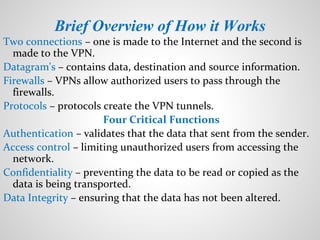
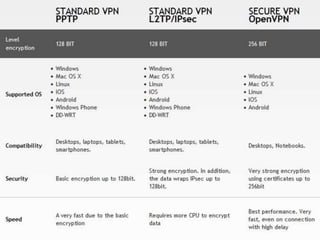
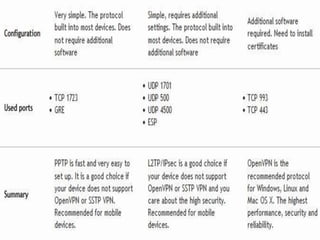
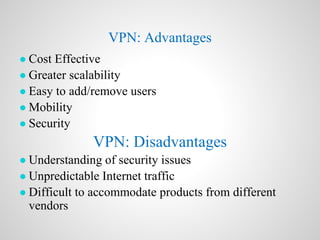
A virtual private network (VPN) allows users to securely send and receive data across shared or public networks as if they are directly connected to a private network. VPNs use authentication and encryption to allow employees to access a company's private network remotely. There are three main types of VPNs: remote access VPNs for employees to connect from various locations, intranet VPNs to connect locations within an organization, and extranet VPNs to securely connect organizations. Common VPN protocols include PPTP, L2TP/IPSec, and OpenVPN. VPNs provide security benefits like authentication, access control, confidentiality and data integrity while allowing remote access and mobility.