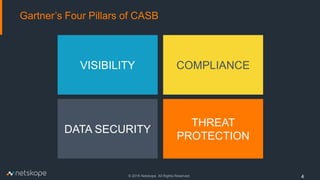
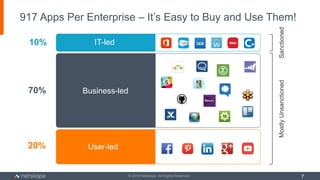
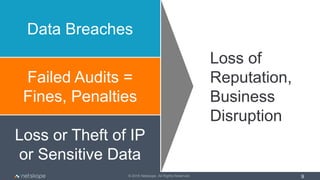
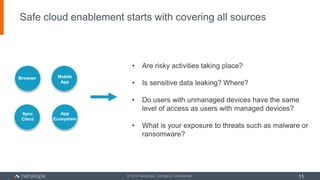
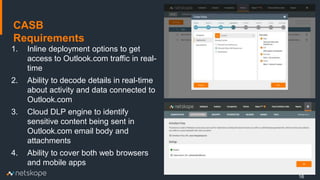
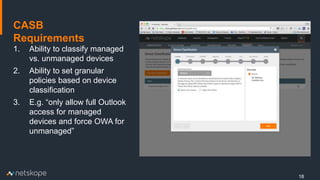
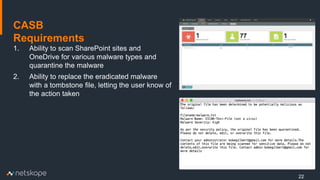
The document outlines five key use cases for Cloud Access Security Brokers (CASBs) in Office 365, emphasizing their importance for data security and compliance. It details how CASBs provide visibility and control over user interactions with cloud applications, aimed at preventing data leakage, ensuring granular access control, detecting data exfiltration, and identifying malware. As the number of enterprise apps increases, organizations are urged to adopt CASBs as a crucial security measure for protecting sensitive data in cloud environments.