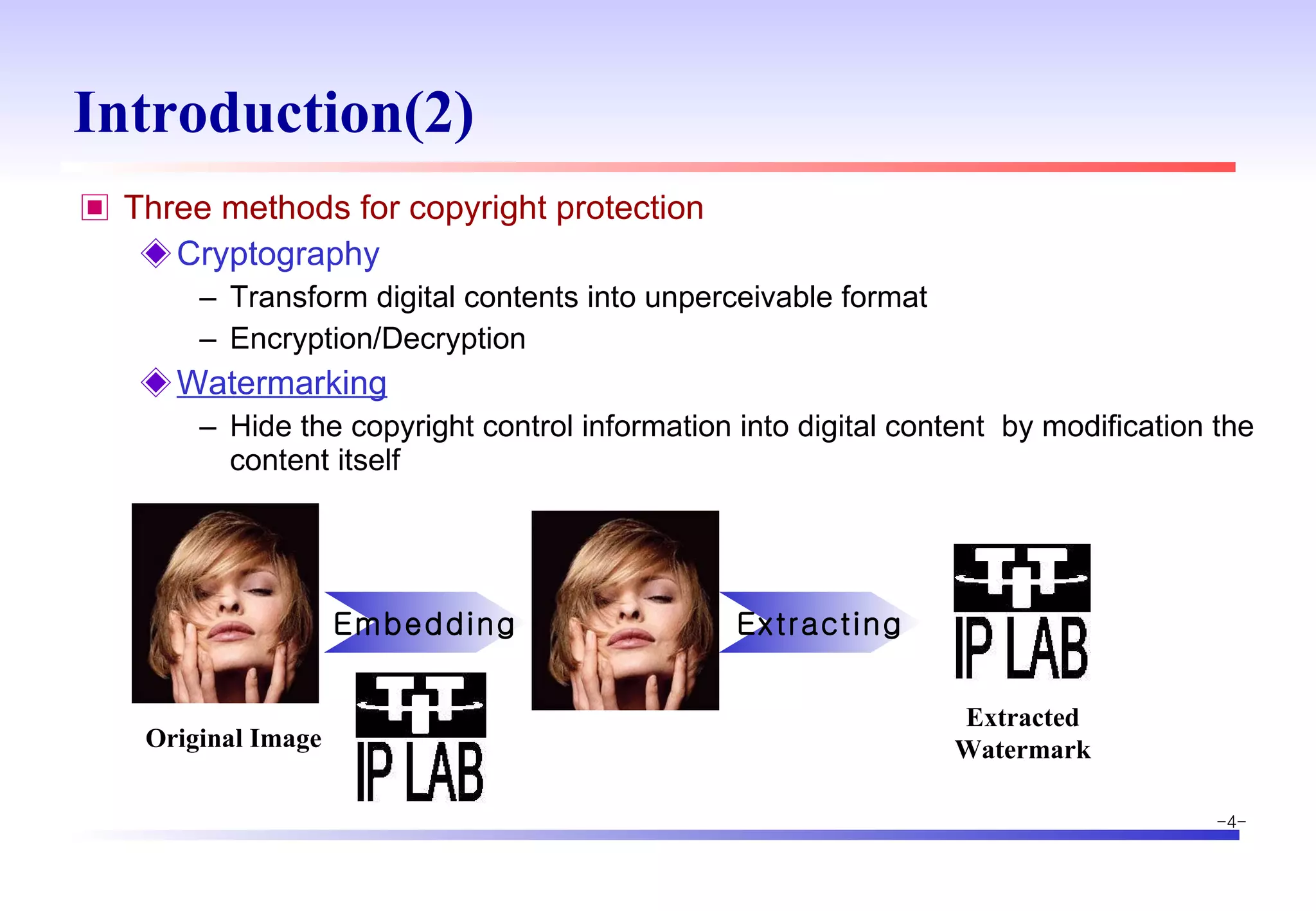
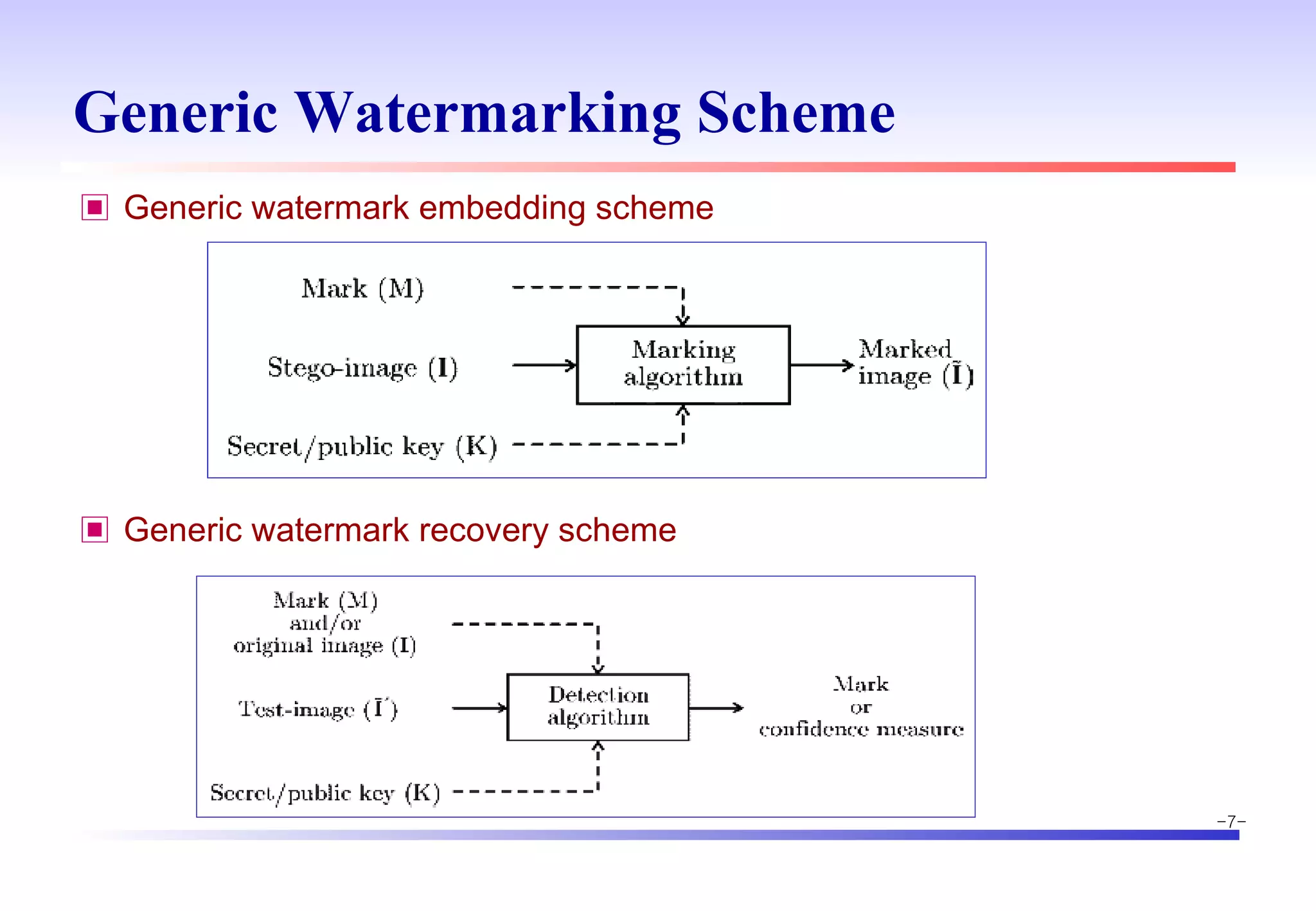
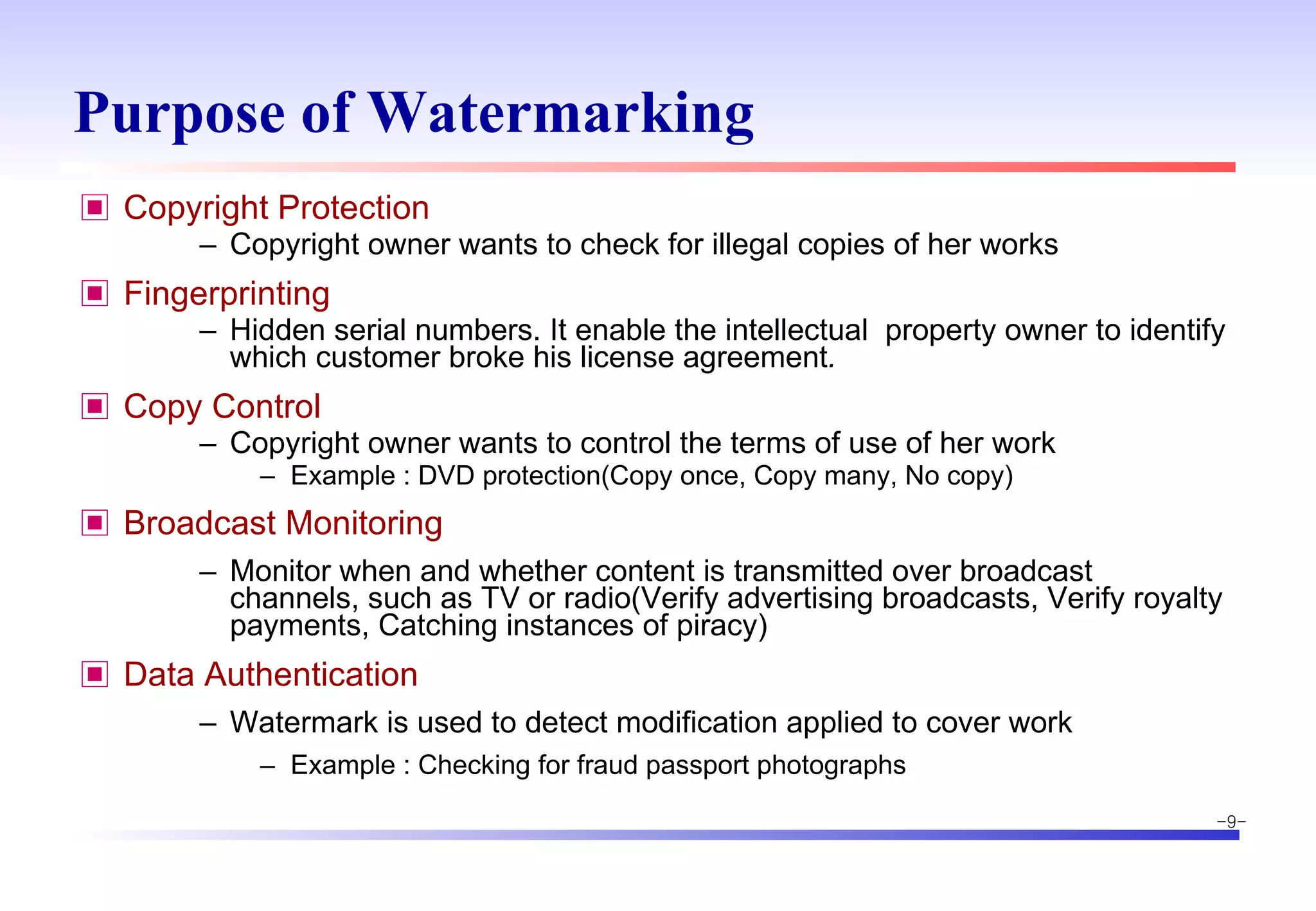
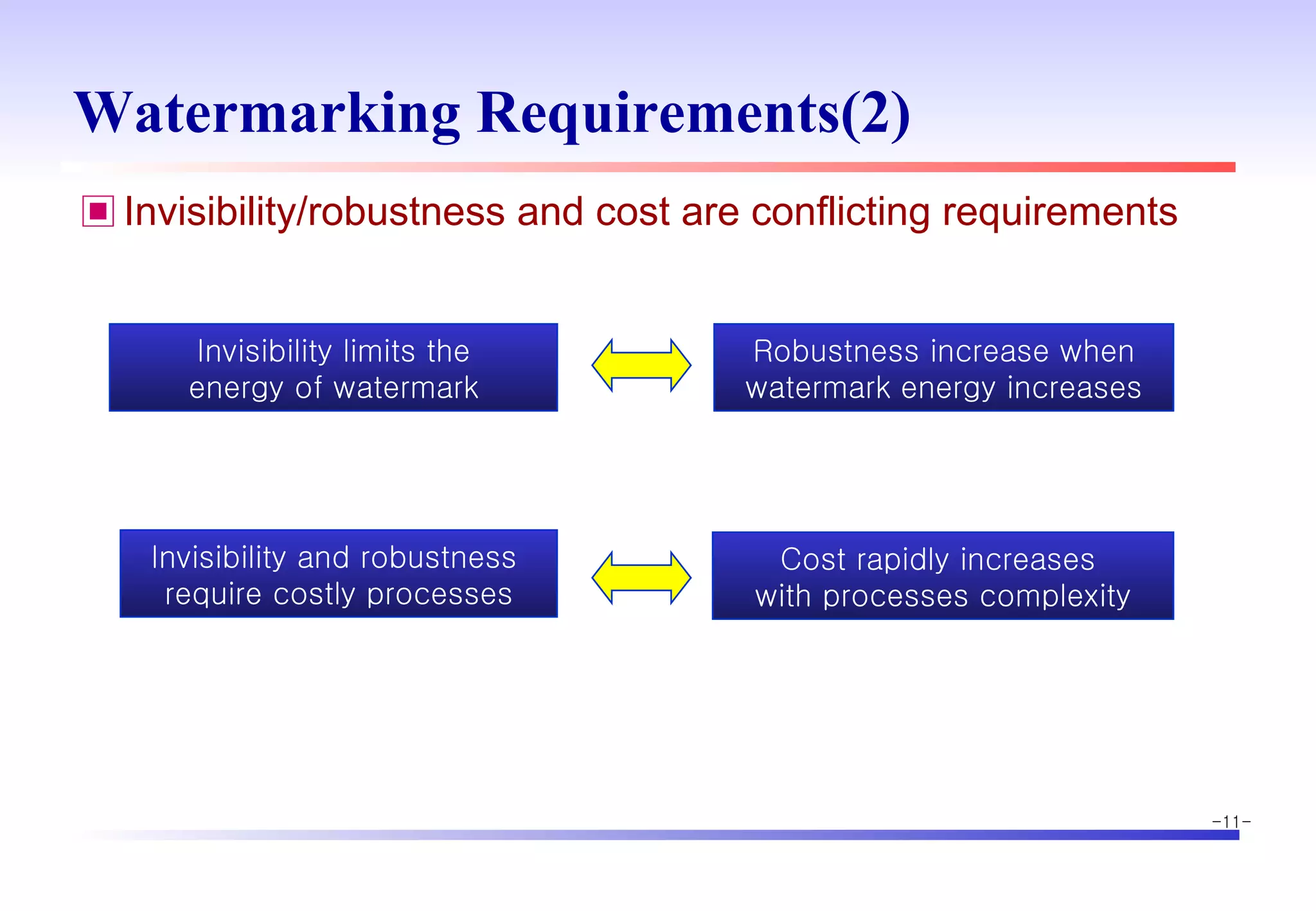
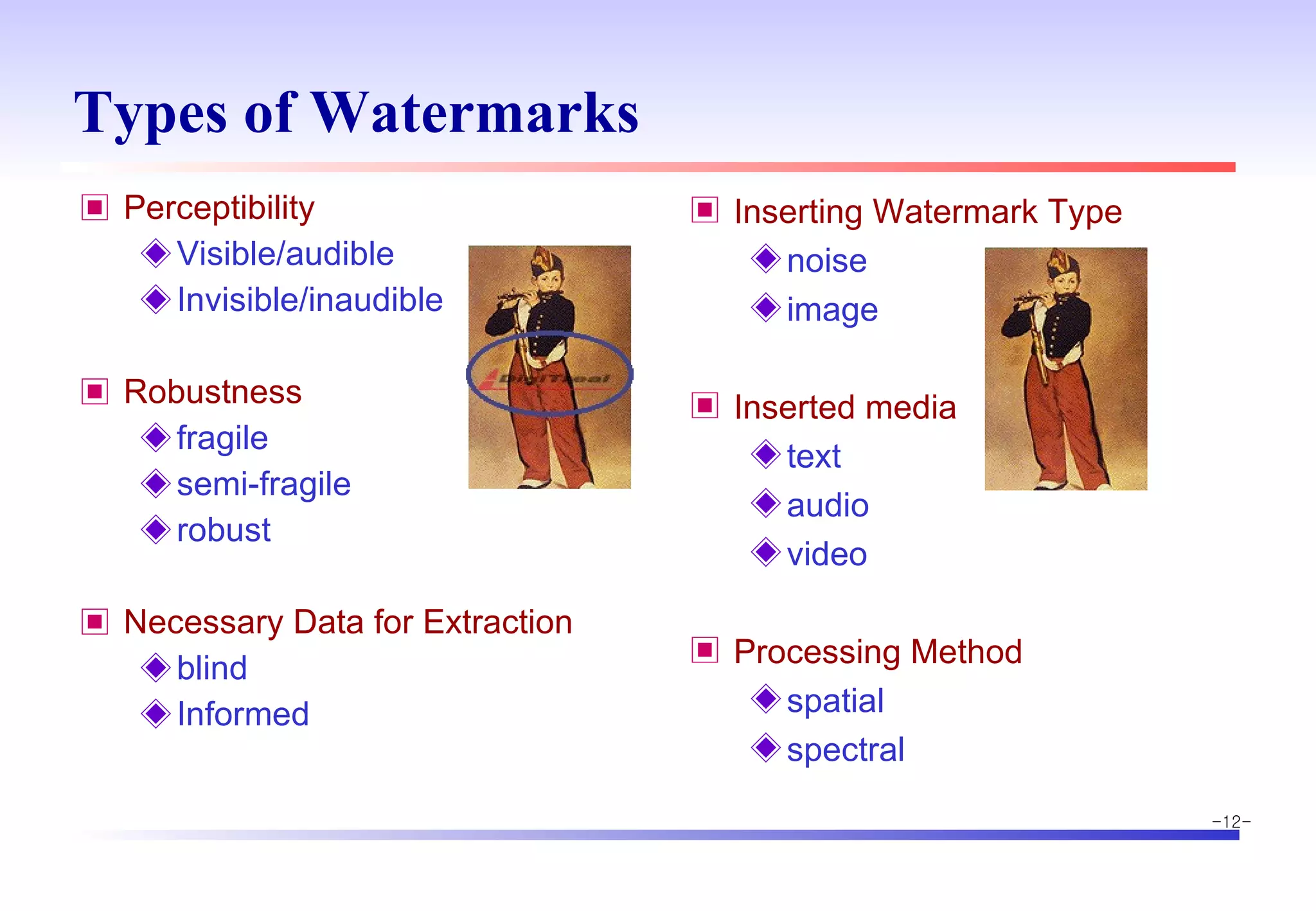
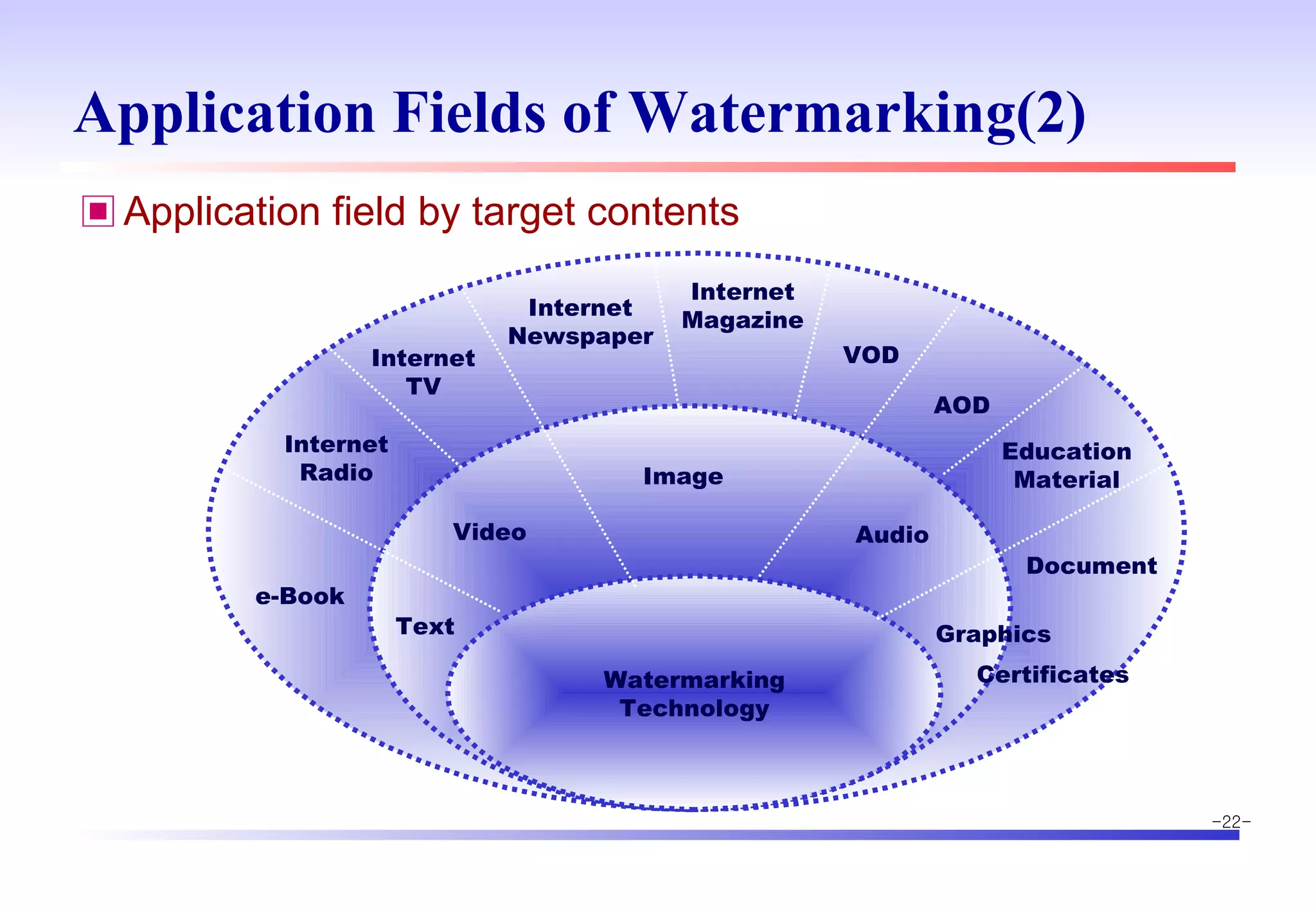
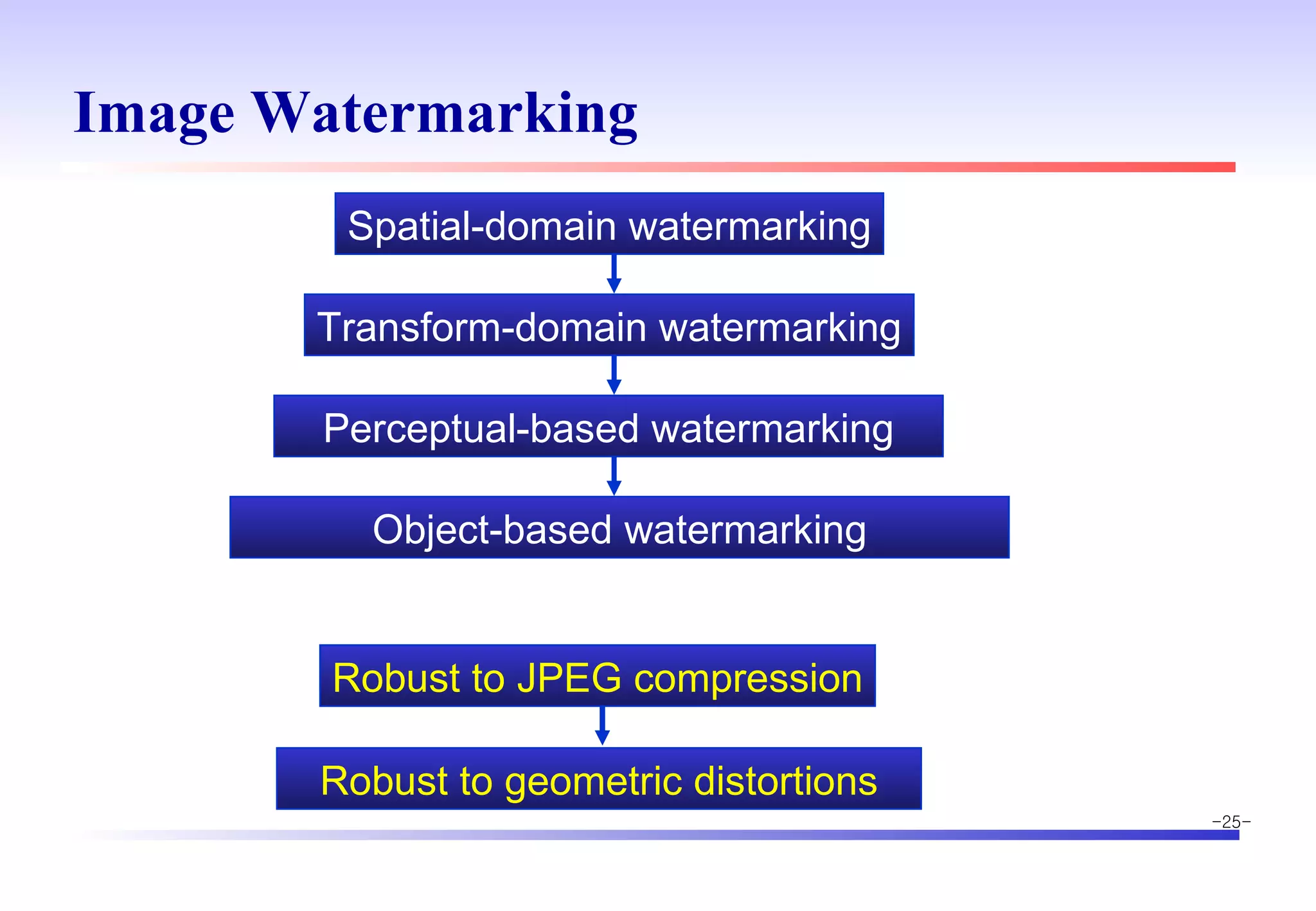
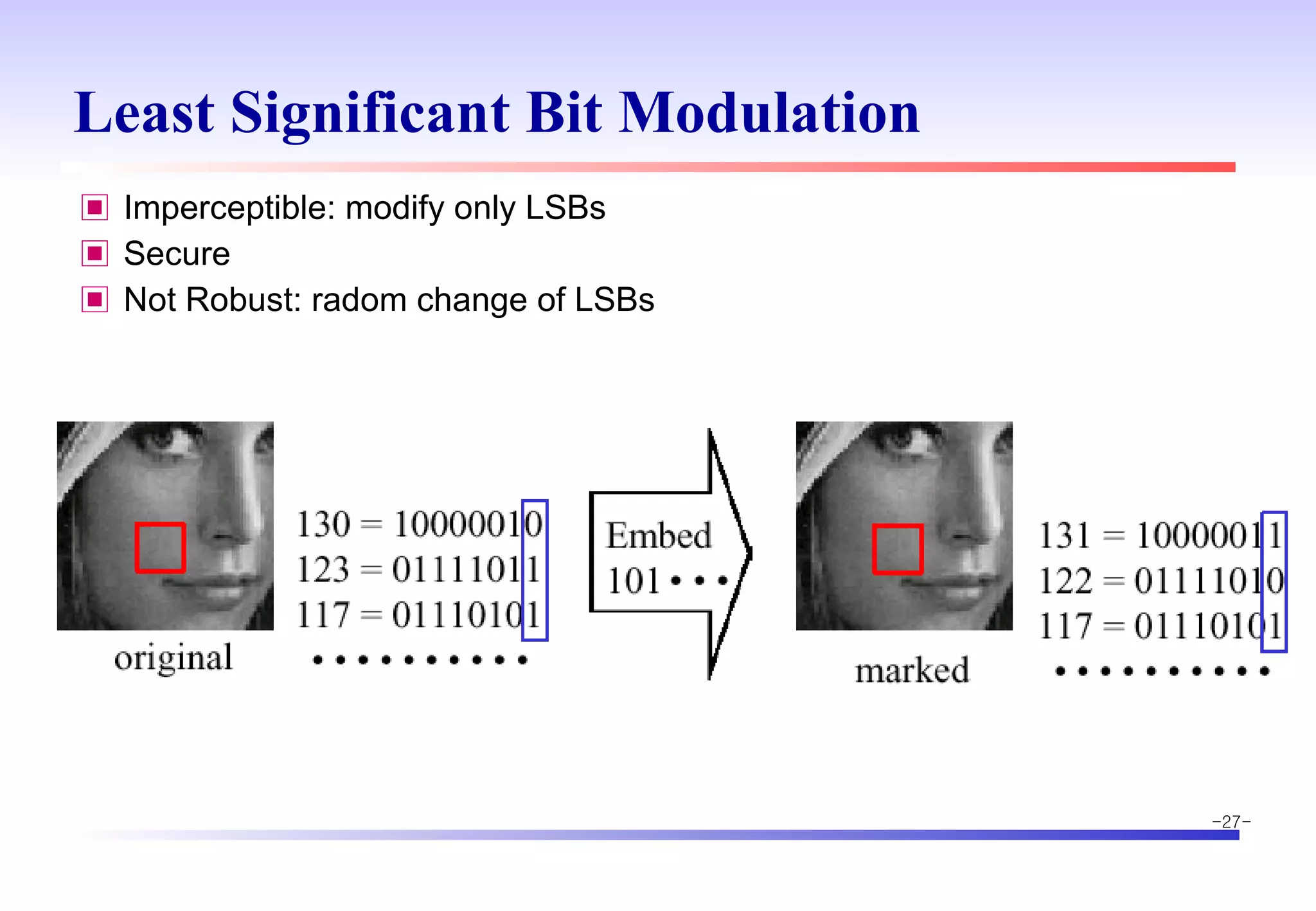
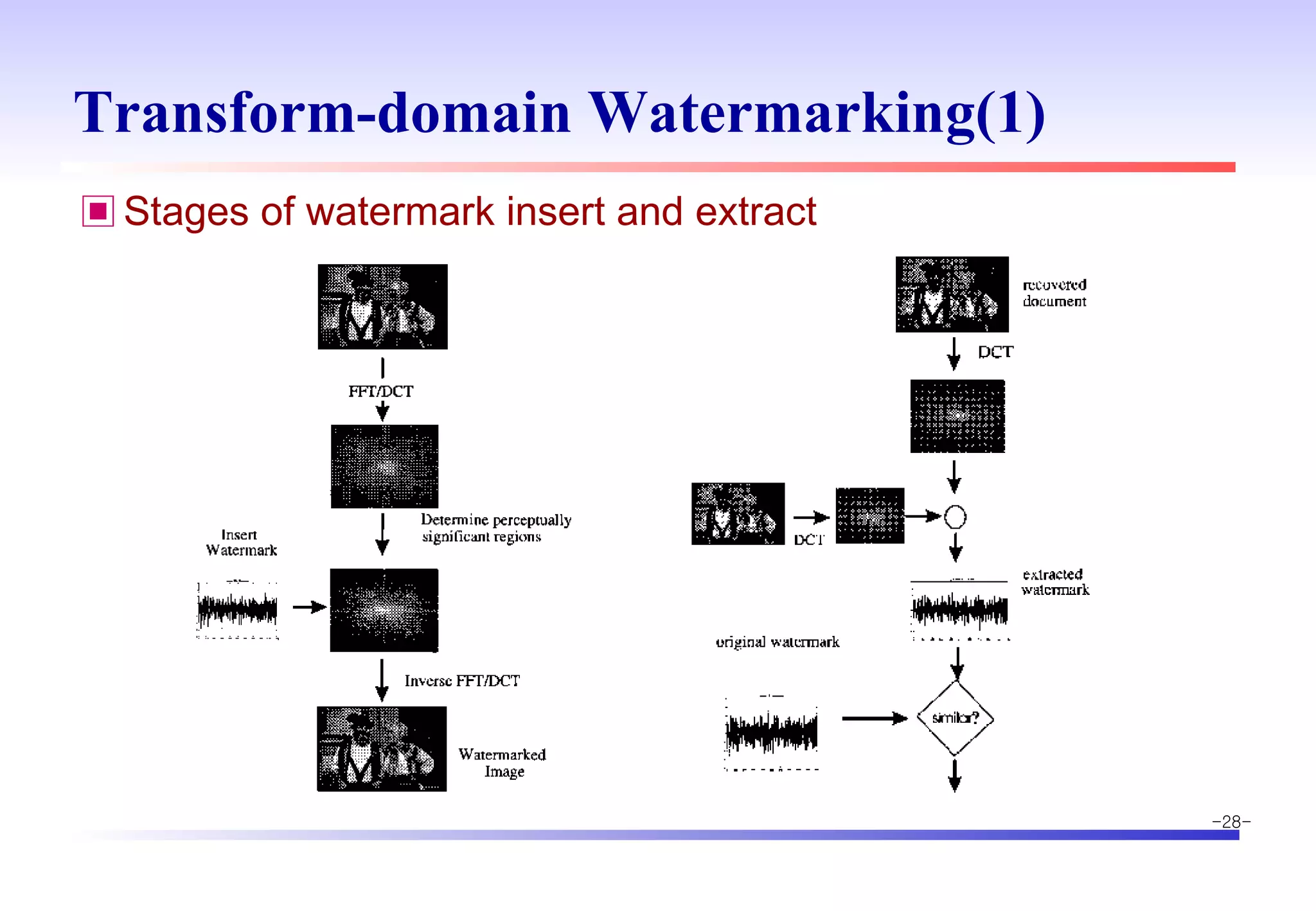
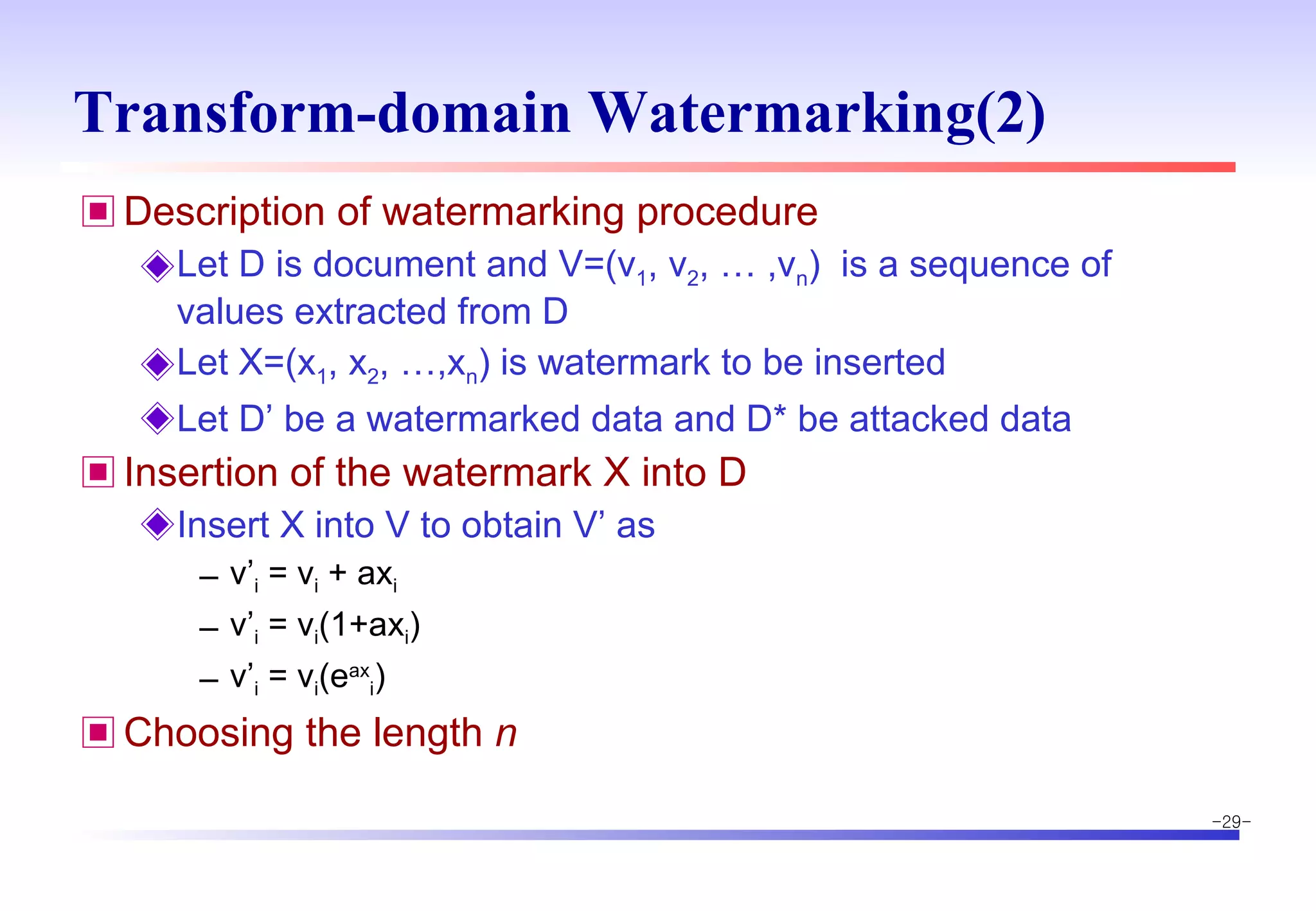
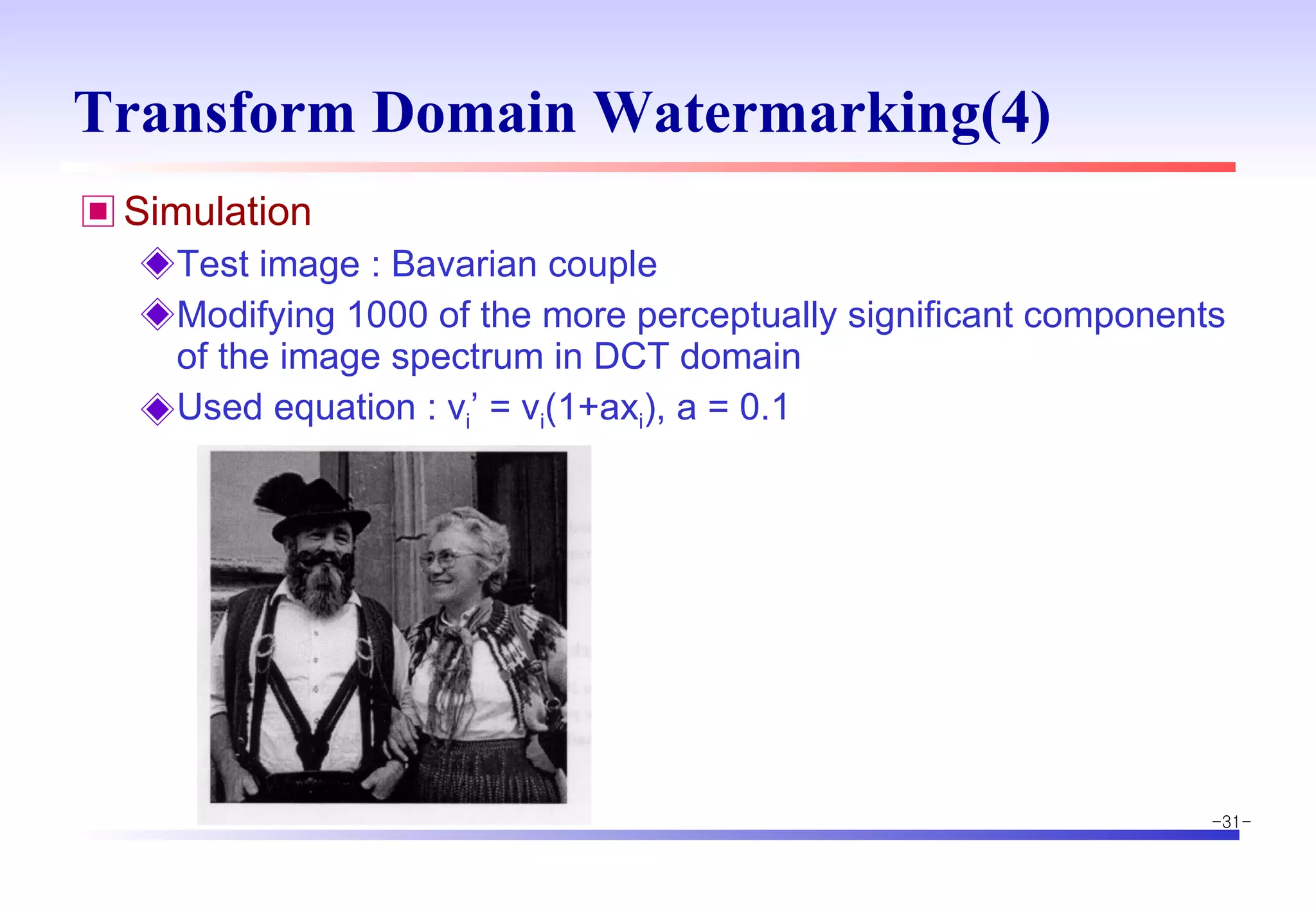
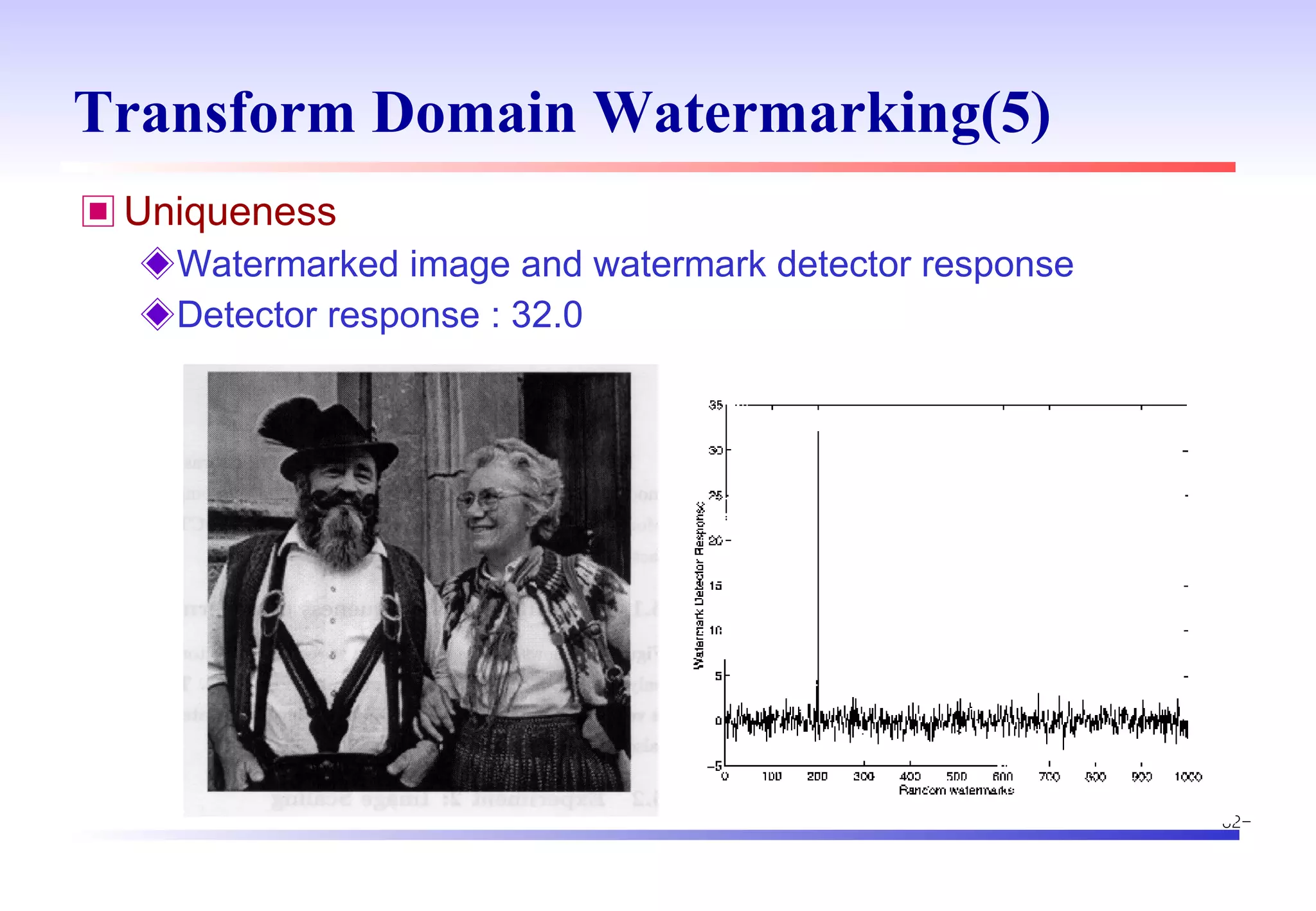
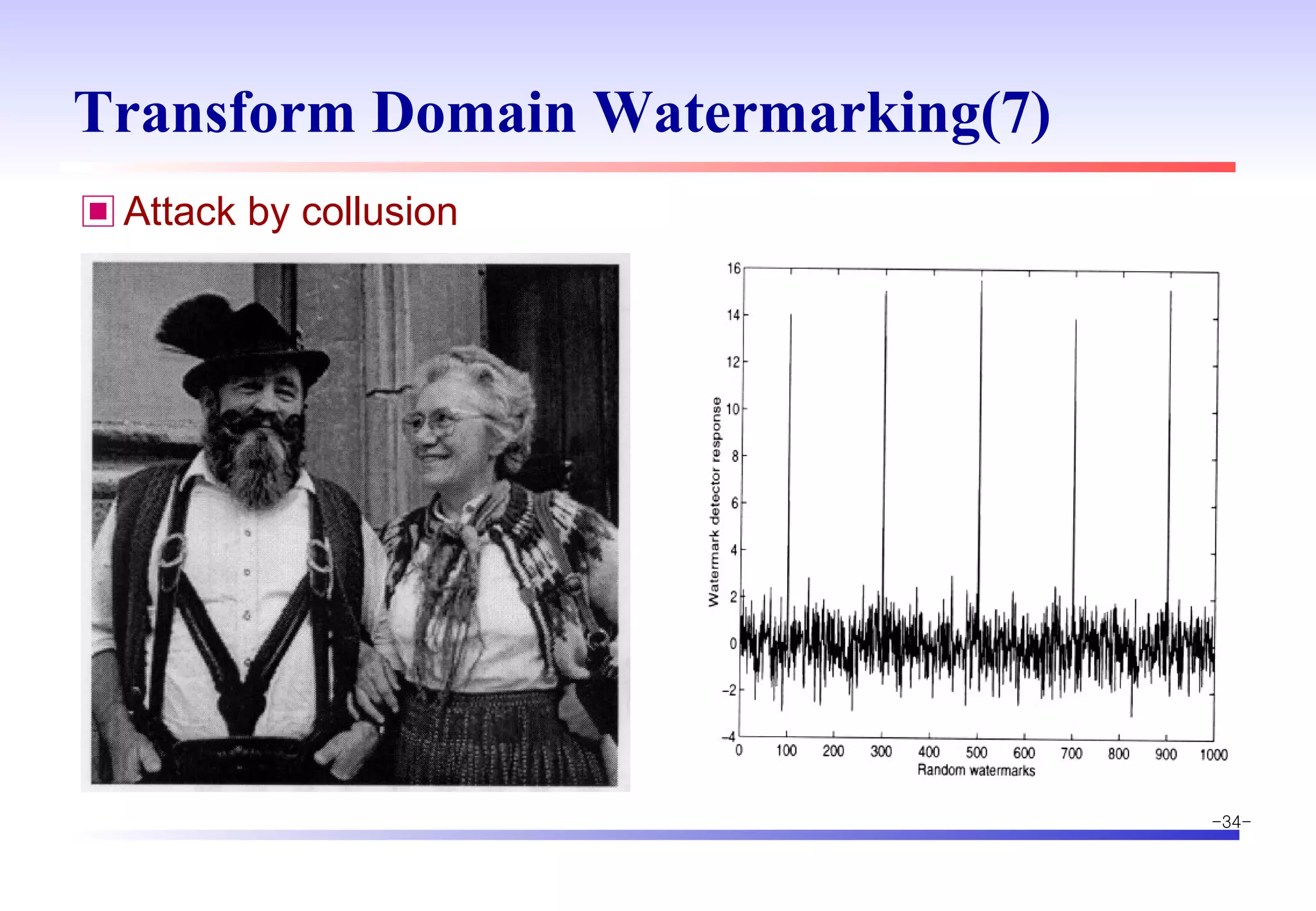
The document discusses digital image watermarking techniques for copyright protection. It introduces watermarking requirements like perceptual transparency and robustness. Common watermarking techniques include spatial-domain methods that modify pixel values and transform-domain methods that modify frequency coefficients. Transform techniques can provide stronger, more robust watermarks but are also more computationally expensive. The document also outlines various attacks against watermarked images and applications of digital watermarking technology.