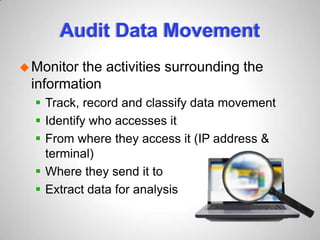
Microsoft Rights Management Services (RMS) offers data protection solutions that safeguard documents within organizations and during external sharing across various devices, such as PCs and tablets. The new features include support for multiple file types beyond Microsoft Office, easy integration with Office 365, and robust control for IT departments over data usage. Additionally, RMS ensures that sensitive data can be monitored and audited while maintaining compliance and security.