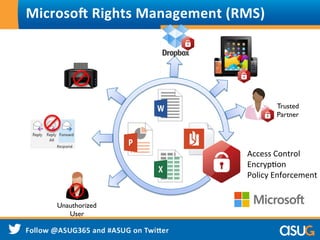
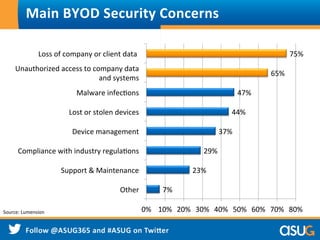
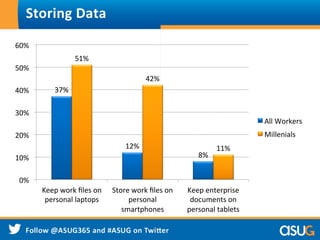
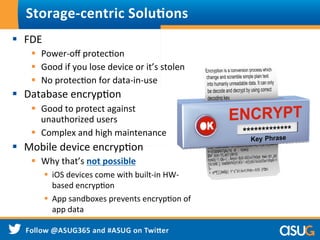
The document discusses the rising trend of Bring Your Own Device (BYOD) in workplaces, highlighting its benefits for both employees and enterprises, such as flexibility, efficiency, and cost reduction. It also addresses the security challenges associated with BYOD, noting that sensitive data is at risk due to inadequate policies and device management. The presentation emphasizes the need for a comprehensive security approach to protect data across various devices and platforms.


![About
SECUDE
1996
Startup
of
Secude,
Spin-‐Off
from
Fraunhofer
&
SAP
2000
SAP
partnership
(world-‐wide
deployment
of
SECUDE
SNC-‐SW)
2001
Market
entry
file/folder
encrypWon
2002
Market
entry
Smartcard
Management
and
E-‐SSO
2004
Startup
of
SECUDE
USA
2005
Market
entry
Full
Disc
EncrypWon
(FDE)
2006
Launch
of
FinallySecure
Enterprise
with
Seagate
(HW-‐based
FDE)
2011
Spin-‐off
of
SECUDE’s
SAP
Security
products
to
SAP
AG
2011
Re-‐focus
on
endpoint
protecWon
&
later
SAP
NetWeaver
Single
Sign-‐On
2012
Halocore
iniWaWve
to
bridge
Microso]
RMS
with
SAP
2014
Spin-‐off
of
non-‐SAP
por^olio](https://image.slidesharecdn.com/asugpptgasecudemay2014slideshare-140521095218-phpapp01/85/Mobility-BYOD-Leveraging-Best-Practices-and-Latest-Technologies-for-Comprehensive-Security-3-320.jpg)







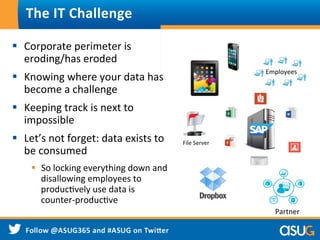
![§ Firewall
§ Protects
the
(eroded)
perimeter
§ DLP
§ Monitoring
§ Good
to
understand
where
data
is
going
§ Problem
is
wealth
of
informaWon
it
produces
§ PrevenWon
§ Too
far
away
from
where
data
is
born
§ Doesn’t
know
the
context
§ Frustrates
users
§ O]en
switched
off
§ VPN
§ Protects
data
in
transit
only
Network-‐centric
Solu9ons](https://image.slidesharecdn.com/asugpptgasecudemay2014slideshare-140521095218-phpapp01/85/Mobility-BYOD-Leveraging-Best-Practices-and-Latest-Technologies-for-Comprehensive-Security-18-320.jpg)
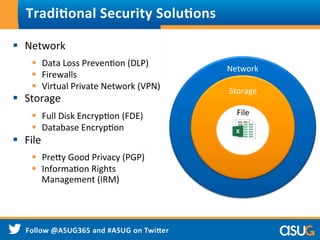
![§ File-‐encrypWon
(PGP…)
§ Key/password
management
issues
§ ProtecWon
is
gone
once
file
is
unlocked/decrypted
§ Rights
Management
(DRM,
IRM
à
RMS)
§ CapabiliWes
of
IRM
§ ProtecWon
=
encrypWon
+
policy
§ Control
who
can
open,
edit,
print,
copy/paste…
§ ExpiraWon
date
§ Established
IRM
soluWons
§ Adobe
§ Oracle
(SealedMedia)
§ Microso]
Data-‐centric
Solu9ons](https://image.slidesharecdn.com/asugpptgasecudemay2014slideshare-140521095218-phpapp01/85/Mobility-BYOD-Leveraging-Best-Practices-and-Latest-Technologies-for-Comprehensive-Security-20-320.jpg)