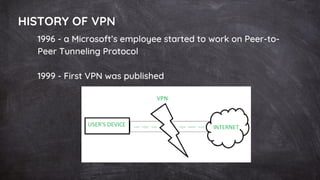
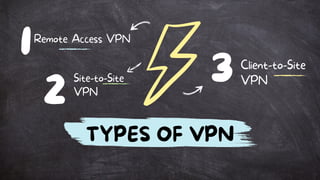
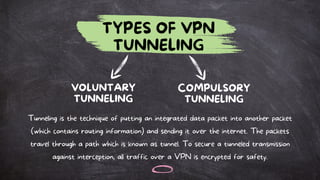
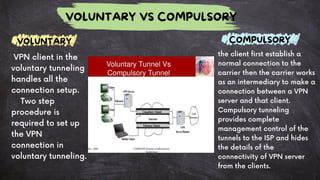
A VPN (Virtual Private Network) securely encrypts user data and masks the IP address to protect privacy and bypass geo-restrictions. It operates by creating a secured connection between the user's device and a VPN server, utilizing various encryption protocols to ensure data integrity and confidentiality. While VPNs offer advantages like improved security and access to restricted content, they may introduce performance issues and potential privacy risks if the provider mishandles data.