Embed presentation
Download as PDF, PPTX


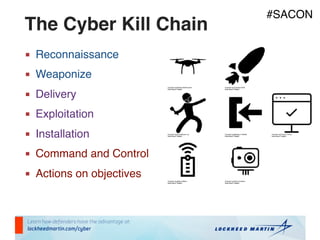

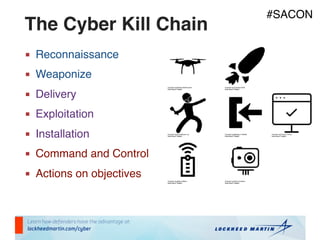

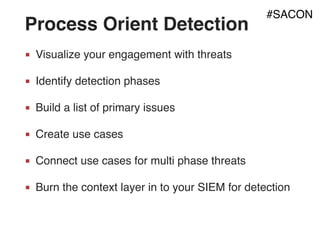

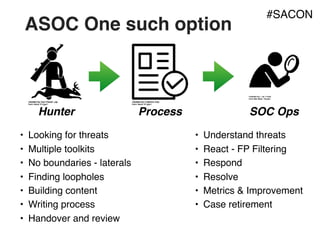

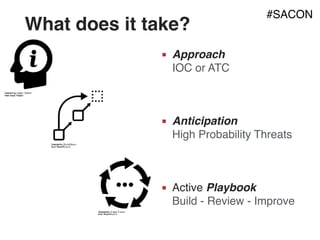




The document outlines strategies for building a next-generation Security Operations Center (SOC) focused on detecting advanced persistent threats (APTs) through a process-oriented detection approach. It discusses the importance of tracking phases of the cyber kill chain, creating use cases, and continuously improving detection capabilities while addressing concerns with traditional SOC methods. Additionally, the document highlights the need for developing an active playbook for threat management and adapting incident management practices to improve response effectiveness.















