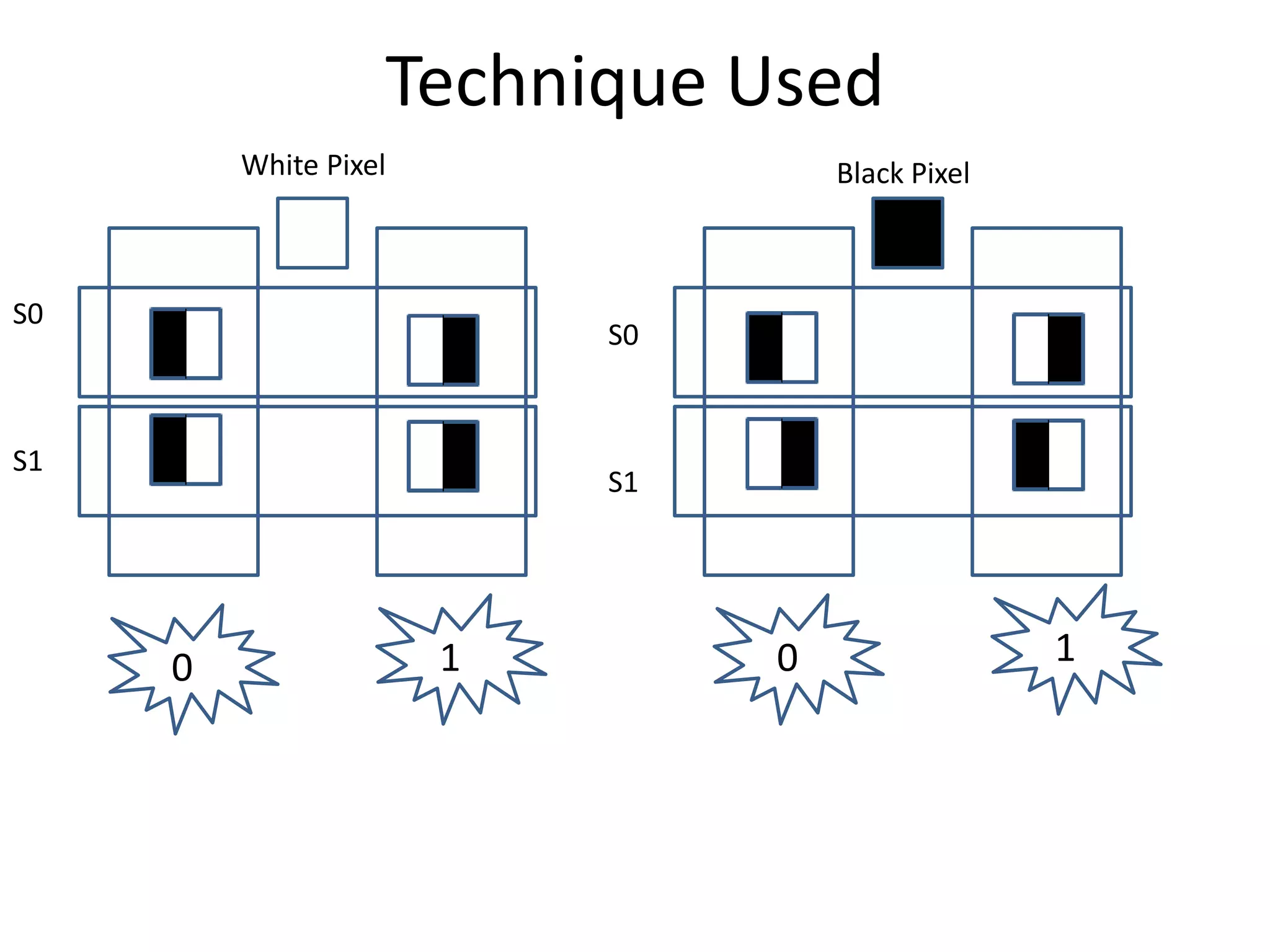
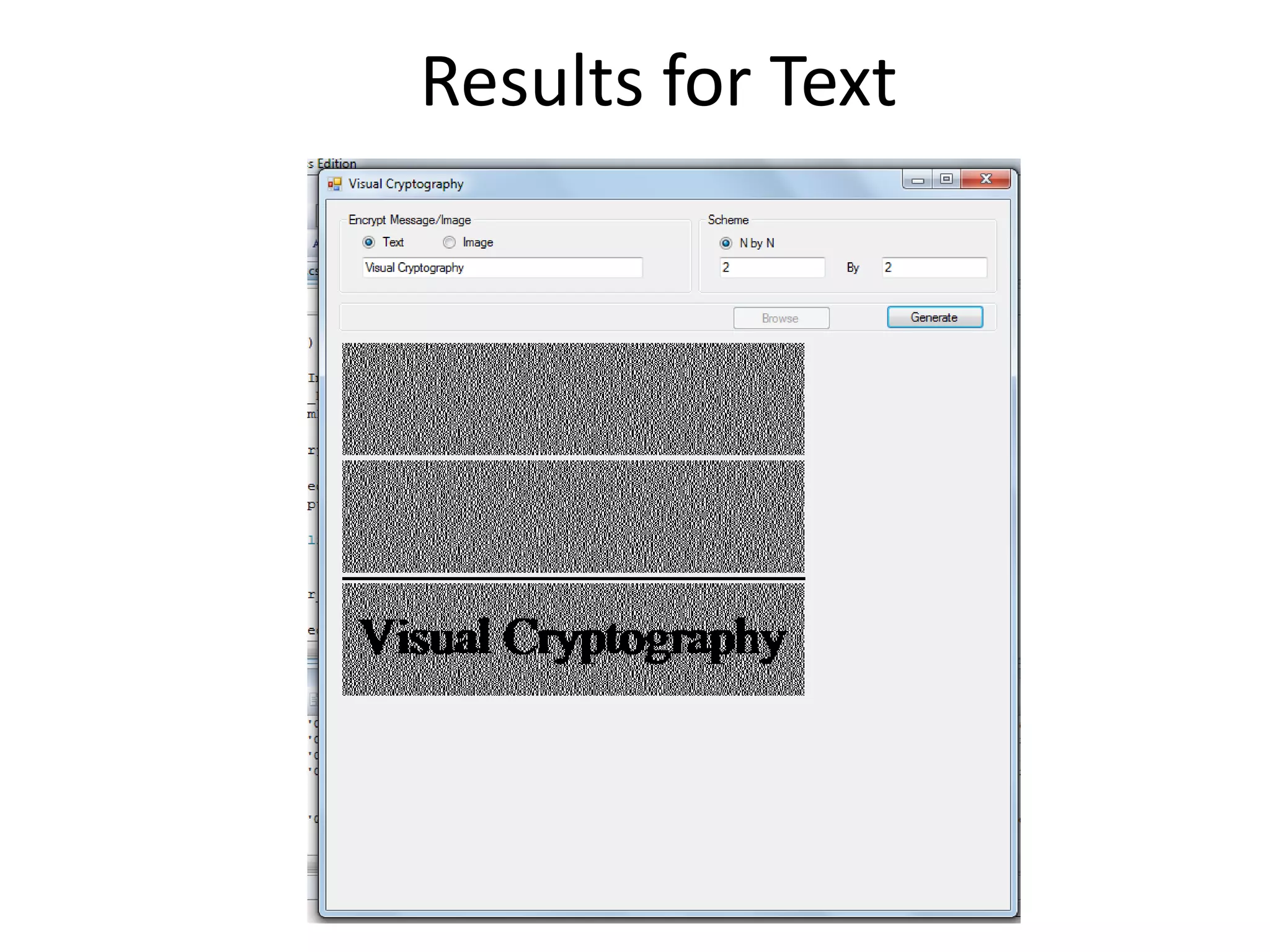
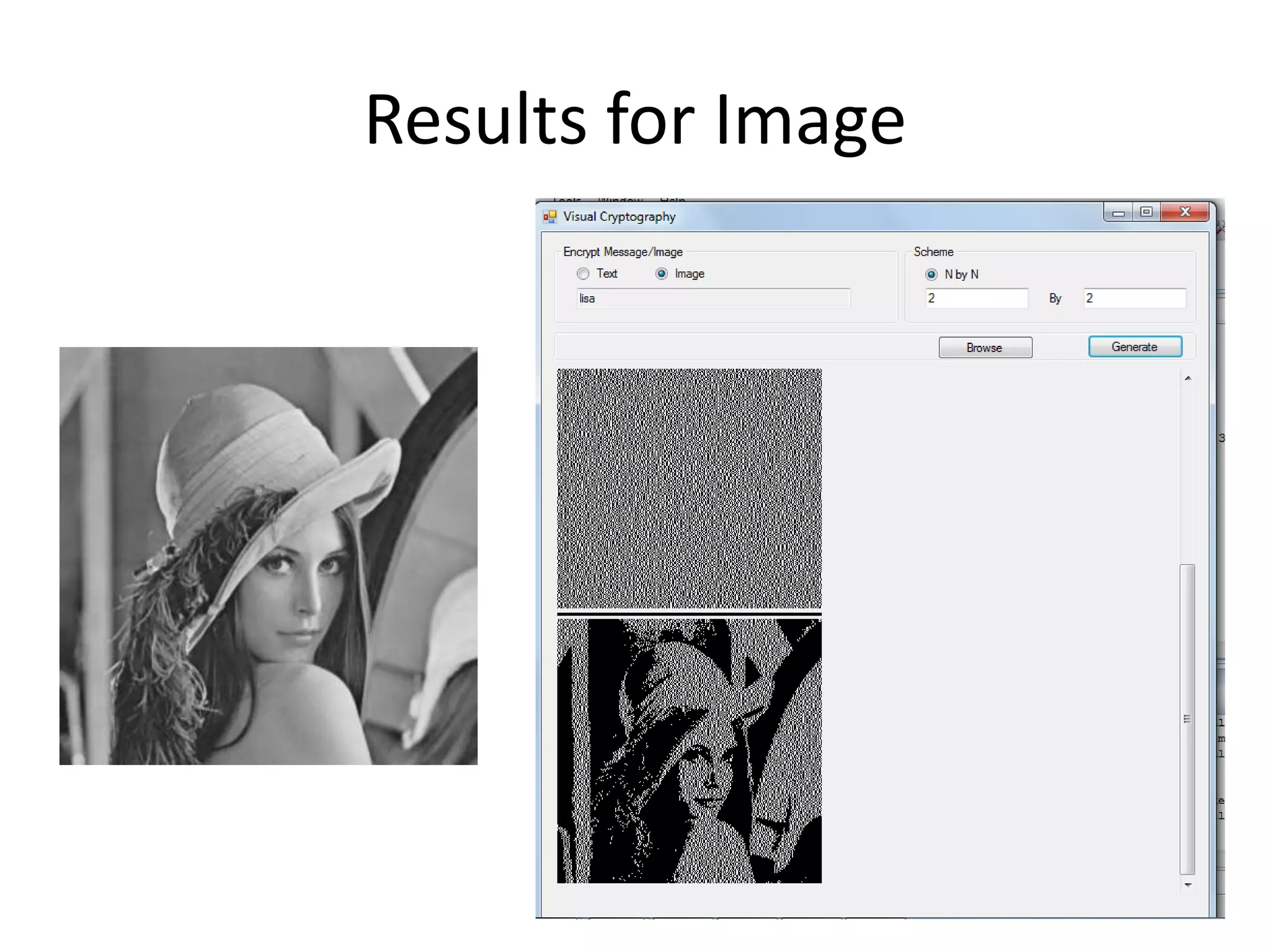
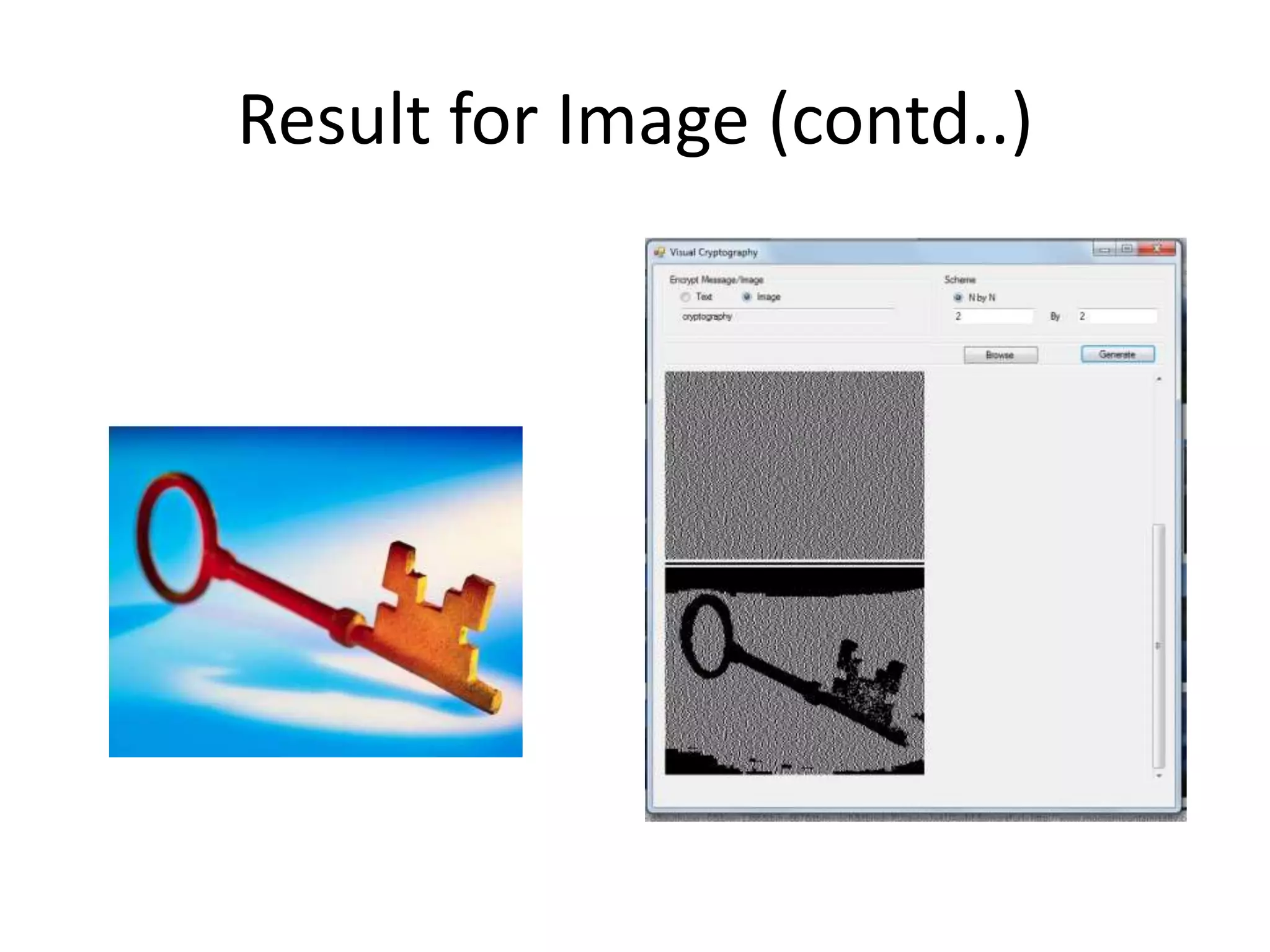
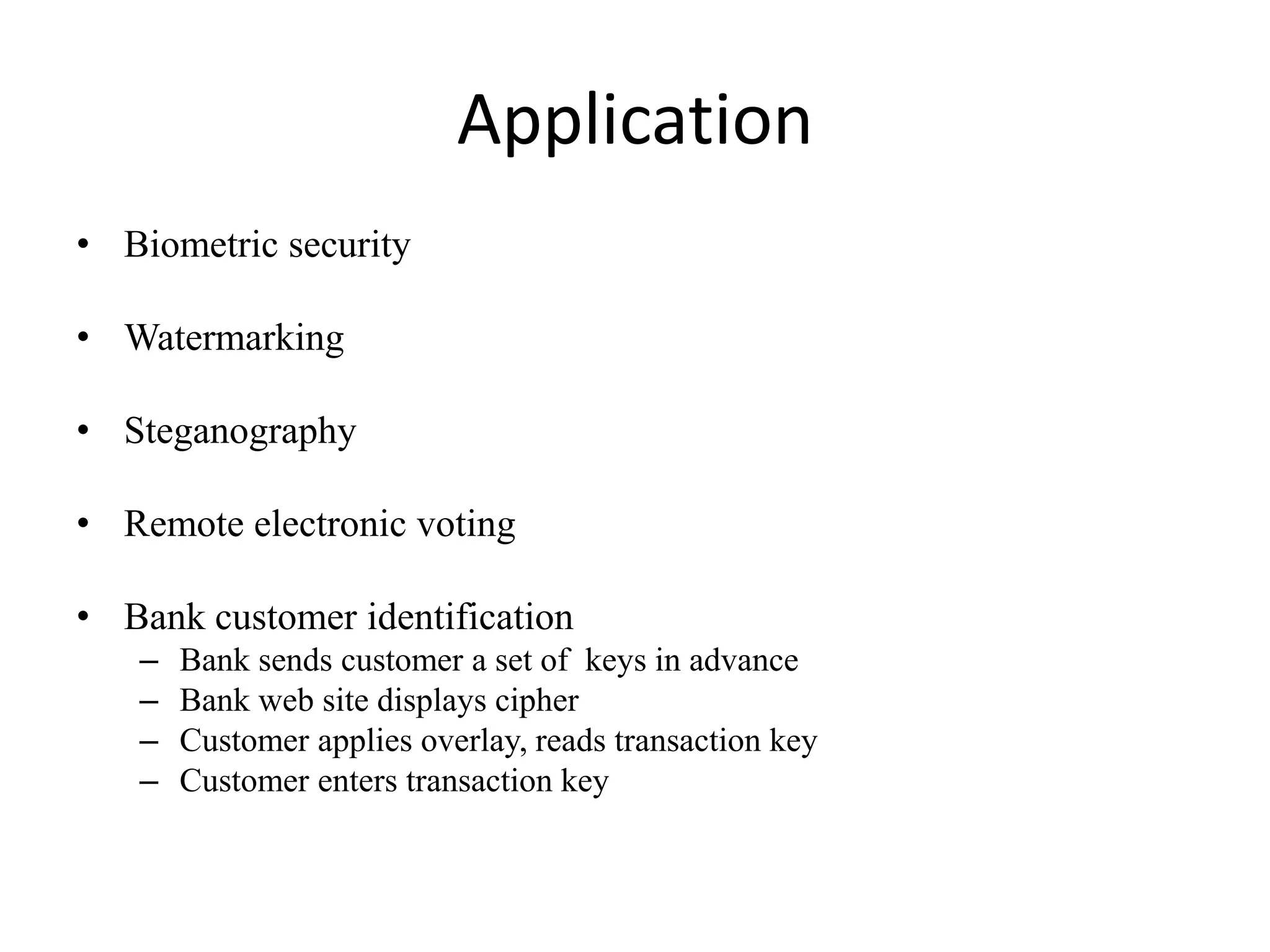
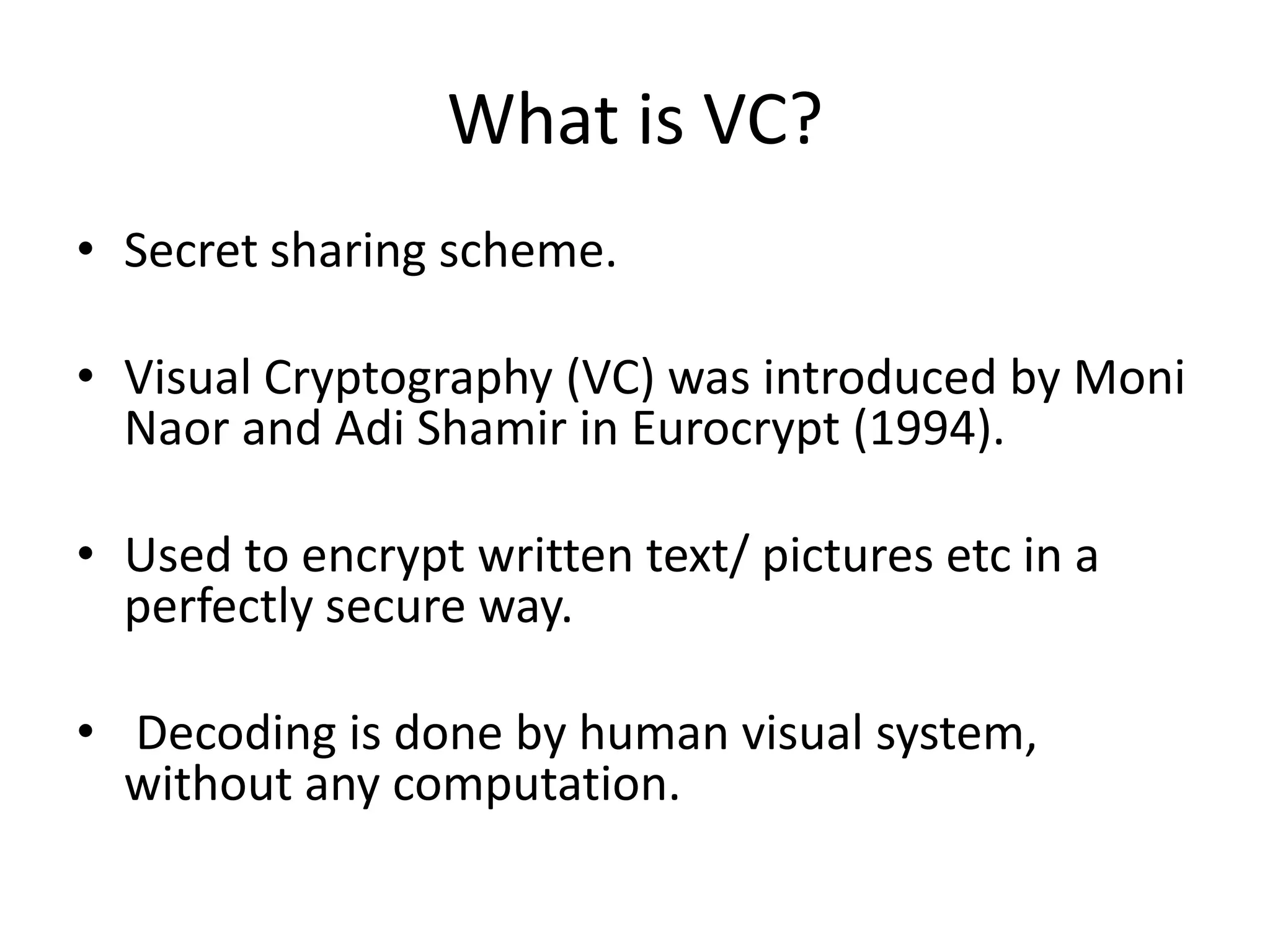
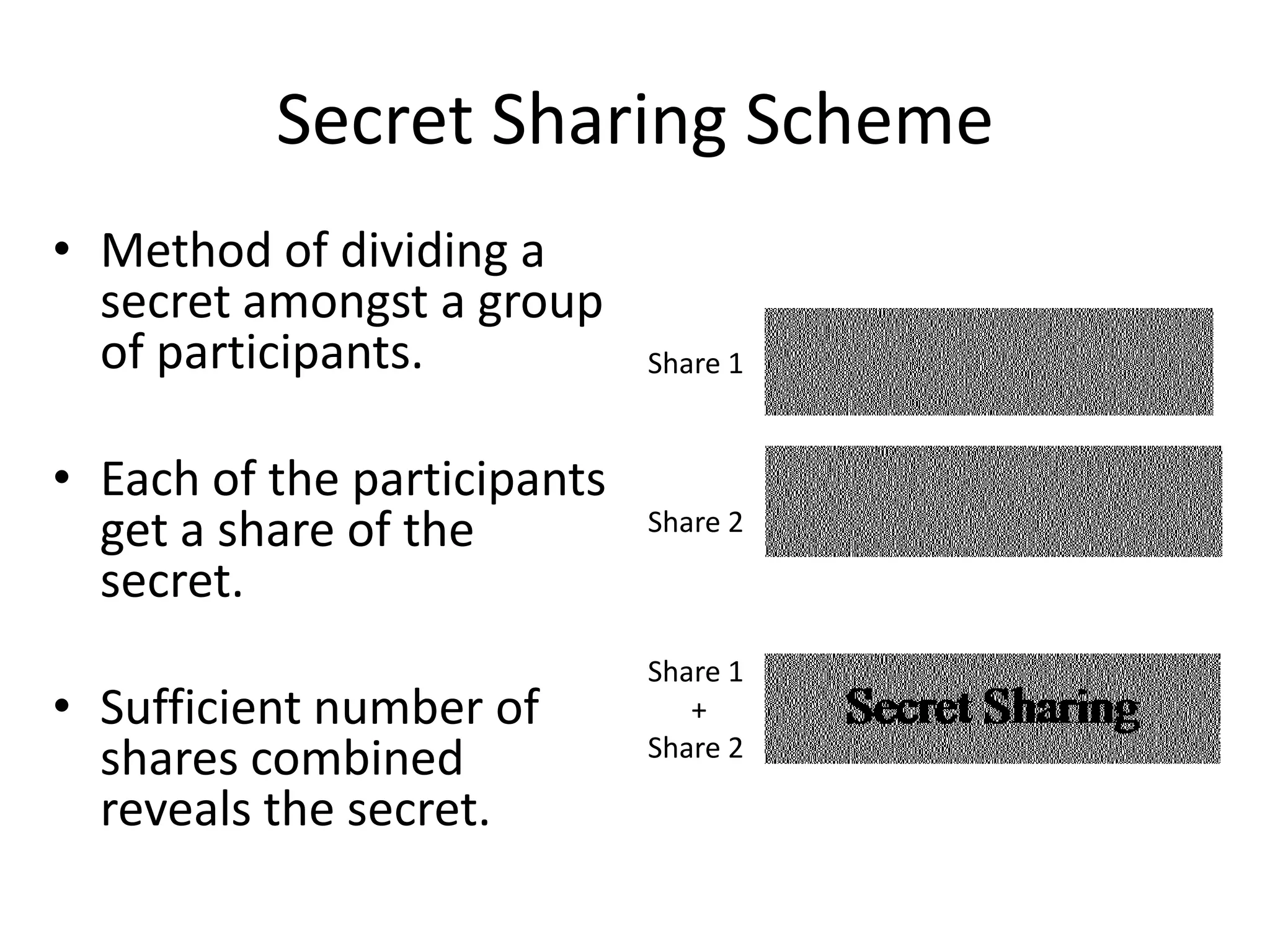
Visual cryptography is a secret sharing scheme that allows for the encryption of written text or images in a perfectly secure way without any computation. It works by dividing the secret into multiple shares, where only when a sufficient number of shares are superimposed can the secret be revealed to the human visual system. For example, in a 2 by 2 scheme, a secret image is encoded into two shares such that individually the shares reveal no information, but when overlayed together the secret image is revealed, though with some loss of contrast and resolution. Visual cryptography has applications in security, watermarking, and remote voting.



![Preliminary Notations (contd..)
• C0 = Collection of n × m Boolean matrices for shares of
white pixel.
• C1 = Collection of n × m Boolean matrices for shares of
black pixel.
• V = ORed k rows.
• H(V) = Hamming weight.
• d = number in [1,m]](https://image.slidesharecdn.com/myprescrypto-130103124511-phpapp02/75/Visual-CryptoGraphy-6-2048.jpg)
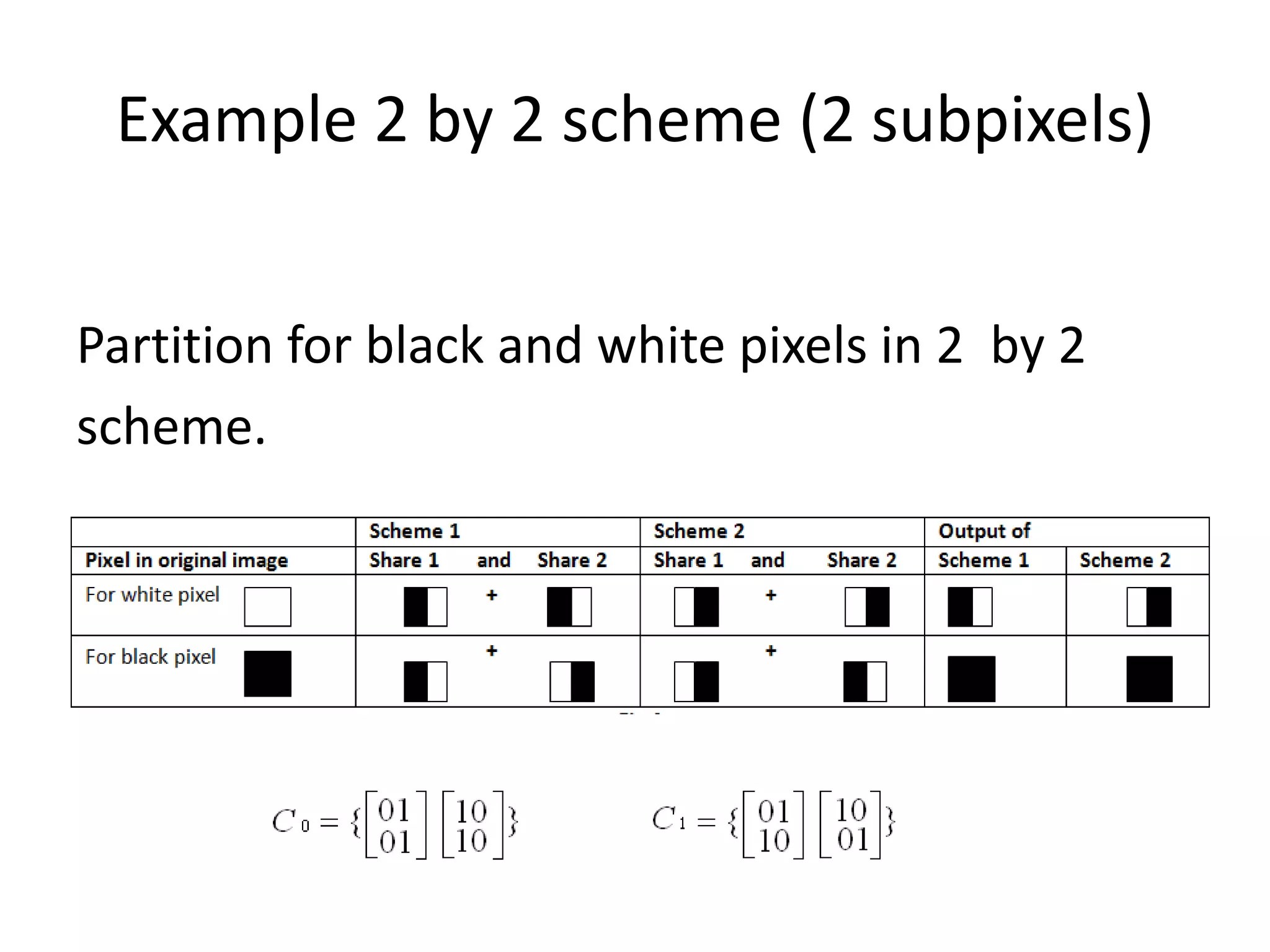
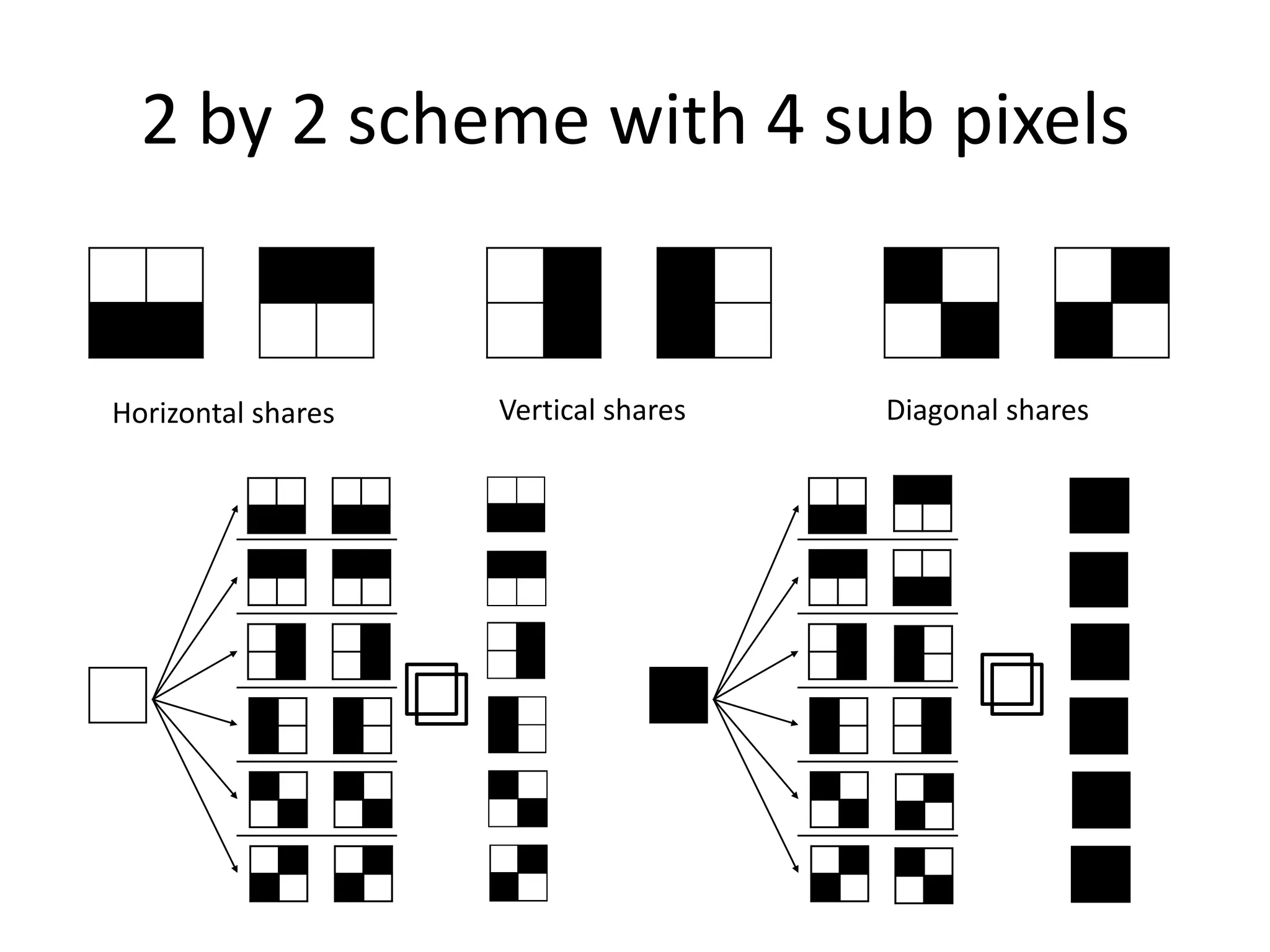
![Example 2 by 2 scheme (2 subpixels)
This scheme can be explained by below values
• n=2 • V1 = [1,1] or [1,1]
• m=2 • H(V0 ) = 1
• k=2 • H(V1) = 2
• V0 = [0,1] or [1,0] • ɑ = H(V1) - H(V0 ) / m = 1/2](https://image.slidesharecdn.com/myprescrypto-130103124511-phpapp02/75/Visual-CryptoGraphy-8-2048.jpg)