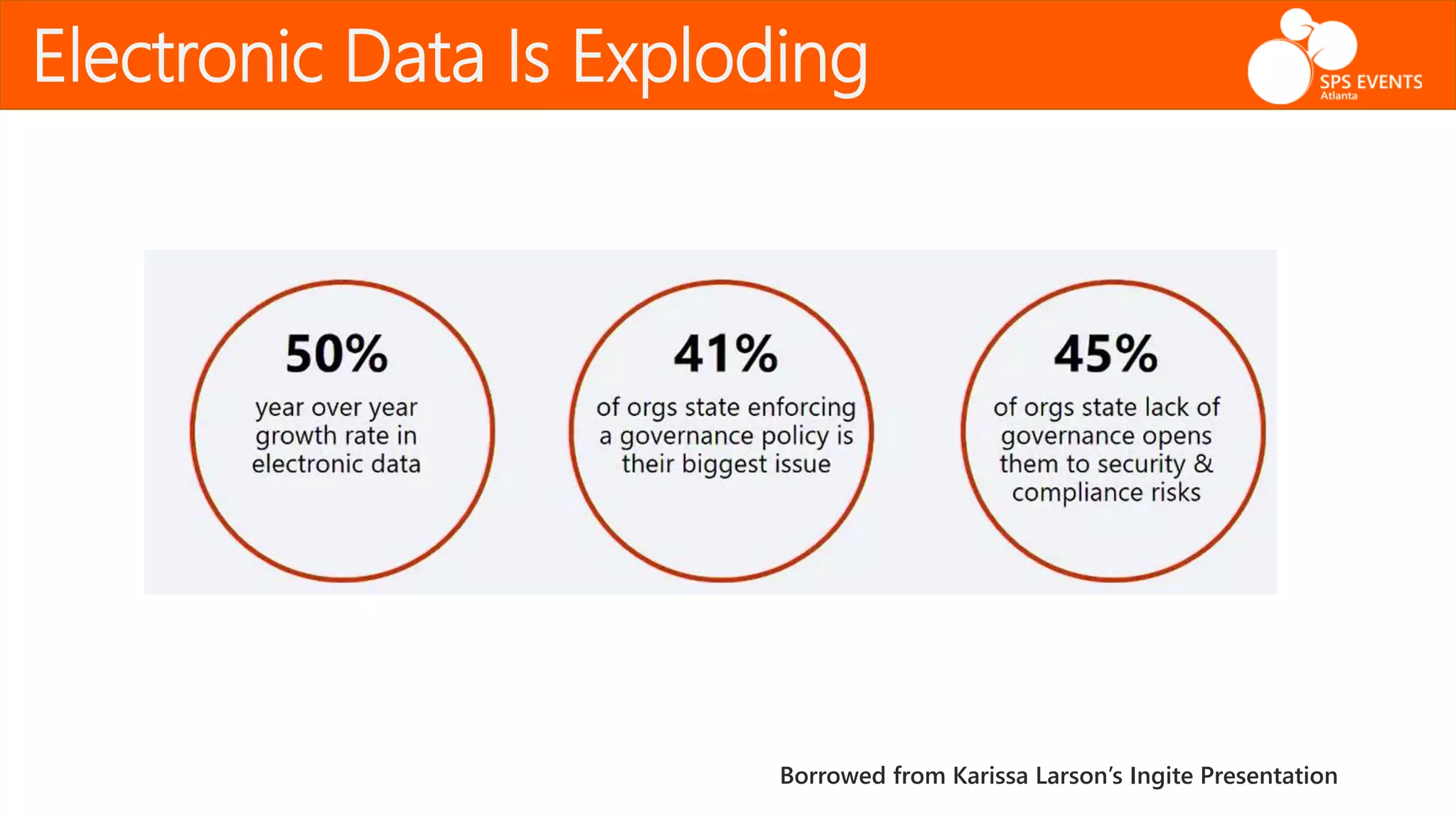
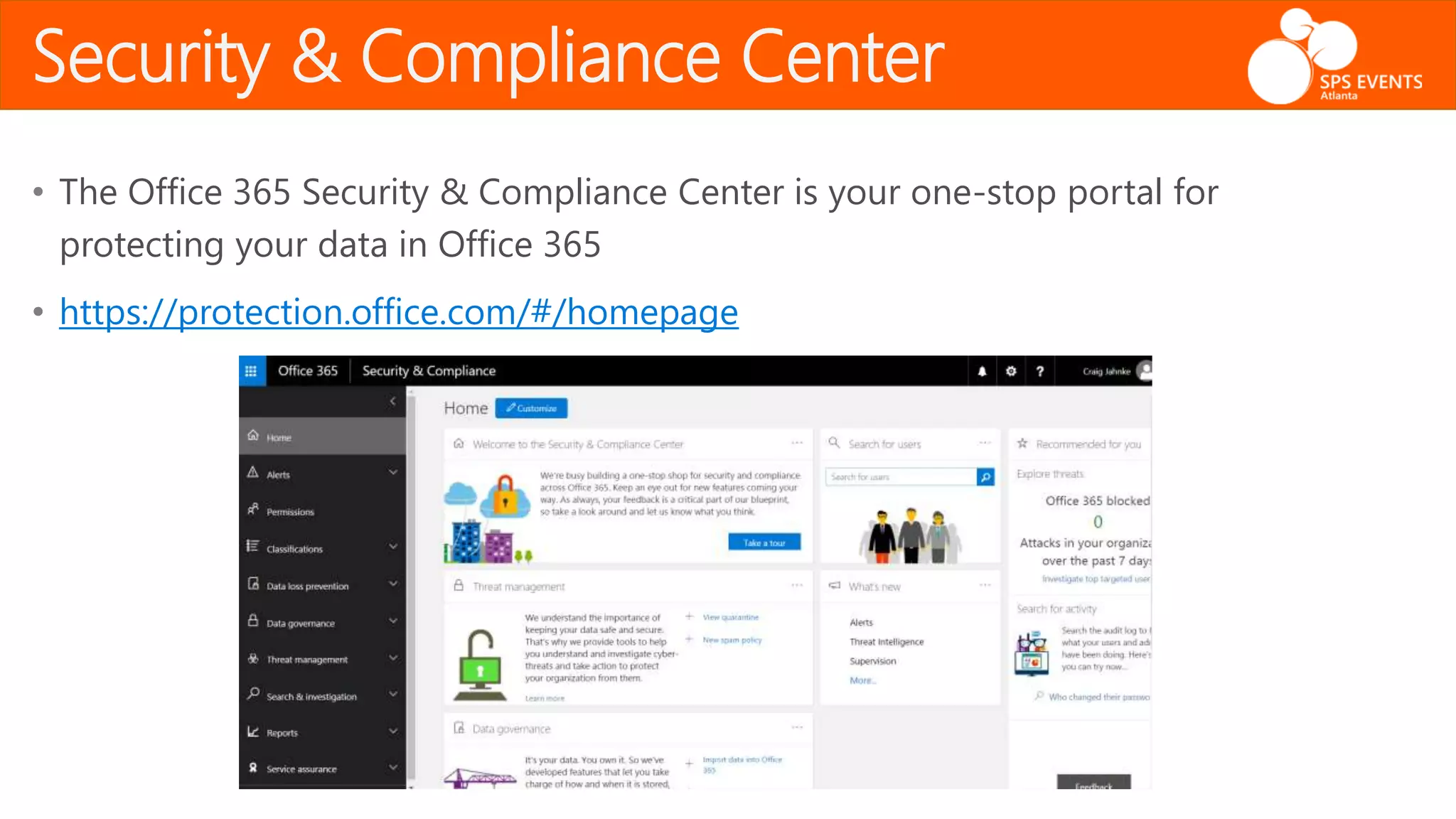
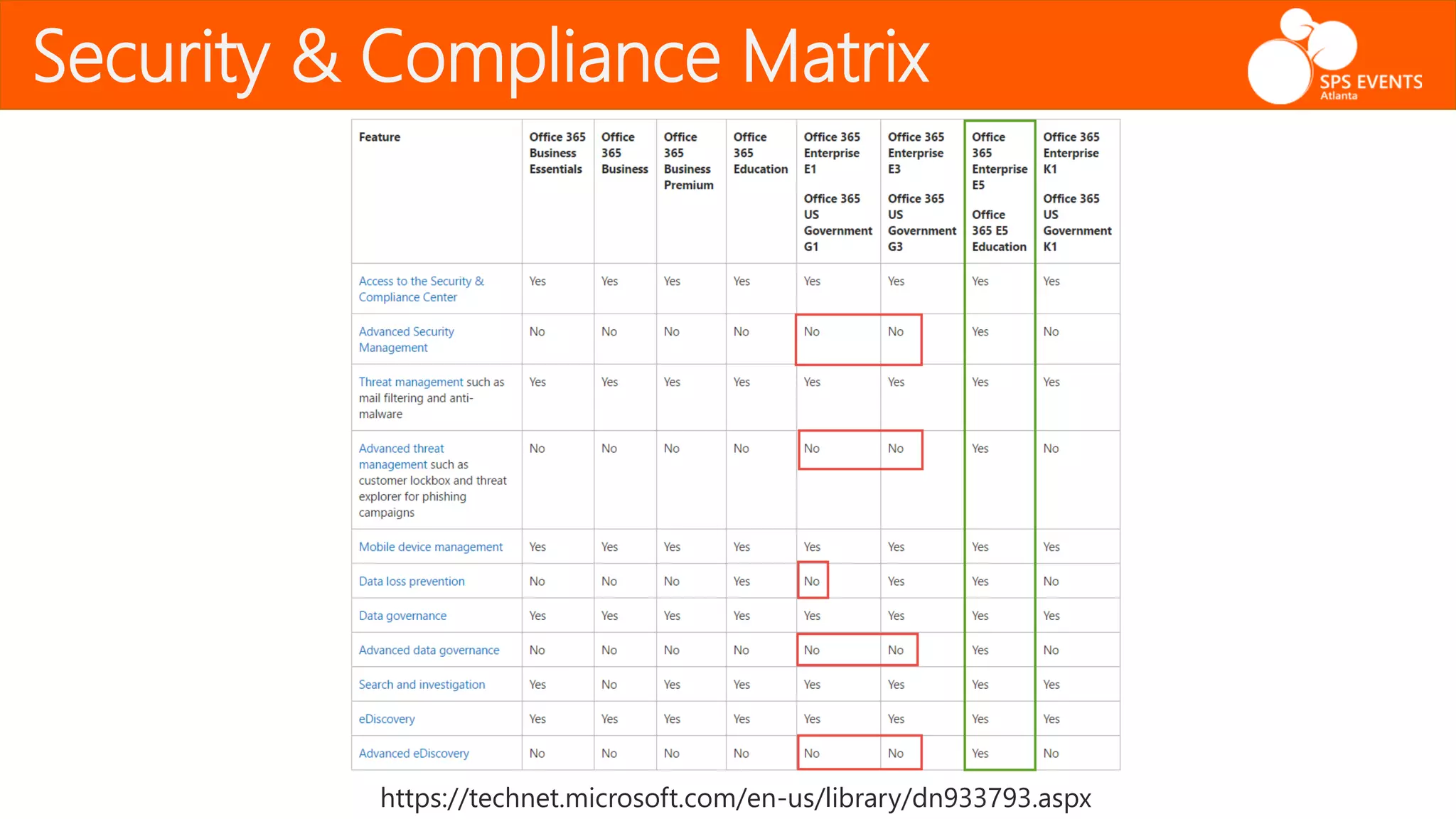
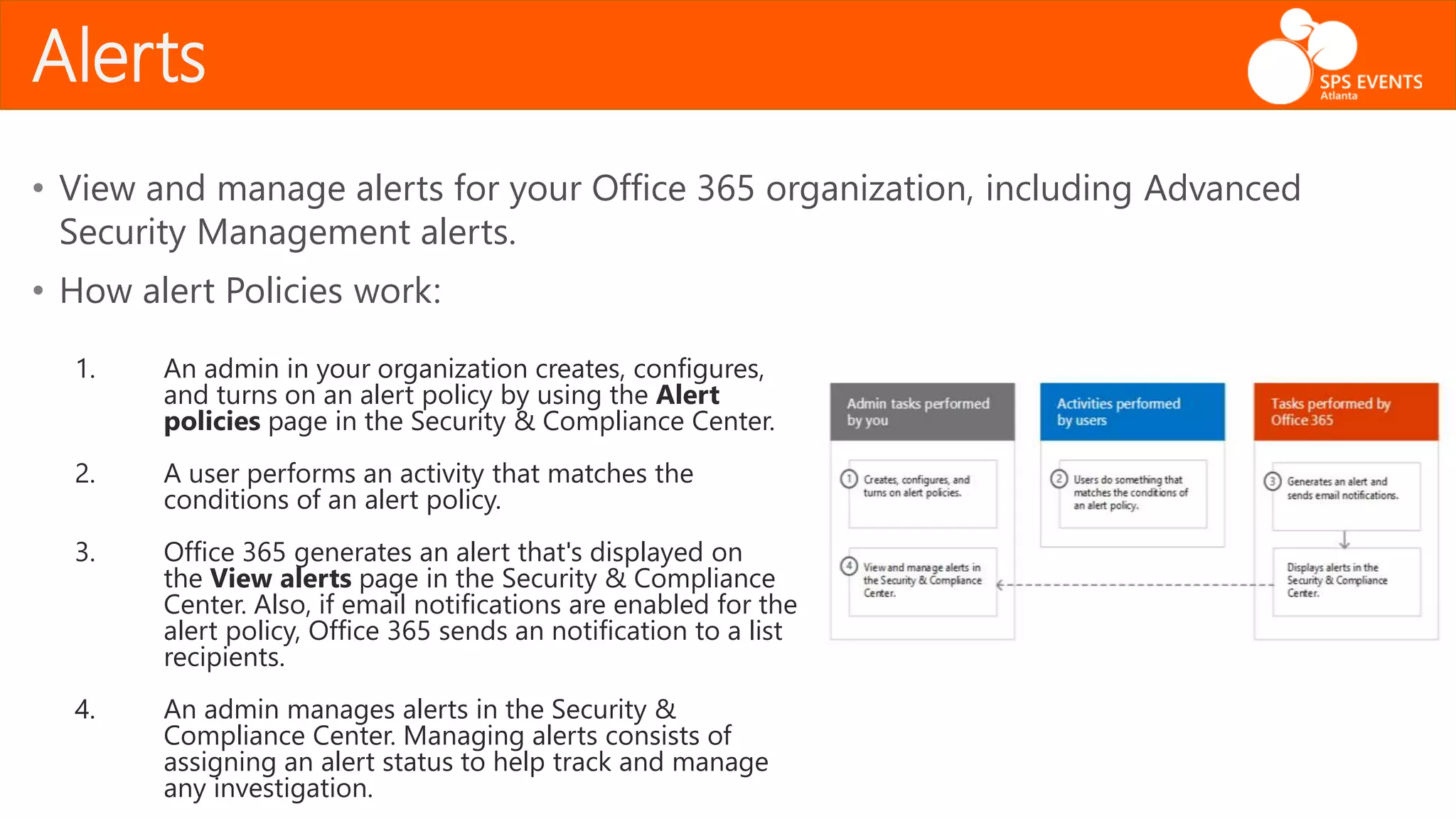
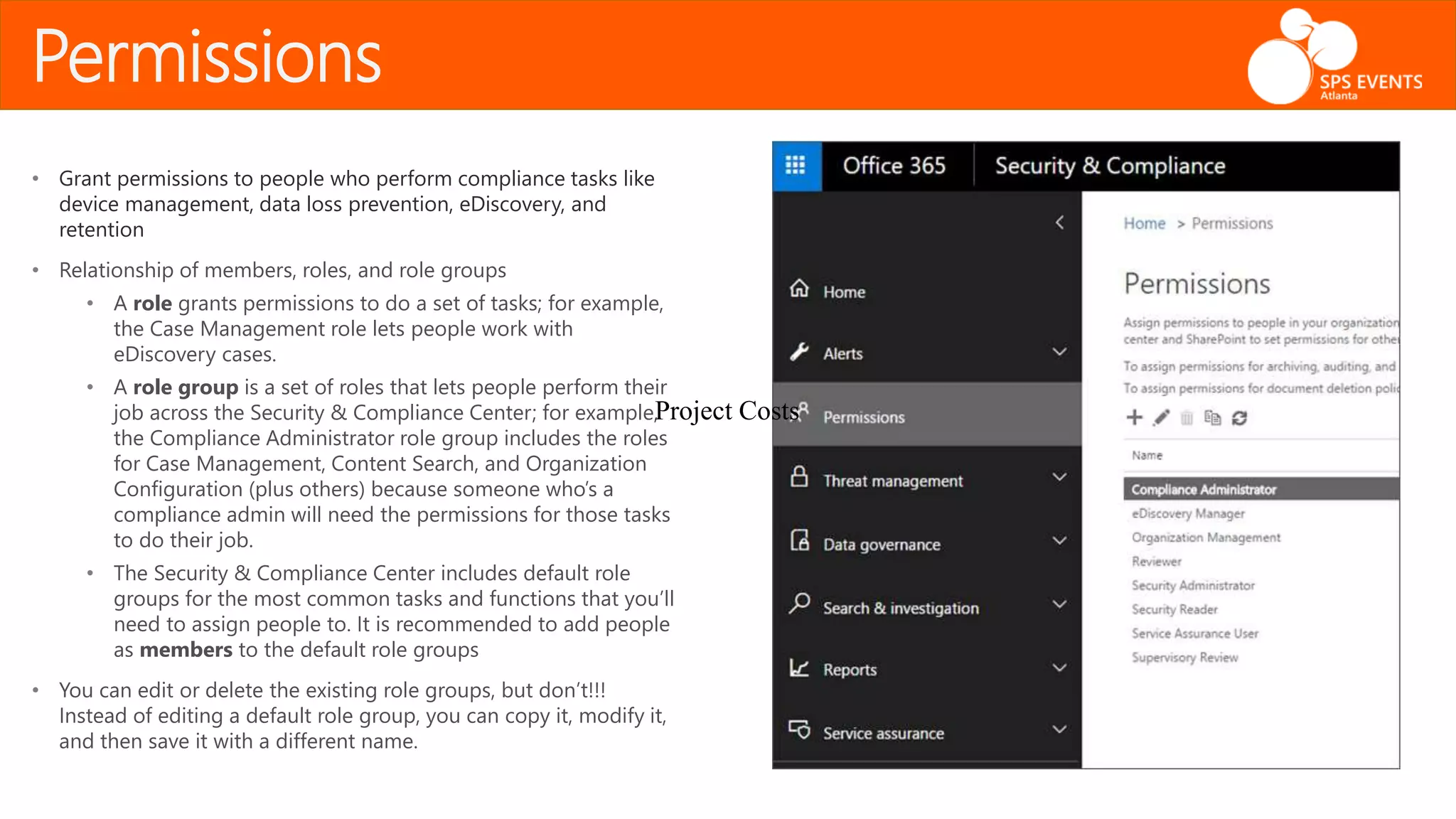
The document outlines the Office 365 Security & Compliance Center, detailing its features such as alerts, permissions, data loss prevention, and threat management. It highlights how organizations can manage their security and compliance through various tools offered within the center, including PowerShell integration for administrative tasks. Additionally, the document emphasizes data governance and monitoring capabilities to protect sensitive information and maintain compliance with industry regulations.