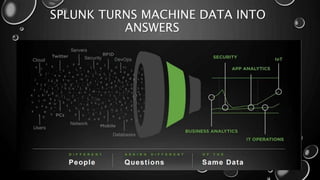
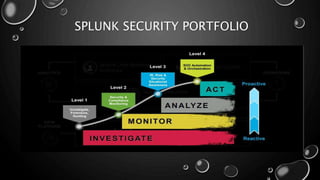
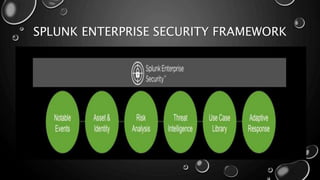
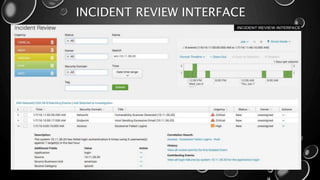
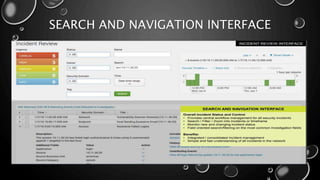
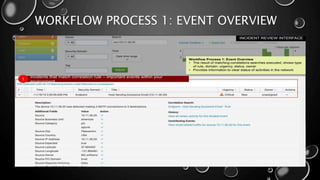
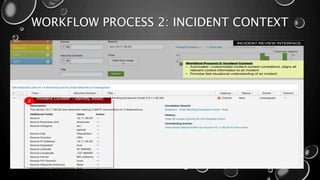
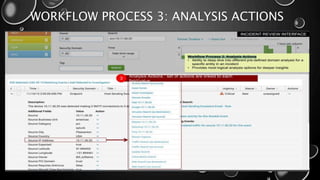
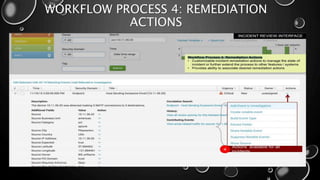
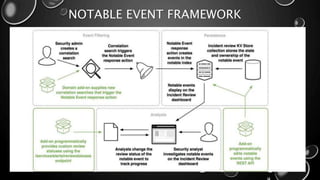
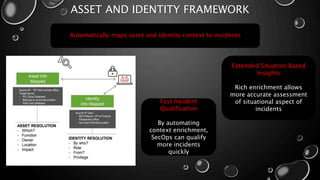
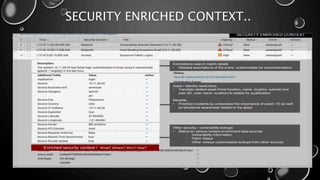
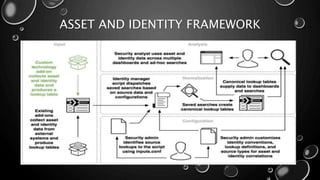
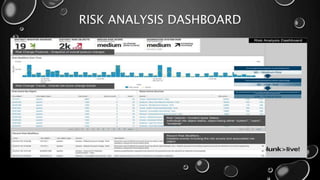
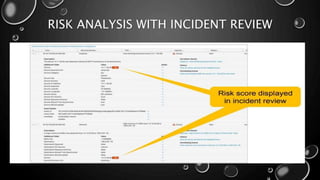
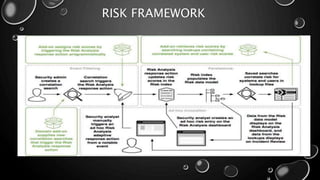
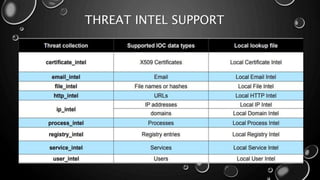
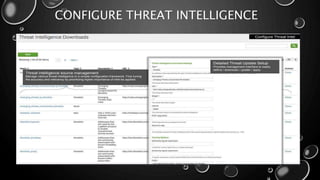
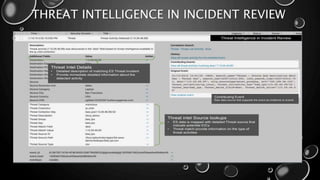
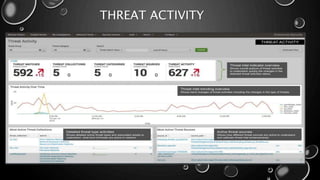
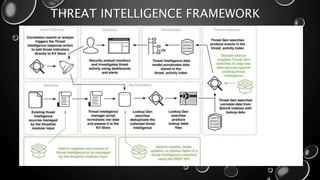
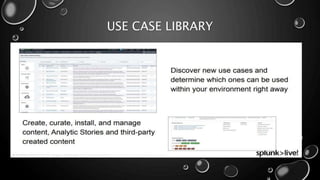
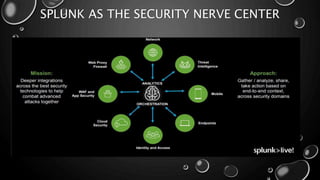
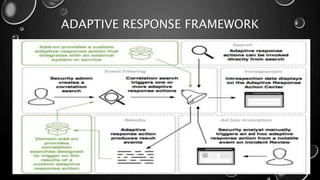
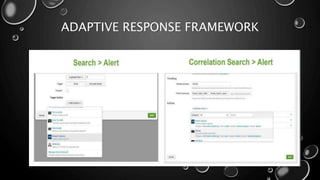
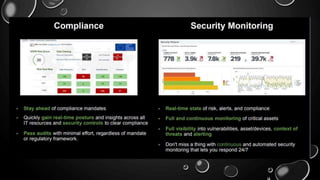
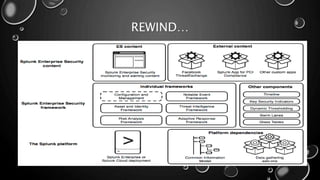
This presentation introduces Splunk Enterprise Security (ES) and its security portfolio. It discusses Splunk's workflow and frameworks that enable key security use cases. The frameworks presented include Notable Events, Asset and Identity, Risk, Threat Intelligence, and Adaptive Response. Desh Cyber is highlighted as a reliable partner that provides Splunk-based security solutions along with training and 24/7 monitoring services.