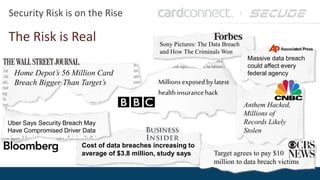
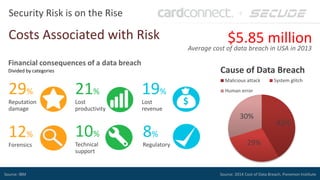
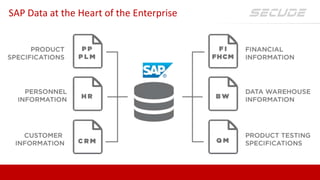
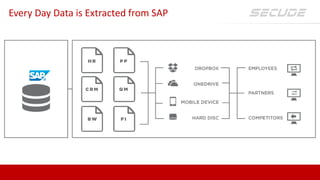
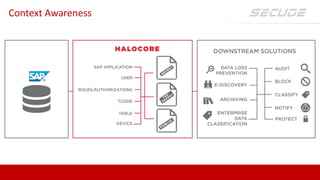
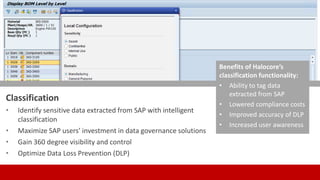
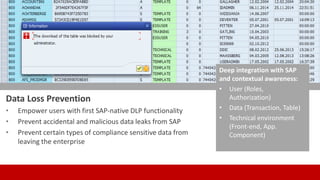
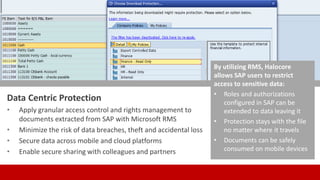
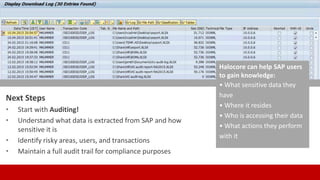
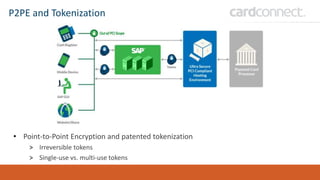
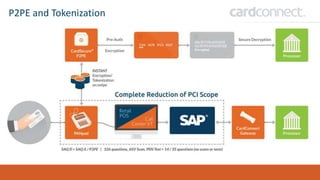
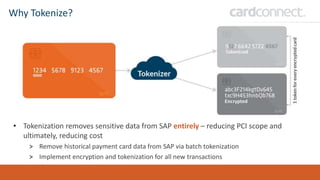
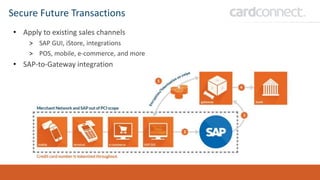
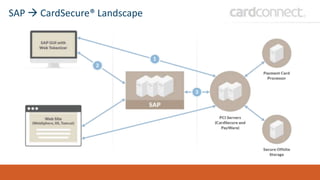
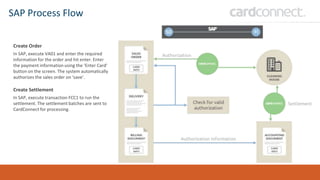
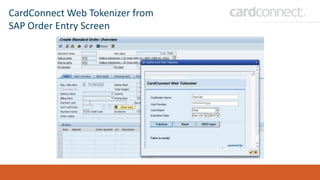
SECUDE is an innovative provider of IT security solutions for SAP customers. It focuses on data-centric security and classification with its Halocore solutions. Halocore allows users to identify sensitive data extracted from SAP, apply data loss prevention controls, and protect documents with rights management. This helps mitigate security risks, reduce compliance costs, and prevent data breaches and theft. The presenters discuss how rising security threats, lack of preparedness, and stringent compliance regulations are pushing companies to find new ways to secure their SAP data.