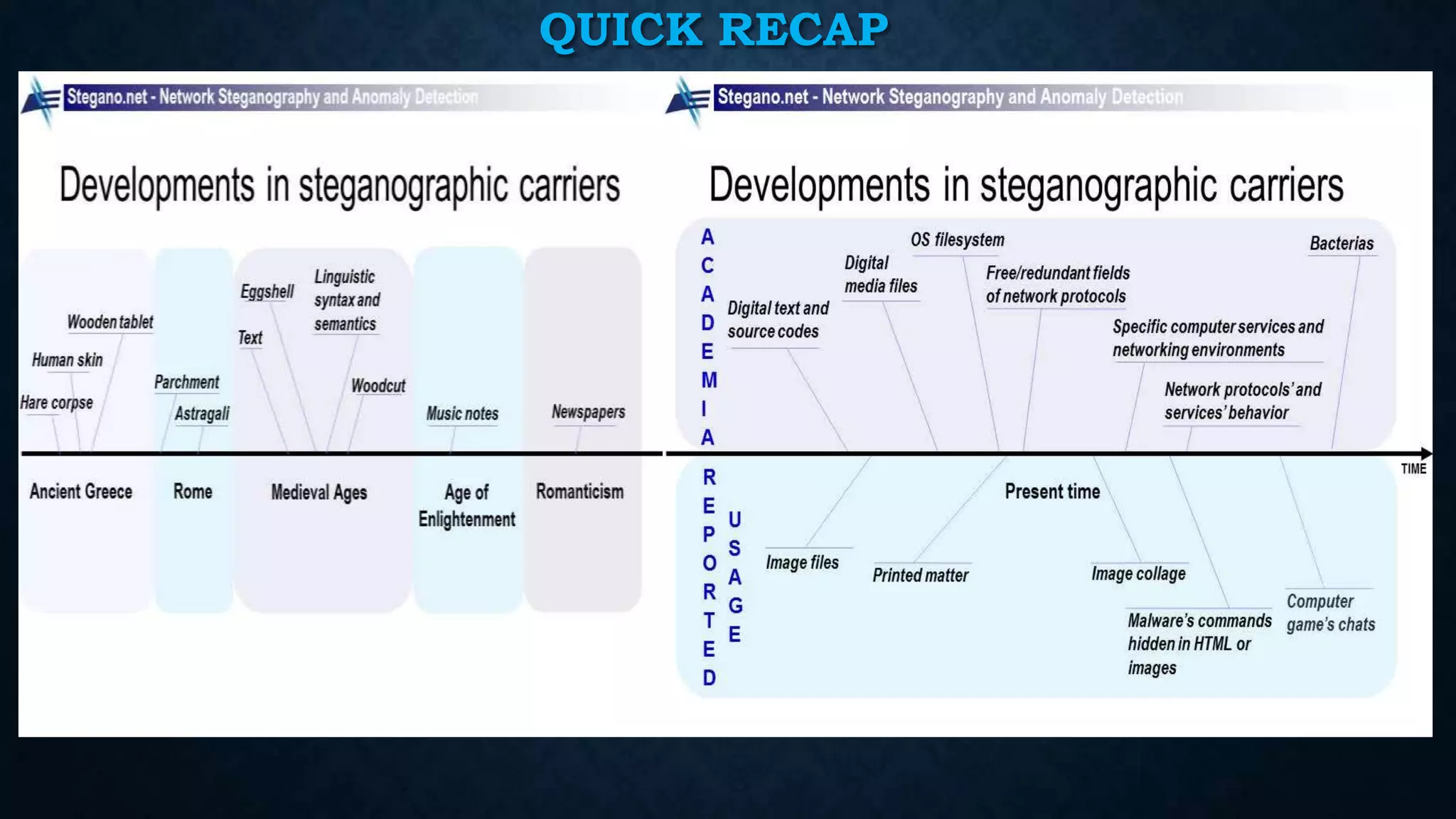
The document provides an overview of steganography, which is the practice of hiding secret messages within other innocent messages or files. It discusses the differences between steganography and cryptography, various historical uses of steganography, and modern techniques such as hiding messages in digital images, audio, video and network traffic. The document also briefly outlines tools for steganography, challenges in steganalysis, and concludes with references for further information.



![HISTORICAL PERSPECTIVE
• Dates back to 400 BC when Histaeus sent a message, by shaving the
head of his most trusted slave, then tattooed a message on the slave's
scalp, to his friend Aristagorus, urging revolt against the Persians.
• Demaratus tells Athens of Persia’s attack plans by writing the secret
message on a tablet, & covers it with wax.
• Chinese wrote messages on silk and encased them in balls of wax. The
wax ball, "la wan," could then be hidden in the messenger.
• A more subtle method, nearly as old, is to use invisible ink( lemon juice,
milk, or urine, all of which turn dark when held over a flame).
• Microdots used by Germany in WW2 documents shrunk to the size of a
dot & embedded within innocent letters. Inkjet dots smaller than human
eyes can see.
5
Wentworth Miller
[Prison Break Serial]](https://image.slidesharecdn.com/steganography-140107235918-phpapp02/75/Steganography-Presentation-5-2048.jpg)