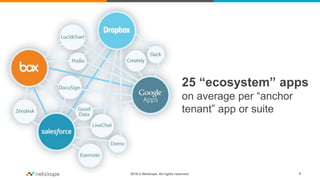
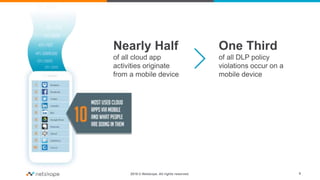
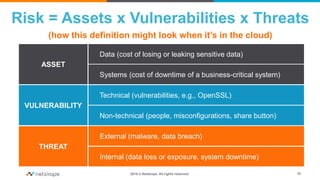
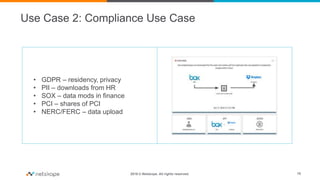
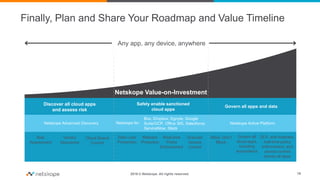
The document presents a comprehensive business case for Cloud Access Security Brokers (CASB), emphasizing their necessity for organizations utilizing cloud services. It outlines the importance of quantifying usage, risks, and potential return on investment through various use cases like visibility, compliance, data security, and threat protection. Finally, it encourages planning and sharing a value timeline for implementing CASB solutions to effectively govern cloud environments.