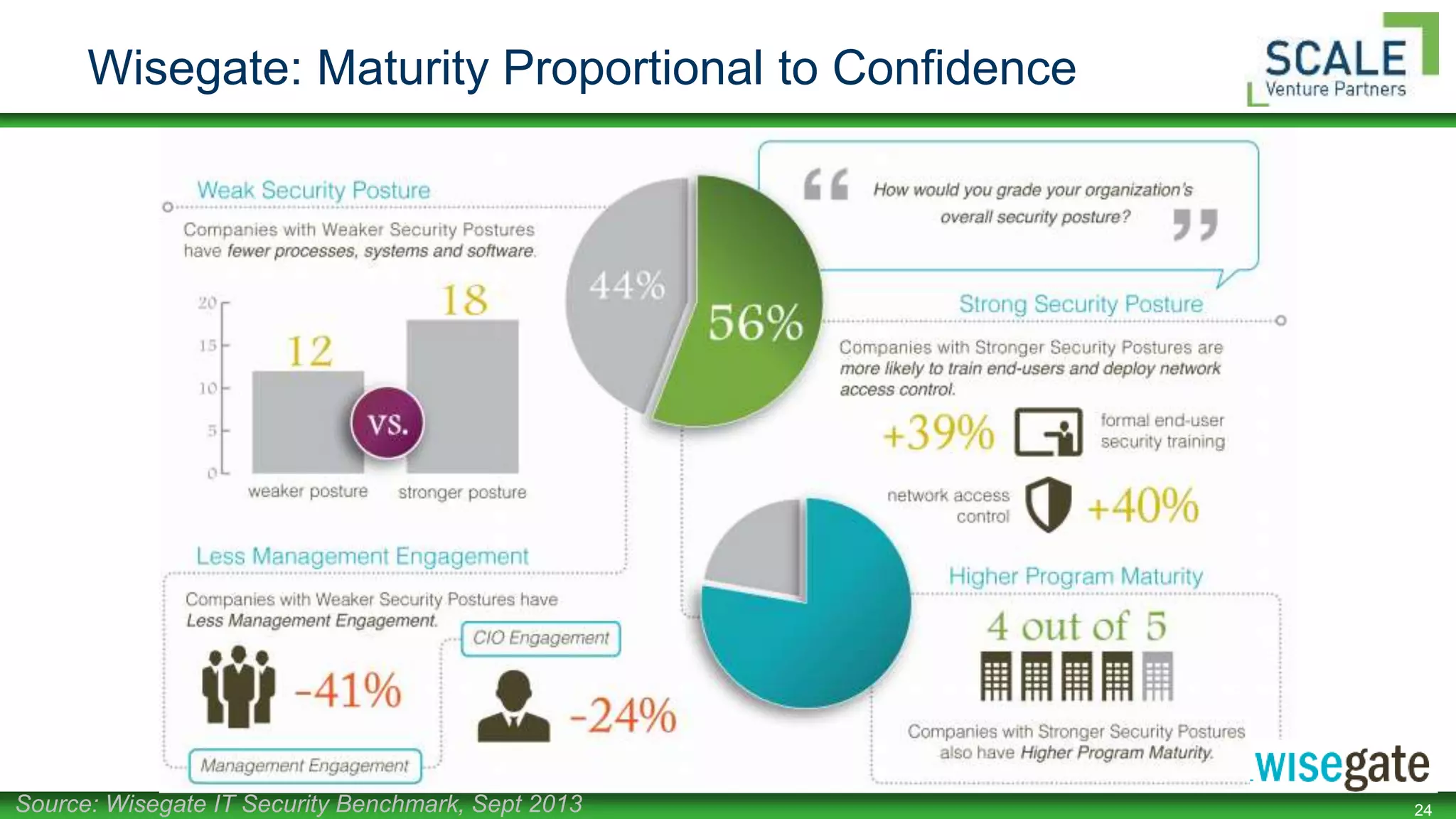
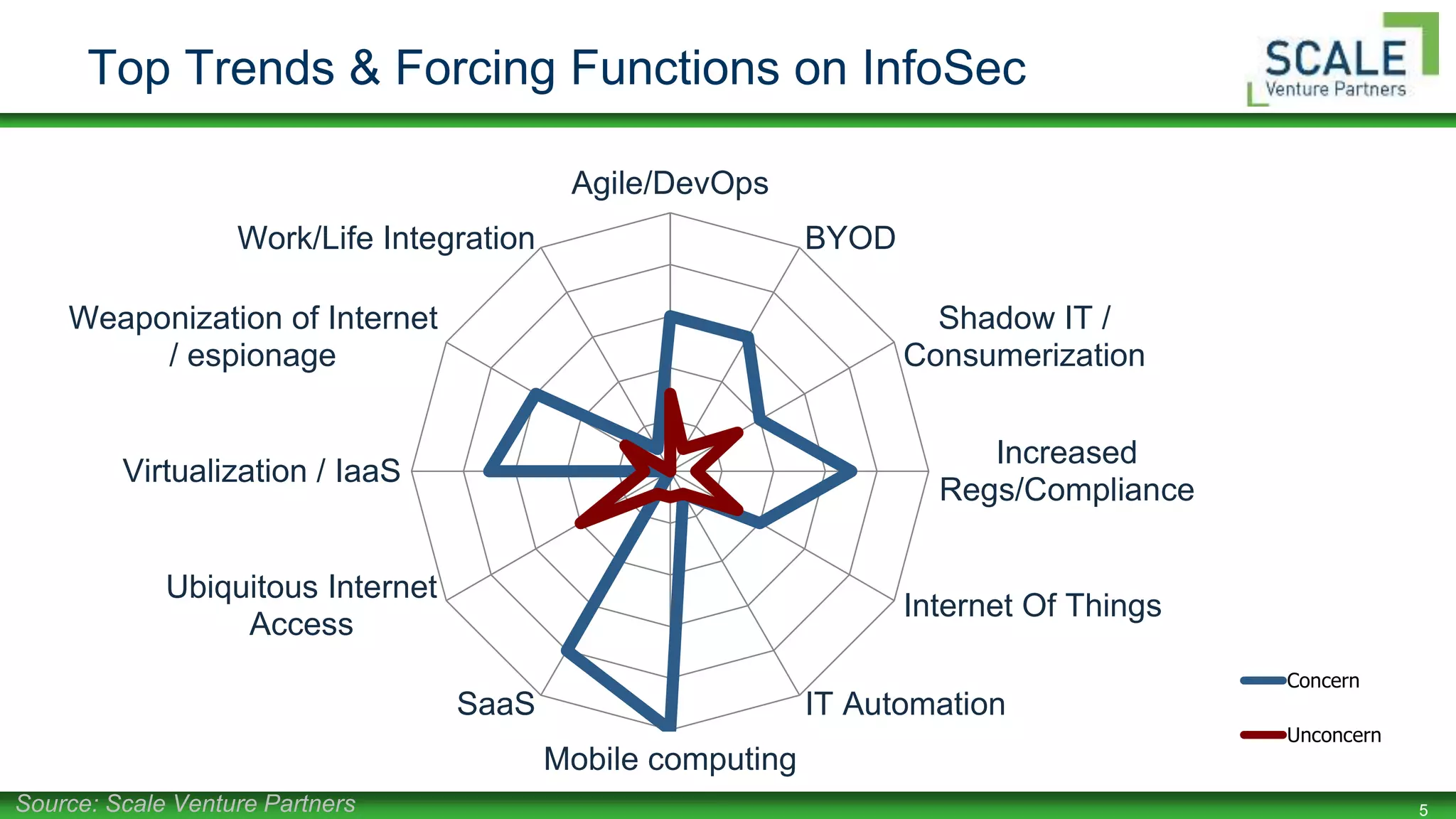
Bill Burns gave a presentation on factors that affect confidence in security programs. He discussed how mobility, BYOD, virtualization, and cloud computing are forcing changes to security controls and perimeters. As data moves to the cloud, security must follow and focus on being proximal, mobile, resilient, holistic, and coordinated. Building maturity in security programs through frameworks, metrics, and culture helps increase confidence. Early research shows higher maturity programs have more confidence.




![7
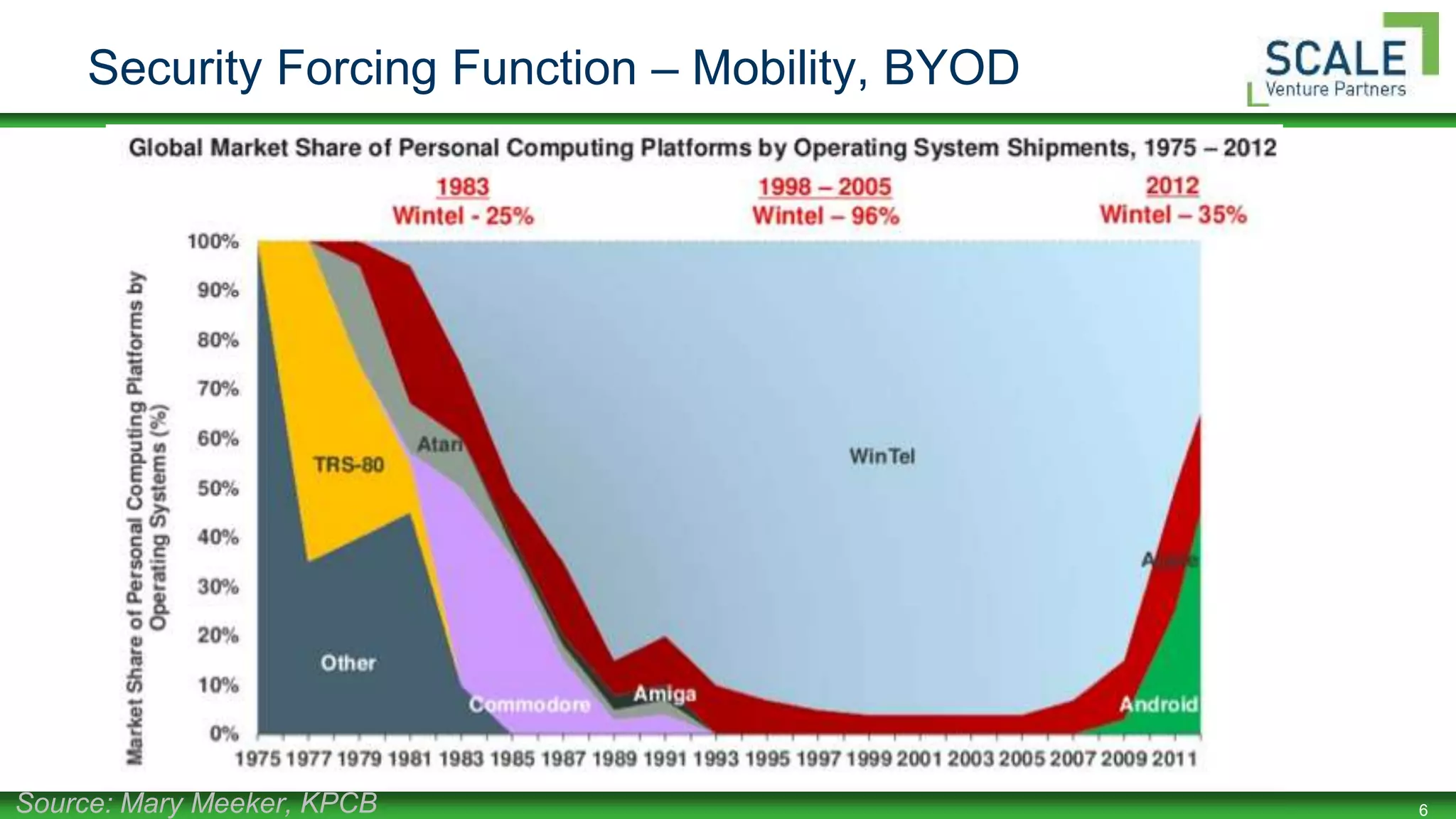
Security Forcing Function – Mobility, BYOD
(1) Pew Research, Jan 2014 | (2) Gartner, May 2013
Smartphone - 58%
Tablet - 42%
By 2017, 50% of employers will
require you to BYOD[2] for
work.](https://image.slidesharecdn.com/rmisc-whataffectssecurityprogramconfidence-may2014-billburns-140528151155-phpapp01/75/What-affects-security-program-confidence-may2014-bill-burns-7-2048.jpg)
![8
Security Forcing Function – Work Anywhere
Blurring work/life integration
– Aruba’s “#GenMobile”initiative
– Starbucks wants to be your life’s “3rd Place”
Ubiquitous network access & seamless roaming
– 802.11ac, n – wireless networking “just works”
• Faster than typical wired ports, easier to provision
– Mobile 4G LTE is also “fast enough”
• Faster than my home’s DSL
– By 2018: 25% of corporate data will flow directly mobile-cloud[3]
(3) Gartner, Nov 2013](https://image.slidesharecdn.com/rmisc-whataffectssecurityprogramconfidence-may2014-billburns-140528151155-phpapp01/75/What-affects-security-program-confidence-may2014-bill-burns-8-2048.jpg)