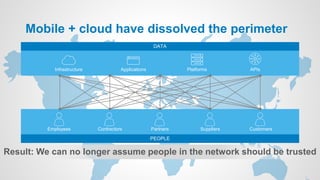
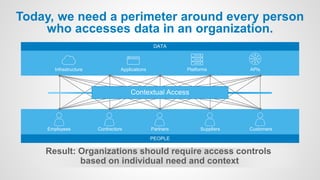
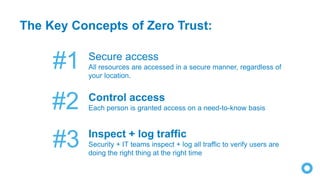
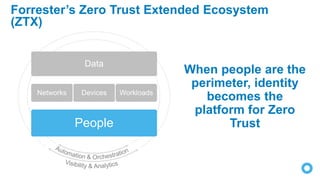
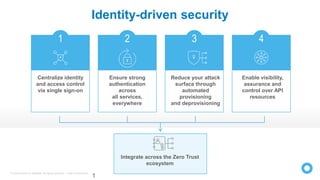
Zero Trust is a security model that requires verification of every individual accessing resources, treating all users and devices as untrusted until verified. As traditional network perimeters dissolve due to mobile and cloud technologies, organizations must implement access controls based on contextual need, ensuring all access is authenticated, authorized, and encrypted. The approach focuses on identity-driven security, emphasizing centralized identity management and continuous risk assessment.