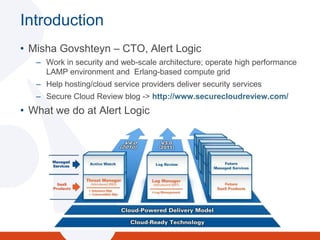
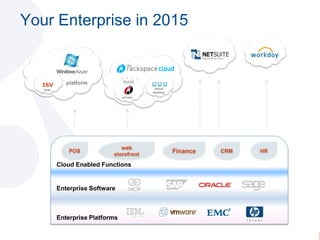
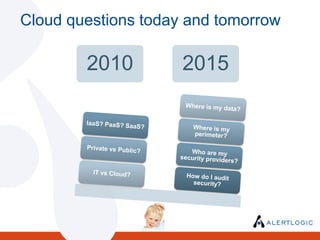
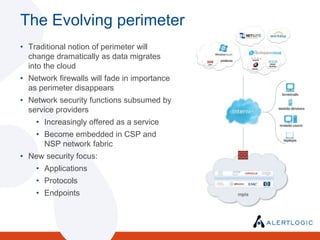
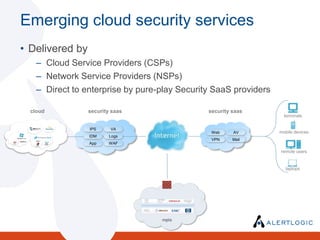
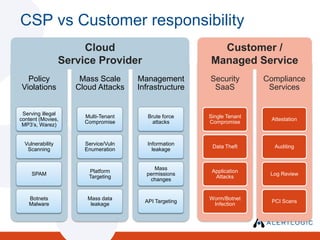
The document discusses the evolving landscape of security and compliance in cloud computing, emphasizing the shift towards IT as a service and the need for organizations to adapt their security strategies. It highlights the increasing responsibility of cloud service providers for data security and the changing nature of network perimeters, as more critical data moves offsite. Additionally, it outlines trends in compliance and governance in cloud environments, suggesting that organizations must engage with security and auditing processes to navigate these changes effectively.