Summer 2015 EMEA Netskope Cloud Report
•
0 likes•2,976 views
In this edition of the Netskope Cloud Report infographic for Europe, Middle East, and Africa, we've compiled the most interesting trends on cloud app adoption and usage based on aggregated, anonymized data from the Netskope Active Platform.
Report
Share
Report
Share
Download to read offline
Recommended
Summer 2015 Worldwide Netskope Cloud Report

In this Netskope Cloud Report infographic, we've compiled the most interesting trends on cloud app adoption and usage based on aggregated, anonymized data from the Netskope Active Platform.
The Internet of Security Things (A Story about Change) 

Lots of change is impacting security. This presentation looks at four key security concerns that are most impacted by application and technology trends and what we can look for in solutions to address those concerns.
Stop Hackers with Integrated CASB & IDaaS Security

Watch this on-demand webinar with CloudLock and OneLogin to: Identify the top five cyber threats to your cloud environment; Protect against cloud security risks using advanced user and entity behavior analysis; Streamline identity and access management; Easily automate your cloud access management process.
Codeless Security for the Apps You Buy & Build on AWS

Watch this webinar to learn what codeless security looks like for the cloud apps you build. Codeless - that means baking in security capabilities to defend your custom apps against data breaches without having to write a single line of code.
Be A Hero: Combat Cloud Security Threats with Google Apps Unlimited & CloudLock

According to the latest IBM X-Force Research report, the average consolidated total cost of a single data breach is $3.8 million. And with data breaches up 22% so far in 2016, across every vertical imaginable, the threat must be addressed. Watch Google and CloudLock's discussion in this hands-on exploration of how your organization can combat these ever changing security threats.
Are Cloud Apps the Invisible Man?

View Demo: https://securityintelligence.com/events/are-cloud-apps-the-invisible-man/
IBM Cloud Security Enforcer is the first solution to combine Cloud Access Security Broker (CASB) functionality with Identity-as-a-Service (IDaaS), policy enforcement, and dynamic threat prevention intelligence into a single integrated SaaS solution.
Join IBM Security’s Chief Architect for Cloud Security, Patrick Wardrop, as he demonstrates how IBM Cloud Security Enforcer accelerates and safeguards adoption of cloud applications in the enterprise.
In this demo, you will learn how to:
- Discover invisible cloud applications and Shadow IT being used in your organization
- Quickly and securely connect your users to sanctioned cloud applications
- Close the mobile blind spot and prevent threats as users connect to cloud apps via mobile devices
Introducing IBM Cloud Security Enforcer, CASB, IDaaS and Threat Prevention

View on demand webinar:
https://securityintelligence.com/events/introducing-ibm-cloud-security-enforcer-casb-idaas-and-threat-prevention/
Cloud Security Enforcer is the first solution to combine Cloud Access Security Broker (CASB) functionality with identity services (IDaaS), policy enforcement and dynamic threat prevention intelligence into a single integrated SaaS solution.
Join Daniel Wolff, Program Director Cloud Security Product Management, and Gonzalo de la Hoz, IAM European Segment Leader, as we discuss how IBM Cloud Security Enforcer has integrated multiple technologies crucial to enabling safe adoption of cloud applications in the enterprise:
- Cloud application discovery and risk
- Cloud identity services and application on-boarding
- Closing the mobile device gap
- Policy enforcement and threat prevention
Why you need to secure mobile apps - now

No matter what size of company you’re at, you probably have a work phone. It might not have been given to you by your company, but you use it for work in one way or another. That means there is company data on your phone. Why do companies need a solution that secures the apps rather than the device – so employees can have the freedom and flexibility they need to get their work done.
Recommended
Summer 2015 Worldwide Netskope Cloud Report

In this Netskope Cloud Report infographic, we've compiled the most interesting trends on cloud app adoption and usage based on aggregated, anonymized data from the Netskope Active Platform.
The Internet of Security Things (A Story about Change) 

Lots of change is impacting security. This presentation looks at four key security concerns that are most impacted by application and technology trends and what we can look for in solutions to address those concerns.
Stop Hackers with Integrated CASB & IDaaS Security

Watch this on-demand webinar with CloudLock and OneLogin to: Identify the top five cyber threats to your cloud environment; Protect against cloud security risks using advanced user and entity behavior analysis; Streamline identity and access management; Easily automate your cloud access management process.
Codeless Security for the Apps You Buy & Build on AWS

Watch this webinar to learn what codeless security looks like for the cloud apps you build. Codeless - that means baking in security capabilities to defend your custom apps against data breaches without having to write a single line of code.
Be A Hero: Combat Cloud Security Threats with Google Apps Unlimited & CloudLock

According to the latest IBM X-Force Research report, the average consolidated total cost of a single data breach is $3.8 million. And with data breaches up 22% so far in 2016, across every vertical imaginable, the threat must be addressed. Watch Google and CloudLock's discussion in this hands-on exploration of how your organization can combat these ever changing security threats.
Are Cloud Apps the Invisible Man?

View Demo: https://securityintelligence.com/events/are-cloud-apps-the-invisible-man/
IBM Cloud Security Enforcer is the first solution to combine Cloud Access Security Broker (CASB) functionality with Identity-as-a-Service (IDaaS), policy enforcement, and dynamic threat prevention intelligence into a single integrated SaaS solution.
Join IBM Security’s Chief Architect for Cloud Security, Patrick Wardrop, as he demonstrates how IBM Cloud Security Enforcer accelerates and safeguards adoption of cloud applications in the enterprise.
In this demo, you will learn how to:
- Discover invisible cloud applications and Shadow IT being used in your organization
- Quickly and securely connect your users to sanctioned cloud applications
- Close the mobile blind spot and prevent threats as users connect to cloud apps via mobile devices
Introducing IBM Cloud Security Enforcer, CASB, IDaaS and Threat Prevention

View on demand webinar:
https://securityintelligence.com/events/introducing-ibm-cloud-security-enforcer-casb-idaas-and-threat-prevention/
Cloud Security Enforcer is the first solution to combine Cloud Access Security Broker (CASB) functionality with identity services (IDaaS), policy enforcement and dynamic threat prevention intelligence into a single integrated SaaS solution.
Join Daniel Wolff, Program Director Cloud Security Product Management, and Gonzalo de la Hoz, IAM European Segment Leader, as we discuss how IBM Cloud Security Enforcer has integrated multiple technologies crucial to enabling safe adoption of cloud applications in the enterprise:
- Cloud application discovery and risk
- Cloud identity services and application on-boarding
- Closing the mobile device gap
- Policy enforcement and threat prevention
Why you need to secure mobile apps - now

No matter what size of company you’re at, you probably have a work phone. It might not have been given to you by your company, but you use it for work in one way or another. That means there is company data on your phone. Why do companies need a solution that secures the apps rather than the device – so employees can have the freedom and flexibility they need to get their work done.
3 Reasons You Need Proactive Protection Against Malware

3 Reasons You Need Proactive Protection Against Malware
Case Closed with IBM Application Security on Cloud infographic

This infographic demonstrates how to leverage IBM Application Security Analyzer (formerly IBM AppScan Mobile Analyzer and IBM AppScan Dynamic Analyzer) to improve mobile and Web application security, by performing periodic application security testing, identifying high-priority vulnerabilities and improving the effectiveness of your application security program. You’ll also have the peace of mind that’s derived by eliminating security vulnerabilities from Web and mobile applications before they’re placed into production and deployed.
For additional information, please visit: www.ibm.com/applicationsecurity.
Securing Governing and Protecting Your Office 365 Investments

Microsoft continues to invest in services and capabilities to help you protect, detect, and respond to a variety of emerging security and compliance needs for Office 365. Come to this session for an interactive scenario based whiteboard and demonstration of how you can implement comprehensive controls based on a variety of dimensions across the identity of the user; their location and device; and the application, service, and content they are accessing.
Infographic network protection security

Is your network security limited to defending against yesterday’s threats? IBM Security Network Protection delivers the next-generation security, visibility and control needed to help you with zero-day threat protection.
Ikano Google Apps Partner Edition.Ppt

Google Apps Partner Edition from IKANO Communications Inc.
www.ikano.com/googleapps
Patches Arrren't Just for Pirates

The web can be a dangerous place. Software that has code defects, also known as vulnerabilities, pose serious risks to users – from the most casual Internet surfers to business owners.
State of Application Security Vol. 4

Arxan Technologies inforgraphic on the current state of application security.
The state of mobile app security 

This infographic talks about the latest in mobile app security, the challenges and the best practices to tackle them by building secure mobile apps.
Secure Access to Your Enterprise

With Azure Active Directory, you can:
Connect your workforce to ANY app and boost productivity for both end users and IT by providing seamless, secure access and scalable management of apps.
Secure and govern access for any type of user (employee, guest, customer) by enforcing strong authentication and conditional access policies while ensuring that the right users have access to the right resources.
Engage your customers and partners with a flexible, scalable identity and access-management solution.
Integrate identity into any app to accelerate adoption and increase stickiness with reduced sign-in friction and simplified management of user accounts, accomplished through single sign-on and user provisioning.
TiEcon 2016 Keynote - Security Challenges & Opportunities with Public Cloud A...

TiEcon 2016 Keynote - Security Challenges & Opportunities with Public Cloud A...Ravinder Reddy Amanaganti
Security Challenges and Opportunities with Public Cloud Adoption 5 Ways to Protect your Mobile Security

As the world becomes more connected, security needs to be at the forefront of people’s minds as they use mobile devices to live every day life. Here are 5 things to consider when using your mobile device.
How Aligned Are IT, Employees and Security Practices in Today's Mobile World?

Gartner projects almost 4 in 10 organizations will rely exclusively on BYOD by 2016, and 85 percent of businesses will allow some level of BYOD by 2020. If enterprises want peace of mind with regard to the security of their data and systems, they must understand employee perceptions and practices. Blurred lines between personal and work use impacts security and puts corporate data at risk.
Apteligent - Choosing the Right SDKs to Optimize App Performance

A typical app has 15 different SDKs. Our Apteligent expert gives you a guide on how to choose the right SDK that doesn't cause the app to crash, slow down, or drain the battery.
Cyber Security at Microsoft - Henkel Keynote Speaker Anton Neidel

Microsoft offers a broad range of products and services which we use at Henkel and also in our private life. Let´s hear from them why cyber security is of strategic importance for their company, where do they see dangers for the future and how is this translated into the security of their products.
Fall 2015 Worldwide Netskope Cloud Report 

In this Netskope Cloud Report infographic, we've compiled the most interesting trends on cloud app adoption and usage based on aggregated, anonymized data from the Netskope Active Platform.
Lions, Tigers, and PHI, Oh My! The latest in data loss prevention in the cloud.

Let’s face it: When it comes to data loss prevention, we’re not in Kansas anymore. Any and all types of sensitive business data is now stored in the cloud and accessed from personal devices and most of the time, IT doesn’t even know it. This presentation is from a webinar with our guest speaker Forrester VP and Principal Analyst John Kindervag and Netskope VP of Product Management Rajneesh Chopra. In it, they explore the following:
- Trends surrounding cloud and data loss prevention
- How on-premises DLP users have helped shape the design of new, cloud-based solutions
- Key architectural considerations for enterprises who have invested in on-premises DLP
- Pitfalls that every IT security professional should look out for when developing a cloud DLP strategy
More Related Content
What's hot
3 Reasons You Need Proactive Protection Against Malware

3 Reasons You Need Proactive Protection Against Malware
Case Closed with IBM Application Security on Cloud infographic

This infographic demonstrates how to leverage IBM Application Security Analyzer (formerly IBM AppScan Mobile Analyzer and IBM AppScan Dynamic Analyzer) to improve mobile and Web application security, by performing periodic application security testing, identifying high-priority vulnerabilities and improving the effectiveness of your application security program. You’ll also have the peace of mind that’s derived by eliminating security vulnerabilities from Web and mobile applications before they’re placed into production and deployed.
For additional information, please visit: www.ibm.com/applicationsecurity.
Securing Governing and Protecting Your Office 365 Investments

Microsoft continues to invest in services and capabilities to help you protect, detect, and respond to a variety of emerging security and compliance needs for Office 365. Come to this session for an interactive scenario based whiteboard and demonstration of how you can implement comprehensive controls based on a variety of dimensions across the identity of the user; their location and device; and the application, service, and content they are accessing.
Infographic network protection security

Is your network security limited to defending against yesterday’s threats? IBM Security Network Protection delivers the next-generation security, visibility and control needed to help you with zero-day threat protection.
Ikano Google Apps Partner Edition.Ppt

Google Apps Partner Edition from IKANO Communications Inc.
www.ikano.com/googleapps
Patches Arrren't Just for Pirates

The web can be a dangerous place. Software that has code defects, also known as vulnerabilities, pose serious risks to users – from the most casual Internet surfers to business owners.
State of Application Security Vol. 4

Arxan Technologies inforgraphic on the current state of application security.
The state of mobile app security 

This infographic talks about the latest in mobile app security, the challenges and the best practices to tackle them by building secure mobile apps.
Secure Access to Your Enterprise

With Azure Active Directory, you can:
Connect your workforce to ANY app and boost productivity for both end users and IT by providing seamless, secure access and scalable management of apps.
Secure and govern access for any type of user (employee, guest, customer) by enforcing strong authentication and conditional access policies while ensuring that the right users have access to the right resources.
Engage your customers and partners with a flexible, scalable identity and access-management solution.
Integrate identity into any app to accelerate adoption and increase stickiness with reduced sign-in friction and simplified management of user accounts, accomplished through single sign-on and user provisioning.
TiEcon 2016 Keynote - Security Challenges & Opportunities with Public Cloud A...

TiEcon 2016 Keynote - Security Challenges & Opportunities with Public Cloud A...Ravinder Reddy Amanaganti
Security Challenges and Opportunities with Public Cloud Adoption 5 Ways to Protect your Mobile Security

As the world becomes more connected, security needs to be at the forefront of people’s minds as they use mobile devices to live every day life. Here are 5 things to consider when using your mobile device.
How Aligned Are IT, Employees and Security Practices in Today's Mobile World?

Gartner projects almost 4 in 10 organizations will rely exclusively on BYOD by 2016, and 85 percent of businesses will allow some level of BYOD by 2020. If enterprises want peace of mind with regard to the security of their data and systems, they must understand employee perceptions and practices. Blurred lines between personal and work use impacts security and puts corporate data at risk.
Apteligent - Choosing the Right SDKs to Optimize App Performance

A typical app has 15 different SDKs. Our Apteligent expert gives you a guide on how to choose the right SDK that doesn't cause the app to crash, slow down, or drain the battery.
Cyber Security at Microsoft - Henkel Keynote Speaker Anton Neidel

Microsoft offers a broad range of products and services which we use at Henkel and also in our private life. Let´s hear from them why cyber security is of strategic importance for their company, where do they see dangers for the future and how is this translated into the security of their products.
What's hot (20)
3 Reasons You Need Proactive Protection Against Malware

3 Reasons You Need Proactive Protection Against Malware
Case Closed with IBM Application Security on Cloud infographic

Case Closed with IBM Application Security on Cloud infographic
Securing Governing and Protecting Your Office 365 Investments

Securing Governing and Protecting Your Office 365 Investments
TiEcon 2016 Keynote - Security Challenges & Opportunities with Public Cloud A...

TiEcon 2016 Keynote - Security Challenges & Opportunities with Public Cloud A...
How Aligned Are IT, Employees and Security Practices in Today's Mobile World?

How Aligned Are IT, Employees and Security Practices in Today's Mobile World?
Apteligent - Choosing the Right SDKs to Optimize App Performance

Apteligent - Choosing the Right SDKs to Optimize App Performance
Cyber Security at Microsoft - Henkel Keynote Speaker Anton Neidel

Cyber Security at Microsoft - Henkel Keynote Speaker Anton Neidel
Viewers also liked
Fall 2015 Worldwide Netskope Cloud Report 

In this Netskope Cloud Report infographic, we've compiled the most interesting trends on cloud app adoption and usage based on aggregated, anonymized data from the Netskope Active Platform.
Lions, Tigers, and PHI, Oh My! The latest in data loss prevention in the cloud.

Let’s face it: When it comes to data loss prevention, we’re not in Kansas anymore. Any and all types of sensitive business data is now stored in the cloud and accessed from personal devices and most of the time, IT doesn’t even know it. This presentation is from a webinar with our guest speaker Forrester VP and Principal Analyst John Kindervag and Netskope VP of Product Management Rajneesh Chopra. In it, they explore the following:
- Trends surrounding cloud and data loss prevention
- How on-premises DLP users have helped shape the design of new, cloud-based solutions
- Key architectural considerations for enterprises who have invested in on-premises DLP
- Pitfalls that every IT security professional should look out for when developing a cloud DLP strategy
Netskope — Shadow IT Is A Good Thing

Shadow IT is often used in a derogatory manner, but what if the apps and services a company's employees are bringing into the enterprise were actually the secret to their success? What if the efficiency and productivity gains your company is experiencing are owed, in part, to these apps that IT isn't responsible for sourcing and enabling? In this presentation Netskope discusses the challenges and opportunities that come from the use of rogue apps in the enterprise and how IT can turn the corner and end the catch-22 between enablement and security.
The Razor's Edge: Enabling Cloud While Mitigating the Risk of a Cloud Data Br...

Shadow IT. It's not a new term and certainly not a new challenge. But with only blunt-force solutions like saying "no" or blocking cloud services at the firewall, IT has not been able to do much to address the challenge. This is all changing. Business and IT leaders alike see real value in cloud services and want to take a lean-forward approach to enabling them. The reality, though, is that cloud services are not without their risks, and the risk of a data breach increases when the cloud is involved. Hear from Netskope about the risks, economic impact, and multiplier effect of a cloud data breach, and how forward-looking organizations are walking the razor’s edge to mitigate these risks while enabling the cloud.
Autumn 2015 EMEA Netskope Cloud Report

In this Netskope Cloud Report infographic, we've compiled the most interesting trends on cloud app adoption and usage based on aggregated, anonymized data from the Netskope Active Platform.
Data Breach: The Cloud Multiplier Effect

The Ponemon Institute issued a first-of-its-kind report sponsored by Netskope that identifies a “cloud multiplier effect” on the probability of a data breach. IT and security professionals believe that increasing the use of cloud services in the enterprise will increase the likelihood of a $20M data breach by as much as 3x. In these slides and the accompanying on-demand video, Dr. Larry Ponemon and Netskope CEO Sanjay Beri for a look at the report findings and for advice on how enterprises can mitigate this multiplier and enable safe cloud usage.
Reference Architecture for Data Loss Prevention in the Cloud

Do you measure up? A new reference architecture for data loss prevention (DLP) in the the cloud. Six key architectural tenets.
Office 365 in Focus. Security and Governance Strategies from the Experts - We...

One of today's biggest cloud trends is enterprise adoption of the Microsoft Office 365 suite. There is one wrinkle, though. Your business wants to move quickly to get immediate value, while your security team needs to proceed a little more cautiously to ensure they can govern usage and protect sensitive data. Can organizations move quickly and instrument the proper controls?
Join Adrian Sanabria, Senior Security Analyst from 451 Research, Shamiana Soderberg, Senior Business Development Manager Cloud Productivity from Microsoft, and Jamie Barnett, CMO of Netskope for a look at safe enablement best practices for Office 365, and the role Cloud Access Security Brokers play in this effort.
Attendees will come away with the ten real-world requirements that every organization should consider when adopting a sanctioned cloud productivity suite like Office 365. These requirements will address areas like:
- Granular administrative and user controls across the Office 365 suite
- DLP for content “at rest” within and “en route” to or from the suite
- Usage and data governance within the suite and its ecosystem
Making Cloud Security Part of Your DNA Webinar Slides

To watch the full Making Cloud Security Part of Your DNA webinar video, please go to: https://resources.netskope.com/h/i/65967799-making-cloud-security-part-of-your-dna
Summary:
As Chief Security Officer for leading cancer diagnostic company Genomic Health, Craig Guinasso makes cloud a strategic advantage while solving some of today’s most complex security challenges.
Join Craig, along with Sanjay Beri, CEO of Netskope, Missy Krasner, Managing Director of Healthcare at Box, and David Baker, CSO of Okta, for a webinar on the top five strategies that healthcare technology leaders should adopt to get the most out of the cloud while also protecting patient health data and keeping their organizations compliant.
In this powerpoint, you will get a glimpse into the webinar where we discussed how to:
- Think about cloud services in relation to business objectives
- Triage Shadow IT and consolidate on the most enterprise-ready cloud services
- Create checks and policies to identify and prevent PHI leaks
- Turn their business stakeholders into security champions
Cure for the Common Cloud: How Healthcare can Safely Enable the Cloud

The explosion of useful cloud applications has enabled new levels of productivity, resulting in strategic advantages for some healthcare providers. But cloud app usage is not without risk.
Craig Guinasso, CSO of Genomic Health, is leveraging the power of the cloud, while solving some of today’s most complex security challenges.
Craig, along with Krishna Narayanaswamy, co-founder and chief scientist of Netskope, discuss the top five strategies that healthcare technology and security leaders are adopting to get the most out of the cloud, while protecting patient health data and maintaining their organization’s compliance.
Attendees will learn how to:
- Think about cloud services in relation to business objectives
- Triage Shadow IT and consolidate on the most enterprise-ready cloud services
- Create checks and policies to identify and prevent PHI leaks
- Turn their business stakeholders into security champions
5 Highest-Impact CASB Use Cases

Cloud app security is a top priority for many enterprises. Whether securing data in the Office 365 suite, ensuring compliance in Salesforce, or getting control over shadow IT, information security leaders are exploring how Cloud Access Security Brokers can make an impact in their organizations.
This presentation covers the top five CASB use cases that have the highest impact on cloud-consuming enterprises.
The Definitive CASB Business Case Kit - Presentation

As #1 on Gartner’s information security agenda, CASB is a must-have. But is your business case lined up? Get started now with the definitive CASB business case starter kit. The kit includes:
- The Gartner Market Guide to Cloud Access Security Brokers
- A CASB justification letter that you can tailor and deliver to your decision-maker
- A CASB ROI calculator into which you can enter your assumptions, plus a 3-slide companion executive presentation
- A sample Cloud Risk Assessment so you know what to expect when you request this analysis from your CASB
- The Netskope Cloud Report, which contains the latest cloud security benchmarks
- The 15 Most Critical CASB Use Cases eBook, which will help you understand and prioritize your CASB use cases
5 Highest-Impact CASB Use Cases - Office 365

Cloud app security is a top priority for many enterprises. Whether securing data in the Office 365 suite, ensuring compliance in Salesforce, or getting control over shadow IT, information security leaders are exploring how Cloud Access Security Brokers can make an impact in their organizations.
This presentation covers the top Office 365-specific five CASB use cases that have the highest impact on cloud-consuming enterprises.
Cloud Security for Dummies Webinar — The Identity Edition

Join "Cloud Security for Dummies" authors Ravi Ithal and Krishna Narayanaswamy, along with Patrick Harding, CTO from Ping Identity for this special “Identity Edition” of the Cloud Security for Dummies webinar series.
In this panel-style discussion, the experts will compare notes, debate approaches, and share stories from the cloud security and identity and access management front lines. IT security professionals will walk away with best practices on:
- Finding and assessing risk of all cloud apps running in your enterprise
- Onboarding new apps and bringing them into the secure Single Sign On fold
- Using identity to enable access and enforce usage and content policies
- Dealing with security issues such as poor reputation users and compromised accounts
- Communicating and coaching users
Quantifying Cloud Risk for Your Corporate Leadership

The “move to the cloud” has long been considered a key initiative by organizations worldwide. With this move, there’s a level of increased risk that enterprises must address. What’s different is using cloud services requires abdicating some control over how systems and data are being protected. We begin this discussion on this footing.
Join Scott Hogrefe, Sr. Director of Market Data for Netskope, who will lead this discussion about what CISOs need to know about:
- Their cloud risk
- How to quantify it for their corporate leadership and board of directors
- How to convey it in the context of their overall cloud strategy
Viewers also liked (15)
Lions, Tigers, and PHI, Oh My! The latest in data loss prevention in the cloud.

Lions, Tigers, and PHI, Oh My! The latest in data loss prevention in the cloud.
The Razor's Edge: Enabling Cloud While Mitigating the Risk of a Cloud Data Br...

The Razor's Edge: Enabling Cloud While Mitigating the Risk of a Cloud Data Br...
Reference Architecture for Data Loss Prevention in the Cloud

Reference Architecture for Data Loss Prevention in the Cloud
Office 365 in Focus. Security and Governance Strategies from the Experts - We...

Office 365 in Focus. Security and Governance Strategies from the Experts - We...
Making Cloud Security Part of Your DNA Webinar Slides

Making Cloud Security Part of Your DNA Webinar Slides
Cure for the Common Cloud: How Healthcare can Safely Enable the Cloud

Cure for the Common Cloud: How Healthcare can Safely Enable the Cloud
The Definitive CASB Business Case Kit - Presentation

The Definitive CASB Business Case Kit - Presentation
Cloud Security for Dummies Webinar — The Identity Edition

Cloud Security for Dummies Webinar — The Identity Edition
Quantifying Cloud Risk for Your Corporate Leadership

Quantifying Cloud Risk for Your Corporate Leadership
Similar to Summer 2015 EMEA Netskope Cloud Report
June 2016 EMEA Netskope Cloud Report 

In this Netskope Cloud Report™, we’ve compiled the most interesting trends on cloud app adoption and usage based on aggregated, anonymized data from the Netskope Active Platform™. Report findings are based on usage seen across millions of users in hundreds of accounts globally, and represent usage trends from January 1 through March 31, 2016.
Report highlights:
- Three-quarters of cloud apps in use lack key capabilities to comply with the upcoming European Union General Data Protection Regulation.
- Malware continues its rise in enterprise clouds, with an average of 11.0 percent of enterprises detecting malware in their sanctioned apps.
- 26.2 percent of malware files discovered in sanctioned apps are shared with internal or external users or publicly.
- Enterprises have an average of 777 cloud apps in use, a slight rise from 769 last quarter. The Microsoft Office 365 suite continues to lead the pack in top-used business productivity apps, with Office 365 Outlook.com, OneDrive for Business, SharePoint, Yammer, and Lync in the number 2, 3, 12, 19, and 20 spots, respectively.
- Cloud Storage apps dominate cloud DLP violations, with 73.6 percent of the total.
June 2016 Worldwide Netskope Cloud Report 

In this Netskope Cloud Report™, we’ve compiled the most interesting trends on cloud app adoption and usage based on aggregated, anonymized data from the Netskope Active Platform™. Report findings are based on usage seen across millions of users in hundreds of accounts globally, and represent usage trends from January 1 through March 31, 2016.
Report highlights:
- Three-quarters of cloud apps in use lack key capabilities to comply with the upcoming European Union General Data Protection Regulation.
- Malware continues its rise in enterprise clouds, with an average of 11.0 percent of enterprises detecting malware in their sanctioned apps.
- 26.2 percent of malware files discovered in sanctioned apps are shared with internal or external users or publicly.
- Enterprises have an average of 935 cloud apps in use, a slight rise from 917 last quarter. The Microsoft Office 365 suite continues to lead the pack in top-used business productivity apps, with Office 365 Outlook.com, OneDrive for Business, SharePoint, Yammer, and Lync in the number 2, 3, 12, 19, and 20 spots, respectively.
- Cloud Storage apps dominate cloud DLP violations, with 73.6 percent of the total.
Every cloud cloud risk assessment 2018

We at EveryCloud, help you to be more cloud confident, we do this in a number of ways that include email security, web security, insider threat management, identity and access management, cloud communications and cloud access security.
Web Security – preventing DLP, URL spoofing, malicious sties, rogue web applications etc. Control access to networks, apps and websites, visualise users, data and device behaviour
Email Security – preventing phishing, ransomware, spam and data exposure. Improved protection against malware and other threats, increase employee and network efficiency.
Identity Access Management - helping your business to stay safe, by providing powerful solutions for MFA, password vulnerabilities, improve visibility and reporting, helping you reduce high volume helpdesk tickets, on boarding and off boarding staff, contractors and suppliers, leveraging best of breed SaaS, unify API access and management to keep apps and data safe, automate user lifecycles by connecting business and IT processes
Insider Threat protection - providing a 360-degree view of activities around your data – the who, what, where and when – by monitoring user behaviour and data flow – then instantly alerting to any anomalous or malicious activity.
Cloud Communications - we help your journey to a Cloud based Contact Centre improving Customer Service in an omni-channel environment integrating Call Centre, Email, Live Chat, co-browsing, Instant Messaging and much more.
Cloud Access Security - we assist you to govern your business’ cloud usage with visibility and control. We help you to understand risky activity, protect and prevent the loss of sensitive data and guard against cloud-based threats such as malware and ransomware.
Email us discover@everycloud.co.uk or visit our website www.everycloud.co.uk - we are happy to help you
ClientSummit2010_CloudWorkshop

Ray Velez of Razorfish discussed how marketers marketers can more effectively manage the peaks and valleys of marketing campaigns by employing cloud technology at the Razorfish Client Summit in Boston. October 12-14, 2010.
Microsoft Power Platform Governance with Runpipe

www.runpipe.com
This Slide Deck is designed for anyone responsible for the governance and adoption of Power Apps and Power Automate and Power Bi in a large organisations.
It will list all the features, tools and practices available in the Power Platform to help you monitor, protect and support your data and applications, while also enabling and encouraging innovation from your makers.
It shares top tips and best practice suggestions for governance, security and monitoring, and strategies employed by customers to enable digital transformation with the Power Platform.
Runpipe provides an intuitive platform that brings together security, governance and enablement for multiple Low-Code Platforms, all in one place.
M365 Virtual Marthon: Protecting your Teamwork across Microsoft 365

Presentation from the M365 Virtual Marathon. Session was about sensitivity labels, DLP, retention labels, and external sharing
Careless Users In the Cloud (And What IT Can Do About It)

A Softchoice survey of 1,000 full-time people in North America found employees who use SaaS apps for work are developing bad tech habits that expose their organizations to security breaches and data loss.
Our report summary provides an in-depth exploration of how SaaS is adding a new element of risk to the way we work, and what IT departments can do to eliminate bad user behavior in the cloud.
April 2023 CIAOPS Need to Know Webinar

Recording of monthly Need to Know webinar for April 2023 that focused on providing a deep dive into Defender for Cloud Apps. The session also includes Microsoft Cloud news and updates along with an open Q and A session around Microsoft 365. Video recording is available at www.ciaopsacademy.com
The 1% Who Can Take Down your Organization

The Cloud Cybersecurity Lessons We Learned from 10M Users. Learn about the top cloud cybersecurity trends that fly under your radar, what the distribution of cloud cybersecurity risk means for your ability to act on it, along with 3 key security skills you should master for an immediately safer cloud environment.
Why Salesforce is the best CRM

Salesforce was founded with a vision to redefine the Cloud CRM model. It sowed the seeds for a new era of cloud computing and brought in revolutionary changes to the concept of Customer Relationship Management. The USP of Salesforce is its presence across-the-board. It competes with Oracle, SAP, and Microsoft in the top-market. While these three competitors match Salesforce’s features, Salesforce offers far superior and flexible solutions with value for your money.
To get in touch, write to us at: jghosh@suyati.com
Proteja sus datos en cualquier servicio Cloud y Web de forma unificada

Hoy en día, una media de más de 1000 aplicaciones Cloud se está utilizando en cada empresa, de las cuales, el 98% se categoriza como «Shadow IT», lo cual significa que la dirección IT no las controla.
Además, 80% de la información que sale afuera de las empresas se comparte utilizando aplicaciones Cloud. Y más de 50% del acceso y uso de las aplicaciones Cloud se realiza desde fuera de las redes corporativas.
Is the Cloud Safe? Ensuring Security in the Cloud

When switching to the cloud, many nonprofits wonder how cloud apps and services will affect their organization’s security. Cloud apps and software, such as Microsoft Office 365, Google G Suite, Box, and Amazon Web Services offer a multitude of benefits to nonprofits when it comes to keeping their devices and data safe. In this 60-minute webinar, hosted by Deena Thomchick, Senior Director of Cloud Security at Symantec, we will cover the many security benefits of switching to the cloud.
Atelier Technique - Symantec - #ACSS2019

Séduites par une vaste gamme d'applications de productivité, réunies sur une même plate-forme, de nombreuses entreprises s’intéressent à Office 365. Mais celles qui franchissent le pas se rendent compte que les enjeux de sécurité du cloud ne sont pas aussi simples à résoudre qu’elles le pensaient.
La plate-forme Office 365 réunit des outils de communication, de création de contenu et de partage au sein d’un environnement cloud ouvert à tous les utilisateurs et compatibles avec tous les appareils. Cette plate-forme
unique concentre ainsi tous les enjeux de sécurité auxquelles l’entreprise doit faire face. Il est donc impératif de
bien réfléchir à cette question.
Retrouvez nous pour ce workshop pour en savoir plus sur les implications de sécurité et les éléments clés à
prendre en considération pour toute entreprise ayant adopté ou prévoyant de passer à Office 365.
Abderezak OUARET - Business Development Manager North Africa - SYMENTEC
DAM 2018 Review, What's next 2019 ?

DAM 2018 Review, What's next 2019 ?
Facts and Trends of the 2018 DAM Market, what's rock, what matters for Brands ? How to Select a DAM solution and more...
API Security Webinar - Security Guidelines for Providing and Consuming APIs

API Security Webinar - Security Guidelines for Providing and Consuming APIs by Faisal Yahya
Simak penjelasan dari pakar industri tentang trend dan tantangan API dalam tahun 2021. Pelajari bagaimana organisasi dapat membebaskan potensi API, untuk secara efektif menangkis serangan dan melindungi aset API. Masalah-masalah yang muncul di event API Security Challenge juga akan dibahas di sini, dan akan ada hadiah-hadiah menarik bagi semua peserta.
Agenda :
- Penelusuran trend keamanan API, tantangan dan masalah-masalah keamanan yang sering dihadapi.
- Temuan dan Statistik yang dipelajari lewat API Security Challenge
- Penelusuran solusi untuk tantangan nyata yang ditemui dalam API Security Challenges
- Pengumuman pemenang API Security Challenge
API Security Webinar : Security Guidelines for Providing and Consuming APIs

API Security Webinar : Security Guidelines for Providing and Consuming APIs by Faisal Yahya
Similar to Summer 2015 EMEA Netskope Cloud Report (20)
M365 Virtual Marthon: Protecting your Teamwork across Microsoft 365

M365 Virtual Marthon: Protecting your Teamwork across Microsoft 365
Careless Users In the Cloud (And What IT Can Do About It)

Careless Users In the Cloud (And What IT Can Do About It)
Proteja sus datos en cualquier servicio Cloud y Web de forma unificada

Proteja sus datos en cualquier servicio Cloud y Web de forma unificada
API Security Webinar - Security Guidelines for Providing and Consuming APIs

API Security Webinar - Security Guidelines for Providing and Consuming APIs
API Security Webinar : Security Guidelines for Providing and Consuming APIs

API Security Webinar : Security Guidelines for Providing and Consuming APIs
More from Netskope
Netskope Threat Labs: Cloud As an Attack Vector

Netskope Threat Labs analyzes how threat actors use the Cloud
Why Everyone Needs a Cloud-First Security Program - SASEfaction Guaranteed!

Security teams are constantly keeping up with complex attacks leveraging the cloud, but traditional security stacks just can’t keep pace with malicious actors or insiders. In the session, we’ll explore Gartner’s new SASE framework and how organizations can utilize Zero Trust, visibility into cloud-based traffic and cloud threat protection to build a modernized cloud-first stack.
Netskope Overview

NetskopeTM is the leader in cloud app analytics and policy enforce- ment. Only Netskope eliminates the catch-22 between being agile and being secure and compliant by providing complete visibility, enforcing sophisticated policies, and protecting data in cloud apps.
Forrester Research: Securing the Cloud When Users are Left to Their Own Devices

90% of cloud apps in the enterprise are being used without IT’s knowledge. Whether brought in by individuals or lines of business, there’s an average of 508 apps per enterprise and more than 5,000 in the world from which people can choose. Where things get even more interesting is when cloud and mobile combine and the opportunity for data loss and breaches multiply.
These slides are from a webinar where leading identity management, cloud security, and fraud management expert Andras Cser from Forrester and Netskope’s Sr. Director of Product Marketing Bob Gilbert talk about the importance of understanding which employees are using which cloud apps and from where they’re accessing them.
View the on-demand webinar here:
http://www.netskope.com/webinars/securing-cloud-users-left-devices/
Data Privacy, Security, and Sovereignty in a Cloudy World

Jon Oltsik, ESG Senior Principal Analyst and widely recognized information security expert, reviews what it means to ensure data privacy, security, and sovereignty, and what you should be looking for from your cloud providers.
Netskope Cloud Report - April 2014

In the third Netskope Cloud Report, we’ve compiled the most interesting trends on cloud app adoption and usage based on aggregated, anonymized data from the Netskope Active Platform.
Here are some of the highlights from the report:
- Cloud app control at the firewall has led to “exception sprawl”, with 90% of usage in “blocked” apps
- 85% of apps aren’t enterprise-ready, and many of those are business-critical
- The top policy violations in cloud apps are upload, edit, and post
More from Netskope (12)
Why Everyone Needs a Cloud-First Security Program - SASEfaction Guaranteed!

Why Everyone Needs a Cloud-First Security Program - SASEfaction Guaranteed!
Forrester Research: Securing the Cloud When Users are Left to Their Own Devices

Forrester Research: Securing the Cloud When Users are Left to Their Own Devices
Data Privacy, Security, and Sovereignty in a Cloudy World

Data Privacy, Security, and Sovereignty in a Cloudy World
Recently uploaded
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic (NeSy) AI is on the rise. However, simply machine learning on just any symbolic structure is not sufficient to really harvest the gains of NeSy. These will only be gained when the symbolic structures have an actual semantics. I give an operational definition of semantics as “predictable inference”.
All of this illustrated with link prediction over knowledge graphs, but the argument is general.
When stars align: studies in data quality, knowledge graphs, and machine lear...

Keynote at DQMLKG workshop at the 21st European Semantic Web Conference 2024
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovation With Your Product by VP of Product Design, Warner Music Group
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Connector Corner: Automate dynamic content and events by pushing a button

Here is something new! In our next Connector Corner webinar, we will demonstrate how you can use a single workflow to:
Create a campaign using Mailchimp with merge tags/fields
Send an interactive Slack channel message (using buttons)
Have the message received by managers and peers along with a test email for review
But there’s more:
In a second workflow supporting the same use case, you’ll see:
Your campaign sent to target colleagues for approval
If the “Approve” button is clicked, a Jira/Zendesk ticket is created for the marketing design team
But—if the “Reject” button is pushed, colleagues will be alerted via Slack message
Join us to learn more about this new, human-in-the-loop capability, brought to you by Integration Service connectors.
And...
Speakers:
Akshay Agnihotri, Product Manager
Charlie Greenberg, Host
ODC, Data Fabric and Architecture User Group

Let's dive deeper into the world of ODC! Ricardo Alves (OutSystems) will join us to tell all about the new Data Fabric. After that, Sezen de Bruijn (OutSystems) will get into the details on how to best design a sturdy architecture within ODC.
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head of Product, Amazon Games
Search and Society: Reimagining Information Access for Radical Futures

The field of Information retrieval (IR) is currently undergoing a transformative shift, at least partly due to the emerging applications of generative AI to information access. In this talk, we will deliberate on the sociotechnical implications of generative AI for information access. We will argue that there is both a critical necessity and an exciting opportunity for the IR community to re-center our research agendas on societal needs while dismantling the artificial separation between the work on fairness, accountability, transparency, and ethics in IR and the rest of IR research. Instead of adopting a reactionary strategy of trying to mitigate potential social harms from emerging technologies, the community should aim to proactively set the research agenda for the kinds of systems we should build inspired by diverse explicitly stated sociotechnical imaginaries. The sociotechnical imaginaries that underpin the design and development of information access technologies needs to be explicitly articulated, and we need to develop theories of change in context of these diverse perspectives. Our guiding future imaginaries must be informed by other academic fields, such as democratic theory and critical theory, and should be co-developed with social science scholars, legal scholars, civil rights and social justice activists, and artists, among others.
Knowledge engineering: from people to machines and back

Keynote at the 21st European Semantic Web Conference
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...

From Siloed Products to Connected Ecosystem: Building a Sustainable and Scalable Platform by VP of Product, The New York Times
JMeter webinar - integration with InfluxDB and Grafana

Watch this recorded webinar about real-time monitoring of application performance. See how to integrate Apache JMeter, the open-source leader in performance testing, with InfluxDB, the open-source time-series database, and Grafana, the open-source analytics and visualization application.
In this webinar, we will review the benefits of leveraging InfluxDB and Grafana when executing load tests and demonstrate how these tools are used to visualize performance metrics.
Length: 30 minutes
Session Overview
-------------------------------------------
During this webinar, we will cover the following topics while demonstrating the integrations of JMeter, InfluxDB and Grafana:
- What out-of-the-box solutions are available for real-time monitoring JMeter tests?
- What are the benefits of integrating InfluxDB and Grafana into the load testing stack?
- Which features are provided by Grafana?
- Demonstration of InfluxDB and Grafana using a practice web application
To view the webinar recording, go to:
https://www.rttsweb.com/jmeter-integration-webinar
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

“AGI should be open source and in the public domain at the service of humanity and the planet.”
AI for Every Business: Unlocking Your Product's Universal Potential by VP of ...

AI for Every Business: Unlocking Your Product's Universal Potential by VP of Product, Slack
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Sidekick Solutions uses Bonterra Impact Management (fka Social Solutions Apricot) and automation solutions to integrate data for business workflows.
We believe integration and automation are essential to user experience and the promise of efficient work through technology. Automation is the critical ingredient to realizing that full vision. We develop integration products and services for Bonterra Case Management software to support the deployment of automations for a variety of use cases.
This video focuses on the notifications, alerts, and approval requests using Slack for Bonterra Impact Management. The solutions covered in this webinar can also be deployed for Microsoft Teams.
Interested in deploying notification automations for Bonterra Impact Management? Contact us at sales@sidekicksolutionsllc.com to discuss next steps.
Essentials of Automations: Optimizing FME Workflows with Parameters

Are you looking to streamline your workflows and boost your projects’ efficiency? Do you find yourself searching for ways to add flexibility and control over your FME workflows? If so, you’re in the right place.
Join us for an insightful dive into the world of FME parameters, a critical element in optimizing workflow efficiency. This webinar marks the beginning of our three-part “Essentials of Automation” series. This first webinar is designed to equip you with the knowledge and skills to utilize parameters effectively: enhancing the flexibility, maintainability, and user control of your FME projects.
Here’s what you’ll gain:
- Essentials of FME Parameters: Understand the pivotal role of parameters, including Reader/Writer, Transformer, User, and FME Flow categories. Discover how they are the key to unlocking automation and optimization within your workflows.
- Practical Applications in FME Form: Delve into key user parameter types including choice, connections, and file URLs. Allow users to control how a workflow runs, making your workflows more reusable. Learn to import values and deliver the best user experience for your workflows while enhancing accuracy.
- Optimization Strategies in FME Flow: Explore the creation and strategic deployment of parameters in FME Flow, including the use of deployment and geometry parameters, to maximize workflow efficiency.
- Pro Tips for Success: Gain insights on parameterizing connections and leveraging new features like Conditional Visibility for clarity and simplicity.
We’ll wrap up with a glimpse into future webinars, followed by a Q&A session to address your specific questions surrounding this topic.
Don’t miss this opportunity to elevate your FME expertise and drive your projects to new heights of efficiency.
Recently uploaded (20)
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic is not enough, we need neuro-*semantic*
When stars align: studies in data quality, knowledge graphs, and machine lear...

When stars align: studies in data quality, knowledge graphs, and machine lear...
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...
Connector Corner: Automate dynamic content and events by pushing a button

Connector Corner: Automate dynamic content and events by pushing a button
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...
Search and Society: Reimagining Information Access for Radical Futures

Search and Society: Reimagining Information Access for Radical Futures
Knowledge engineering: from people to machines and back

Knowledge engineering: from people to machines and back
FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf

FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...

From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...
JMeter webinar - integration with InfluxDB and Grafana

JMeter webinar - integration with InfluxDB and Grafana
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...
AI for Every Business: Unlocking Your Product's Universal Potential by VP of ...

AI for Every Business: Unlocking Your Product's Universal Potential by VP of ...
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...
Essentials of Automations: Optimizing FME Workflows with Parameters

Essentials of Automations: Optimizing FME Workflows with Parameters
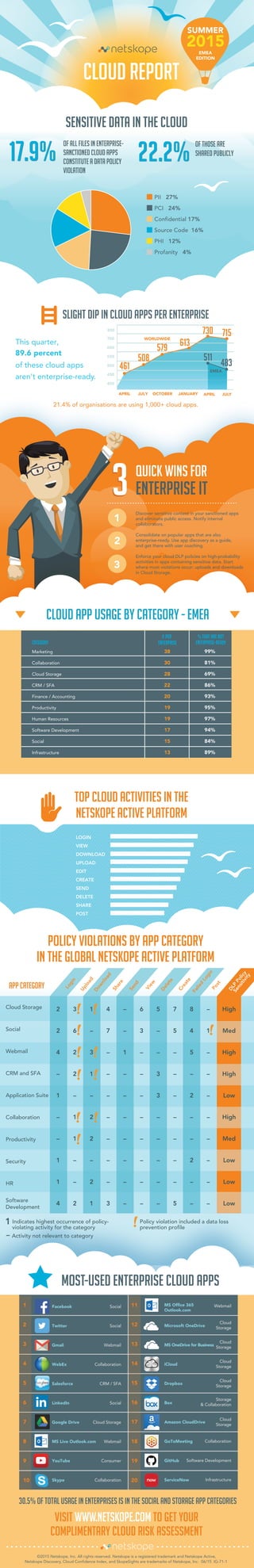
Summer 2015 EMEA Netskope Cloud Report
- 1. CLOUD REPORT SUMMER 2015 1 2 33 quick wins FOR enterprise IT 3 slight dip in cloud apps per enterprise 400 450 500 550 600 700 461 508 579 This quarter, 89.6 percent of these cloud apps aren't enterprise-ready. APRIL JULY OCTOBER JANUARY 21.4% of organisations are using 1,000+ cloud apps. APRIL JULY 800 715730 613 WORLDWIDE 511 483 EMEA sensitive data in the cloud of all files in enterprise- sanctioned cloud apps constitute a data policy violation of those are shared publicly Discover sensitive content in your sanctioned apps and eliminate public access. Notify internal collaborators. Consolidate on popular apps that are also enterprise-ready. Use app discovery as a guide, and get there with user coaching. Enforce your cloud DLP policies on high-probability activities in apps containing sensitive data. Start where most violations occur: uploads and downloads in Cloud Storage. PII 27% PCI 24% Confidential 17% Source Code 16% PHI 12% Profanity 4% 17.9%17.9% 22.2%22.2% Marketing Collaboration Cloud Storage CRM / SFA Finance / Accounting Productivity Human Resources Software Development Social Infrastructure 38 30 28 22 20 19 19 17 15 13 99% 81% 69% 86% 93% 95% 97% 94% 84% 89% CATEGORY # per ENTERPRISE % that are not ENTERPRISE-READY cloud app usage by category - EMEA EMEA EDITION LOGIN VIEW DOWNLOAD UPLOAD EDIT CREATE SEND DELETE SHARE POST TOP CLOUD ACTIVITIES IN THE NETSKOPE ACTIVE PLATFORM ©2015 Netskope, Inc. All rights reserved. Netskope is a registered trademark and Netskope Active, Netskope Discovery, Cloud Confidence Index, and SkopeSights are trademarks of Netskope, Inc. 06/15 IG-71-1 30.5% of total usage in enterprises is in the social and storage app categories VISIT WWW.NETSKOPE.COM TO GET YOUR COMPLIMENTARY CLOUD RISK ASSESSMENT Facebook Twitter Gmail WebEx Salesforce LinkedIn Google Drive MS Live Outlook.com YouTube Skype Social Social Webmail Collaboration CRM / SFA Social Cloud Storage Webmail Consumer Collaboration 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 MOST-USED ENTERPRISE CLOUD APPS Login Upload Dow nload Share Send View APP CATEGORY 2 3 1 4 – 6 5 7 8 – High 2 6 – 7 – 3 – 5 4 1 Med 4 2 3 – 1 – – – 5 – High – 2 1 – – – 3 – – – High 1 – – – – – 3 – 2 – Low – 1 2 – – – – – – – High – 1 2 – – – – – – – Med 1 – – – – – – – 2 – Low 1 – 2 – – – – – – – Low 4 2 1 3 – – – 5 – – Low DLP Policy Sensitivity Cloud Storage Social Webmail CRM and SFA Application Suite Collaboration Productivity Security HR Software Development policy violations by app category in the global Netskope Active Platform Delete Create Failed Login Post Policy violation included a data loss prevention profile Indicates highest occurrence of policy- violating activity for the category 1 Activity not relevant to category– MS Office 365 Outlook.com Microsoft OneDrive MS OneDrive for Business iCloud Dropbox Box Amazon CloudDrive GoToMeeting GitHub ServiceNow Webmail Cloud Storage Cloud Storage Cloud Storage Cloud Storage Storage & Collaboration Cloud Storage Collaboration Software Development Infrastructure
